-
Notifications
You must be signed in to change notification settings - Fork 34
sPMP implementation
IPADS edited this page Dec 31, 2019
·
2 revisions
-
cpu_bits.h
- csr_spmpcfg0
3 **0x1a00x1a3** - csr_spmpaddr0
15 **0x1b00x1bf** - csr_spmpexcp 0x145
- csr_spmpcfg0
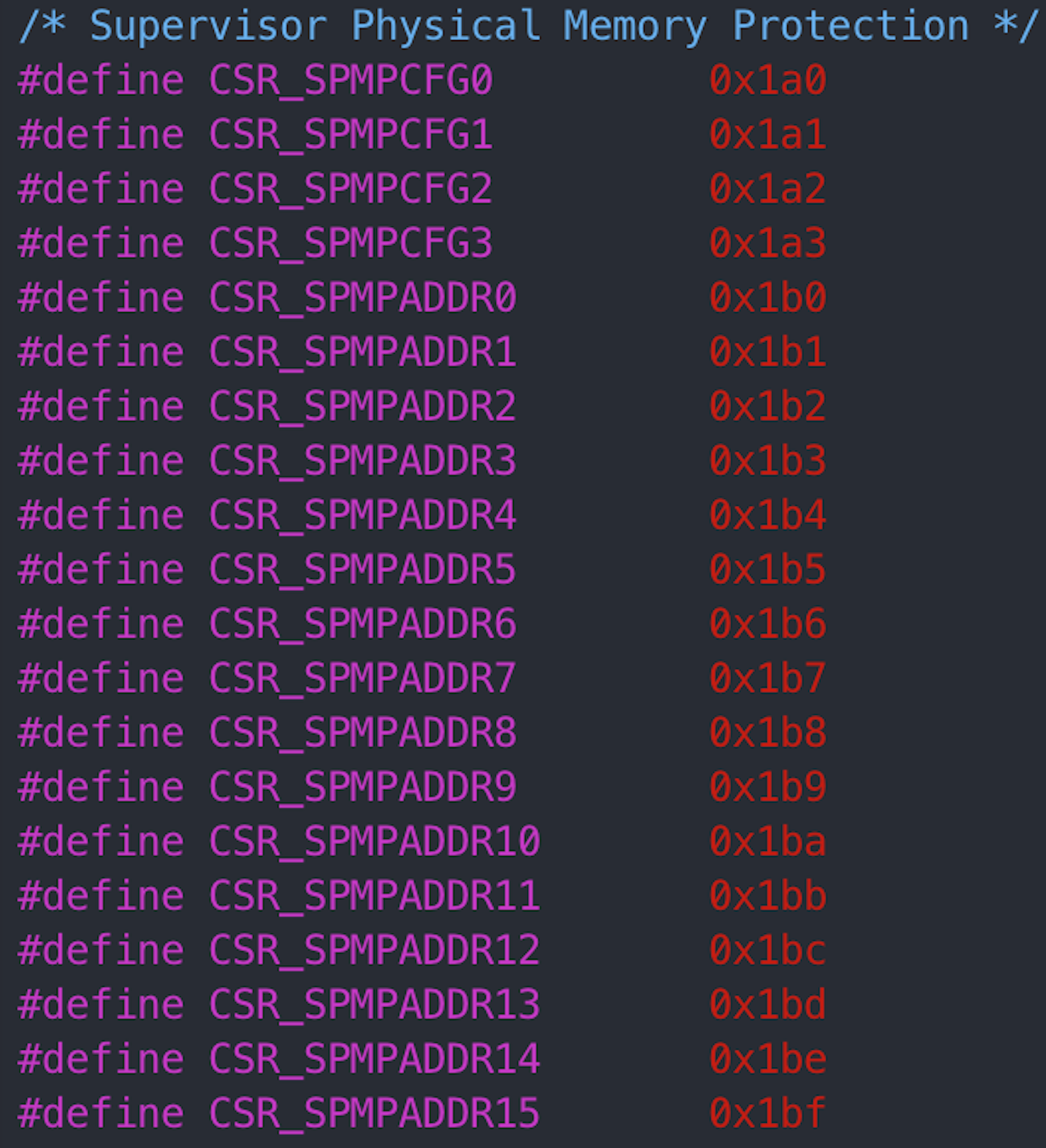
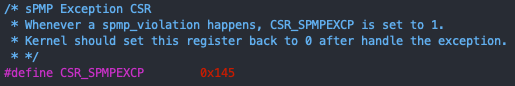
-
cpu.h
- MAX_RISCV_SPMPS
- spmp_state
-
pmp.h
- date structures for spmp_table_t

-
cpu.h
- add RISCV_FEATURE_SPMP
- add cpu->cfg.spmp
-
cpu.c
- set_feature(env, RISCV_FEATURE_SPMP)
- set cpu -> cfg.spmp
- add riscv_cpu_properties -> spmp
-
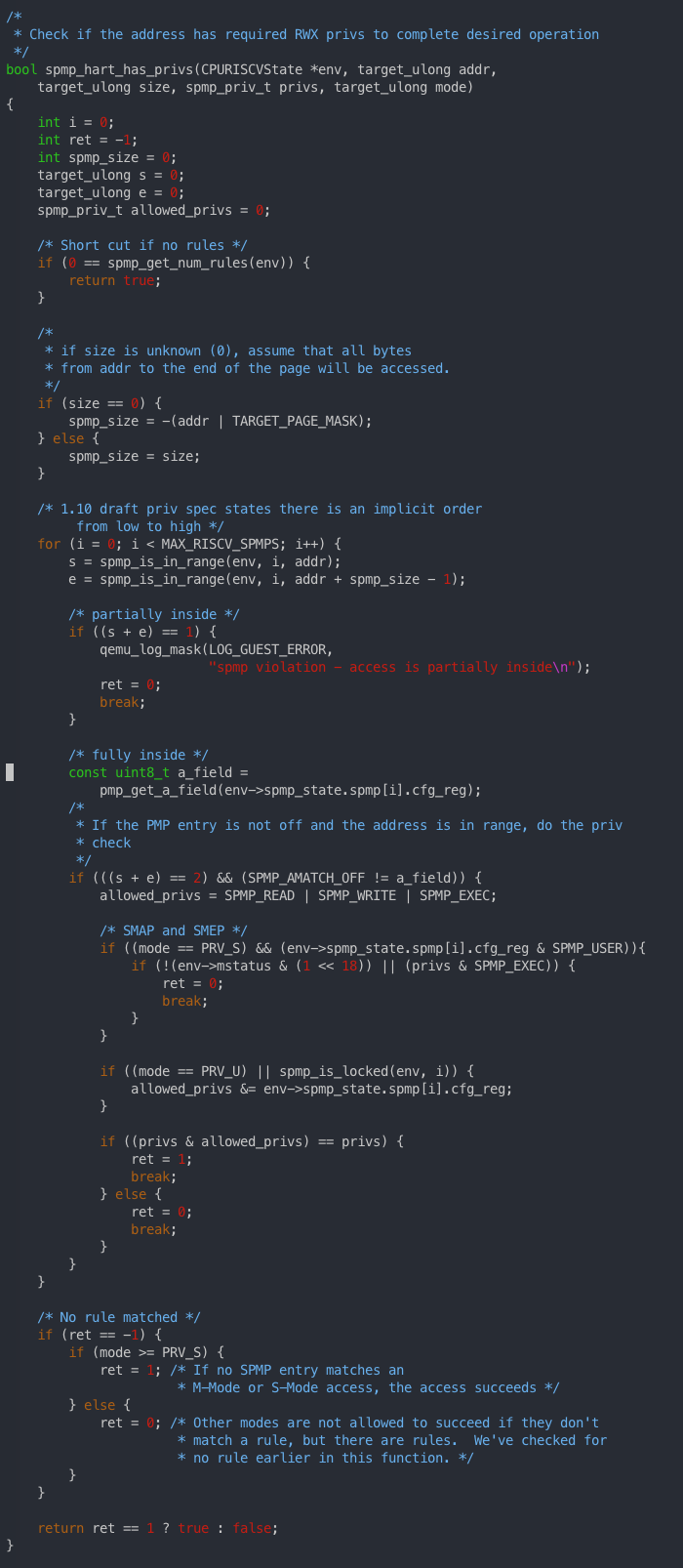
cpu_helper.c
- check riscv_feature && spmp_hart_has_privs
- get physical addr
- tlb fill
- add spmp_violation
- check riscv_feature && spmp_hart_has_privs


-
csr.c
- csr function table
- define spmp_csr access priv to spmp
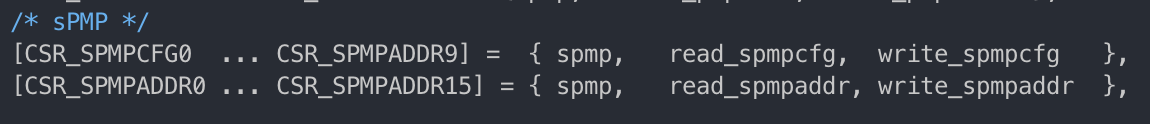

-
csr.c
-
read\write_spmp_cfg
-
read\write_spmp_addr
-
pmp.c
- Everything except pmp_get_a_field and pmp_decode_napot
-
sPMP read/write
- set region0
- cfg0 = 0b00001111 -> 0x0f
- spmpaddr0 = 0x22000000
- try to read the spmpcfg and spmpaddr
- set region0
-
sPMP L-bit test
-
test write ignore
- cfg0 = 0b10011101 -> 0x9d
- spmpaddr = 0x208ccdff
- re-write spmpcfg and spmpaddr
- write should be ignored
-
test access without proper permission
- cfg0 = 0b11011101 -> 0xdd
- access paddr = 0x82333000
- kernel should panic
-
-
SMAP
- access region0 with U-bit set
- cfg0 = 0b01011111 -> 0x5f
- spmpaddr0 = 0x208ccdff
- set SUM in sstatus to 1
- access 0x82333000 in region0 shall succeed
- set SUM in sstatus to 0
- attempt to access 0x82333000 in region0
- kernel should panic
- access region0 with U-bit set
-
SMEP
- excute code in region0 with U-bit set
- inject code in paddr 0x82333000
- 0xe900893 (li a7, 233)
- little-endian -> 0x9308900e
- cfg0 = 0b01011111 -> 0x5f
- spmpaddr0 = 0x208ccdff
- attempt to execute code at 0x82333000
- kernel should panic
- inject code in paddr 0x82333000
- excute code in region0 with U-bit set