In today’s digital world, user engagement is key to the success of any application. Implementing DevSecOps practices is essential for ensuring security, reliability, and efficient deployment processes. In this project, we aim to implement DevSecOps for deploying an OpenAI Chatbot UI. We will use Kubernetes (EKS) for container orchestration, Jenkins for Continuous Integration/Continuous Deployment (CI/CD), and Docker for containerization.
What is ChatBOT?
ChatBOT is an AI-powered conversational agent trained on extensive human conversation data. It utilizes natural language processing techniques to understand user queries and provide human-like responses. By simulating natural language interactions, ChatBOT enhances user engagement and provides personalized assistance to users.
Why ChatBOT?
1. Personalized Interactions: ChatBOT enables personalized interactions by understanding user queries and responding in a conversational manner, fostering engagement and satisfaction.
2. 24/7 Availability: Unlike human agents, ChatBOT is available 24/7, ensuring instant responses to user queries and delivering a seamless user experience round the clock.
3. Scalability: With ChatBOT deployed in our application, we can efficiently handle a large volume of user interactions, ensuring scalability as our user base expands.
How We’re Deploying ChatBOT?
1. Containerization with Docker: We’re containerizing the ChatBOT application using Docker, which provides lightweight, portable, and isolated environments for running applications. Docker enables consistent deployment across different environments, simplifying the deployment process and ensuring consistency.
2. Orchestration with Kubernetes (EKS): Kubernetes provides powerful orchestration capabilities for managing containerized applications at scale. We’re leveraging Amazon Elastic Kubernetes Service (EKS) to deploy and manage our Docker containers efficiently. EKS automates container deployment, scaling, and management, ensuring high availability and resilience.
3. CI/CD with Jenkins: Jenkins serves as our CI/CD tool for automating the deployment pipeline. We’ve configured Jenkins to continuously integrate code changes, run automated tests, and deploy the ChatBOT application to EKS. By automating the deployment process, Jenkins accelerates the delivery of updates and enhancements, improving efficiency and reliability.
4. DevSecOps Practices: Throughout the deployment pipeline, we’re integrating security practices into every stage to ensure the security of our ChatBOT application. This includes vulnerability scanning, code analysis, and security testing to identify and mitigate potential security threats early in the development lifecycle.
By implementing DevSecOps practices and leveraging modern technologies like Kubernetes, Docker, and Jenkins, we’re ensuring the secure, scalable, and efficient deployment of ChatBOT, enhancing user engagement and satisfaction.
Step:1 :- Create Jenkins Server.
- Clone the GitHub repository.
GITHUB REPO: [Chatbot-UI](github repo)
git clone (github repo)
cd Jenkins-Server-TF
2. Before proceeding to next steps. Do the following things.
i. Create a DynamoDB table named “Lock-Files”.
ii. Create a Key-Pair and download the PEM file.
iii. Create a user and save the access keys.
iv. Create an S3 bucket.
v. Download Terraform and AWS CLI.
#Terraform Installation Script
wget -O- https://apt.releases.hashicorp.com/gpg | sudo gpg - dearmor -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/hashicorp.list
sudo apt update
sudo apt install terraform -y
#AWSCLI Installation Script
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
sudo apt install unzip -y
unzip awscliv2.zip
sudo ./aws/install3. Do some modifications to the backend.tf file such as changing the bucket name and DynamoDB table.
4. Configure AWS CLI: Run the below command, and add your access keys.
aws configure5. You have to replace the Pem File name with one that is already created on AWS.
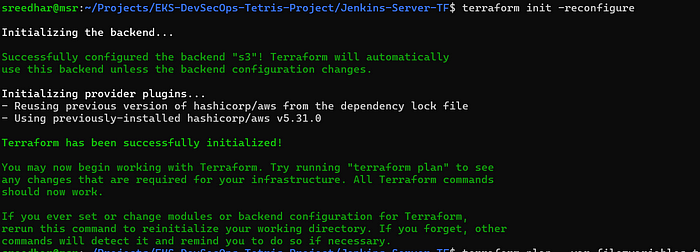
6. Initialize the backend by running the below command.
terraform init7. Run the below command to get the blueprint of what kind of AWS services will be created.
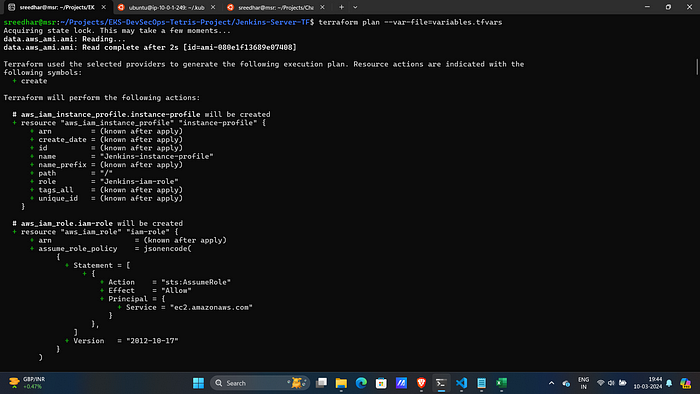
terraform plan -var-file=variables.tfvars8. Now, run the below command to create the infrastructure on AWS Cloud which will take 3 to 4 minutes maximum.
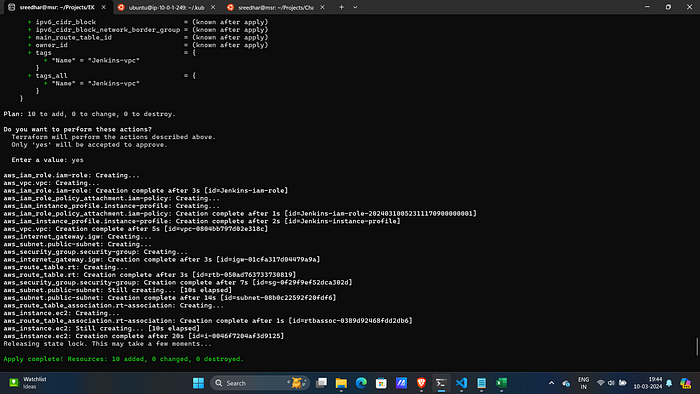
terraform apply -var-file=variables.tfvars --auto-approve9. Upon success,this will create an ec2 server with name “Jenkins-server”.
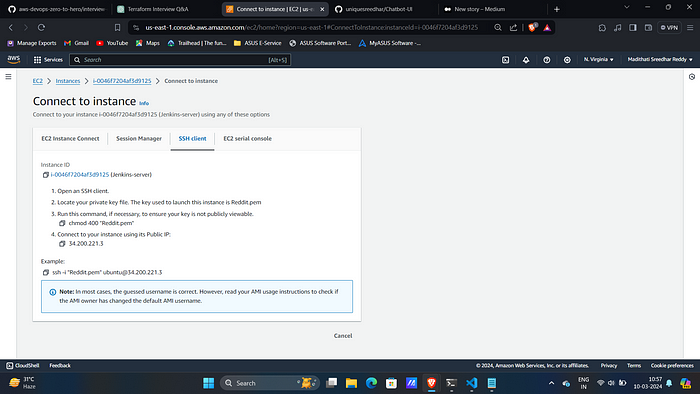
10. Connect to it with SSH.
Step:2 :- Configure Jenkins server.
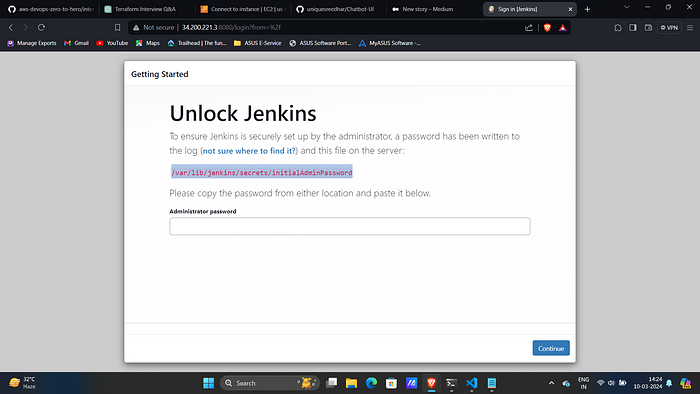
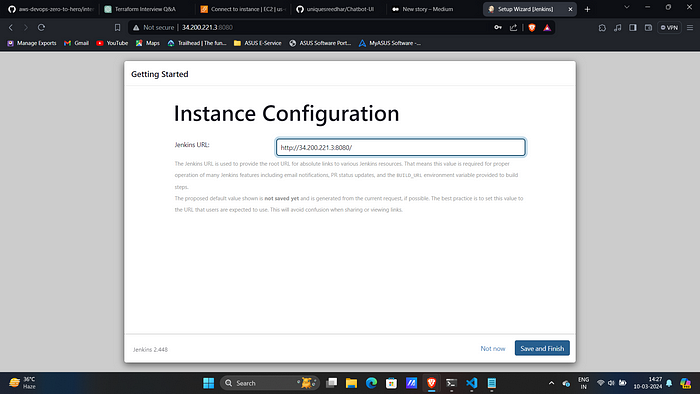
- Access jenkins on port 8080 of ec2 public ip.
2. Now, run the below command to get the administrator password and paste it on your Jenkins.
sudo cat /var/lib/jenkins/secrets/initialAdminPassword\
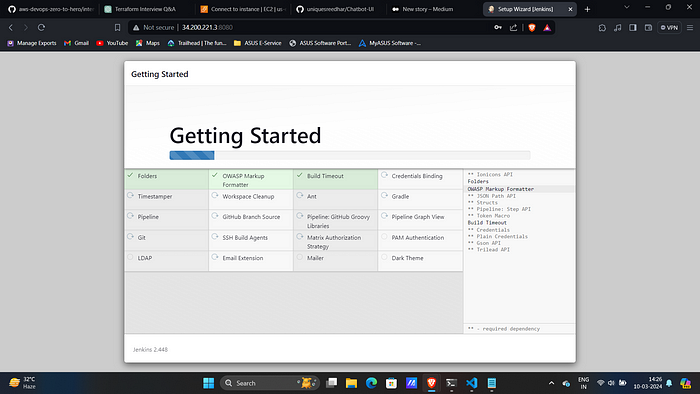
3. Install suggested plugins.
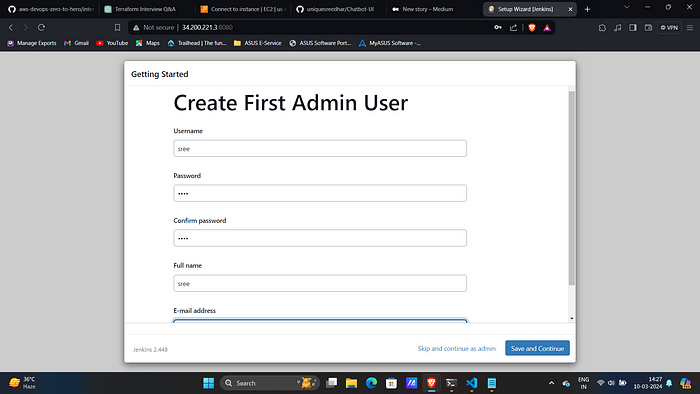
4. Create user help us customize username and password of Jenkins.
5. Save and Continue all the rest.
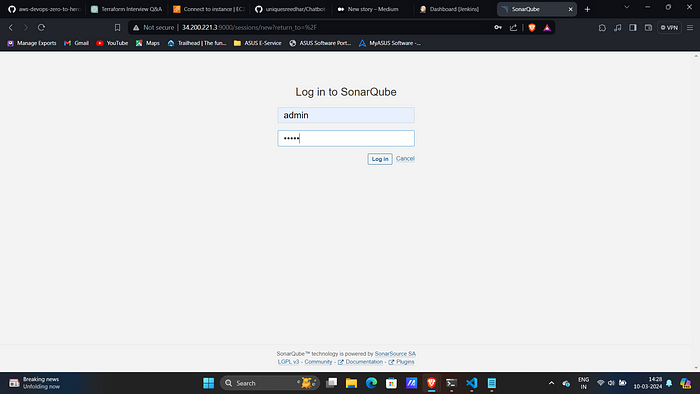
6. Access SonarQube on port 9000 of Same Jenkins server.
Username: admin
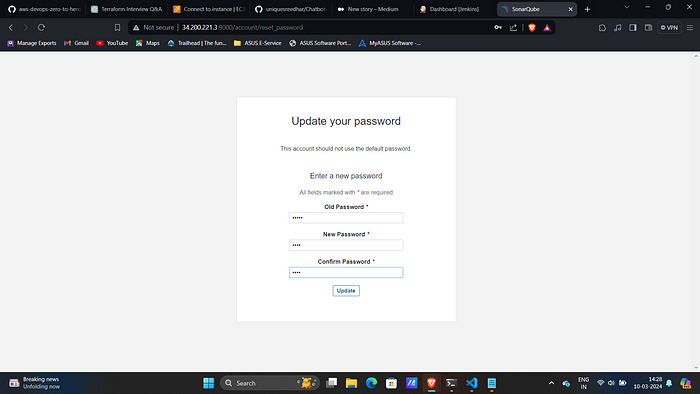
Password: admin7. Customize the password.
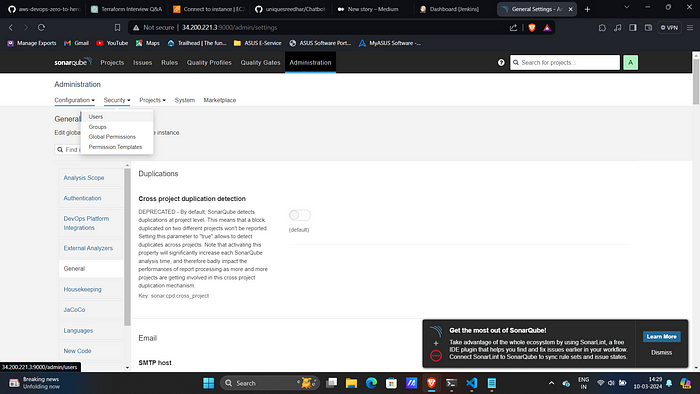
8. Navigate to Security → Users →Administrator.
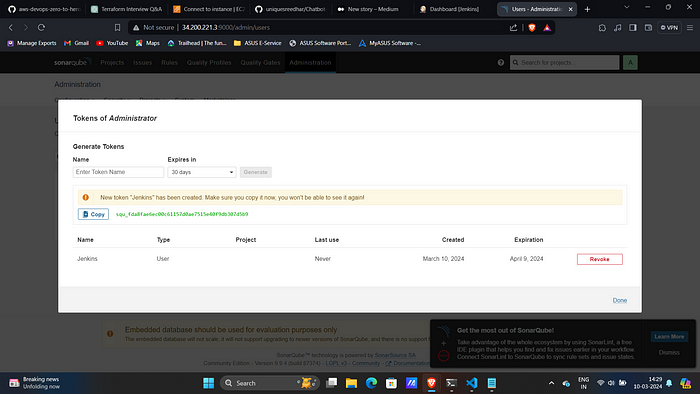
9. Click on Tokens.
10. Create one and save it.
11. Now go to Configuration → Webhooks →Create
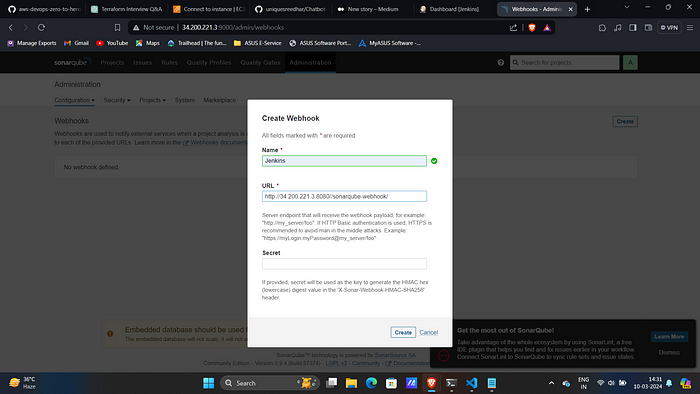
12. Then configure webhook and create.
Name: Jenkins
URL : http://<public_ip>:8080/sonarqube-webhook/13. Now in Jenkins Navigate to Manage Jenkins → Plugins →Available Plugins and install the following.
1 → Eclipse Temurin Installer
2 → SonarQube Scanner
3 → NodeJs Plugin
4 → Docker
5 → Docker commons
6 → Docker pipeline
7 → Docker API
8 → Docker Build step
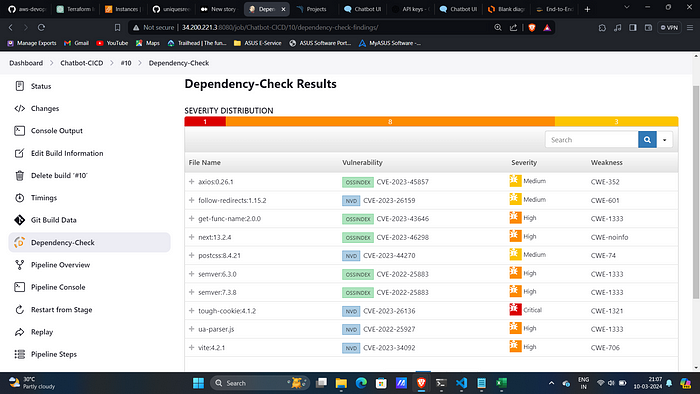
9 → Owasp Dependency Check
10 → Kubernetes
11 → Kubernetes CLI
12 → Kubernetes Client API
13 → Kubernetes Pipeline DevOps steps
10 → AWS Credentials
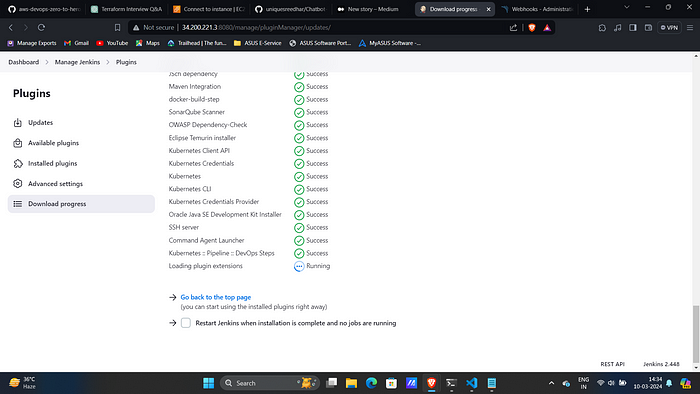
11 → Pipeline: AWS Steps14. Restart Jenkins after they got installed.
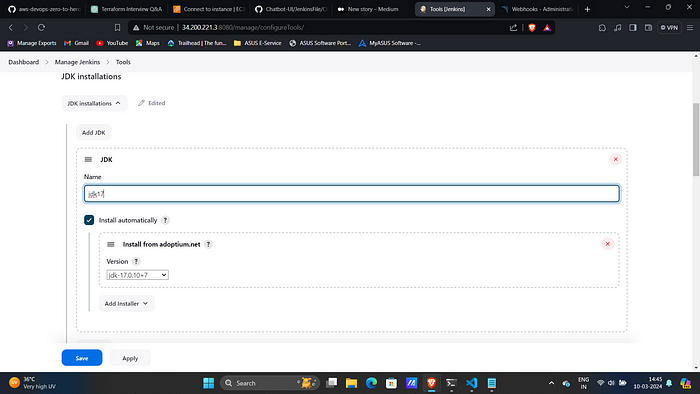
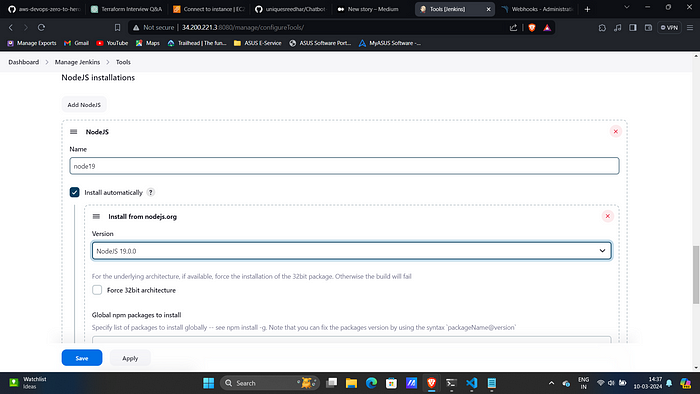
14. Go to Manage Jenkins → Tools → Install JDK(17) and NodeJs(19)→ Click on Apply and Save.
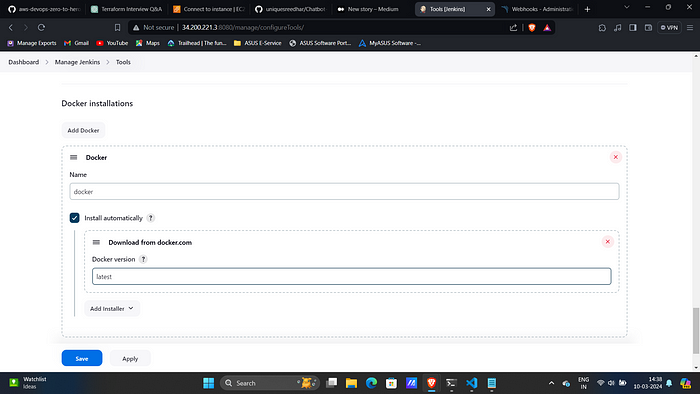
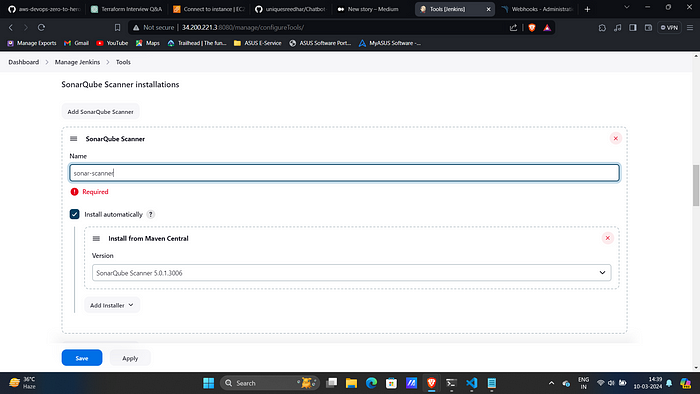
15. Similarly install DP-check, Sonar-Scanner and Docker.
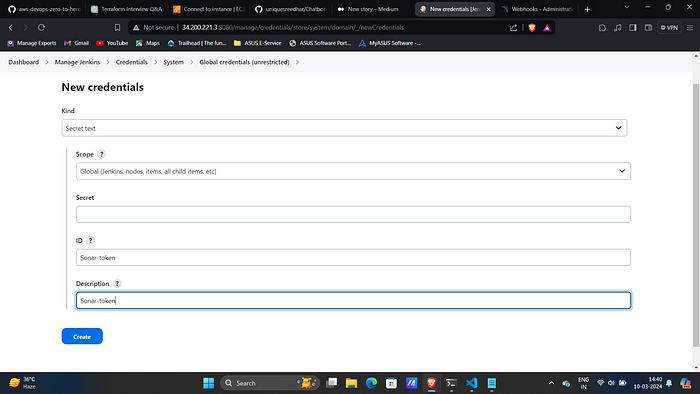
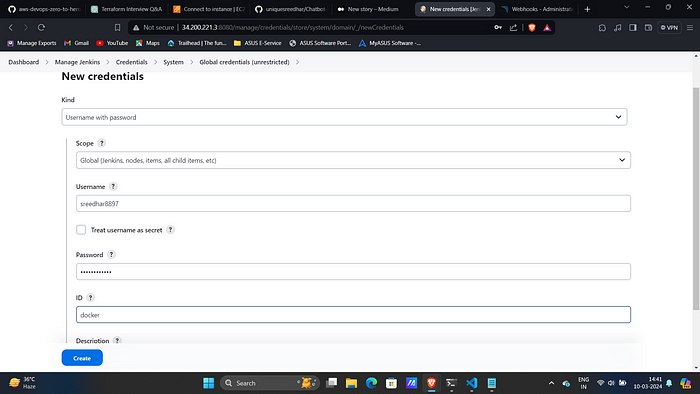
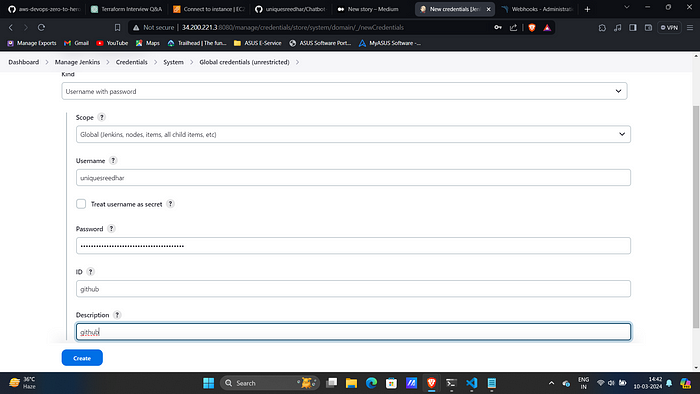
16. Go to Jenkins Dashboard → Manage Jenkins → Credentials. Add
Sonar-token as secret text.
Docker credentials.
GitHub Credentials.
AWS access keys as AWS Credentials.
17. Manage Jenkins → Tools → SonarQube Scanner. Then add sonar-server and created sonar-token.
Step :3 :- Create Jenkins Pipeline
- Up to this Let’s create a pipeline and see if anything gone wrong.
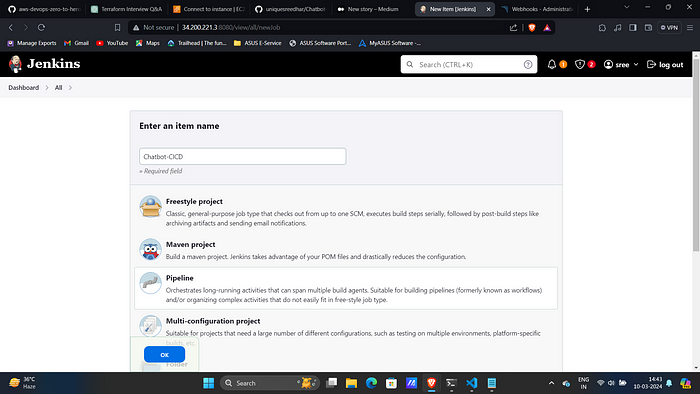
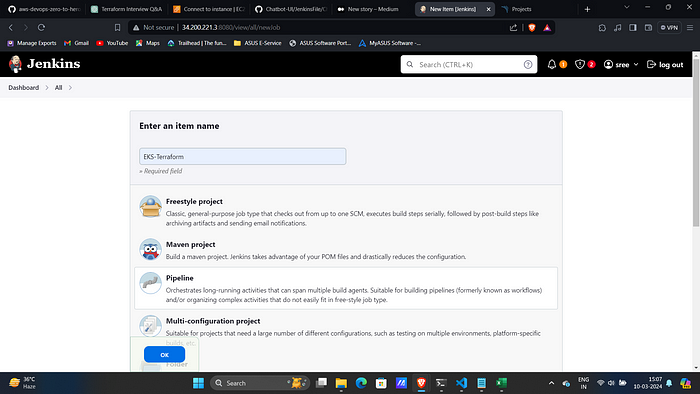
Click on “New Item” and give it a name selecting pipeline and then ok.
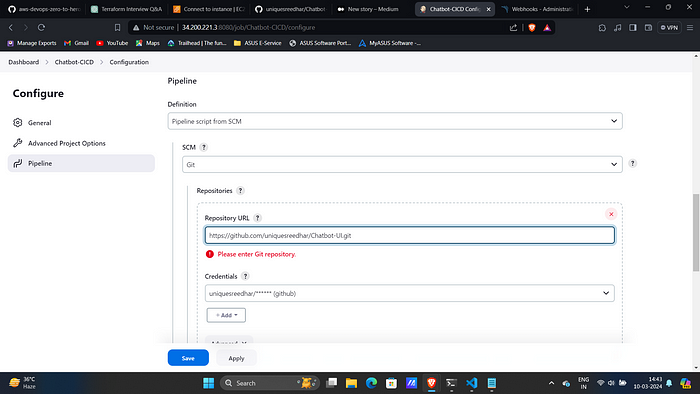
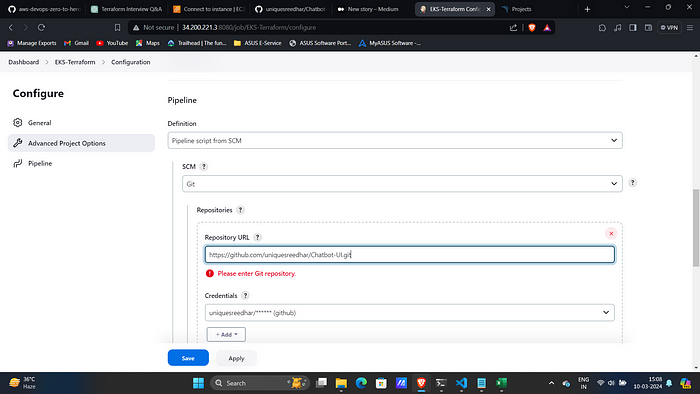
2. Under Pipeline section Provide
Definition: Pipeline script from SCM
SCM : Git
Repo URL : Your Github Repo
Credentials: Created GitHub Credentials
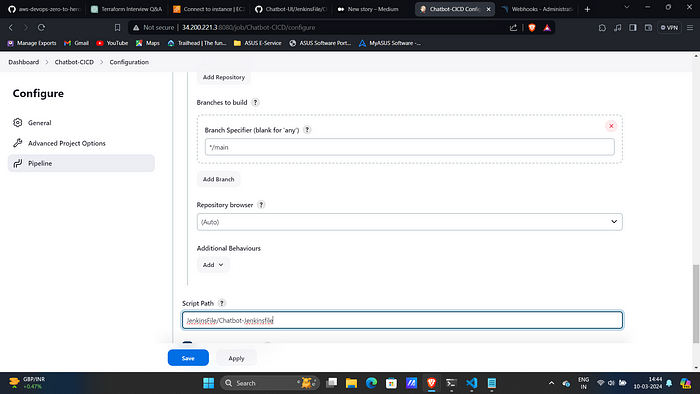
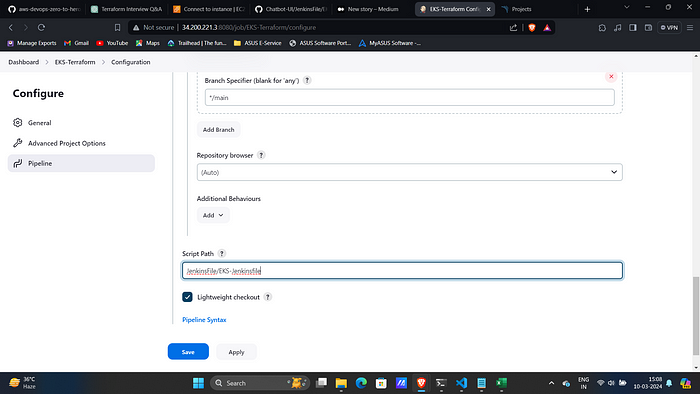
Branch: Main
Path: Your Jenkinsfile path in GitHub repo.3. Click on “Build”.
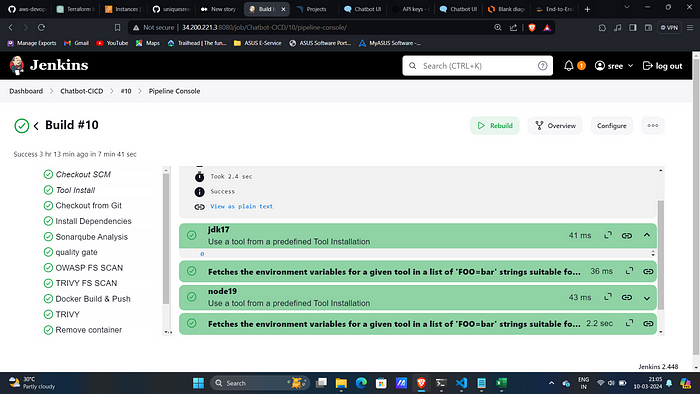
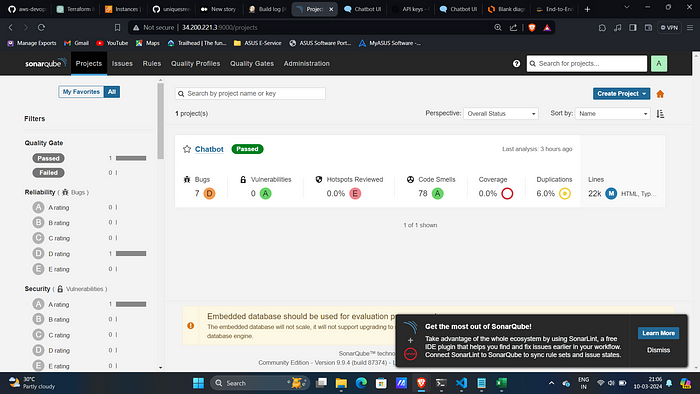
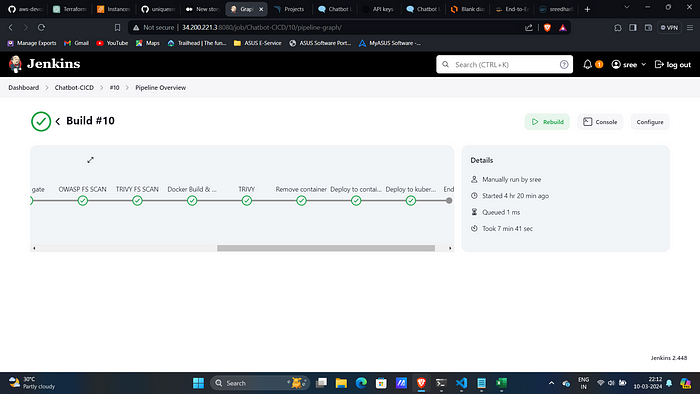
Upon successful execution you can see all stages as green.
Sonar- Console.
Dependency Check:
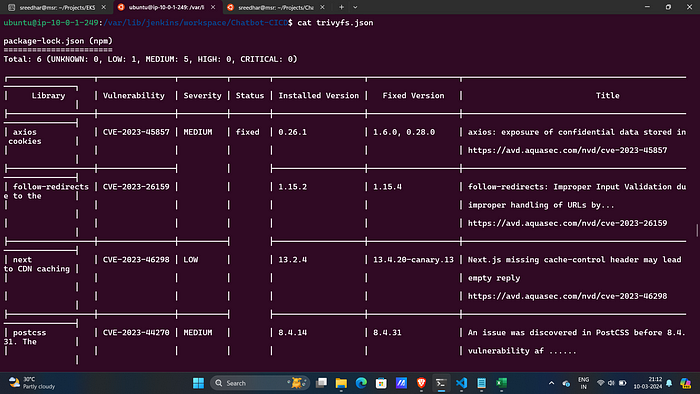
Trivy File scan:
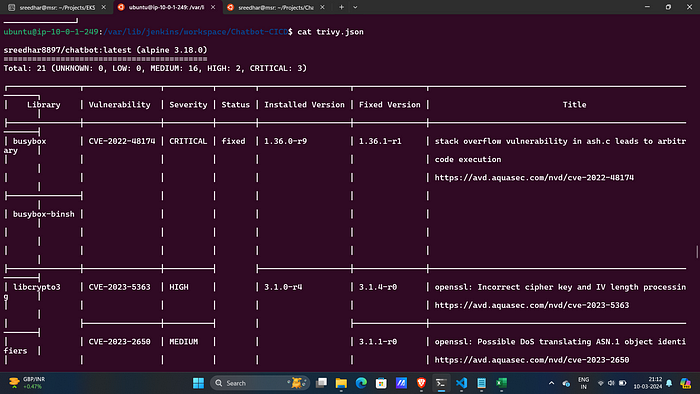
Trivy Image Scan:
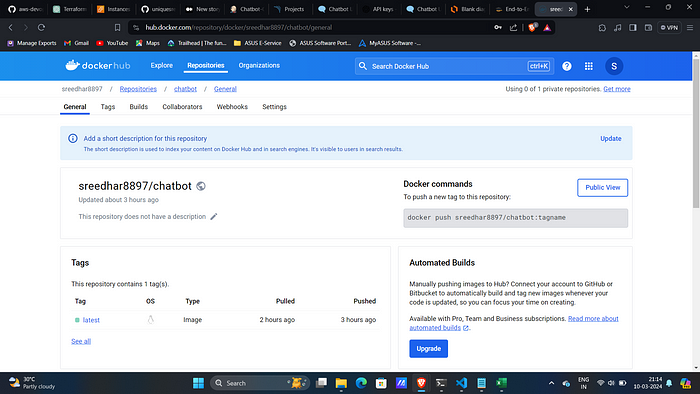
Docker Hub:
4. Now access the application on port 3000 of Jenkins public ip.
Note: Make sure you allowed port 3000 in Security Group of Jenkins Server.
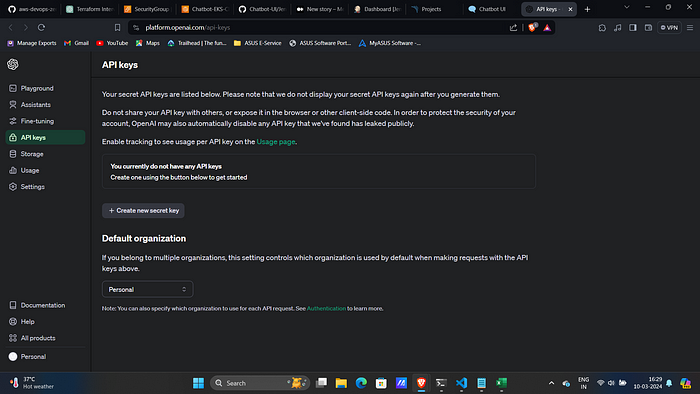
5. Click on openai.com(Blue in color)
This will take you ChatGPT login page enter email and password.
In API Keys Create Click on new secret key.
Give a name and copy it.
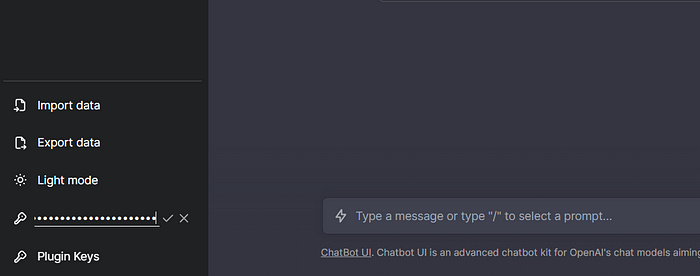
6. Come back to chatbot UI that we deployed and bottom of the page you will see OpenAI API key and give the Generated key and click on save (RIGHT MARK).
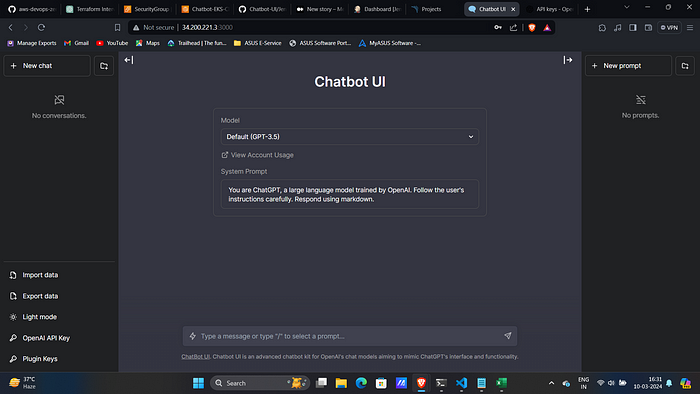
UI look like:
7. Now, You can ask questions and test it.
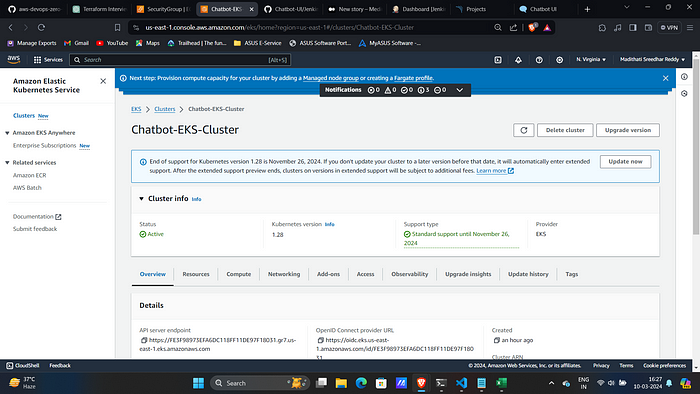
Step:4 :- Create EKS Cluster withy Jenkins
- Click on New item give it a name by choosing pipeline and then click “OK”.
2. Under Pipeline section provide:
Definition: Pipeline script from SCM
SCM : Git
Repo URL : Your Github Repo
Credentials: Created GitHub Credentials
Branch: Main
Path: Your EKS Cluster Jenkinsfile path in GitHub repo.3. Click on Build and on successful execution Your Jenkins UI resembles:
This will create a cluster in AWS:
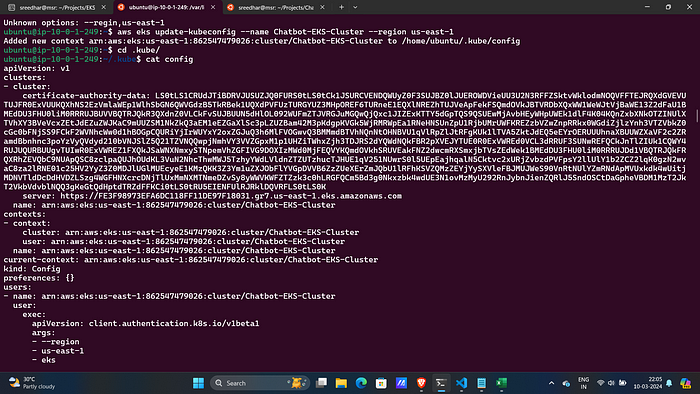
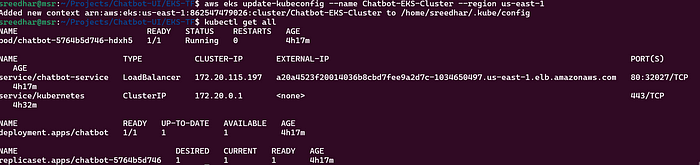
4. Now In the Jenkins server. Give this command to add context.
aws eks update-kubeconfig --name <clustername> --region <region>5. It will Generate an Kubernetes configuration file.
Navigate to the path of config file and copy it.
cd .kube
cat config6. Save it in your local file explorer, at your desired location with any name as text file.
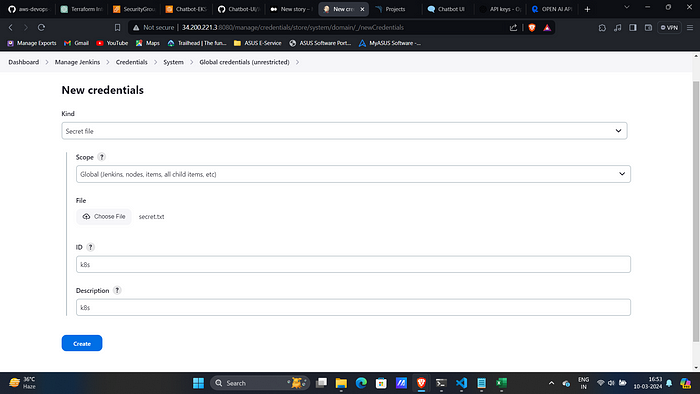
7. Now in Jenkins Console add this file in Credentials section with id k8s as secret file.
Step:5 :- Deployment on EKS
1. Now add this deployment stage in Jenkins file.
stage('Deploy to kubernetes'){
steps{
withAWS(credentials: 'aws-key', region: 'us-east-1'){
script{
withKubeConfig(caCertificate: '', clusterName: '', contextName: '', credentialsId: 'k8s', namespace: '', restrictKubeConfigAccess: false, serverUrl: '') {
sh 'kubectl apply -f k8s/chatbot-ui.yaml'
}
}
}
}
}2. Now rerun the Jenkins Pipeline again.
Upon Success:
This create all the resources in the Cluster:
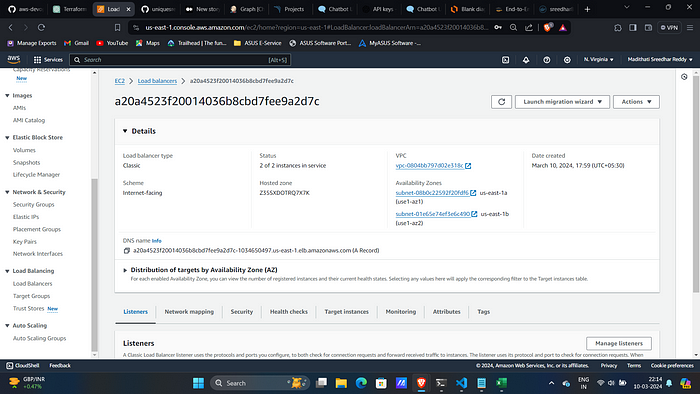
kubectl get allThis will create an Classic Load Balancer on AWS Console:
Copy the DNS Name and Paste it on your browser and use it:
Note: Do the same process and add key to get output.
The Complete Jenkins file:
pipeline{
agent any
tools{
jdk 'jdk17'
nodejs 'node19'
}
environment {
SCANNER_HOME=tool 'sonar-scanner'
}
stages {
stage('Checkout from Git'){
steps{
git branch: 'master', url: 'https://github.com/NotHarshhaa/DevOps-Project-28/Chatbot-UI.git'
}
}
stage('Install Dependencies') {
steps {
sh "npm install"
}
}
stage("Sonarqube Analysis "){
steps{
withSonarQubeEnv('sonar-server') {
sh ''' $SCANNER_HOME/bin/sonar-scanner -Dsonar.projectName=Chatbot \
-Dsonar.projectKey=Chatbot '''
}
}
}
stage("quality gate"){
steps {
script {
waitForQualityGate abortPipeline: false, credentialsId: 'Sonar-token'
}
}
}
stage('OWASP FS SCAN') {
steps {
dependencyCheck additionalArguments: '--scan ./ --disableYarnAudit --disableNodeAudit', odcInstallation: 'DP-Check'
dependencyCheckPublisher pattern: '**/dependency-check-report.xml'
}
}
stage('TRIVY FS SCAN') {
steps {
sh "trivy fs . > trivyfs.json"
}
}
stage("Docker Build & Push"){
steps{
script{
withDockerRegistry(credentialsId: 'docker', toolName: 'docker'){
sh "docker build -t chatbot ."
sh "docker tag chatbot ProDevOpsGuyTech/chatbot:latest "
sh "docker push ProDevOpsGuyTech/chatbot:latest "
}
}
}
}
stage("TRIVY"){
steps{
sh "trivy image ProDevOpsGuyTech/chatbot:latest > trivy.json"
}
}
stage ("Remove container") {
steps{
sh "docker stop chatbot | true"
sh "docker rm chatbot | true"
}
}
stage('Deploy to container'){
steps{
sh 'docker run -d --name chatbot -p 3000:3000 sreedhar8897/chatbot:latest'
}
}
stage('Deploy to kubernetes'){
steps{
withAWS(credentials: 'aws-key', region: 'us-east-1'){
script{
withKubeConfig(caCertificate: '', clusterName: '', contextName: '', credentialsId: 'k8s', namespace: '', restrictKubeConfigAccess: false, serverUrl: '') {
sh 'kubectl apply -f k8s/chatbot-ui.yaml'
}
}
}
}
}
}
}Step: 6 :- Clean Up
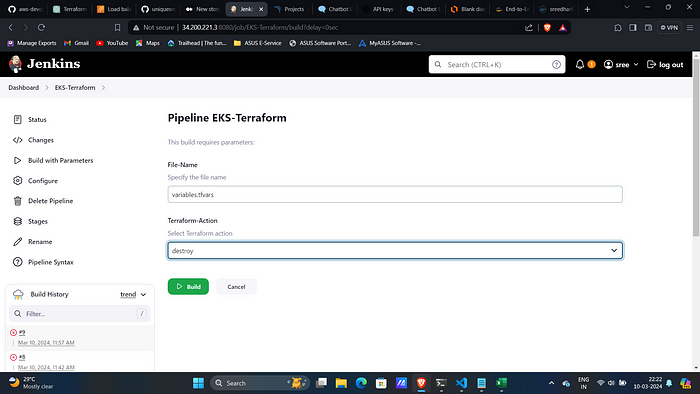
- This is so simple Firstly Delete the EKS Cluster By selecting destroy as the build option.
2. Then destroy Jenkins server by running this on Local:
terraform destroy -auto-approve -var-file=variables.tfvars