Quickly bootstrap an ERC20 token airdrop to a Merkle tree of recipients.
Steps:
- Generate Merkle tree of recipients by following README in generator/
- Setup and deploy MerkleClaimERC20 contracts by following README in contracts/
- Setup and deploy front-end by following README in frontend/
- Astrodrop—Simpler way to spin up a airdrop with claim page, given existing token
- Uniswap Merkle Distributor—Uniswap's merkle distribution smart contracts
These smart contracts are being provided as is. No guarantee, representation or warranty is being made, express or implied, as to the safety or correctness of the user interface or the smart contracts. They have not been audited and as such there can be no assurance they will work as intended, and users may experience delays, failures, errors, omissions or loss of transmitted information. Anish Agnihotri is not liable for any of the foregoing. Users should proceed with caution and use at their own risk.
A function that maps a bit string of arbitrary length to a fixed-length bit string. Depending upon the relying application, the security strength that can be supported by a hash function is typically measured by the extent to which it possesses one or more of the following properties
-
(Collision resistance) It is computationally infeasible to find any two distinct inputs that map to the same output.
-
(Preimage resistance) Given a randomly chosen target output, it is computationally infeasible to find any input that maps to that output. (This property is called the one-way property.)
-
(Second preimage resistance) Given one input value, it is computationally infeasible to find a second (distinct) input value that maps to the same output as the first value.
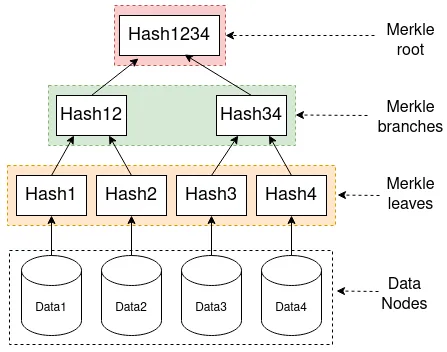
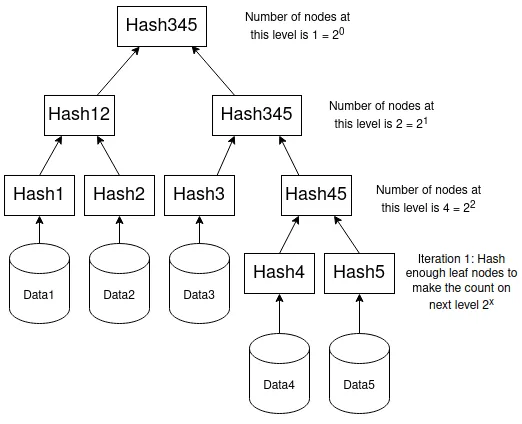
A Merkle tree is fundamentally just a hierarchical set of hash values, building from a set of actual data (Merkle leaf) to intermediate hashes (Merkle braches) and up to the Merkle root that summarizes all the data in one hash value.
In this figure, the bottom nodes (Data1-Data4) are the actual data processed by the application. Each of these is summarized by their respective hash value (Hash1-Hash4), as a Merkle leaf. From these, the Merkle tree builds a hierarchy, combining hashes together until only one is left. The nodes combining other hash nodes are called Merkle branches (here Hash12 and Hash34). When there is only one left (here Hash1234), this is called the Merkle root. There can be multiple levels of branches and hashing as following examples will demonstrate.
- AWS DynamoDB distributed database
- ZFS filesystem
- Git version control system
- Transaction Data (Block) Immutability
- Blockchain pruning
- Simplified Payment Verification (SPV)
- Pool Mining: The Stratum Protocol
- Airdrop