- 1. A windows operating system (preferably Win10).
- 2. An external file provider : could be an apache, on a vps or on your personnal machine, if it can distribute you a file just by the ip you have defined, on WAN or LAN (Like X.X.X.X/MyFile) it will work fine.
- 3. A Host who will listen for a TCP connection on a defined port. You can use a metasploit framework handler for example, using "multi/handler" and setting your LPORT to the trojan defined port.
- 4. g++ (and gcc if you want to recompile "Source_Code_Generator.cpp") you can install gcc or g++ with CygWin.
This tool is meant to be used only for benevolent purposes.
I am in no way responsible for your actions and the use you can make of that tool.
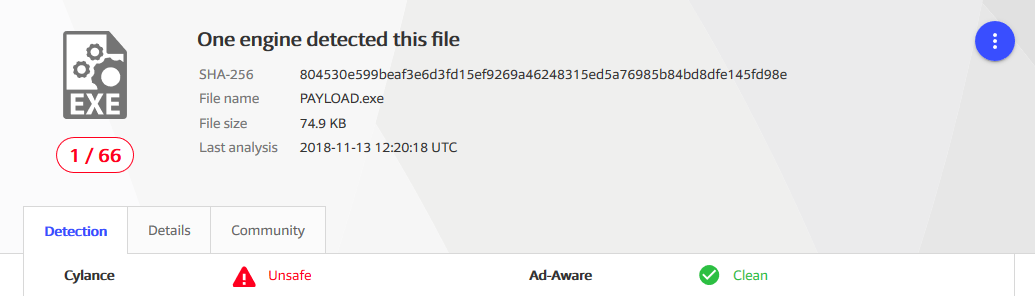
This tool let you create a fully obfuscated trojan horse. This trojan will :
- Create a directory on the "Victim".
- Download 2 files (FileA and FileB) from the File provider you have specified into the created dir.
- Run FileA who will run FileB.
- FileB will send by TCP a SHELL from the victim to your specified host IP and PORT.
- You can create a planified task who will run FileA.
- 1. Define the path and the name of the created dir (ex: C:/test)
- 2. Define the ip of your file provider (ex : X.X.X.X:85/Files)
- 3. Define the name of the two files who will be downloaded (ex: FileA,FileB)
- 4. Define the host ip and port who will receive the connection (ex : X.X.X.X and 4499)
- 5. The exe will be created !