diff --git a/.gitignore b/.gitignore
index 09fcc1ee..7a767137 100644
--- a/.gitignore
+++ b/.gitignore
@@ -113,3 +113,6 @@ local.properties
# VS Code
.vscode
+
+# Document
+doc
diff --git a/.travis.yml b/.travis.yml
index 04bd608f..3f613680 100644
--- a/.travis.yml
+++ b/.travis.yml
@@ -5,6 +5,7 @@ cache:
apt: true
os: linux
+dist: trusty
addons:
apt:
@@ -86,6 +87,17 @@ matrix:
env:
- COMPILERS="CC=gcc-7 CXX=g++-7"
- COMPILE=main
+ - name: g++-7 daemon DISABLE x86 64bit elliptic curve
+ addons:
+ apt:
+ sources:
+ - ubuntu-toolchain-r-test
+ packages:
+ - g++-7
+ env:
+ - COMPILERS="CC=gcc-7 CXX=g++-7"
+ - DEF_CMAKE_OPTIONS="CMAKE_OPTIONS=-DUSE_EC_64=OFF"
+ - COMPILE=main
- name: g++-7 test
addons:
apt:
@@ -176,6 +188,7 @@ install:
sudo apt-get install -y libldns-dev;
sudo apt-get install -y libgtest-dev;
sudo apt-get install -y libunwind8-dev;
+ sudo apt-get install -y nasm;
fi
# clang 5.0 ships libunwind in own lib folder
- if [ "$CC" == "clang-5.0" ] ; then
@@ -184,14 +197,15 @@ install:
script:
- eval "${COMPILERS}"
+ - eval "${DEF_CMAKE_OPTIONS}"
- cd $HOME
- |
if [ "$COMPILE" == "main" ] ; then
- mkdir linux-x64-build
- cd linux-x64-build
- cmake -DCMAKE_INSTALL_PREFIX=$HOME/ryo-linux-x64-release -DARCH="x86-64" -DBUILD_64=ON -DCMAKE_BUILD_TYPE=Debug -DBUILD_TAG="linux-x64-release" $TRAVIS_BUILD_DIR
- make -j "$NUMBER_OF_CPUS"
- make install
+ mkdir linux-x64-build &&
+ cd linux-x64-build &&
+ cmake -DCMAKE_INSTALL_PREFIX=$HOME/ryo-linux-x64-release -DARCH="x86-64" -DBUILD_64=ON -DCMAKE_BUILD_TYPE=Debug -DBUILD_TAG="linux-x64-release" $CMAKE_OPTIONS $TRAVIS_BUILD_DIR &&
+ make -j "$NUMBER_OF_CPUS" &&
+ make install &&
cd bin
# runtime tests are currently disabled because the help is exiting with error code 1
#for prog in $(find . -type f -executable)
@@ -201,14 +215,14 @@ script:
#done
elif [ "$COMPILE" == "tests" ] ; then
# compile tests
- cd $HOME
- mkdir linux-x64-tests-build
- cd linux-x64-tests-build
- cmake -DBUILD_TESTS=ON -DCMAKE_BUILD_TYPE=Debug $TRAVIS_BUILD_DIR
+ cd $HOME &&
+ mkdir linux-x64-tests-build &&
+ cd linux-x64-tests-build &&
+ cmake -DBUILD_TESTS=ON -DCMAKE_BUILD_TYPE=Debug $CMAKE_OPTIONS $TRAVIS_BUILD_DIR &&
# build all tests
- make -j "$NUMBER_OF_CPUS"
+ make -j "$NUMBER_OF_CPUS" &&
# run unit tests
- cd tests
+ cd tests &&
ctest -V
else
echo "not supported compile option '$COMPILE'"
diff --git a/CMakeLists.txt b/CMakeLists.txt
index 97bf2d1d..4f60f93b 100644
--- a/CMakeLists.txt
+++ b/CMakeLists.txt
@@ -1,4 +1,4 @@
-# Copyright (c) 2018, Ryo Currency Project
+# Copyright (c) 2019, Ryo Currency Project
# Copyright (c) 2014-2018, The Monero Project
#
# All rights reserved.
@@ -29,7 +29,7 @@
# Authors and copyright holders agree that:
#
# 8. This licence expires and the work covered by it is released into the
-# public domain on 1st of February 2019
+# public domain on 1st of February 2020
#
# THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY
# EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
@@ -58,6 +58,65 @@ cmake_minimum_required(VERSION 3.1.0)
project(ryo)
+# enforce C++11
+set(CMAKE_CXX_STANDARD_REQUIRED ON)
+set(CMAKE_CXX_EXTENSIONS OFF)
+set(CMAKE_CXX_STANDARD 11)
+
+# enforce C11
+set(CMAKE_C_STANDARD_REQUIRED ON)
+set(CMAKE_C_EXTENSIONS OFF)
+set(CMAKE_C_STANDARD 11)
+
+# helper function to generate options
+function(ryo_option name description default)
+ set(USE_${name} ${default} CACHE STRING "${description}")
+ set_property(CACHE USE_${name} PROPERTY
+ STRINGS "ON;TRUE;AUTO;OFF;FALSE")
+ if(HAVE_${name})
+ set(HAVE_${name} TRUE PARENT_SCOPE)
+ else()
+ set(HAVE_${name} PARENT_SCOPE)
+ endif()
+endfunction()
+
+# detect 64bit x86 architecture and set ARCH_X86_64
+if (CMAKE_SYSTEM_PROCESSOR STREQUAL "x86_64")
+ set(ARCH_X86_64 TRUE)
+elseif (CMAKE_SYSTEM_PROCESSOR STREQUAL "amd64")
+ set(ARCH_X86_64 TRUE)
+elseif (CMAKE_SYSTEM_PROCESSOR STREQUAL "AMD64")
+ # cmake reports AMD64 on Windows, but we might be building for 32-bit.
+ if (CMAKE_CL_64)
+ set(ARCH_X86_64 TRUE)
+ endif()
+endif()
+
+################################################################################
+### ELLIPTIC CURVE
+ryo_option(EC_64 "use optimized x86 64bit elliptic curve implementation" AUTO)
+# check if x86_64 elliptic curve implementation can be used
+if(USE_EC_64 STREQUAL AUTO)
+ enable_language(ASM_NASM OPTIONAL)
+ if(ARCH_X86_64 AND CMAKE_ASM_NASM_COMPILER)
+ set(HAVE_EC_64 TRUE)
+ endif()
+elseif(USE_EC_64)
+ enable_language(ASM_NASM)
+ if(NOT CMAKE_ASM_NASM_COMPILER_LOADED)
+ message(FATAL_ERROR "Could not load NASM compiler.")
+ endif()
+ set(HAVE_EC_64 TRUE)
+endif()
+
+if(HAVE_EC_64)
+ message(STATUS "Using 64bit elliptic curve implementation for x68_64")
+ add_definitions("-DHAVE_EC_64")
+endif()
+
+### ELLIPTIC CURVE
+################################################################################
+
function (die msg)
if (NOT WIN32)
string(ASCII 27 Esc)
@@ -248,7 +307,7 @@ endif()
# elseif(CMAKE_SYSTEM_NAME MATCHES ".*BSDI.*")
# set(BSDI TRUE)
-include_directories(external/rapidjson/include external/easylogging++ src contrib/epee/include external)
+include_directories(external/rapidjson/include src contrib/epee/include external)
if(APPLE)
include_directories(SYSTEM /usr/include/malloc)
@@ -369,10 +428,6 @@ add_definitions("-DBLOCKCHAIN_DB=${BLOCKCHAIN_DB}")
if (APPLE)
set(DEFAULT_STACK_TRACE OFF)
set(LIBUNWIND_LIBRARIES "")
-elseif(CMAKE_C_COMPILER_ID STREQUAL "GNU" AND NOT MINGW)
- set(DEFAULT_STACK_TRACE ON)
- set(STACK_TRACE_LIB "easylogging++") # for diag output only
- set(LIBUNWIND_LIBRARIES "")
elseif (ARM AND STATIC)
set(DEFAULT_STACK_TRACE OFF)
set(LIBUNWIND_LIBRARIES "")
@@ -430,8 +485,6 @@ add_definition_if_library_exists(c memset_s "string.h" HAVE_MEMSET_S)
add_definition_if_library_exists(c explicit_bzero "strings.h" HAVE_EXPLICIT_BZERO)
add_definition_if_function_found(strptime HAVE_STRPTIME)
-add_definitions(-DAUTO_INITIALIZE_EASYLOGGINGPP)
-
# Generate header for embedded translations
include(ExternalProject)
ExternalProject_Add(generate_translations_header
@@ -446,10 +499,6 @@ add_subdirectory(external)
include_directories(${UNBOUND_INCLUDE})
link_directories(${UNBOUND_LIBRARY_DIRS})
-# Final setup for easylogging++
-include_directories(${EASYLOGGING_INCLUDE})
-link_directories(${EASYLOGGING_LIBRARY_DIRS})
-
# Final setup for liblmdb
include_directories(${LMDB_INCLUDE})
@@ -621,8 +670,8 @@ else()
message(STATUS "AES support disabled")
endif()
- set(CMAKE_C_FLAGS "${CMAKE_C_FLAGS} -std=c11 -D_GNU_SOURCE ${MINGW_FLAG} ${STATIC_ASSERT_FLAG} ${WARNINGS} ${C_WARNINGS} ${ARCH_FLAG} ${COVERAGE_FLAGS} ${PIC_FLAG} ${C_SECURITY_FLAGS}")
- set(CMAKE_CXX_FLAGS "${CMAKE_CXX_FLAGS} -std=c++11 -D_GNU_SOURCE ${MINGW_FLAG} ${STATIC_ASSERT_CPP_FLAG} ${WARNINGS} ${CXX_WARNINGS} ${ARCH_FLAG} ${COVERAGE_FLAGS} ${PIC_FLAG} ${CXX_SECURITY_FLAGS}")
+ set(CMAKE_C_FLAGS "${CMAKE_C_FLAGS} -D_GNU_SOURCE ${MINGW_FLAG} ${STATIC_ASSERT_FLAG} ${WARNINGS} ${C_WARNINGS} ${ARCH_FLAG} ${COVERAGE_FLAGS} ${PIC_FLAG} ${C_SECURITY_FLAGS}")
+ set(CMAKE_CXX_FLAGS "${CMAKE_CXX_FLAGS} -D_GNU_SOURCE ${MINGW_FLAG} ${STATIC_ASSERT_CPP_FLAG} ${WARNINGS} ${CXX_WARNINGS} ${ARCH_FLAG} ${COVERAGE_FLAGS} ${PIC_FLAG} ${CXX_SECURITY_FLAGS}")
set(CMAKE_EXE_LINKER_FLAGS "${CMAKE_EXE_LINKER_FLAGS} ${LD_SECURITY_FLAGS}")
# With GCC 6.1.1 the compiled binary malfunctions due to aliasing. Until that
@@ -786,6 +835,11 @@ if (${BOOST_IGNORE_SYSTEM_PATHS} STREQUAL "ON")
endif()
set(OLD_LIB_SUFFIXES ${CMAKE_FIND_LIBRARY_SUFFIXES})
+
+if(MINGW)
+ set(Boost_NO_BOOST_CMAKE ON)
+endif()
+
if(STATIC)
if(MINGW)
set(CMAKE_FIND_LIBRARY_SUFFIXES .a)
@@ -801,7 +855,7 @@ if(NOT Boost_FOUND)
die("Could not find Boost libraries, please make sure you have installed Boost or libboost-all-dev (1.58) or the equivalent")
elseif(Boost_FOUND)
message(STATUS "Found Boost Version: ${Boost_VERSION}")
- if (Boost_VERSION VERSION_LESS 106200 AND NOT (OPENSSL_VERSION VERSION_LESS 1.1))
+ if (Boost_VERSION VERSION_LESS 1.62.0 AND NOT (OPENSSL_VERSION VERSION_LESS 1.1))
message(FATAL_ERROR "Boost older than 1.62 is too old to link with OpenSSL 1.1 or newer. "
"Update Boost or install OpenSSL 1.0 and set path to it when running cmake: "
"cmake -DOPENSSL_ROOT_DIR='/usr/include/openssl-1.0;/usr/lib/openssl-1.0'")
diff --git a/Doxyfile b/Doxyfile
index f622c618..51d5d223 100644
--- a/Doxyfile
+++ b/Doxyfile
@@ -32,7 +32,7 @@ DOXYFILE_ENCODING = UTF-8
# title of most generated pages and in a few other places.
# The default value is: My Project.
-PROJECT_NAME = "Monero"
+PROJECT_NAME = "Ryo"
# The PROJECT_NUMBER tag can be used to enter a project or revision number. This
# could be handy for archiving the generated documentation or if some version
diff --git a/LICENSE b/LICENSE
index 344aa641..8a208b4f 100644
--- a/LICENSE
+++ b/LICENSE
@@ -1,4 +1,4 @@
-Copyright (c) 2018, Ryo Currency Project
+Copyright (c) 2019, Ryo Currency Project
Portions of this software are available under BSD-3 license. Please see ORIGINAL-LICENSE for details
@@ -30,7 +30,7 @@ As long as the following conditions are met:
Authors and copyright holders agree that:
8. This licence expires and the work covered by it is released into the
- public domain on 1st of February 2019
+ public domain on 1st of February 2020
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
diff --git a/README.md b/README.md
index 432e4efb..919ee5fd 100644
--- a/README.md
+++ b/README.md
@@ -1,592 +1,113 @@
-# Ryo
+[ ](https://ryo-currency.com/ryo-serious-competitor-to-monero)
-Copyright (c) 2018, Ryo Currency Project
-
-Copyright (c) 2014-2017, The Monero Project
-
-Copyright (c) 2012-2013, The Cryptonote developers
-
-Copyright (c) 2017, Sumokoin.org
-
-
-## Development Resources
-
-- Web: [ryo-currency.com](https://ryo-currency.com)
+Ryo is one of very few cryptonote currencies that does actual, rapid development. Its team is led by fireice_uk, mosu_forge and psychocrypt who are the developers of [Cryptonight-GPU](https://medium.com/@crypto_ryo/cryptonight-gpu-fpga-proof-pow-algorithm-based-on-floating-point-instructions-92524debf8e8) and [Cryptonight-Heavy](https://github.com/ryo-currency/ryo-writeups/blob/master/cn-heavy.md) mining algorithms, GUI Wallet with built-in GPU solo mining feature called [Ryo Wallet Atom](https://ryo-currency.com/atom) and [Xmr-Stak](https://github.com/fireice-uk/xmr-stak/releases) miner.
+- Website: [ryo-currency.com](https://ryo-currency.com)
- Mail: [contact@ryo-currency.com](mailto:contact@ryo-currency.com)
-Please note that code is developed on the [dev branch](https://github.com/ryo-currency/ryo-currency/tree/dev), if you want to check out the latest updates, before they are merged on main branch, please refer there. Master branch will always point to a version that we consider stable, so you can download the code by simply typing `git clone https://github.com/ryo-currency/ryo-currency.git`
+## Contents
+| | |
+| --- | --- |
+| 1. [Introduction](#introduction) | 7. [Community](#community) |
+| 2. [Check Development and get release binaries](#check-development-and-get-release-binaries) | 8. [Compiling Ryo from source](doc/compiling.md) |
+| 3. [Project Roadmap](#project-roadmap) | 9. [Debugging](doc/debugging.md) |
+| 4. [Features](#features) | 10. [LMDB](doc/lmdb.md) |
+| 5. [Research and contributing](#research-and-contributing) | 11. [Using Ryo with TOR and Readline](doc/tor_readline.md) |
+| 6. [Coin Supply & Emission](#coin-supply--emission) | 12. [Licensing details](#licensing-details) |
+
## Introduction
+Ryo (両 in Japanese: one syllable) is the most **secure, private and untraceable cryptocurrency out there**. Ryo originated from the [_Tael_](https://en.wikipedia.org/wiki/Ry%C5%8D), an ancient Far East unit of weight standard used for exchanging gold and silver. Based on the foundations of Monero, Ryo emerged and is poised to dominate the privacy conscious crypto scene. Ryo is a fork of Sumokoin. You can read all fork-related information [here](doc/sumokoin.md).
-Ryo (両 in Japanese: one syllable) is the most **secure, private and untraceable cryptocurrency out there**. Ryo originated from the _Tael_, an ancient Far East unit of weight standard used for exchanging gold and silver. Based on the foundations of Monero, Ryo emerged and is poised to dominate the privacy conscious crypto scene. Backed by a full featured and balanced development team headed by the legendary fireice_uk and psychocrypt.
+## Check Development and get release binaries
+[
](https://ryo-currency.com/ryo-serious-competitor-to-monero)
-Copyright (c) 2018, Ryo Currency Project
-
-Copyright (c) 2014-2017, The Monero Project
-
-Copyright (c) 2012-2013, The Cryptonote developers
-
-Copyright (c) 2017, Sumokoin.org
-
-
-## Development Resources
-
-- Web: [ryo-currency.com](https://ryo-currency.com)
+Ryo is one of very few cryptonote currencies that does actual, rapid development. Its team is led by fireice_uk, mosu_forge and psychocrypt who are the developers of [Cryptonight-GPU](https://medium.com/@crypto_ryo/cryptonight-gpu-fpga-proof-pow-algorithm-based-on-floating-point-instructions-92524debf8e8) and [Cryptonight-Heavy](https://github.com/ryo-currency/ryo-writeups/blob/master/cn-heavy.md) mining algorithms, GUI Wallet with built-in GPU solo mining feature called [Ryo Wallet Atom](https://ryo-currency.com/atom) and [Xmr-Stak](https://github.com/fireice-uk/xmr-stak/releases) miner.
+- Website: [ryo-currency.com](https://ryo-currency.com)
- Mail: [contact@ryo-currency.com](mailto:contact@ryo-currency.com)
-Please note that code is developed on the [dev branch](https://github.com/ryo-currency/ryo-currency/tree/dev), if you want to check out the latest updates, before they are merged on main branch, please refer there. Master branch will always point to a version that we consider stable, so you can download the code by simply typing `git clone https://github.com/ryo-currency/ryo-currency.git`
+## Contents
+| | |
+| --- | --- |
+| 1. [Introduction](#introduction) | 7. [Community](#community) |
+| 2. [Check Development and get release binaries](#check-development-and-get-release-binaries) | 8. [Compiling Ryo from source](doc/compiling.md) |
+| 3. [Project Roadmap](#project-roadmap) | 9. [Debugging](doc/debugging.md) |
+| 4. [Features](#features) | 10. [LMDB](doc/lmdb.md) |
+| 5. [Research and contributing](#research-and-contributing) | 11. [Using Ryo with TOR and Readline](doc/tor_readline.md) |
+| 6. [Coin Supply & Emission](#coin-supply--emission) | 12. [Licensing details](#licensing-details) |
+
## Introduction
+Ryo (両 in Japanese: one syllable) is the most **secure, private and untraceable cryptocurrency out there**. Ryo originated from the [_Tael_](https://en.wikipedia.org/wiki/Ry%C5%8D), an ancient Far East unit of weight standard used for exchanging gold and silver. Based on the foundations of Monero, Ryo emerged and is poised to dominate the privacy conscious crypto scene. Ryo is a fork of Sumokoin. You can read all fork-related information [here](doc/sumokoin.md).
-Ryo (両 in Japanese: one syllable) is the most **secure, private and untraceable cryptocurrency out there**. Ryo originated from the _Tael_, an ancient Far East unit of weight standard used for exchanging gold and silver. Based on the foundations of Monero, Ryo emerged and is poised to dominate the privacy conscious crypto scene. Backed by a full featured and balanced development team headed by the legendary fireice_uk and psychocrypt.
+## Check Development and get release binaries
+[ ](https://github.com/ryo-currency/ryo-currency/commits/dev)
-Our blockchain ensures the highest level of privacy out there by
-from the get-go having(1) **Ring Confidential Transactions (RingCT)** (2) and hardcoding **minimum transaction _mixin_ to 12**. These settings significantly reduce the chance of being identified, traced or attacked by blockchain statistical analysis.
+Please note that code is developed on the [dev branch](https://github.com/ryo-currency/ryo-currency/tree/dev), if you want to check out the latest updates, before they are merged on main branch, please refer there. Master branch will always point to a version that we consider stable, so you can download the code by simply typing `git clone https://github.com/ryo-currency/ryo-currency.git`
-Ryo has a very high privacy setting that is suitable for all high confidential transactions as well as for storage of value without being traced, monitored or identified. We call this **true fungibility**. This means that each coin is **equal** and **interchangable**; it is highly unlikely that any coin can ever by blacklisted due to previous transactions. Over the course of many years these characteristics will pay off as crypto attacks become more sophisticated with much greater computation power in the future.
+Along with each release you can find our [precompiled binaries](https://github.com/ryo-currency/ryo-currency/releases).
+To verify that the downloaded binaries are created by one of our developer please verify the checksums.
+The authenticity of the checksums can be verified with the [PGP-key's](doc/pgp_keys.md).
+
+
+## Project Roadmap
+The Ryo dev team has several vectors of development, and it has already brought results that we can see.
+[
](https://github.com/ryo-currency/ryo-currency/commits/dev)
-Our blockchain ensures the highest level of privacy out there by
-from the get-go having(1) **Ring Confidential Transactions (RingCT)** (2) and hardcoding **minimum transaction _mixin_ to 12**. These settings significantly reduce the chance of being identified, traced or attacked by blockchain statistical analysis.
+Please note that code is developed on the [dev branch](https://github.com/ryo-currency/ryo-currency/tree/dev), if you want to check out the latest updates, before they are merged on main branch, please refer there. Master branch will always point to a version that we consider stable, so you can download the code by simply typing `git clone https://github.com/ryo-currency/ryo-currency.git`
-Ryo has a very high privacy setting that is suitable for all high confidential transactions as well as for storage of value without being traced, monitored or identified. We call this **true fungibility**. This means that each coin is **equal** and **interchangable**; it is highly unlikely that any coin can ever by blacklisted due to previous transactions. Over the course of many years these characteristics will pay off as crypto attacks become more sophisticated with much greater computation power in the future.
+Along with each release you can find our [precompiled binaries](https://github.com/ryo-currency/ryo-currency/releases).
+To verify that the downloaded binaries are created by one of our developer please verify the checksums.
+The authenticity of the checksums can be verified with the [PGP-key's](doc/pgp_keys.md).
+
+
+## Project Roadmap
+The Ryo dev team has several vectors of development, and it has already brought results that we can see.
+[ ](https://ryo-currency.com#roadmap)
+Navigate to Ryo official website to explore development track record and [roadmap](https://ryo-currency.com#roadmap) details.
+
+
+## Features
+We have a solid track record and unique features that are not copied from other projects:
+
+
+[
](https://ryo-currency.com#roadmap)
+Navigate to Ryo official website to explore development track record and [roadmap](https://ryo-currency.com#roadmap) details.
+
+
+## Features
+We have a solid track record and unique features that are not copied from other projects:
+
+
+[ ](https://github.com/ryo-currency/ryo-currency/pull/206)
+### Core:
+- **Built-in elliptic curve library**. This library significantly increases wallet scan speeds compared to other CN projects.
+- **[Cryptonight-GPU mining algorithm](https://medium.com/@crypto_ryo/cryptonight-gpu-fpga-proof-pow-algorithm-based-on-floating-point-instructions-92524debf8e8)**. ASIC/FPGA/BOTNET resistant mining algorithm. GPU friendly and suitable for both AMD and Nvidia cards.
+- **Uniform payment ID-s**. Our uniform payment ID system, makes transactions that use payment ID-s untraceable and hides the very fact that you use ID-s.
+- **Default ring size of transactions set to 25**. Increased default ring size significantly reduces the chance of being identified, traced or attacked by blockchain statistical analysis.
+- **QWMA mining difficulty algorithm**. Reworked network difficulty adjustment algorithm, to make it more adaptive to network hashrate fluctuations thus bringing more stabillity.
+- **[Poisson probability check](https://github.com/ryo-currency/ryo-writeups/blob/master/poisson-writeup.md)**. This feature stops Verge-like offline timestamp attacks.
+- **(Optional) Short address format**. Short address format for users who don't need viewkey.
+- **CRC-12 mnemonic seed validation** / **Non-latin characters support** / **Varios critical bugfixes**
+
+### Infrastructure
+- **[Ryo Wallet Atom](https://ryo-currency.com/atom)**. Modern, intuitive and rich with feature GUI wallet. Available for Windows, Linux and MacOSX.
+- **[Quasar Web wallet](https://ryowebwallet.com)**. Ultra-fast WEB based wallet that shares same design with Atom wallet.
+- **[Solo mining in GUI wallet](https://solo-pool.ryoblocks.com/getting-started)**. Built-in pool software with workers support, statistics and charts display.
+- **[Woo commerce plugin](https://github.com/ryo-currency/ryo-payments-woocommerce-gateway)**. Plug-in for web developers, to implement accepting Ryo on website.
+- **[Ryo Business room](https://ryo-currency.com/ryo-business-room)**. Business community of people fostering ecosystem development.
+
+GUI wallet | Web wallet | Cli wallet | Mobile | Hardware
+--- | --- | --- | --- | ---
+[v. 1.4.0](https://github.com/ryo-currency/ryo-wallet/releases/latest) | [Ryowebwallet](https://www.ryowebwallet.com/wallet-select) | [v. 0.4.1.0](https://github.com/ryo-currency/ryo-currency/releases/latest) | Developing | Planned
+
+## Research and contributing
+With privacy and security as the core foundation of Ryo, we invest time and effort into security research as well as investigate and analyze issues with the Cryptonote protocol in order to bring true default anonymity for users.
+- [Hiding your IP while using Ryo or other Cryptonotes](https://www.reddit.com/r/ryocurrency/comments/a4mppi/hiding_your_ip_while_using_ryo_or_other/)
+- [Tracing Cryptonote ring signatures using external metadata](https://medium.com/@crypto_ryo/tracing-cryptonote-ring-signatures-using-external-metadata-8e4866810006).
+- [How buying pot with Monero will get you busted — Knacc attack on Cryptonote coins](https://medium.com/@crypto_ryo/how-buying-pot-with-monero-will-get-you-busted-knacc-attack-on-cryptonote-coins-b157cd97e82f).
+- [On-chain tracking of Monero and other Cryptonotes](https://medium.com/@crypto_ryo/on-chain-tracking-of-monero-and-other-cryptonotes-e0afc6752527).
+You can find all write-ups in our [Ryo library](https://ryo-currency.com/library/) on the website.
+
+Although Ryo Currency code in main repository is source available until February 2020, we have contributed back bug fixes and features to Monero project:
+- [Add Unicode input line](https://github.com/monero-project/monero/pull/4390).
+- [Fix for a wallet caching bug](https://github.com/monero-project/monero/pull/4247).
+Loki Project decided to use own version of wallet, based on Ryo Wallet Atom [(libre repository)](https://github.com/ryo-currency/ryo-wallet-libre) as official GUI wallet. Triton Project uses GUI wallet that is based on Ryo Wallet Atom too.
+
## Coin Supply & Emission
-
-- **Total supply**: **80,188,888** coins in 20 years, then **263,000** coins will be emitted yearly to account for inflation.
+- **Total supply**: **88,188,888** coins in 20 years, then **263,000** coins will be emitted yearly to account for inflation.
- More than **80 million coins are available** for community mining.
-- 8,790,000 Ryo coins were burned to get rid of the original Sumokoin premine. Additionally, 100,000 coins were premined and instantly unlocked to Sumokoin devs in 2017.
+- 8,790,000 Ryo coins were burned to get rid of the original Sumokoin premine. (You can check [burned premine keyimages](https://github.com/ryo-currency/ryo-currency/tree/master/utils/burned_premine_keyimages)). Additionally, 100,000 coins were premined and instantly unlocked to Sumokoin devs in 2017. The pre-mined coins have been [frozen/burned](https://github.com/ryo-currency/ryo-currency/blob/917dbb993178bb8a2ea571f214b15adcbb7c708f/src/blockchain_db/blockchain_db.cpp#L364) as announced on [reddit](https://www.reddit.com/r/ryocurrency/comments/8nb8eq/direction_for_ryo/). This can be verified using [those](/doc/verify_premine_burn_instructions.md) instructions.
-The pre-mined coins have been frozen/burned in commit [c3a3cb6](https://github.com/ryo-currency/ryo-emergency/commit/c3a3cb620488e88be7c52e017072261a3063b872)/ [blockchain_db/blockchain_db.cpp#L250-L258](https://github.com/ryo-currency/ryo-emergency/blob/c3a3cb620488e88be7c52e017072261a3063b872/src/blockchain_db/blockchain_db.cpp#L250-L258) as announced on [reddit](https://www.reddit.com/r/ryocurrency/comments/8nb8eq/direction_for_ryo/).
+- After 2 rounds of community debates [(pt1](https://www.reddit.com/r/ryocurrency/comments/8xsyqo/community_debate_lets_talk_about_the_development/e26i1vw/) / [pt2)](https://github.com/ryo-currency/ryo-writeups/blob/master/dev-fund.md) **8,000,000** Ryo coins were introduced as development fund which is located in 2/3 multisig wallet and emitted on weekly basis next 6 years. In an effort to provide transparency to the community on how the development fund is allocated, Ryo dev team built the following [dev-fund explorer page](https://ryo-currency.com/dev-fund/).
- **Coin symbol**: **RYO**
+- **Hash algorithm**: CryptoNight-GPU (ASIC/FPGA/Botnet resistant Proof-Of-Work)
+- **Total supply**: **88,188,888** coins in 20 years (including 8M dev. fund). Then 263,000 coins each year for inflation.
+- **Block time**: **240 seconds** (difficulty is adjusted every block)
- **Coin Units**:
+ 1 nanoRyo = 0.000000001 **RYO** (10-9-_the smallest coin unit_)
+ 1 microRyo = 0.000001 **RYO** (10-6)
+ 1 milliRyo = 0.001 **RYO** (10-3)
-- **Hash algorithm**: CryptoNight Heavy (Proof-Of-Work)
-- **Emission scheme**: Ryo's block reward changes _every 6-months_ according to the following "Camel" distribution*. Our emission scheme is inspired by real-world mining production comparable to crude oil, coal and gas which is often slow at first, accelerated in the next few years before declining and becoming depleted. However, the emission path of Ryo is generally not that far apart from Bitcoin.
-
-
-
-
-
-
-
-\* The emulated algorithm of Ryo block-reward emission can be found in Python and C++ scripts at [scripts](scripts) directory.
-
-## I have Sumokoin, how can i claim my Ryo?
-- You can claim your Ryo, if you had Sumokoin before they forked at block #137500. Ryo Currency as a chain fork kept all the transactions -and thus coins you had in your wallet- up and until Sumokoin forked at block #137500. To further secure your Ryo, we're going to tie the coins to a block after the fork.
-- First, install the latest Ryo wallet. Run it and generate a new wallet. Write down the seeds. Copy the MAIN ADDRESS under the RECEIVE tab. Then from the Ryo gui, click SETTINGS » NEW WALLET and restore your Ryo from the same seeds used for your old Sumokoin wallet in the Ryo GUI.
-- Send all your coins to the new Ryo MAIN ADDRESS you copied before.
-After this, you can safely transact Sumokoin, it's important to first move your Ryo, before you move your Sumokoin.
-- If you are comfortable using the CLI, you can just SWEEP ALL Ryo to yourself instead of all the above.
-
-## About this Project
-
-This is the core implementation of Ryo. It is open source and completely free to use without restrictions, except for those specified in the license agreement below. There are no restrictions on anyone creating an alternative implementation of Ryo that uses the protocol and network in a compatible manner.
-
-## Precompiled binaries
-
-Along with each release you can find our [precompiled binaries](https://github.com/ryo-currency/ryo-currency/releases).
-To verify that the downloaded binaries are created by one of our developer please verify the checksums.
-The authenticity of the checksums can by verified with the [PGP-key's](docs/pgp_keys.md).
-
-## Compiling Ryo from source
-
-### Dependencies
-
-The following table summarizes the tools and libraries required to build. A
-few of the libraries are also included in this repository (marked as
-"Vendored"). By default, the build uses the library installed on the system,
-and ignores the vendored sources. However, if no library is found installed on
-the system, then the vendored source will be built and used. The vendored
-sources are also used for statically-linked builds because distribution
-packages often include only shared library binaries (`.so`) but not static
-library archives (`.a`).
-
-| Dep | Min. version | Vendored | Debian/Ubuntu pkg | Arch pkg | Fedora | Optional | Purpose |
-| ------------ | ------------- | -------- | ------------------ | ------------ | ----------------- | -------- | -------------- |
-| GCC | 4.7.3 | NO | `build-essential` | `base-devel` | `gcc` | NO | |
-| CMake | 3.0.0 | NO | `cmake` | `cmake` | `cmake` | NO | |
-| pkg-config | any | NO | `pkg-config` | `base-devel` | `pkgconf` | NO | |
-| Boost | 1.58 | NO | `libboost-all-dev` | `boost` | `boost-devel` | NO | C++ libraries |
-| OpenSSL | basically any | NO | `libssl-dev` | `openssl` | `openssl-devel` | NO | sha256 sum |
-| libzmq | 3.0.0 | NO | `libzmq3-dev` | `zeromq` | `cppzmq-devel` | NO | ZeroMQ library |
-| libunbound | 1.4.16 | YES | `libunbound-dev` | `unbound` | `unbound-devel` | NO | DNS resolver |
-| libsodium | ? | NO | `libsodium-dev` | ? | `libsodium-devel` | NO | libsodium |
-| libminiupnpc | 2.0 | YES | `libminiupnpc-dev` | `miniupnpc` | `miniupnpc-devel` | YES | NAT punching |
-| libunwind | any | NO | `libunwind8-dev` | `libunwind` | `libunwind-devel` | YES | Stack traces |
-| liblzma | any | NO | `liblzma-dev` | `xz` | `xz-devel` | YES | For libunwind |
-| libreadline | 6.3.0 | NO | `libreadline6-dev` | `readline` | `readline-devel` | YES | Input editing |
-| ldns | 1.6.17 | NO | `libldns-dev` | `ldns` | `ldns-devel` | YES | SSL toolkit |
-| expat | 1.1 | NO | `libexpat1-dev` | `expat` | `expat-devel` | YES | XML parsing |
-| GTest | 1.5 | YES | `libgtest-dev`^ | `gtest` | `gtest-devel` | YES | Test suite |
-| Doxygen | any | NO | `doxygen` | `doxygen` | `doxygen` | YES | Documentation |
-| Graphviz | any | NO | `graphviz` | `graphviz` | `graphviz` | YES | Documentation |
-
-
-[^] On Debian/Ubuntu `libgtest-dev` only includes sources and headers. You must
-build the library binary manually. This can be done with the following command ```sudo apt-get install libgtest-dev && cd /usr/src/gtest && sudo cmake . && sudo make && sudo mv libg* /usr/lib/ ```
-
-### Cloning the repository
-
-Clone recursively to pull-in needed submodule(s):
-
-`$ git clone https://github.com/ryo-currency/ryo-currency.git`
-
-If you already have a repo cloned, initialize and update:
-
-`$ cd ryo-currency`
-
-### Build instructions
-
-Ryo uses the CMake build system and a top-level [Makefile](Makefile) that
-invokes cmake commands as needed.
-
-#### On Linux and OS X
-
-* Install the dependencies
-* Change to the root of the source code directory, change to the most recent release branch, and build:
-
- cd ryo-currency
- git checkout tags/0.2.0
- make
-
- *Optional*: If your machine has several cores and enough memory, enable
- parallel build by running `make -j` instead of `make`. For
- this to be worthwhile, the machine should have one core and about 2GB of RAM
- available per thread.
-
- *Note*: If cmake can not find zmq.hpp file on OS X, installing `zmq.hpp` from
- https://github.com/zeromq/cppzmq to `/usr/local/include` should fix that error.
-
- *Note*: The instructions above will compile the most stable release of the
- Ryo software. If you would like to use and test the most recent software,
- use ```git checkout master```. The master branch may contain updates that are
- both unstable and incompatible with release software, though testing is always
- encouraged.
-
-* The resulting executables can be found in `build/release/bin`
-
-* Add `PATH="$PATH:$HOME/ryo/build/release/bin"` to `.profile`
-
-* Run Ryo with `ryod --detach`
-
-* **Optional**: build and run the test suite to verify the binaries:
-
- make release-test
-
- *NOTE*: `core_tests` test may take a few hours to complete.
-
-* **Optional**: to build binaries suitable for debugging:
-
- make debug
-
-* **Optional**: to build statically-linked binaries:
-
- make release-static
-
-Dependencies need to be built with -fPIC. Static libraries usually aren't, so you may have to build them yourself with -fPIC. Refer to their documentation for how to build them.
-
-* **Optional**: build documentation in `doc/html` (omit `HAVE_DOT=YES` if `graphviz` is not installed):
-
- HAVE_DOT=YES doxygen Doxyfile
-
-#### On the Raspberry Pi
-
-Tested on a Raspberry Pi Zero with a clean install of minimal Raspbian Stretch (2017-09-07 or later) from https://www.raspberrypi.org/downloads/raspbian/. If you are using Raspian Jessie, [please see note in the following section](#note-for-raspbian-jessie-users).
-
-* `apt-get update && apt-get upgrade` to install all of the latest software
-
-* Install the dependencies for Ryo from the 'Debian' column in the table above.
-
-* Enable zram:
-```
- sudo zramctl --find --size=1024M # Note the device name
- sudo mkswap
- sudo swapon
-```
-* Clone ryo and checkout most recent release version:
-```
- git clone https://github.com/ryo-currency/ryo-currency.git
- cd ryo-currency
- git checkout tags/0.2.0
-```
-* Build:
-```
- make release
-```
-* Wait 4-6 hours
-
-* The resulting executables can be found in `build/release/bin`
-
-* Add `PATH="$PATH:$HOME/ryo/build/release/bin"` to `.profile`
-
-* Run Ryo with `ryod --detach`
-
-* You may wish to reduce the size of the swap file after the build has finished, and delete the boost directory from your home directory
-
-#### *Note for Raspbian Jessie users:*
-
-If you are using the older Raspbian Jessie image, compiling Ryo is a bit more complicated. The version of Boost available in the Debian Jessie repositories is too old to use with Ryo, and thus you must compile a newer version yourself. The following explains the extra steps, and has been tested on a Raspberry Pi 2 with a clean install of minimal Raspbian Jessie.
-
-* As before, `apt-get update && apt-get upgrade` to install all of the latest software, and enable zram
-
-```
- sudo zramctl --find --size=1024M # Note the device name
- sudo mkswap
- sudo swapon
-```
-
-* Then, install the dependencies for Ryo except `libunwind` and `libboost-all-dev`
-
-* Install the latest version of boost (this may first require invoking `apt-get remove --purge libboost*` to remove a previous version if you're not using a clean install):
-```
- cd
- wget https://sourceforge.net/projects/boost/files/boost/1.64.0/boost_1_64_0.tar.bz2
- tar xvfo boost_1_64_0.tar.bz2
- cd boost_1_64_0
- ./bootstrap.sh
- sudo ./b2
-```
-* Wait ~8 hours
-```
- sudo ./bjam install
-```
-* Wait ~4 hours
-
-* From here, follow the [general Raspberry Pi instructions](#on-the-raspberry-pi) from the "Clone ryo and checkout most recent release version" step.
-
-#### On Windows:
-
-Binaries for Windows are built on Windows using the MinGW toolchain within
-[MSYS2 environment](http://msys2.github.io). The MSYS2 environment emulates a
-POSIX system. The toolchain runs within the environment and *cross-compiles*
-binaries that can run outside of the environment as a regular Windows
-application.
-
-**Preparing the Build Environment**
-
-* Download and install the [MSYS2 installer](http://msys2.github.io), either the 64-bit or the 32-bit package, depending on your system.
-* Open the MSYS shell via the `MSYS2 Shell` shortcut
-* Update packages using pacman:
-
- pacman -Syuu
-
-* Exit the MSYS shell using Alt+F4
-* Edit the properties for the `MSYS2 Shell` shortcut changing "msys2_shell.bat" to "msys2_shell.cmd -mingw64" for 64-bit builds or "msys2_shell.cmd -mingw32" for 32-bit builds
-* Restart MSYS shell via modified shortcut and update packages again using pacman:
-
- pacman -Syuu
-
-
-* Install dependencies:
-
- To build for 64-bit Windows:
-
- pacman -S mingw-w64-x86_64-toolchain make mingw-w64-x86_64-cmake mingw-w64-x86_64-boost mingw-w64-x86_64-openssl mingw-w64-x86_64-zeromq mingw-w64-x86_64-libsodium
-
- To build for 32-bit Windows:
-
- pacman -S mingw-w64-i686-toolchain make mingw-w64-i686-cmake mingw-w64-i686-boost mingw-w64-i686-openssl mingw-w64-i686-zeromq mingw-w64-i686-libsodium
-
-* Open the MingW shell via `MinGW-w64-Win64 Shell` shortcut on 64-bit Windows
- or `MinGW-w64-Win64 Shell` shortcut on 32-bit Windows. Note that if you are
- running 64-bit Windows, you will have both 64-bit and 32-bit MinGW shells.
-
-**Cloning**
-
-* To git clone, run:
-
- git clone https://github.com/ryo-currency/ryo-currency.git
-
-**Building**
-
-* Change to the cloned directory, run:
-
- cd ryo-currency
-
-* If you would like a specific [version/tag](https://github.com/ryo-currency/ryo-currency/tags), do a git checkout for that version. eg. '0.2.0'. If you dont care about the version and just want binaries from master, skip this step:
-
- git checkout 0.2.0
-
-* If you are on a 64-bit system, run:
-
- make release-static-win64
-
-* If you are on a 32-bit system, run:
-
- make release-static-win32
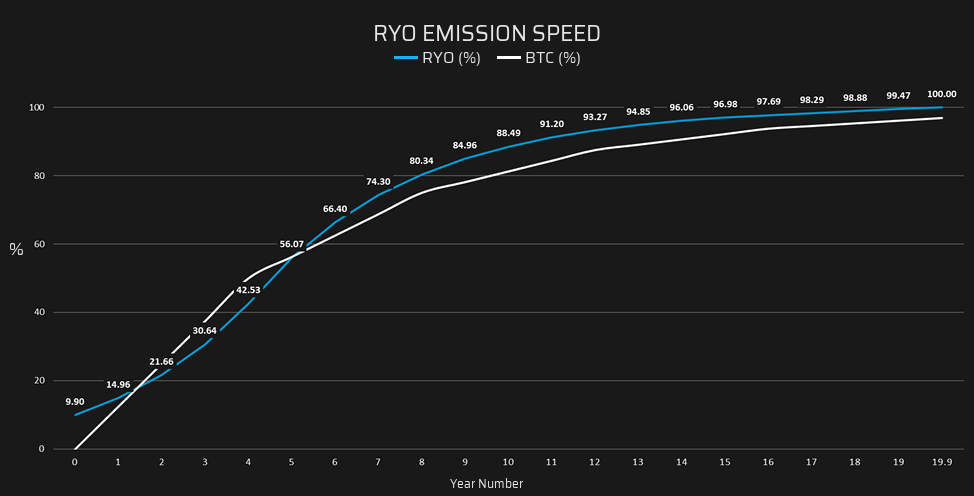
+- **Emission scheme**: Ryo's block reward changes _every 6-months_ according to the following "Plateau" distribution*. Our emission scheme is inspired by real-world mining production comparable to crude oil, coal and gas which is often slow at first, accelerated in the next few years before declining and becoming depleted. However, the emission path of Ryo is generally not that far apart from Bitcoin. The emission curve for Ryo was one of the final aspects of the code we inherited from Sumokoin that was re-written and had to be even [fixed](https://medium.com/@ryo.currency/fixing-a-broken-emission-curve-818300e145a2) during May 2019 [community debates](https://github.com/ryo-currency/ryo-writeups/blob/master/emission-change-part-two.md).
-* The resulting executables can be found in `build/release/bin`
+
-* **Optional**: to build Windows binaries suitable for debugging on a 64-bit system, run:
+
- make debug-static-win64
-* **Optional**: to build Windows binaries suitable for debugging on a 32-bit system, run:
+## Community
+You can join our [community](https://ryo-currency.com/social) and ask the developers about their perspectives, ask for technical support, and get the latest news
- make debug-static-win32
+## Licensing details
+This is the core implementation of Ryo. It is free to get and modify for your own usage, however, you [can't](https://www.reddit.com/r/ryocurrency/comments/8tc5tg/decision_our_source_code_will_be_sourceavailable) distribute modified copies from this repository.
-* The resulting executables can be found in `build/debug/bin`
+[Ryo-libre](https://github.com/ryo-currency/ryo-libre) is open source and completely free to use version of this repository without restrictions which is updated on yearly basis. There are no restrictions on anyone creating an alternative implementation of Ryo that uses the protocol and network in a compatible manner. [(Read more about Ryo-libre)](https://www.reddit.com/r/ryocurrency/comments/am4g0y/ann_ryolibre_open_source_repository_of_ryo)
-### On FreeBSD:
+Copyright (c) 2019, Ryo Currency Project
-The project can be built from scratch by following instructions for Linux above. If you are running ryo in a jail you need to add the flag: `allow.sysvipc=1` to your jail configuration, otherwise lmdb will throw the error message: `Failed to open lmdb environment: Function not implemented`.
-
-We expect to add Ryo into the ports tree in the near future, which will aid in managing installations using ports or packages.
-
-### On OpenBSD:
-
-#### OpenBSD < 6.2
-
-This has been tested on OpenBSD 5.8.
-
-You will need to add a few packages to your system. `pkg_add db cmake gcc gcc-libs g++ miniupnpc gtest`.
-
-The doxygen and graphviz packages are optional and require the xbase set.
-
-The Boost package has a bug that will prevent librpc.a from building correctly. In order to fix this, you will have to Build boost yourself from scratch. Follow the directions here (under "Building Boost"):
-https://github.com/bitcoin/bitcoin/blob/master/doc/build-openbsd.md
-
-You will have to add the serialization, date_time, and regex modules to Boost when building as they are needed by Ryo.
-
-To build: `env CC=egcc CXX=eg++ CPP=ecpp DEVELOPER_LOCAL_TOOLS=1 BOOST_ROOT=/path/to/the/boost/you/built make release-static-64`
-
-#### OpenBSD >= 6.2
-
-You will need to add a few packages to your system. `pkg_add cmake miniupnpc zeromq libiconv`.
-
-The doxygen and graphviz packages are optional and require the xbase set.
-
-
-Build the Boost library using clang. This guide is derived from: https://github.com/bitcoin/bitcoin/blob/master/doc/build-openbsd.md
-
-We assume you are compiling with a non-root user and you have `doas` enabled.
-
-Note: do not use the boost package provided by OpenBSD, as we are installing boost to `/usr/local`.
-
-```
-# Create boost building directory
-mkdir ~/boost
-cd ~/boost
-
-# Fetch boost source
-ftp -o boost_1_64_0.tar.bz2 https://netcologne.dl.sourceforge.net/project/boost/boost/1.64.0/boost_1_64_0.tar.bz2
-
-# MUST output: (SHA256) boost_1_64_0.tar.bz2: OK
-echo "7bcc5caace97baa948931d712ea5f37038dbb1c5d89b43ad4def4ed7cb683332 boost_1_64_0.tar.bz2" | sha256 -c
-tar xfj boost_1_64_0.tar.bz2
-
-# Fetch and apply boost patches, required for OpenBSD
-ftp -o boost_test_impl_execution_monitor_ipp.patch https://raw.githubusercontent.com/openbsd/ports/bee9e6df517077a7269ff0dfd57995f5c6a10379/devel/boost/patches/patch-boost_test_impl_execution_monitor_ipp
-ftp -o boost_config_platform_bsd_hpp.patch https://raw.githubusercontent.com/openbsd/ports/90658284fb786f5a60dd9d6e8d14500c167bdaa0/devel/boost/patches/patch-boost_config_platform_bsd_hpp
-
-# MUST output: (SHA256) boost_config_platform_bsd_hpp.patch: OK
-echo "1f5e59d1154f16ee1e0cc169395f30d5e7d22a5bd9f86358f738b0ccaea5e51d boost_config_platform_bsd_hpp.patch" | sha256 -c
-# MUST output: (SHA256) boost_test_impl_execution_monitor_ipp.patch: OK
-echo "30cec182a1437d40c3e0bd9a866ab5ddc1400a56185b7e671bb3782634ed0206 boost_test_impl_execution_monitor_ipp.patch" | sha256 -c
-
-cd boost_1_64_0
-patch -p0 < ../boost_test_impl_execution_monitor_ipp.patch
-patch -p0 < ../boost_config_platform_bsd_hpp.patch
-
-# Start building boost
-echo 'using clang : : c++ : "-fvisibility=hidden -fPIC" "" "ar" "strip" "ranlib" "" : ;' > user-config.jam
-./bootstrap.sh --without-icu --with-libraries=chrono,filesystem,program_options,system,thread,test,date_time,regex,serialization,locale --with-toolset=clang
-./b2 toolset=clang cxxflags="-stdlib=libc++" linkflags="-stdlib=libc++" -sICONV_PATH=/usr/local
-doas ./b2 -d0 runtime-link=shared threadapi=pthread threading=multi link=static variant=release --layout=tagged --build-type=complete --user-config=user-config.jam -sNO_BZIP2=1 -sICONV_PATH=/usr/local --prefix=/usr/local install
-```
-
-Build cppzmq
-
-Build the cppzmq bindings.
-
-We assume you are compiling with a non-root user and you have `doas` enabled.
-
-```
-# Create cppzmq building directory
-mkdir ~/cppzmq
-cd ~/cppzmq
-
-# Fetch cppzmq source
-ftp -o cppzmq-4.2.3.tar.gz https://github.com/zeromq/cppzmq/archive/v4.2.3.tar.gz
-
-# MUST output: (SHA256) cppzmq-4.2.3.tar.gz: OK
-echo "3e6b57bf49115f4ae893b1ff7848ead7267013087dc7be1ab27636a97144d373 cppzmq-4.2.3.tar.gz" | sha256 -c
-tar xfz cppzmq-4.2.3.tar.gz
-
-# Start building cppzmq
-cd cppzmq-4.2.3
-mkdir build
-cd build
-cmake ..
-doas make install
-```
-
-Build Ryo: `env DEVELOPER_LOCAL_TOOLS=1 BOOST_ROOT=/usr/local make release-static`
-
-### On Solaris:
-
-The default Solaris linker can't be used, you have to install GNU ld, then run cmake manually with the path to your copy of GNU ld:
-
- mkdir -p build/release
- cd build/release
- cmake -DCMAKE_LINKER=/path/to/ld -D CMAKE_BUILD_TYPE=Release ../..
- cd ../..
-
-Then you can run make as usual.
-
-### On Linux for Android (using docker):
-
- # Build image (select android64.Dockerfile for aarch64)
- cd utils/build_scripts/ && docker build -f android32.Dockerfile -t ryo-android .
- # Create container
- docker create -it --name ryo-android ryo-android bash
- # Get binaries
- docker cp ryo-android:/opt/android/ryo/build/release/bin .
-
-### Building portable statically linked binaries
-
-By default, in either dynamically or statically linked builds, binaries target the specific host processor on which the build happens and are not portable to other processors. Portable binaries can be built using the following targets:
-
-* ```make release-static-linux-x86_64``` builds binaries on Linux on x86_64 portable across POSIX systems on x86_64 processors
-* ```make release-static-linux-i686``` builds binaries on Linux on x86_64 or i686 portable across POSIX systems on i686 processors
-* ```make release-static-linux-armv8``` builds binaries on Linux portable across POSIX systems on armv8 processors
-* ```make release-static-linux-armv7``` builds binaries on Linux portable across POSIX systems on armv7 processors
-* ```make release-static-linux-armv6``` builds binaries on Linux portable across POSIX systems on armv6 processors
-* ```make release-static-win64``` builds binaries on 64-bit Windows portable across 64-bit Windows systems
-* ```make release-static-win32``` builds binaries on 64-bit or 32-bit Windows portable across 32-bit Windows systems
-
-## Installing Ryo from a package
-
-**DISCLAIMER: These packages are not part of this repository or maintained by this project's contributors, and as such, do not go through the same review process to ensure their trustworthiness and security.**
-
-Packages are available for
-
-* Docker
-
- # Build using all available cores
- `docker build -t ryo .`
-
- # or build using a specific number of cores (reduce RAM requirement)
- `docker build --build-arg NPROC=1 -t ryo .`
-
- # either run in foreground
- `docker run -it -v /ryo/chain:/root/.ryo -v /ryo/wallet:/wallet -p 18080:18080 ryo`
-
- # or in background
- `docker run -it -d -v /ryo/chain:/root/.ryo -v /ryo/wallet:/wallet -p 18080:18080 ryo`
-
-Packaging for your favorite distribution would be a welcome contribution!
-
-## Running ryod
-
-The build places the binary in `bin/` sub-directory within the build directory
-from which cmake was invoked (repository root by default). To run in
-foreground:
-
- ./bin/ryod
-
-To list all available options, run `./bin/ryod --help`. Options can be
-specified either on the command line or in a configuration file passed by the
-`--config-file` argument. To specify an option in the configuration file, add
-a line with the syntax `argumentname=value`, where `argumentname` is the name
-of the argument without the leading dashes, for example `log-level=1`.
-
-To run in background:
-
- ./bin/ryod --log-file ryod.log --detach
-
-To run as a systemd service, copy
-[ryod.service](utils/systemd/ryod.service) to `/etc/systemd/system/` and
-[ryod.conf](utils/conf/ryod.conf) to `/etc/`. The [example
-service](utils/systemd/ryod.service) assumes that the user `ryo` exists
-and its home is the data directory specified in the [example
-config](utils/conf/ryod.conf).
-
-If you're on Mac, you may need to add the `--max-concurrency 1` option to
-ryo-wallet-cli, and possibly ryod, if you get crashes refreshing.
-
-## Using Tor
-
-While Ryo isn't made to integrate with Tor, it can be used wrapped with torsocks, by
-setting the following configuration parameters and environment variables:
-
-* `--p2p-bind-ip 127.0.0.1` on the command line or `p2p-bind-ip=127.0.0.1` in
- ryod.conf to disable listening for connections on external interfaces.
-* `--no-igd` on the command line or `no-igd=1` in ryod.conf to disable IGD
- (UPnP port forwarding negotiation), which is pointless with Tor.
-* `DNS_PUBLIC=tcp` or `DNS_PUBLIC=tcp://x.x.x.x` where x.x.x.x is the IP of the
- desired DNS server, for DNS requests to go over TCP, so that they are routed
- through Tor. When IP is not specified, ryod uses the default list of
- servers defined in [src/common/dns_utils.cpp](src/common/dns_utils.cpp).
-* `TORSOCKS_ALLOW_INBOUND=1` to tell torsocks to allow ryod to bind to interfaces
- to accept connections from the wallet. On some Linux systems, torsocks
- allows binding to localhost by default, so setting this variable is only
- necessary to allow binding to local LAN/VPN interfaces to allow wallets to
- connect from remote hosts. On other systems, it may be needed for local wallets
- as well.
-* Do NOT pass `--detach` when running through torsocks with systemd, (see
- [utils/systemd/ryod.service](utils/systemd/ryod.service) for details).
-* If you use the wallet with a Tor daemon via the loopback IP (eg, 127.0.0.1:9050),
- then use `--untrusted-daemon` unless it is your own hidden service.
-
-Example command line to start ryod through Tor:
-
- DNS_PUBLIC=tcp torsocks ryod --p2p-bind-ip 127.0.0.1 --no-igd
-
-### Using Tor on Tails
-
-TAILS ships with a very restrictive set of firewall rules. Therefore, you need
-to add a rule to allow this connection too, in addition to telling torsocks to
-allow inbound connections. Full example:
-
- sudo iptables -I OUTPUT 2 -p tcp -d 127.0.0.1 -m tcp --dport 18081 -j ACCEPT
- DNS_PUBLIC=tcp torsocks ./ryod --p2p-bind-ip 127.0.0.1 --no-igd --rpc-bind-ip 127.0.0.1 \
- --data-dir /home/amnesia/Persistent/your/directory/to/the/blockchain
-
-## Using readline
-
-While `ryod` and `ryo-wallet-cli` do not use readline directly, most of the functionality can be obtained by running them via `rlwrap`. This allows command recall, edit capabilities, etc. It does not give autocompletion without an extra completion file, however. To use rlwrap, simply prepend `rlwrap` to the command line, eg:
-
-`rlwrap bin/ryo-wallet-cli --wallet-file /path/to/wallet`
-
-Note: rlwrap will save things like your seed and private keys, if you supply them on prompt. You may want to not use rlwrap when you use simplewallet to restore from seed, etc.
-
-# Debugging
-
-This section contains general instructions for debugging failed installs or problems encountered with Ryo. First ensure you are running the latest version built from the github repo.
-
-### Obtaining stack traces and core dumps on Unix systems
-
-We generally use the tool `gdb` (GNU debugger) to provide stack trace functionality, and `ulimit` to provide core dumps in builds which crash or segfault.
-
-* To use gdb in order to obtain a stack trace for a build that has stalled:
-
-Run the build.
-
-Once it stalls, enter the following command:
-
-```
-gdb /path/to/ryod `pidof ryod`
-```
-
-Type `thread apply all bt` within gdb in order to obtain the stack trace
-
-* If however the core dumps or segfaults:
-
-Enter `ulimit -c unlimited` on the command line to enable unlimited filesizes for core dumps
-
-Enter `echo core | sudo tee /proc/sys/kernel/core_pattern` to stop cores from being hijacked by other tools
-
-Run the build.
-
-When it terminates with an output along the lines of "Segmentation fault (core dumped)", there should be a core dump file in the same directory as ryod. It may be named just `core`, or `core.xxxx` with numbers appended.
-
-You can now analyse this core dump with `gdb` as follows:
-
-`gdb /path/to/ryod /path/to/dumpfile`
-
-Print the stack trace with `bt`
-
-* To run ryo within gdb:
-
-Type `gdb /path/to/ryod`
-
-Pass command-line options with `--args` followed by the relevant arguments
-
-Type `run` to run ryod
-
-### Analysing memory corruption
-
-We use the tool `valgrind` for this.
-
-Run with `valgrind /path/to/ryod`. It will be slow.
-
-# LMDB
-
-There is an `mdb_stat` command in the LMDB source that can print statistics about the database but it's not routinely built. This can be built with the following command:
-
-`cd ~/ryo/external/db_drivers/liblmdb && make`
-
-The output of `mdb_stat -ea ` will indicate inconsistencies in the blocks, block_heights and block_info table.
+Copyright (c) 2014-2017, The Monero Project
-The output of `mdb_dump -s blocks ` and `mdb_dump -s block_info ` is useful for indicating whether blocks and block_info contain the same keys.
+Copyright (c) 2012-2013, The Cryptonote developers
-These records are dumped as hex data, where the first line is the key and the second line is the data.
+Copyright (c) 2017, Sumokoin.org
diff --git a/contrib/epee/demo/demo_http_server/stdafx.h b/contrib/epee/demo/demo_http_server/stdafx.h
index 6ee6087a..ef268f22 100644
--- a/contrib/epee/demo/demo_http_server/stdafx.h
+++ b/contrib/epee/demo/demo_http_server/stdafx.h
@@ -32,4 +32,5 @@
#define BOOST_FILESYSTEM_VERSION 3
#define ENABLE_RELEASE_LOGGING
-#include "misc_log_ex.h"
+#include "common/gulps.hpp"
+
diff --git a/contrib/epee/demo/demo_levin_server/stdafx.h b/contrib/epee/demo/demo_levin_server/stdafx.h
index 077d9007..1a8bdb53 100644
--- a/contrib/epee/demo/demo_levin_server/stdafx.h
+++ b/contrib/epee/demo/demo_levin_server/stdafx.h
@@ -33,4 +33,5 @@
#define BOOST_FILESYSTEM_VERSION 3
#define ENABLE_RELEASE_LOGGING
#include "log_opt_defs.h"
-#include "misc_log_ex.h"
+#include "common/gulps.hpp"
+
diff --git a/contrib/epee/demo/iface/transport_defs.h b/contrib/epee/demo/iface/transport_defs.h
index b1e3a078..7460c2a3 100644
--- a/contrib/epee/demo/iface/transport_defs.h
+++ b/contrib/epee/demo/iface/transport_defs.h
@@ -10,7 +10,7 @@ struct some_test_subdata
{
std::string m_str;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(some_test_subdata)
KV_SERIALIZE(m_str)
END_KV_SERIALIZE_MAP()
};
@@ -44,7 +44,7 @@ struct some_test_data
epee::serialization::storage_entry m_storage_entry_int;
epee::serialization::storage_entry m_storage_entry_string;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(some_test_data)
KV_SERIALIZE(m_str)
KV_SERIALIZE(m_uint64)
KV_SERIALIZE(m_uint32)
@@ -86,7 +86,7 @@ struct COMMAND_EXAMPLE_1
std::string example_string_data;
some_test_data sub;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(request)
KV_SERIALIZE(example_string_data)
KV_SERIALIZE(sub)
END_KV_SERIALIZE_MAP()
@@ -97,7 +97,7 @@ struct COMMAND_EXAMPLE_1
bool m_success;
std::list subs;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(response)
KV_SERIALIZE(m_success)
KV_SERIALIZE(subs)
END_KV_SERIALIZE_MAP()
@@ -112,7 +112,7 @@ struct COMMAND_EXAMPLE_2
{
std::string example_string_data2;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(request)
KV_SERIALIZE(example_string_data2)
END_KV_SERIALIZE_MAP()
};
@@ -121,7 +121,7 @@ struct COMMAND_EXAMPLE_2
{
bool m_success;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(response)
KV_SERIALIZE(m_success)
END_KV_SERIALIZE_MAP()
};
diff --git a/contrib/epee/include/ado_db_helper.h b/contrib/epee/include/ado_db_helper.h
index cc23bf19..ca047215 100644
--- a/contrib/epee/include/ado_db_helper.h
+++ b/contrib/epee/include/ado_db_helper.h
@@ -34,6 +34,8 @@
#include
#include
+#include "common/gulps.hpp"
+
#define BEGIN_TRY_SECTION() \
try \
{
@@ -44,7 +46,8 @@
} \
catch(const std::exception &ex) \
{ \
- LOG_PRINT_J("DB_ERROR: " << ex.what(), LOG_LEVEL_0); \
+ GULPS_CAT_MAJOR("epee_ado_db_help"); \
+ GULPSF_ERROR("DB_ERROR: {}", ex.what(); \
return ret_val; \
} \
catch(const _com_error &comm_err) \
@@ -53,13 +56,15 @@
std::string descr = string_encoding::convert_to_ansii(pstr ? pstr : TEXT("")); \
const TCHAR *pmessage = comm_err.ErrorMessage(); \
pstr = comm_err.Source(); \
+ GULPS_CAT_MAJOR("epee_ado_db_help"); \
std::string source = string_encoding::convert_to_ansii(pstr ? pstr : TEXT("")); \
- LOG_PRINT_J("COM_ERROR " << mess_where << ":\n\tDescriprion:" << descr << ", \n\t Message: " << string_encoding::convert_to_ansii(pmessage) << "\n\t Source: " << source, LOG_LEVEL_0); \
+ GULPSF_ERROR("COM_ERROR {}:\n\tDescriprion:{}, \n\t Message: {}\n\t Source: {}", mess_where, descr, string_encoding::convert_to_ansii(pmessage), source); \
return ret_val; \
} \
catch(...) \
{ \
- LOG_PRINT_J("..._ERROR: Unknown error.", LOG_LEVEL_0); \
+ GULPS_CAT_MAJOR("epee_ado_db_help"); \
+ GULPS_ERROR("..._ERROR: Unknown error."); \
return ret_val; \
}
@@ -82,6 +87,7 @@ struct profile_entry
class profiler_manager
{
+ GULPS_CAT_MAJOR("epee_ado_db_help");
public:
typedef std::map sqls_map;
profiler_manager() {}
@@ -352,7 +358,7 @@ inline bool select_helper(ADODB::_CommandPtr cmd, table &result_vector)
ADODB::_RecordsetPtr precordset = cmd->Execute(NULL, NULL, NULL);
if(!precordset)
{
- LOG_ERROR("DB_ERROR: cmd->Execute returned NULL!!!");
+ GULPS_ERROR("DB_ERROR: cmd->Execute returned NULL!!!");
return false;
}
@@ -364,7 +370,7 @@ inline bool select_helper(ADODB::_CommandPtr cmd, table &result_vector)
{
if(precordset->MoveFirst()!= S_OK)
{
- LOG_ERROR("DB_ERROR: Filed to move first!!!");
+ GULPS_ERROR("DB_ERROR: Filed to move first!!!");
return false;
}
}
@@ -956,18 +962,18 @@ class per_thread_connection_pool
if(S_OK != conn.CreateInstance(__uuidof(ADODB::Connection)))
{
- LOG_ERROR("Failed to Create, instance, was CoInitialize called ???!");
+ GULPS_ERROR("Failed to Create, instance, was CoInitialize called ???!");
return conn;
}
HRESULT res = conn->Open(_bstr_t(m_connection_string.c_str()), _bstr_t(m_login.c_str()), _bstr_t(m_password.c_str()), NULL);
if(res != S_OK)
{
- LOG_ERROR("Failed to connect do DB, connection str:" << m_connection_string);
+ GULPSF_ERROR("Failed to connect do DB, connection str:{}", m_connection_string);
return conn;
}
CATCH_TRY_SECTION_MESS(conn, "while creating another connection");
- LOG_PRINT("New DB Connection added for threadid=" << ::GetCurrentThreadId(), LOG_LEVEL_0);
+ GULPSF_PRINT("New DB Connection added for threadid={}", ::GetCurrentThreadId());
ado_db_helper::execute_helper(conn, "set enable_seqscan=false;");
return conn;
}
@@ -994,7 +1000,7 @@ class per_thread_connection_pool
HRESULT res = rconn->Open(_bstr_t(m_connection_string.c_str()), _bstr_t(m_login.c_str()), _bstr_t(m_password.c_str()), NULL);
if(res != S_OK)
{
- LOG_PRINT("Failed to restore connection to local AI DB", LOG_LEVEL_1);
+ GULPS_LOG_L1("Failed to restore connection to local AI DB");
return false;
}
CATCH_TRY_SECTION(false);
@@ -1053,7 +1059,7 @@ bool find_or_add_t(const std::string &sql_select_statment, const std::string &sq
template
bool find_or_add_t_multiparametred(const std::string &sql_select_statment, const std::string &sql_insert_statment, OUT default_id_type &id, OUT bool &new_object_added, TParams params, t_conn &c)
{
-
+ GULPS_CAT_MAJOR("epee_ado_db_help");
//CHECK_CONNECTION(false);
new_object_added = false;
@@ -1067,8 +1073,8 @@ bool find_or_add_t_multiparametred(const std::string &sql_select_statment, const
{
//last time try to select
res = select_helper_multiparam(c.get_db_connection(), sql_select_statment, params, result_table);
- CHECK_AND_ASSERT_MES(res, false, "Failed to execute statment: " << sql_select_statment);
- CHECK_AND_ASSERT_MES(result_table.size(), false, "No records returned from statment: " << sql_select_statment);
+ GULPS_CHECK_AND_ASSERT_MES(res, false, "Failed to execute statment: " , sql_select_statment);
+ GULPS_CHECK_AND_ASSERT_MES(result_table.size(), false, "No records returned from statment: " , sql_select_statment);
}
else
{
diff --git a/contrib/epee/include/console_handler.h b/contrib/epee/include/console_handler.h
index 91b2a313..9fdb3095 100644
--- a/contrib/epee/include/console_handler.h
+++ b/contrib/epee/include/console_handler.h
@@ -26,7 +26,6 @@
#pragma once
-#include "misc_log_ex.h"
#include "string_tools.h"
#include
#include
@@ -41,6 +40,8 @@
#include
#include
+#include "common/gulps.hpp"
+
#ifdef HAVE_READLINE
#include "readline_buffer.h"
#endif
@@ -288,6 +289,7 @@ bool empty_commands_handler(t_server *psrv, const std::string &command)
class async_console_handler
{
+ GULPS_CAT_MAJOR("epee_csl_hand");
public:
async_console_handler()
{
@@ -322,14 +324,12 @@ class async_console_handler
color_prompt += " ";
color_prompt += "\001\033[0m\002";
m_stdin_reader.get_readline_buffer().set_prompt(color_prompt);
-#else
- epee::set_console_color(epee::console_color_yellow, true);
- std::cout << prompt;
- if(' ' != prompt.back())
- std::cout << ' ';
- epee::reset_console_color();
- std::cout.flush();
#endif
+
+ if(prompt.back() != ' ')
+ prompt += ' ';
+ gulps::inst().log(gulps::message(gulps::OUT_USER_0, gulps::LEVEL_PRINT, gulps_major_cat::c_str(),
+ "cmd_prompt", __FILE__, __LINE__, std::move(prompt), gulps::COLOR_BOLD_YELLOW, false));
}
}
@@ -357,11 +357,10 @@ class async_console_handler
}
if(!get_line_ret)
{
- MERROR("Failed to read line.");
+ GULPS_ERROR("Failed to read line.");
}
string_tools::trim(command);
-
- LOG_PRINT_L2("Read command: " << command);
+ GULPS_LOG_L2("Read command: ", command);
if(command.empty())
{
continue;
@@ -379,13 +378,13 @@ class async_console_handler
#ifdef HAVE_READLINE
rdln::suspend_readline pause_readline;
#endif
- std::cout << "unknown command: " << command << std::endl;
- std::cout << usage;
+ GULPS_PRINT("unknown command: ", command);
+ GULPS_PRINT(usage);
}
}
catch(const std::exception &ex)
{
- LOG_ERROR("Exception at [console_handler], what=" << ex.what());
+ GULPSF_ERROR("Exception at [console_handler], what={}", ex.what());
}
}
if(exit_handler)
@@ -484,7 +483,7 @@ class command_handler
for(auto &x : m_command_handlers)
{
- ss << x.second.second.first << ENDL;
+ ss << x.second.second.first << "\n";
}
return ss.str();
}
diff --git a/contrib/epee/include/gzip_encoding.h b/contrib/epee/include/gzip_encoding.h
index f0ab5d98..f6166283 100644
--- a/contrib/epee/include/gzip_encoding.h
+++ b/contrib/epee/include/gzip_encoding.h
@@ -106,7 +106,7 @@ class content_encoding_gzip : public i_sub_handler
int flag = Z_SYNC_FLUSH;
int ret = inflate(&m_zstream_in, flag);
- CHECK_AND_ASSERT_MES(ret >= 0 || m_zstream_in.avail_out || m_is_deflate_mode, false, "content_encoding_gzip::update_in() Failed to inflate. err = " << ret);
+ GULPS_CHECK_AND_ASSERT_MES(ret >= 0 || m_zstream_in.avail_out || m_is_deflate_mode, false, "content_encoding_gzip::update_in() Failed to inflate. err = " , ret);
if(Z_STREAM_END == ret)
m_is_stream_ended = true;
@@ -126,7 +126,7 @@ class content_encoding_gzip : public i_sub_handler
ret = inflate(&m_zstream_in, Z_NO_FLUSH);
if(ret != Z_OK)
{
- LOCAL_ASSERT(0);
+ GULPS_LOCAL_ASSERT(0);
m_pre_decode.swap(piece_of_transfer);
return false;
}
@@ -136,7 +136,7 @@ class content_encoding_gzip : public i_sub_handler
ret = inflate(&m_zstream_in, Z_NO_FLUSH);
if(ret != Z_OK)
{
- LOCAL_ASSERT(0);
+ GULPS_LOCAL_ASSERT(0);
m_pre_decode.swap(piece_of_transfer);
return false;
}
diff --git a/contrib/epee/include/include_base_utils.h b/contrib/epee/include/include_base_utils.h
index 3484d842..1e89b0fc 100644
--- a/contrib/epee/include/include_base_utils.h
+++ b/contrib/epee/include/include_base_utils.h
@@ -29,4 +29,4 @@
#define BOOST_FILESYSTEM_VERSION 3
#define ENABLE_RELEASE_LOGGING
-#include "misc_log_ex.h"
+#include "common/gulps.hpp"
diff --git a/contrib/epee/include/math_helper.h b/contrib/epee/include/math_helper.h
index efaf8b9c..27520bfe 100644
--- a/contrib/epee/include/math_helper.h
+++ b/contrib/epee/include/math_helper.h
@@ -26,7 +26,7 @@
#pragma once
-#include
+#include
#include
#include
#include
](https://github.com/ryo-currency/ryo-currency/pull/206)
+### Core:
+- **Built-in elliptic curve library**. This library significantly increases wallet scan speeds compared to other CN projects.
+- **[Cryptonight-GPU mining algorithm](https://medium.com/@crypto_ryo/cryptonight-gpu-fpga-proof-pow-algorithm-based-on-floating-point-instructions-92524debf8e8)**. ASIC/FPGA/BOTNET resistant mining algorithm. GPU friendly and suitable for both AMD and Nvidia cards.
+- **Uniform payment ID-s**. Our uniform payment ID system, makes transactions that use payment ID-s untraceable and hides the very fact that you use ID-s.
+- **Default ring size of transactions set to 25**. Increased default ring size significantly reduces the chance of being identified, traced or attacked by blockchain statistical analysis.
+- **QWMA mining difficulty algorithm**. Reworked network difficulty adjustment algorithm, to make it more adaptive to network hashrate fluctuations thus bringing more stabillity.
+- **[Poisson probability check](https://github.com/ryo-currency/ryo-writeups/blob/master/poisson-writeup.md)**. This feature stops Verge-like offline timestamp attacks.
+- **(Optional) Short address format**. Short address format for users who don't need viewkey.
+- **CRC-12 mnemonic seed validation** / **Non-latin characters support** / **Varios critical bugfixes**
+
+### Infrastructure
+- **[Ryo Wallet Atom](https://ryo-currency.com/atom)**. Modern, intuitive and rich with feature GUI wallet. Available for Windows, Linux and MacOSX.
+- **[Quasar Web wallet](https://ryowebwallet.com)**. Ultra-fast WEB based wallet that shares same design with Atom wallet.
+- **[Solo mining in GUI wallet](https://solo-pool.ryoblocks.com/getting-started)**. Built-in pool software with workers support, statistics and charts display.
+- **[Woo commerce plugin](https://github.com/ryo-currency/ryo-payments-woocommerce-gateway)**. Plug-in for web developers, to implement accepting Ryo on website.
+- **[Ryo Business room](https://ryo-currency.com/ryo-business-room)**. Business community of people fostering ecosystem development.
+
+GUI wallet | Web wallet | Cli wallet | Mobile | Hardware
+--- | --- | --- | --- | ---
+[v. 1.4.0](https://github.com/ryo-currency/ryo-wallet/releases/latest) | [Ryowebwallet](https://www.ryowebwallet.com/wallet-select) | [v. 0.4.1.0](https://github.com/ryo-currency/ryo-currency/releases/latest) | Developing | Planned
+
+## Research and contributing
+With privacy and security as the core foundation of Ryo, we invest time and effort into security research as well as investigate and analyze issues with the Cryptonote protocol in order to bring true default anonymity for users.
+- [Hiding your IP while using Ryo or other Cryptonotes](https://www.reddit.com/r/ryocurrency/comments/a4mppi/hiding_your_ip_while_using_ryo_or_other/)
+- [Tracing Cryptonote ring signatures using external metadata](https://medium.com/@crypto_ryo/tracing-cryptonote-ring-signatures-using-external-metadata-8e4866810006).
+- [How buying pot with Monero will get you busted — Knacc attack on Cryptonote coins](https://medium.com/@crypto_ryo/how-buying-pot-with-monero-will-get-you-busted-knacc-attack-on-cryptonote-coins-b157cd97e82f).
+- [On-chain tracking of Monero and other Cryptonotes](https://medium.com/@crypto_ryo/on-chain-tracking-of-monero-and-other-cryptonotes-e0afc6752527).
+You can find all write-ups in our [Ryo library](https://ryo-currency.com/library/) on the website.
+
+Although Ryo Currency code in main repository is source available until February 2020, we have contributed back bug fixes and features to Monero project:
+- [Add Unicode input line](https://github.com/monero-project/monero/pull/4390).
+- [Fix for a wallet caching bug](https://github.com/monero-project/monero/pull/4247).
+Loki Project decided to use own version of wallet, based on Ryo Wallet Atom [(libre repository)](https://github.com/ryo-currency/ryo-wallet-libre) as official GUI wallet. Triton Project uses GUI wallet that is based on Ryo Wallet Atom too.
+
## Coin Supply & Emission
-
-- **Total supply**: **80,188,888** coins in 20 years, then **263,000** coins will be emitted yearly to account for inflation.
+- **Total supply**: **88,188,888** coins in 20 years, then **263,000** coins will be emitted yearly to account for inflation.
- More than **80 million coins are available** for community mining.
-- 8,790,000 Ryo coins were burned to get rid of the original Sumokoin premine. Additionally, 100,000 coins were premined and instantly unlocked to Sumokoin devs in 2017.
+- 8,790,000 Ryo coins were burned to get rid of the original Sumokoin premine. (You can check [burned premine keyimages](https://github.com/ryo-currency/ryo-currency/tree/master/utils/burned_premine_keyimages)). Additionally, 100,000 coins were premined and instantly unlocked to Sumokoin devs in 2017. The pre-mined coins have been [frozen/burned](https://github.com/ryo-currency/ryo-currency/blob/917dbb993178bb8a2ea571f214b15adcbb7c708f/src/blockchain_db/blockchain_db.cpp#L364) as announced on [reddit](https://www.reddit.com/r/ryocurrency/comments/8nb8eq/direction_for_ryo/). This can be verified using [those](/doc/verify_premine_burn_instructions.md) instructions.
-The pre-mined coins have been frozen/burned in commit [c3a3cb6](https://github.com/ryo-currency/ryo-emergency/commit/c3a3cb620488e88be7c52e017072261a3063b872)/ [blockchain_db/blockchain_db.cpp#L250-L258](https://github.com/ryo-currency/ryo-emergency/blob/c3a3cb620488e88be7c52e017072261a3063b872/src/blockchain_db/blockchain_db.cpp#L250-L258) as announced on [reddit](https://www.reddit.com/r/ryocurrency/comments/8nb8eq/direction_for_ryo/).
+- After 2 rounds of community debates [(pt1](https://www.reddit.com/r/ryocurrency/comments/8xsyqo/community_debate_lets_talk_about_the_development/e26i1vw/) / [pt2)](https://github.com/ryo-currency/ryo-writeups/blob/master/dev-fund.md) **8,000,000** Ryo coins were introduced as development fund which is located in 2/3 multisig wallet and emitted on weekly basis next 6 years. In an effort to provide transparency to the community on how the development fund is allocated, Ryo dev team built the following [dev-fund explorer page](https://ryo-currency.com/dev-fund/).
- **Coin symbol**: **RYO**
+- **Hash algorithm**: CryptoNight-GPU (ASIC/FPGA/Botnet resistant Proof-Of-Work)
+- **Total supply**: **88,188,888** coins in 20 years (including 8M dev. fund). Then 263,000 coins each year for inflation.
+- **Block time**: **240 seconds** (difficulty is adjusted every block)
- **Coin Units**:
+ 1 nanoRyo = 0.000000001 **RYO** (10-9-_the smallest coin unit_)
+ 1 microRyo = 0.000001 **RYO** (10-6)
+ 1 milliRyo = 0.001 **RYO** (10-3)
-- **Hash algorithm**: CryptoNight Heavy (Proof-Of-Work)
-- **Emission scheme**: Ryo's block reward changes _every 6-months_ according to the following "Camel" distribution*. Our emission scheme is inspired by real-world mining production comparable to crude oil, coal and gas which is often slow at first, accelerated in the next few years before declining and becoming depleted. However, the emission path of Ryo is generally not that far apart from Bitcoin.
-
-
-
-
-
-
-
-\* The emulated algorithm of Ryo block-reward emission can be found in Python and C++ scripts at [scripts](scripts) directory.
-
-## I have Sumokoin, how can i claim my Ryo?
-- You can claim your Ryo, if you had Sumokoin before they forked at block #137500. Ryo Currency as a chain fork kept all the transactions -and thus coins you had in your wallet- up and until Sumokoin forked at block #137500. To further secure your Ryo, we're going to tie the coins to a block after the fork.
-- First, install the latest Ryo wallet. Run it and generate a new wallet. Write down the seeds. Copy the MAIN ADDRESS under the RECEIVE tab. Then from the Ryo gui, click SETTINGS » NEW WALLET and restore your Ryo from the same seeds used for your old Sumokoin wallet in the Ryo GUI.
-- Send all your coins to the new Ryo MAIN ADDRESS you copied before.
-After this, you can safely transact Sumokoin, it's important to first move your Ryo, before you move your Sumokoin.
-- If you are comfortable using the CLI, you can just SWEEP ALL Ryo to yourself instead of all the above.
-
-## About this Project
-
-This is the core implementation of Ryo. It is open source and completely free to use without restrictions, except for those specified in the license agreement below. There are no restrictions on anyone creating an alternative implementation of Ryo that uses the protocol and network in a compatible manner.
-
-## Precompiled binaries
-
-Along with each release you can find our [precompiled binaries](https://github.com/ryo-currency/ryo-currency/releases).
-To verify that the downloaded binaries are created by one of our developer please verify the checksums.
-The authenticity of the checksums can by verified with the [PGP-key's](docs/pgp_keys.md).
-
-## Compiling Ryo from source
-
-### Dependencies
-
-The following table summarizes the tools and libraries required to build. A
-few of the libraries are also included in this repository (marked as
-"Vendored"). By default, the build uses the library installed on the system,
-and ignores the vendored sources. However, if no library is found installed on
-the system, then the vendored source will be built and used. The vendored
-sources are also used for statically-linked builds because distribution
-packages often include only shared library binaries (`.so`) but not static
-library archives (`.a`).
-
-| Dep | Min. version | Vendored | Debian/Ubuntu pkg | Arch pkg | Fedora | Optional | Purpose |
-| ------------ | ------------- | -------- | ------------------ | ------------ | ----------------- | -------- | -------------- |
-| GCC | 4.7.3 | NO | `build-essential` | `base-devel` | `gcc` | NO | |
-| CMake | 3.0.0 | NO | `cmake` | `cmake` | `cmake` | NO | |
-| pkg-config | any | NO | `pkg-config` | `base-devel` | `pkgconf` | NO | |
-| Boost | 1.58 | NO | `libboost-all-dev` | `boost` | `boost-devel` | NO | C++ libraries |
-| OpenSSL | basically any | NO | `libssl-dev` | `openssl` | `openssl-devel` | NO | sha256 sum |
-| libzmq | 3.0.0 | NO | `libzmq3-dev` | `zeromq` | `cppzmq-devel` | NO | ZeroMQ library |
-| libunbound | 1.4.16 | YES | `libunbound-dev` | `unbound` | `unbound-devel` | NO | DNS resolver |
-| libsodium | ? | NO | `libsodium-dev` | ? | `libsodium-devel` | NO | libsodium |
-| libminiupnpc | 2.0 | YES | `libminiupnpc-dev` | `miniupnpc` | `miniupnpc-devel` | YES | NAT punching |
-| libunwind | any | NO | `libunwind8-dev` | `libunwind` | `libunwind-devel` | YES | Stack traces |
-| liblzma | any | NO | `liblzma-dev` | `xz` | `xz-devel` | YES | For libunwind |
-| libreadline | 6.3.0 | NO | `libreadline6-dev` | `readline` | `readline-devel` | YES | Input editing |
-| ldns | 1.6.17 | NO | `libldns-dev` | `ldns` | `ldns-devel` | YES | SSL toolkit |
-| expat | 1.1 | NO | `libexpat1-dev` | `expat` | `expat-devel` | YES | XML parsing |
-| GTest | 1.5 | YES | `libgtest-dev`^ | `gtest` | `gtest-devel` | YES | Test suite |
-| Doxygen | any | NO | `doxygen` | `doxygen` | `doxygen` | YES | Documentation |
-| Graphviz | any | NO | `graphviz` | `graphviz` | `graphviz` | YES | Documentation |
-
-
-[^] On Debian/Ubuntu `libgtest-dev` only includes sources and headers. You must
-build the library binary manually. This can be done with the following command ```sudo apt-get install libgtest-dev && cd /usr/src/gtest && sudo cmake . && sudo make && sudo mv libg* /usr/lib/ ```
-
-### Cloning the repository
-
-Clone recursively to pull-in needed submodule(s):
-
-`$ git clone https://github.com/ryo-currency/ryo-currency.git`
-
-If you already have a repo cloned, initialize and update:
-
-`$ cd ryo-currency`
-
-### Build instructions
-
-Ryo uses the CMake build system and a top-level [Makefile](Makefile) that
-invokes cmake commands as needed.
-
-#### On Linux and OS X
-
-* Install the dependencies
-* Change to the root of the source code directory, change to the most recent release branch, and build:
-
- cd ryo-currency
- git checkout tags/0.2.0
- make
-
- *Optional*: If your machine has several cores and enough memory, enable
- parallel build by running `make -j` instead of `make`. For
- this to be worthwhile, the machine should have one core and about 2GB of RAM
- available per thread.
-
- *Note*: If cmake can not find zmq.hpp file on OS X, installing `zmq.hpp` from
- https://github.com/zeromq/cppzmq to `/usr/local/include` should fix that error.
-
- *Note*: The instructions above will compile the most stable release of the
- Ryo software. If you would like to use and test the most recent software,
- use ```git checkout master```. The master branch may contain updates that are
- both unstable and incompatible with release software, though testing is always
- encouraged.
-
-* The resulting executables can be found in `build/release/bin`
-
-* Add `PATH="$PATH:$HOME/ryo/build/release/bin"` to `.profile`
-
-* Run Ryo with `ryod --detach`
-
-* **Optional**: build and run the test suite to verify the binaries:
-
- make release-test
-
- *NOTE*: `core_tests` test may take a few hours to complete.
-
-* **Optional**: to build binaries suitable for debugging:
-
- make debug
-
-* **Optional**: to build statically-linked binaries:
-
- make release-static
-
-Dependencies need to be built with -fPIC. Static libraries usually aren't, so you may have to build them yourself with -fPIC. Refer to their documentation for how to build them.
-
-* **Optional**: build documentation in `doc/html` (omit `HAVE_DOT=YES` if `graphviz` is not installed):
-
- HAVE_DOT=YES doxygen Doxyfile
-
-#### On the Raspberry Pi
-
-Tested on a Raspberry Pi Zero with a clean install of minimal Raspbian Stretch (2017-09-07 or later) from https://www.raspberrypi.org/downloads/raspbian/. If you are using Raspian Jessie, [please see note in the following section](#note-for-raspbian-jessie-users).
-
-* `apt-get update && apt-get upgrade` to install all of the latest software
-
-* Install the dependencies for Ryo from the 'Debian' column in the table above.
-
-* Enable zram:
-```
- sudo zramctl --find --size=1024M # Note the device name
- sudo mkswap
- sudo swapon
-```
-* Clone ryo and checkout most recent release version:
-```
- git clone https://github.com/ryo-currency/ryo-currency.git
- cd ryo-currency
- git checkout tags/0.2.0
-```
-* Build:
-```
- make release
-```
-* Wait 4-6 hours
-
-* The resulting executables can be found in `build/release/bin`
-
-* Add `PATH="$PATH:$HOME/ryo/build/release/bin"` to `.profile`
-
-* Run Ryo with `ryod --detach`
-
-* You may wish to reduce the size of the swap file after the build has finished, and delete the boost directory from your home directory
-
-#### *Note for Raspbian Jessie users:*
-
-If you are using the older Raspbian Jessie image, compiling Ryo is a bit more complicated. The version of Boost available in the Debian Jessie repositories is too old to use with Ryo, and thus you must compile a newer version yourself. The following explains the extra steps, and has been tested on a Raspberry Pi 2 with a clean install of minimal Raspbian Jessie.
-
-* As before, `apt-get update && apt-get upgrade` to install all of the latest software, and enable zram
-
-```
- sudo zramctl --find --size=1024M # Note the device name
- sudo mkswap
- sudo swapon
-```
-
-* Then, install the dependencies for Ryo except `libunwind` and `libboost-all-dev`
-
-* Install the latest version of boost (this may first require invoking `apt-get remove --purge libboost*` to remove a previous version if you're not using a clean install):
-```
- cd
- wget https://sourceforge.net/projects/boost/files/boost/1.64.0/boost_1_64_0.tar.bz2
- tar xvfo boost_1_64_0.tar.bz2
- cd boost_1_64_0
- ./bootstrap.sh
- sudo ./b2
-```
-* Wait ~8 hours
-```
- sudo ./bjam install
-```
-* Wait ~4 hours
-
-* From here, follow the [general Raspberry Pi instructions](#on-the-raspberry-pi) from the "Clone ryo and checkout most recent release version" step.
-
-#### On Windows:
-
-Binaries for Windows are built on Windows using the MinGW toolchain within
-[MSYS2 environment](http://msys2.github.io). The MSYS2 environment emulates a
-POSIX system. The toolchain runs within the environment and *cross-compiles*
-binaries that can run outside of the environment as a regular Windows
-application.
-
-**Preparing the Build Environment**
-
-* Download and install the [MSYS2 installer](http://msys2.github.io), either the 64-bit or the 32-bit package, depending on your system.
-* Open the MSYS shell via the `MSYS2 Shell` shortcut
-* Update packages using pacman:
-
- pacman -Syuu
-
-* Exit the MSYS shell using Alt+F4
-* Edit the properties for the `MSYS2 Shell` shortcut changing "msys2_shell.bat" to "msys2_shell.cmd -mingw64" for 64-bit builds or "msys2_shell.cmd -mingw32" for 32-bit builds
-* Restart MSYS shell via modified shortcut and update packages again using pacman:
-
- pacman -Syuu
-
-
-* Install dependencies:
-
- To build for 64-bit Windows:
-
- pacman -S mingw-w64-x86_64-toolchain make mingw-w64-x86_64-cmake mingw-w64-x86_64-boost mingw-w64-x86_64-openssl mingw-w64-x86_64-zeromq mingw-w64-x86_64-libsodium
-
- To build for 32-bit Windows:
-
- pacman -S mingw-w64-i686-toolchain make mingw-w64-i686-cmake mingw-w64-i686-boost mingw-w64-i686-openssl mingw-w64-i686-zeromq mingw-w64-i686-libsodium
-
-* Open the MingW shell via `MinGW-w64-Win64 Shell` shortcut on 64-bit Windows
- or `MinGW-w64-Win64 Shell` shortcut on 32-bit Windows. Note that if you are
- running 64-bit Windows, you will have both 64-bit and 32-bit MinGW shells.
-
-**Cloning**
-
-* To git clone, run:
-
- git clone https://github.com/ryo-currency/ryo-currency.git
-
-**Building**
-
-* Change to the cloned directory, run:
-
- cd ryo-currency
-
-* If you would like a specific [version/tag](https://github.com/ryo-currency/ryo-currency/tags), do a git checkout for that version. eg. '0.2.0'. If you dont care about the version and just want binaries from master, skip this step:
-
- git checkout 0.2.0
-
-* If you are on a 64-bit system, run:
-
- make release-static-win64
-
-* If you are on a 32-bit system, run:
-
- make release-static-win32
+- **Emission scheme**: Ryo's block reward changes _every 6-months_ according to the following "Plateau" distribution*. Our emission scheme is inspired by real-world mining production comparable to crude oil, coal and gas which is often slow at first, accelerated in the next few years before declining and becoming depleted. However, the emission path of Ryo is generally not that far apart from Bitcoin. The emission curve for Ryo was one of the final aspects of the code we inherited from Sumokoin that was re-written and had to be even [fixed](https://medium.com/@ryo.currency/fixing-a-broken-emission-curve-818300e145a2) during May 2019 [community debates](https://github.com/ryo-currency/ryo-writeups/blob/master/emission-change-part-two.md).
-* The resulting executables can be found in `build/release/bin`
+
-* **Optional**: to build Windows binaries suitable for debugging on a 64-bit system, run:
+
- make debug-static-win64
-* **Optional**: to build Windows binaries suitable for debugging on a 32-bit system, run:
+## Community
+You can join our [community](https://ryo-currency.com/social) and ask the developers about their perspectives, ask for technical support, and get the latest news
- make debug-static-win32
+## Licensing details
+This is the core implementation of Ryo. It is free to get and modify for your own usage, however, you [can't](https://www.reddit.com/r/ryocurrency/comments/8tc5tg/decision_our_source_code_will_be_sourceavailable) distribute modified copies from this repository.
-* The resulting executables can be found in `build/debug/bin`
+[Ryo-libre](https://github.com/ryo-currency/ryo-libre) is open source and completely free to use version of this repository without restrictions which is updated on yearly basis. There are no restrictions on anyone creating an alternative implementation of Ryo that uses the protocol and network in a compatible manner. [(Read more about Ryo-libre)](https://www.reddit.com/r/ryocurrency/comments/am4g0y/ann_ryolibre_open_source_repository_of_ryo)
-### On FreeBSD:
+Copyright (c) 2019, Ryo Currency Project
-The project can be built from scratch by following instructions for Linux above. If you are running ryo in a jail you need to add the flag: `allow.sysvipc=1` to your jail configuration, otherwise lmdb will throw the error message: `Failed to open lmdb environment: Function not implemented`.
-
-We expect to add Ryo into the ports tree in the near future, which will aid in managing installations using ports or packages.
-
-### On OpenBSD:
-
-#### OpenBSD < 6.2
-
-This has been tested on OpenBSD 5.8.
-
-You will need to add a few packages to your system. `pkg_add db cmake gcc gcc-libs g++ miniupnpc gtest`.
-
-The doxygen and graphviz packages are optional and require the xbase set.
-
-The Boost package has a bug that will prevent librpc.a from building correctly. In order to fix this, you will have to Build boost yourself from scratch. Follow the directions here (under "Building Boost"):
-https://github.com/bitcoin/bitcoin/blob/master/doc/build-openbsd.md
-
-You will have to add the serialization, date_time, and regex modules to Boost when building as they are needed by Ryo.
-
-To build: `env CC=egcc CXX=eg++ CPP=ecpp DEVELOPER_LOCAL_TOOLS=1 BOOST_ROOT=/path/to/the/boost/you/built make release-static-64`
-
-#### OpenBSD >= 6.2
-
-You will need to add a few packages to your system. `pkg_add cmake miniupnpc zeromq libiconv`.
-
-The doxygen and graphviz packages are optional and require the xbase set.
-
-
-Build the Boost library using clang. This guide is derived from: https://github.com/bitcoin/bitcoin/blob/master/doc/build-openbsd.md
-
-We assume you are compiling with a non-root user and you have `doas` enabled.
-
-Note: do not use the boost package provided by OpenBSD, as we are installing boost to `/usr/local`.
-
-```
-# Create boost building directory
-mkdir ~/boost
-cd ~/boost
-
-# Fetch boost source
-ftp -o boost_1_64_0.tar.bz2 https://netcologne.dl.sourceforge.net/project/boost/boost/1.64.0/boost_1_64_0.tar.bz2
-
-# MUST output: (SHA256) boost_1_64_0.tar.bz2: OK
-echo "7bcc5caace97baa948931d712ea5f37038dbb1c5d89b43ad4def4ed7cb683332 boost_1_64_0.tar.bz2" | sha256 -c
-tar xfj boost_1_64_0.tar.bz2
-
-# Fetch and apply boost patches, required for OpenBSD
-ftp -o boost_test_impl_execution_monitor_ipp.patch https://raw.githubusercontent.com/openbsd/ports/bee9e6df517077a7269ff0dfd57995f5c6a10379/devel/boost/patches/patch-boost_test_impl_execution_monitor_ipp
-ftp -o boost_config_platform_bsd_hpp.patch https://raw.githubusercontent.com/openbsd/ports/90658284fb786f5a60dd9d6e8d14500c167bdaa0/devel/boost/patches/patch-boost_config_platform_bsd_hpp
-
-# MUST output: (SHA256) boost_config_platform_bsd_hpp.patch: OK
-echo "1f5e59d1154f16ee1e0cc169395f30d5e7d22a5bd9f86358f738b0ccaea5e51d boost_config_platform_bsd_hpp.patch" | sha256 -c
-# MUST output: (SHA256) boost_test_impl_execution_monitor_ipp.patch: OK
-echo "30cec182a1437d40c3e0bd9a866ab5ddc1400a56185b7e671bb3782634ed0206 boost_test_impl_execution_monitor_ipp.patch" | sha256 -c
-
-cd boost_1_64_0
-patch -p0 < ../boost_test_impl_execution_monitor_ipp.patch
-patch -p0 < ../boost_config_platform_bsd_hpp.patch
-
-# Start building boost
-echo 'using clang : : c++ : "-fvisibility=hidden -fPIC" "" "ar" "strip" "ranlib" "" : ;' > user-config.jam
-./bootstrap.sh --without-icu --with-libraries=chrono,filesystem,program_options,system,thread,test,date_time,regex,serialization,locale --with-toolset=clang
-./b2 toolset=clang cxxflags="-stdlib=libc++" linkflags="-stdlib=libc++" -sICONV_PATH=/usr/local
-doas ./b2 -d0 runtime-link=shared threadapi=pthread threading=multi link=static variant=release --layout=tagged --build-type=complete --user-config=user-config.jam -sNO_BZIP2=1 -sICONV_PATH=/usr/local --prefix=/usr/local install
-```
-
-Build cppzmq
-
-Build the cppzmq bindings.
-
-We assume you are compiling with a non-root user and you have `doas` enabled.
-
-```
-# Create cppzmq building directory
-mkdir ~/cppzmq
-cd ~/cppzmq
-
-# Fetch cppzmq source
-ftp -o cppzmq-4.2.3.tar.gz https://github.com/zeromq/cppzmq/archive/v4.2.3.tar.gz
-
-# MUST output: (SHA256) cppzmq-4.2.3.tar.gz: OK
-echo "3e6b57bf49115f4ae893b1ff7848ead7267013087dc7be1ab27636a97144d373 cppzmq-4.2.3.tar.gz" | sha256 -c
-tar xfz cppzmq-4.2.3.tar.gz
-
-# Start building cppzmq
-cd cppzmq-4.2.3
-mkdir build
-cd build
-cmake ..
-doas make install
-```
-
-Build Ryo: `env DEVELOPER_LOCAL_TOOLS=1 BOOST_ROOT=/usr/local make release-static`
-
-### On Solaris:
-
-The default Solaris linker can't be used, you have to install GNU ld, then run cmake manually with the path to your copy of GNU ld:
-
- mkdir -p build/release
- cd build/release
- cmake -DCMAKE_LINKER=/path/to/ld -D CMAKE_BUILD_TYPE=Release ../..
- cd ../..
-
-Then you can run make as usual.
-
-### On Linux for Android (using docker):
-
- # Build image (select android64.Dockerfile for aarch64)
- cd utils/build_scripts/ && docker build -f android32.Dockerfile -t ryo-android .
- # Create container
- docker create -it --name ryo-android ryo-android bash
- # Get binaries
- docker cp ryo-android:/opt/android/ryo/build/release/bin .
-
-### Building portable statically linked binaries
-
-By default, in either dynamically or statically linked builds, binaries target the specific host processor on which the build happens and are not portable to other processors. Portable binaries can be built using the following targets:
-
-* ```make release-static-linux-x86_64``` builds binaries on Linux on x86_64 portable across POSIX systems on x86_64 processors
-* ```make release-static-linux-i686``` builds binaries on Linux on x86_64 or i686 portable across POSIX systems on i686 processors
-* ```make release-static-linux-armv8``` builds binaries on Linux portable across POSIX systems on armv8 processors
-* ```make release-static-linux-armv7``` builds binaries on Linux portable across POSIX systems on armv7 processors
-* ```make release-static-linux-armv6``` builds binaries on Linux portable across POSIX systems on armv6 processors
-* ```make release-static-win64``` builds binaries on 64-bit Windows portable across 64-bit Windows systems
-* ```make release-static-win32``` builds binaries on 64-bit or 32-bit Windows portable across 32-bit Windows systems
-
-## Installing Ryo from a package
-
-**DISCLAIMER: These packages are not part of this repository or maintained by this project's contributors, and as such, do not go through the same review process to ensure their trustworthiness and security.**
-
-Packages are available for
-
-* Docker
-
- # Build using all available cores
- `docker build -t ryo .`
-
- # or build using a specific number of cores (reduce RAM requirement)
- `docker build --build-arg NPROC=1 -t ryo .`
-
- # either run in foreground
- `docker run -it -v /ryo/chain:/root/.ryo -v /ryo/wallet:/wallet -p 18080:18080 ryo`
-
- # or in background
- `docker run -it -d -v /ryo/chain:/root/.ryo -v /ryo/wallet:/wallet -p 18080:18080 ryo`
-
-Packaging for your favorite distribution would be a welcome contribution!
-
-## Running ryod
-
-The build places the binary in `bin/` sub-directory within the build directory
-from which cmake was invoked (repository root by default). To run in
-foreground:
-
- ./bin/ryod
-
-To list all available options, run `./bin/ryod --help`. Options can be
-specified either on the command line or in a configuration file passed by the
-`--config-file` argument. To specify an option in the configuration file, add
-a line with the syntax `argumentname=value`, where `argumentname` is the name
-of the argument without the leading dashes, for example `log-level=1`.
-
-To run in background:
-
- ./bin/ryod --log-file ryod.log --detach
-
-To run as a systemd service, copy
-[ryod.service](utils/systemd/ryod.service) to `/etc/systemd/system/` and
-[ryod.conf](utils/conf/ryod.conf) to `/etc/`. The [example
-service](utils/systemd/ryod.service) assumes that the user `ryo` exists
-and its home is the data directory specified in the [example
-config](utils/conf/ryod.conf).
-
-If you're on Mac, you may need to add the `--max-concurrency 1` option to
-ryo-wallet-cli, and possibly ryod, if you get crashes refreshing.
-
-## Using Tor
-
-While Ryo isn't made to integrate with Tor, it can be used wrapped with torsocks, by
-setting the following configuration parameters and environment variables:
-
-* `--p2p-bind-ip 127.0.0.1` on the command line or `p2p-bind-ip=127.0.0.1` in
- ryod.conf to disable listening for connections on external interfaces.
-* `--no-igd` on the command line or `no-igd=1` in ryod.conf to disable IGD
- (UPnP port forwarding negotiation), which is pointless with Tor.
-* `DNS_PUBLIC=tcp` or `DNS_PUBLIC=tcp://x.x.x.x` where x.x.x.x is the IP of the
- desired DNS server, for DNS requests to go over TCP, so that they are routed
- through Tor. When IP is not specified, ryod uses the default list of
- servers defined in [src/common/dns_utils.cpp](src/common/dns_utils.cpp).
-* `TORSOCKS_ALLOW_INBOUND=1` to tell torsocks to allow ryod to bind to interfaces
- to accept connections from the wallet. On some Linux systems, torsocks
- allows binding to localhost by default, so setting this variable is only
- necessary to allow binding to local LAN/VPN interfaces to allow wallets to
- connect from remote hosts. On other systems, it may be needed for local wallets
- as well.
-* Do NOT pass `--detach` when running through torsocks with systemd, (see
- [utils/systemd/ryod.service](utils/systemd/ryod.service) for details).
-* If you use the wallet with a Tor daemon via the loopback IP (eg, 127.0.0.1:9050),
- then use `--untrusted-daemon` unless it is your own hidden service.
-
-Example command line to start ryod through Tor:
-
- DNS_PUBLIC=tcp torsocks ryod --p2p-bind-ip 127.0.0.1 --no-igd
-
-### Using Tor on Tails
-
-TAILS ships with a very restrictive set of firewall rules. Therefore, you need
-to add a rule to allow this connection too, in addition to telling torsocks to
-allow inbound connections. Full example:
-
- sudo iptables -I OUTPUT 2 -p tcp -d 127.0.0.1 -m tcp --dport 18081 -j ACCEPT
- DNS_PUBLIC=tcp torsocks ./ryod --p2p-bind-ip 127.0.0.1 --no-igd --rpc-bind-ip 127.0.0.1 \
- --data-dir /home/amnesia/Persistent/your/directory/to/the/blockchain
-
-## Using readline
-
-While `ryod` and `ryo-wallet-cli` do not use readline directly, most of the functionality can be obtained by running them via `rlwrap`. This allows command recall, edit capabilities, etc. It does not give autocompletion without an extra completion file, however. To use rlwrap, simply prepend `rlwrap` to the command line, eg:
-
-`rlwrap bin/ryo-wallet-cli --wallet-file /path/to/wallet`
-
-Note: rlwrap will save things like your seed and private keys, if you supply them on prompt. You may want to not use rlwrap when you use simplewallet to restore from seed, etc.
-
-# Debugging
-
-This section contains general instructions for debugging failed installs or problems encountered with Ryo. First ensure you are running the latest version built from the github repo.
-
-### Obtaining stack traces and core dumps on Unix systems
-
-We generally use the tool `gdb` (GNU debugger) to provide stack trace functionality, and `ulimit` to provide core dumps in builds which crash or segfault.
-
-* To use gdb in order to obtain a stack trace for a build that has stalled:
-
-Run the build.
-
-Once it stalls, enter the following command:
-
-```
-gdb /path/to/ryod `pidof ryod`
-```
-
-Type `thread apply all bt` within gdb in order to obtain the stack trace
-
-* If however the core dumps or segfaults:
-
-Enter `ulimit -c unlimited` on the command line to enable unlimited filesizes for core dumps
-
-Enter `echo core | sudo tee /proc/sys/kernel/core_pattern` to stop cores from being hijacked by other tools
-
-Run the build.
-
-When it terminates with an output along the lines of "Segmentation fault (core dumped)", there should be a core dump file in the same directory as ryod. It may be named just `core`, or `core.xxxx` with numbers appended.
-
-You can now analyse this core dump with `gdb` as follows:
-
-`gdb /path/to/ryod /path/to/dumpfile`
-
-Print the stack trace with `bt`
-
-* To run ryo within gdb:
-
-Type `gdb /path/to/ryod`
-
-Pass command-line options with `--args` followed by the relevant arguments
-
-Type `run` to run ryod
-
-### Analysing memory corruption
-
-We use the tool `valgrind` for this.
-
-Run with `valgrind /path/to/ryod`. It will be slow.
-
-# LMDB
-
-There is an `mdb_stat` command in the LMDB source that can print statistics about the database but it's not routinely built. This can be built with the following command:
-
-`cd ~/ryo/external/db_drivers/liblmdb && make`
-
-The output of `mdb_stat -ea ` will indicate inconsistencies in the blocks, block_heights and block_info table.
+Copyright (c) 2014-2017, The Monero Project
-The output of `mdb_dump -s blocks ` and `mdb_dump -s block_info ` is useful for indicating whether blocks and block_info contain the same keys.
+Copyright (c) 2012-2013, The Cryptonote developers
-These records are dumped as hex data, where the first line is the key and the second line is the data.
+Copyright (c) 2017, Sumokoin.org
diff --git a/contrib/epee/demo/demo_http_server/stdafx.h b/contrib/epee/demo/demo_http_server/stdafx.h
index 6ee6087a..ef268f22 100644
--- a/contrib/epee/demo/demo_http_server/stdafx.h
+++ b/contrib/epee/demo/demo_http_server/stdafx.h
@@ -32,4 +32,5 @@
#define BOOST_FILESYSTEM_VERSION 3
#define ENABLE_RELEASE_LOGGING
-#include "misc_log_ex.h"
+#include "common/gulps.hpp"
+
diff --git a/contrib/epee/demo/demo_levin_server/stdafx.h b/contrib/epee/demo/demo_levin_server/stdafx.h
index 077d9007..1a8bdb53 100644
--- a/contrib/epee/demo/demo_levin_server/stdafx.h
+++ b/contrib/epee/demo/demo_levin_server/stdafx.h
@@ -33,4 +33,5 @@
#define BOOST_FILESYSTEM_VERSION 3
#define ENABLE_RELEASE_LOGGING
#include "log_opt_defs.h"
-#include "misc_log_ex.h"
+#include "common/gulps.hpp"
+
diff --git a/contrib/epee/demo/iface/transport_defs.h b/contrib/epee/demo/iface/transport_defs.h
index b1e3a078..7460c2a3 100644
--- a/contrib/epee/demo/iface/transport_defs.h
+++ b/contrib/epee/demo/iface/transport_defs.h
@@ -10,7 +10,7 @@ struct some_test_subdata
{
std::string m_str;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(some_test_subdata)
KV_SERIALIZE(m_str)
END_KV_SERIALIZE_MAP()
};
@@ -44,7 +44,7 @@ struct some_test_data
epee::serialization::storage_entry m_storage_entry_int;
epee::serialization::storage_entry m_storage_entry_string;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(some_test_data)
KV_SERIALIZE(m_str)
KV_SERIALIZE(m_uint64)
KV_SERIALIZE(m_uint32)
@@ -86,7 +86,7 @@ struct COMMAND_EXAMPLE_1
std::string example_string_data;
some_test_data sub;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(request)
KV_SERIALIZE(example_string_data)
KV_SERIALIZE(sub)
END_KV_SERIALIZE_MAP()
@@ -97,7 +97,7 @@ struct COMMAND_EXAMPLE_1
bool m_success;
std::list subs;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(response)
KV_SERIALIZE(m_success)
KV_SERIALIZE(subs)
END_KV_SERIALIZE_MAP()
@@ -112,7 +112,7 @@ struct COMMAND_EXAMPLE_2
{
std::string example_string_data2;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(request)
KV_SERIALIZE(example_string_data2)
END_KV_SERIALIZE_MAP()
};
@@ -121,7 +121,7 @@ struct COMMAND_EXAMPLE_2
{
bool m_success;
- BEGIN_KV_SERIALIZE_MAP()
+ BEGIN_KV_SERIALIZE_MAP(response)
KV_SERIALIZE(m_success)
END_KV_SERIALIZE_MAP()
};
diff --git a/contrib/epee/include/ado_db_helper.h b/contrib/epee/include/ado_db_helper.h
index cc23bf19..ca047215 100644
--- a/contrib/epee/include/ado_db_helper.h
+++ b/contrib/epee/include/ado_db_helper.h
@@ -34,6 +34,8 @@
#include
#include
+#include "common/gulps.hpp"
+
#define BEGIN_TRY_SECTION() \
try \
{
@@ -44,7 +46,8 @@
} \
catch(const std::exception &ex) \
{ \
- LOG_PRINT_J("DB_ERROR: " << ex.what(), LOG_LEVEL_0); \
+ GULPS_CAT_MAJOR("epee_ado_db_help"); \
+ GULPSF_ERROR("DB_ERROR: {}", ex.what(); \
return ret_val; \
} \
catch(const _com_error &comm_err) \
@@ -53,13 +56,15 @@
std::string descr = string_encoding::convert_to_ansii(pstr ? pstr : TEXT("")); \
const TCHAR *pmessage = comm_err.ErrorMessage(); \
pstr = comm_err.Source(); \
+ GULPS_CAT_MAJOR("epee_ado_db_help"); \
std::string source = string_encoding::convert_to_ansii(pstr ? pstr : TEXT("")); \
- LOG_PRINT_J("COM_ERROR " << mess_where << ":\n\tDescriprion:" << descr << ", \n\t Message: " << string_encoding::convert_to_ansii(pmessage) << "\n\t Source: " << source, LOG_LEVEL_0); \
+ GULPSF_ERROR("COM_ERROR {}:\n\tDescriprion:{}, \n\t Message: {}\n\t Source: {}", mess_where, descr, string_encoding::convert_to_ansii(pmessage), source); \
return ret_val; \
} \
catch(...) \
{ \
- LOG_PRINT_J("..._ERROR: Unknown error.", LOG_LEVEL_0); \
+ GULPS_CAT_MAJOR("epee_ado_db_help"); \
+ GULPS_ERROR("..._ERROR: Unknown error."); \
return ret_val; \
}
@@ -82,6 +87,7 @@ struct profile_entry
class profiler_manager
{
+ GULPS_CAT_MAJOR("epee_ado_db_help");
public:
typedef std::map sqls_map;
profiler_manager() {}
@@ -352,7 +358,7 @@ inline bool select_helper(ADODB::_CommandPtr cmd, table &result_vector)
ADODB::_RecordsetPtr precordset = cmd->Execute(NULL, NULL, NULL);
if(!precordset)
{
- LOG_ERROR("DB_ERROR: cmd->Execute returned NULL!!!");
+ GULPS_ERROR("DB_ERROR: cmd->Execute returned NULL!!!");
return false;
}
@@ -364,7 +370,7 @@ inline bool select_helper(ADODB::_CommandPtr cmd, table &result_vector)
{
if(precordset->MoveFirst()!= S_OK)
{
- LOG_ERROR("DB_ERROR: Filed to move first!!!");
+ GULPS_ERROR("DB_ERROR: Filed to move first!!!");
return false;
}
}
@@ -956,18 +962,18 @@ class per_thread_connection_pool
if(S_OK != conn.CreateInstance(__uuidof(ADODB::Connection)))
{
- LOG_ERROR("Failed to Create, instance, was CoInitialize called ???!");
+ GULPS_ERROR("Failed to Create, instance, was CoInitialize called ???!");
return conn;
}
HRESULT res = conn->Open(_bstr_t(m_connection_string.c_str()), _bstr_t(m_login.c_str()), _bstr_t(m_password.c_str()), NULL);
if(res != S_OK)
{
- LOG_ERROR("Failed to connect do DB, connection str:" << m_connection_string);
+ GULPSF_ERROR("Failed to connect do DB, connection str:{}", m_connection_string);
return conn;
}
CATCH_TRY_SECTION_MESS(conn, "while creating another connection");
- LOG_PRINT("New DB Connection added for threadid=" << ::GetCurrentThreadId(), LOG_LEVEL_0);
+ GULPSF_PRINT("New DB Connection added for threadid={}", ::GetCurrentThreadId());
ado_db_helper::execute_helper(conn, "set enable_seqscan=false;");
return conn;
}
@@ -994,7 +1000,7 @@ class per_thread_connection_pool
HRESULT res = rconn->Open(_bstr_t(m_connection_string.c_str()), _bstr_t(m_login.c_str()), _bstr_t(m_password.c_str()), NULL);
if(res != S_OK)
{
- LOG_PRINT("Failed to restore connection to local AI DB", LOG_LEVEL_1);
+ GULPS_LOG_L1("Failed to restore connection to local AI DB");
return false;
}
CATCH_TRY_SECTION(false);
@@ -1053,7 +1059,7 @@ bool find_or_add_t(const std::string &sql_select_statment, const std::string &sq
template
bool find_or_add_t_multiparametred(const std::string &sql_select_statment, const std::string &sql_insert_statment, OUT default_id_type &id, OUT bool &new_object_added, TParams params, t_conn &c)
{
-
+ GULPS_CAT_MAJOR("epee_ado_db_help");
//CHECK_CONNECTION(false);
new_object_added = false;
@@ -1067,8 +1073,8 @@ bool find_or_add_t_multiparametred(const std::string &sql_select_statment, const
{
//last time try to select
res = select_helper_multiparam(c.get_db_connection(), sql_select_statment, params, result_table);
- CHECK_AND_ASSERT_MES(res, false, "Failed to execute statment: " << sql_select_statment);
- CHECK_AND_ASSERT_MES(result_table.size(), false, "No records returned from statment: " << sql_select_statment);
+ GULPS_CHECK_AND_ASSERT_MES(res, false, "Failed to execute statment: " , sql_select_statment);
+ GULPS_CHECK_AND_ASSERT_MES(result_table.size(), false, "No records returned from statment: " , sql_select_statment);
}
else
{
diff --git a/contrib/epee/include/console_handler.h b/contrib/epee/include/console_handler.h
index 91b2a313..9fdb3095 100644
--- a/contrib/epee/include/console_handler.h
+++ b/contrib/epee/include/console_handler.h
@@ -26,7 +26,6 @@
#pragma once
-#include "misc_log_ex.h"
#include "string_tools.h"
#include
#include
@@ -41,6 +40,8 @@
#include
#include
+#include "common/gulps.hpp"
+
#ifdef HAVE_READLINE
#include "readline_buffer.h"
#endif
@@ -288,6 +289,7 @@ bool empty_commands_handler(t_server *psrv, const std::string &command)
class async_console_handler
{
+ GULPS_CAT_MAJOR("epee_csl_hand");
public:
async_console_handler()
{
@@ -322,14 +324,12 @@ class async_console_handler
color_prompt += " ";
color_prompt += "\001\033[0m\002";
m_stdin_reader.get_readline_buffer().set_prompt(color_prompt);
-#else
- epee::set_console_color(epee::console_color_yellow, true);
- std::cout << prompt;
- if(' ' != prompt.back())
- std::cout << ' ';
- epee::reset_console_color();
- std::cout.flush();
#endif
+
+ if(prompt.back() != ' ')
+ prompt += ' ';
+ gulps::inst().log(gulps::message(gulps::OUT_USER_0, gulps::LEVEL_PRINT, gulps_major_cat::c_str(),
+ "cmd_prompt", __FILE__, __LINE__, std::move(prompt), gulps::COLOR_BOLD_YELLOW, false));
}
}
@@ -357,11 +357,10 @@ class async_console_handler
}
if(!get_line_ret)
{
- MERROR("Failed to read line.");
+ GULPS_ERROR("Failed to read line.");
}
string_tools::trim(command);
-
- LOG_PRINT_L2("Read command: " << command);
+ GULPS_LOG_L2("Read command: ", command);
if(command.empty())
{
continue;
@@ -379,13 +378,13 @@ class async_console_handler
#ifdef HAVE_READLINE
rdln::suspend_readline pause_readline;
#endif
- std::cout << "unknown command: " << command << std::endl;
- std::cout << usage;
+ GULPS_PRINT("unknown command: ", command);
+ GULPS_PRINT(usage);
}
}
catch(const std::exception &ex)
{
- LOG_ERROR("Exception at [console_handler], what=" << ex.what());
+ GULPSF_ERROR("Exception at [console_handler], what={}", ex.what());
}
}
if(exit_handler)
@@ -484,7 +483,7 @@ class command_handler
for(auto &x : m_command_handlers)
{
- ss << x.second.second.first << ENDL;
+ ss << x.second.second.first << "\n";
}
return ss.str();
}
diff --git a/contrib/epee/include/gzip_encoding.h b/contrib/epee/include/gzip_encoding.h
index f0ab5d98..f6166283 100644
--- a/contrib/epee/include/gzip_encoding.h
+++ b/contrib/epee/include/gzip_encoding.h
@@ -106,7 +106,7 @@ class content_encoding_gzip : public i_sub_handler
int flag = Z_SYNC_FLUSH;
int ret = inflate(&m_zstream_in, flag);
- CHECK_AND_ASSERT_MES(ret >= 0 || m_zstream_in.avail_out || m_is_deflate_mode, false, "content_encoding_gzip::update_in() Failed to inflate. err = " << ret);
+ GULPS_CHECK_AND_ASSERT_MES(ret >= 0 || m_zstream_in.avail_out || m_is_deflate_mode, false, "content_encoding_gzip::update_in() Failed to inflate. err = " , ret);
if(Z_STREAM_END == ret)
m_is_stream_ended = true;
@@ -126,7 +126,7 @@ class content_encoding_gzip : public i_sub_handler
ret = inflate(&m_zstream_in, Z_NO_FLUSH);
if(ret != Z_OK)
{
- LOCAL_ASSERT(0);
+ GULPS_LOCAL_ASSERT(0);
m_pre_decode.swap(piece_of_transfer);
return false;
}
@@ -136,7 +136,7 @@ class content_encoding_gzip : public i_sub_handler
ret = inflate(&m_zstream_in, Z_NO_FLUSH);
if(ret != Z_OK)
{
- LOCAL_ASSERT(0);
+ GULPS_LOCAL_ASSERT(0);
m_pre_decode.swap(piece_of_transfer);
return false;
}
diff --git a/contrib/epee/include/include_base_utils.h b/contrib/epee/include/include_base_utils.h
index 3484d842..1e89b0fc 100644
--- a/contrib/epee/include/include_base_utils.h
+++ b/contrib/epee/include/include_base_utils.h
@@ -29,4 +29,4 @@
#define BOOST_FILESYSTEM_VERSION 3
#define ENABLE_RELEASE_LOGGING
-#include "misc_log_ex.h"
+#include "common/gulps.hpp"
diff --git a/contrib/epee/include/math_helper.h b/contrib/epee/include/math_helper.h
index efaf8b9c..27520bfe 100644
--- a/contrib/epee/include/math_helper.h
+++ b/contrib/epee/include/math_helper.h
@@ -26,7 +26,7 @@
#pragma once
-#include
+#include
#include
#include
#include
diff --git a/contrib/epee/include/misc_language.h b/contrib/epee/include/misc_language.h
index 542a036c..64bbb15a 100644
--- a/contrib/epee/include/misc_language.h
+++ b/contrib/epee/include/misc_language.h
@@ -29,6 +29,9 @@
#include
#include
#include
+
+#include "common/gulps.hpp"
+
namespace epee
{
#define STD_TRY_BEGIN() \
@@ -39,12 +42,14 @@ namespace epee
} \
catch(const std::exception &e) \
{ \
- LOG_ERROR("EXCEPTION: " << where_ << ", mes: " << e.what()); \
+ GULPS_CAT_MAJOR("epee_msc_lang"); \
+ GULPSF_ERROR("EXCEPTION: {}, mes: {}", where_, e.what()); \
return ret_val; \
} \
catch(...) \
{ \
- LOG_ERROR("EXCEPTION: " << where_); \
+ GULPS_CAT_MAJOR("epee_msc_lang"); \
+ GULPSF_ERROR("EXCEPTION: {}", where_); \
return ret_val; \
}
diff --git a/contrib/epee/include/misc_log_ex.h b/contrib/epee/include/misc_log_ex.h
deleted file mode 100644
index aa7d80fe..00000000
--- a/contrib/epee/include/misc_log_ex.h
+++ /dev/null
@@ -1,254 +0,0 @@
-// Copyright (c) 2006-2013, Andrey N. Sabelnikov, www.sabelnikov.net
-// All rights reserved.
-//
-// Redistribution and use in source and binary forms, with or without
-// modification, are permitted provided that the following conditions are met:
-// * Redistributions of source code must retain the above copyright
-// notice, this list of conditions and the following disclaimer.
-// * Redistributions in binary form must reproduce the above copyright
-// notice, this list of conditions and the following disclaimer in the
-// documentation and/or other materials provided with the distribution.
-// * Neither the name of the Andrey N. Sabelnikov nor the
-// names of its contributors may be used to endorse or promote products
-// derived from this software without specific prior written permission.
-//
-// THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND
-// ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
-// WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
-// DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER BE LIABLE FOR ANY
-// DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
-// (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
-// LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
-// ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
-// (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
-// SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
-//
-
-#ifndef _MISC_LOG_EX_H_
-#define _MISC_LOG_EX_H_
-
-#include
-
-#include "easylogging++.h"
-
-#define RYO_DEFAULT_LOG_CATEGORY "default"
-#define MAX_LOG_FILE_SIZE 104850000 // 100 MB - 7600 bytes
-
-#define MCFATAL(cat, x) CLOG(FATAL, cat) << x
-#define MCERROR(cat, x) CLOG(ERROR, cat) << x
-#define MCWARNING(cat, x) CLOG(WARNING, cat) << x
-#define MCINFO(cat, x) CLOG(INFO, cat) << x
-#define MCDEBUG(cat, x) CLOG(DEBUG, cat) << x
-#define MCTRACE(cat, x) CLOG(TRACE, cat) << x
-#define MCLOG(level, cat, x) ELPP_WRITE_LOG(el::base::Writer, level, el::base::DispatchAction::NormalLog, cat) << x
-#define MCLOG_FILE(level, cat, x) ELPP_WRITE_LOG(el::base::Writer, level, el::base::DispatchAction::FileOnlyLog, cat) << x
-
-#define MCLOG_COLOR(level, cat, color, x) MCLOG(level, cat, "\033[1;" color "m" << x << "\033[0m")
-#define MCLOG_RED(level, cat, x) MCLOG_COLOR(level, cat, "31", x)
-#define MCLOG_GREEN(level, cat, x) MCLOG_COLOR(level, cat, "32", x)
-#define MCLOG_YELLOW(level, cat, x) MCLOG_COLOR(level, cat, "33", x)
-#define MCLOG_BLUE(level, cat, x) MCLOG_COLOR(level, cat, "34", x)
-#define MCLOG_MAGENTA(level, cat, x) MCLOG_COLOR(level, cat, "35", x)
-#define MCLOG_CYAN(level, cat, x) MCLOG_COLOR(level, cat, "36", x)
-
-#define MLOG_RED(level, x) MCLOG_RED(level, RYO_DEFAULT_LOG_CATEGORY, x)
-#define MLOG_GREEN(level, x) MCLOG_GREEN(level, RYO_DEFAULT_LOG_CATEGORY, x)
-#define MLOG_YELLOW(level, x) MCLOG_YELLOW(level, RYO_DEFAULT_LOG_CATEGORY, x)
-#define MLOG_BLUE(level, x) MCLOG_BLUE(level, RYO_DEFAULT_LOG_CATEGORY, x)
-#define MLOG_MAGENTA(level, x) MCLOG_MAGENTA(level, RYO_DEFAULT_LOG_CATEGORY, x)
-#define MLOG_CYAN(level, x) MCLOG_CYAN(level, RYO_DEFAULT_LOG_CATEGORY, x)
-
-#define MFATAL(x) MCFATAL(RYO_DEFAULT_LOG_CATEGORY, x)
-#define MERROR(x) MCERROR(RYO_DEFAULT_LOG_CATEGORY, x)
-#define MWARNING(x) MCWARNING(RYO_DEFAULT_LOG_CATEGORY, x)
-#define MINFO(x) MCINFO(RYO_DEFAULT_LOG_CATEGORY, x)
-#define MDEBUG(x) MCDEBUG(RYO_DEFAULT_LOG_CATEGORY, x)
-#define MTRACE(x) MCTRACE(RYO_DEFAULT_LOG_CATEGORY, x)
-#define MLOG(level, x) MCLOG(level, RYO_DEFAULT_LOG_CATEGORY, x)
-
-#define MGINFO(x) MCINFO("global", x)
-#define MGINFO_RED(x) MCLOG_RED(el::Level::Info, "global", x)
-#define MGINFO_GREEN(x) MCLOG_GREEN(el::Level::Info, "global", x)
-#define MGINFO_YELLOW(x) MCLOG_YELLOW(el::Level::Info, "global", x)
-#define MGINFO_BLUE(x) MCLOG_BLUE(el::Level::Info, "global", x)
-#define MGINFO_MAGENTA(x) MCLOG_MAGENTA(el::Level::Info, "global", x)
-#define MGINFO_CYAN(x) MCLOG_CYAN(el::Level::Info, "global", x)
-
-#define LOG_ERROR(x) MERROR(x)
-#define LOG_PRINT_L0(x) MWARNING(x)
-#define LOG_PRINT_L1(x) MINFO(x)
-#define LOG_PRINT_L2(x) MDEBUG(x)
-#define LOG_PRINT_L3(x) MTRACE(x)
-#define LOG_PRINT_L4(x) MTRACE(x)
-
-#define _dbg3(x) MTRACE(x)
-#define _dbg2(x) MDEBUG(x)
-#define _dbg1(x) MDEBUG(x)
-#define _info(x) MINFO(x)
-#define _note(x) MDEBUG(x)
-#define _fact(x) MDEBUG(x)
-#define _mark(x) MDEBUG(x)
-#define _warn(x) MWARNING(x)
-#define _erro(x) MERROR(x)
-
-#define MLOG_SET_THREAD_NAME(x) el::Helpers::setThreadName(x)
-
-#ifndef LOCAL_ASSERT
-#include
-#if(defined _MSC_VER)
-#define LOCAL_ASSERT(expr) \
- { \
- if(epee::debug::get_set_enable_assert()) \
- { \
- _ASSERTE(expr); \
- } \
- }
-#else
-#define LOCAL_ASSERT(expr)
-#endif
-
-#endif
-
-std::string mlog_get_default_log_path(const char *default_filename);
-void mlog_configure(const std::string &filename_base, bool console, const std::size_t max_log_file_size = MAX_LOG_FILE_SIZE);
-void mlog_set_categories(const char *categories);
-std::string mlog_get_categories();
-void mlog_set_log_level(int level);
-void mlog_set_log(const char *log);
-
-namespace epee
-{
-namespace debug
-{
-inline bool get_set_enable_assert(bool set = false, bool v = false)
-{
- static bool e = true;
- if(set)
- e = v;
- return e;
-}
-}
-
-#define ENDL std::endl
-
-#define TRY_ENTRY() \
- try \
- {
-#define CATCH_ENTRY(location, return_val) \
- } \
- catch(const std::exception &ex) \
- { \
- (void)(ex); \
- LOG_ERROR("Exception at [" << location << "], what=" << ex.what()); \
- return return_val; \
- } \
- catch(...) \
- { \
- LOG_ERROR("Exception at [" << location << "], generic exception \"...\""); \
- return return_val; \
- }
-
-#define CATCH_ENTRY_L0(lacation, return_val) CATCH_ENTRY(lacation, return_val)
-#define CATCH_ENTRY_L1(lacation, return_val) CATCH_ENTRY(lacation, return_val)
-#define CATCH_ENTRY_L2(lacation, return_val) CATCH_ENTRY(lacation, return_val)
-#define CATCH_ENTRY_L3(lacation, return_val) CATCH_ENTRY(lacation, return_val)
-#define CATCH_ENTRY_L4(lacation, return_val) CATCH_ENTRY(lacation, return_val)
-
-#define ASSERT_MES_AND_THROW(message) \
- { \
- LOG_ERROR(message); \
- std::stringstream ss; \
- ss << message; \
- throw std::runtime_error(ss.str()); \
- }
-#define CHECK_AND_ASSERT_THROW_MES(expr, message) \
- do \
- { \
- if(!(expr)) \
- ASSERT_MES_AND_THROW(message); \
- } while(0)
-
-#ifndef CHECK_AND_ASSERT
-#define CHECK_AND_ASSERT(expr, fail_ret_val) \
- do \
- { \
- if(!(expr)) \
- { \
- LOCAL_ASSERT(expr); \
- return fail_ret_val; \
- }; \
- } while(0)
-#endif
-
-#ifndef CHECK_AND_ASSERT_MES
-#define CHECK_AND_ASSERT_MES(expr, fail_ret_val, message) \
- do \
- { \
- if(!(expr)) \
- { \
- LOG_ERROR(message); \
- return fail_ret_val; \
- }; \
- } while(0)
-#endif
-
-#ifndef CHECK_AND_NO_ASSERT_MES_L
-#define CHECK_AND_NO_ASSERT_MES_L(expr, fail_ret_val, l, message) \
- do \
- { \
- if(!(expr)) \
- { \
- LOG_PRINT_L##l(message); /*LOCAL_ASSERT(expr);*/ \
- return fail_ret_val; \
- }; \
- } while(0)
-#endif
-
-#ifndef CHECK_AND_NO_ASSERT_MES
-#define CHECK_AND_NO_ASSERT_MES(expr, fail_ret_val, message) CHECK_AND_NO_ASSERT_MES_L(expr, fail_ret_val, 0, message)
-#endif
-
-#ifndef CHECK_AND_NO_ASSERT_MES_L1
-#define CHECK_AND_NO_ASSERT_MES_L1(expr, fail_ret_val, message) CHECK_AND_NO_ASSERT_MES_L(expr, fail_ret_val, 1, message)
-#endif
-
-#ifndef CHECK_AND_ASSERT_MES_NO_RET
-#define CHECK_AND_ASSERT_MES_NO_RET(expr, message) \
- do \
- { \
- if(!(expr)) \
- { \
- LOG_ERROR(message); \
- return; \
- }; \
- } while(0)
-#endif
-
-#ifndef CHECK_AND_ASSERT_MES2
-#define CHECK_AND_ASSERT_MES2(expr, message) \
- do \
- { \
- if(!(expr)) \
- { \
- LOG_ERROR(message); \
- }; \
- } while(0)
-#endif
-
-enum console_colors
-{
- console_color_default,
- console_color_white,
- console_color_red,
- console_color_green,
- console_color_blue,
- console_color_cyan,
- console_color_magenta,
- console_color_yellow
-};
-
-bool is_stdout_a_tty();
-void set_console_color(int color, bool bright);
-void reset_console_color();
-}
-#endif //_MISC_LOG_EX_H_
diff --git a/contrib/epee/include/misc_os_dependent.h b/contrib/epee/include/misc_os_dependent.h
index 4c50bcc0..1037ba92 100644
--- a/contrib/epee/include/misc_os_dependent.h
+++ b/contrib/epee/include/misc_os_dependent.h
@@ -23,6 +23,7 @@
// (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
// SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
//
+
#ifdef _WIN32
#include
#endif
@@ -48,6 +49,8 @@
#include
#include
+#include "common/gulps.hpp"
+
#pragma once
namespace epee
{
@@ -92,7 +95,8 @@ inline uint64_t get_tick_count()
inline int call_sys_cmd(const std::string &cmd)
{
- std::cout << "# " << cmd << std::endl;
+ GULPS_CAT_MAJOR("epee_msc_os_dep");
+ GULPS_PRINT("# {}", cmd);
FILE *fp;
//char tstCommand[] ="ls *";
@@ -103,7 +107,7 @@ inline int call_sys_cmd(const std::string &cmd)
fp = popen(cmd.c_str(), "r");
#endif
while(fgets(path, 1000, fp) != NULL)
- std::cout << path;
+ GULPS_PRINT(path);
#if !defined(__GNUC__)
_pclose(fp);
diff --git a/contrib/epee/include/net/abstract_tcp_server.h b/contrib/epee/include/net/abstract_tcp_server.h
index 9a42dbdd..26c3f04e 100644
--- a/contrib/epee/include/net/abstract_tcp_server.h
+++ b/contrib/epee/include/net/abstract_tcp_server.h
@@ -36,8 +36,9 @@
#pragma comment(lib, "Ws2_32.lib")
-#undef RYO_DEFAULT_LOG_CATEGORY
-#define RYO_DEFAULT_LOG_CATEGORY "net"
+#include "common/gulps.hpp"
+
+
namespace epee
{
@@ -56,7 +57,8 @@ class soket_sender : public i_service_endpoint
if(cb != send(m_sock, (char *)ptr, (int)cb, 0))
{
int sock_err = WSAGetLastError();
- LOG_ERROR("soket_sender: Failed to send " << cb << " bytes, Error=" << sock_err);
+ GULPS_CAT_MAJOR("epee_tcp_srv");
+ GULPSF_LOG_ERROR("soket_sender: Failed to send {} bytes, Error={}", cb , sock_err);
return false;
}
return true;
@@ -71,6 +73,7 @@ class soket_sender : public i_service_endpoint
template
class abstract_tcp_server
{
+ GULPS_CAT_MAJOR("epee_tcp_srv");
public:
abstract_tcp_server();
@@ -121,7 +124,7 @@ unsigned __stdcall abstract_tcp_server::ConnectionHandlerProc(void *lp
::CoInitialize(NULL);
- LOG_PRINT("Handler thread STARTED with socket=" << pthread_context->m_socket, LOG_LEVEL_2);
+ GULPSF_LOG_L2("Handler thread STARTED with socket={}", pthread_context->m_socket);
int res = 0;
soket_sender sndr(pthread_context->m_socket);
@@ -133,7 +136,7 @@ unsigned __stdcall abstract_tcp_server::ConnectionHandlerProc(void *lp
std::string ansver;
while((res = recv(pthread_context->m_socket, (char *)buff, 1000, 0)) > 0)
{
- LOG_PRINT("Data in, " << res << " bytes", LOG_LEVEL_3);
+ GULPSF_LOG_L3("Data in, {} bytes", res );
if(!srv.handle_recv(buff, res))
break;
}
@@ -141,7 +144,7 @@ unsigned __stdcall abstract_tcp_server::ConnectionHandlerProc(void *lp
closesocket(pthread_context->m_socket);
abstract_tcp_server *powner = pthread_context->powner;
- LOG_PRINT("Handler thread with socket=" << pthread_context->m_socket << " STOPPED", LOG_LEVEL_2);
+ GULPSF_LOG_L2("Handler thread with socket={} STOPPED", pthread_context->m_socket );
powner->m_connections_lock.lock();
::CloseHandle(pthread_context->m_htread);
pthread_context->powner->m_connections.erase(pthread_context->m_self_it);
@@ -167,7 +170,7 @@ bool abstract_tcp_server::init_server(int port_no)
int err = ::WSAStartup(MAKEWORD(2, 2), &wsad);
if(err != 0 || LOBYTE(wsad.wVersion) != 2 || HIBYTE(wsad.wVersion) != 2)
{
- LOG_ERROR("Could not find a usable WinSock DLL, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"");
+ GULPSF_LOG_ERROR("Could not find a usable WinSock DLL, err = {} \"{}\"", err , socket_errors::get_socket_error_text(err) );
return false;
}
@@ -177,7 +180,7 @@ bool abstract_tcp_server::init_server(int port_no)
if(INVALID_SOCKET == m_listen_socket)
{
err = ::WSAGetLastError();
- LOG_ERROR("Failed to create socket, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"");
+ GULPSF_LOG_ERROR("Failed to create socket, err = {} \"{}\"", err , socket_errors::get_socket_error_text(err) );
return false;
}
@@ -193,7 +196,7 @@ bool abstract_tcp_server::init_server(int port_no)
if(SOCKET_ERROR == err)
{
err = ::WSAGetLastError();
- LOG_PRINT("Failed to Bind, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"", LOG_LEVEL_2);
+ GULPSF_LOG_L2("Failed to Bind, err = {} \"{}\"", err, socket_errors::get_socket_error_text(err));
deinit_server();
return false;
}
@@ -217,7 +220,7 @@ bool abstract_tcp_server::deinit_server()
if(SOCKET_ERROR == res)
{
int err = ::WSAGetLastError();
- LOG_ERROR("Failed to closesocket(), err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"");
+ GULPSF_LOG_ERROR("Failed to closesocket(), err = {} \"{}\"", err , socket_errors::get_socket_error_text(err) );
}
m_listen_socket = INVALID_SOCKET;
}
@@ -226,7 +229,7 @@ bool abstract_tcp_server::deinit_server()
if(SOCKET_ERROR == res)
{
int err = ::WSAGetLastError();
- LOG_ERROR("Failed to WSACleanup(), err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"");
+ GULPSF_LOG_ERROR("Failed to WSACleanup(), err = {} \"{}\"", err , socket_errors::get_socket_error_text(err) );
}
m_initialized = false;
@@ -247,11 +250,11 @@ bool abstract_tcp_server::run_server()
if(SOCKET_ERROR == err)
{
err = ::WSAGetLastError();
- LOG_ERROR("Failed to listen, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"");
+ GULPSF_LOG_ERROR("Failed to listen, err = {} \"{}\"", err , socket_errors::get_socket_error_text(err) );
return false;
}
- LOG_PRINT("Listening port " << m_port << "....", LOG_LEVEL_2);
+ GULPSF_LOG_L2("Listening port {}....", m_port );
while(!m_stop_server)
{
@@ -266,7 +269,7 @@ bool abstract_tcp_server::run_server()
if(!select_res)
continue;
SOCKET new_sock = WSAAccept(m_listen_socket, (sockaddr *)&adr_from, &adr_len, NULL, NULL);
- LOG_PRINT("Accepted connection on socket=" << new_sock, LOG_LEVEL_2);
+ GULPSF_LOG_L2("Accepted connection on socket={}", new_sock);
invoke_connection(new_sock, adr_from.sin_addr.s_addr, adr_from.sin_port);
}
@@ -282,7 +285,7 @@ bool abstract_tcp_server::run_server()
::Sleep(ABSTR_TCP_SRV_WAIT_COUNT_INTERVAL);
wait_count++;
}
- LOG_PRINT("abstract_tcp_server exit with wait count=" << wait_count * ABSTR_TCP_SRV_WAIT_COUNT_INTERVAL << "(max=" << ABSTR_TCP_SRV_WAIT_COUNT_MAX << ")", LOG_LEVEL_0);
+ GULPSF_PRINT("abstract_tcp_server exit with wait count={}(max={})", wait_count * ABSTR_TCP_SRV_WAIT_COUNT_INTERVAL , ABSTR_TCP_SRV_WAIT_COUNT_MAX );
return true;
}
diff --git a/contrib/epee/include/net/abstract_tcp_server2.h b/contrib/epee/include/net/abstract_tcp_server2.h
index 5e3906b5..8ca2aa59 100644
--- a/contrib/epee/include/net/abstract_tcp_server2.h
+++ b/contrib/epee/include/net/abstract_tcp_server2.h
@@ -54,8 +54,7 @@
#include
#include
-#undef RYO_DEFAULT_LOG_CATEGORY
-#define RYO_DEFAULT_LOG_CATEGORY "net"
+
#define ABSTRACT_SERVER_SEND_QUE_MAX_COUNT 1000
@@ -83,6 +82,7 @@ class connection
public i_service_endpoint,
public connection_basic
{
+ GULPS_CAT_MAJOR("epee_tcp_srv");
public:
typedef typename t_protocol_handler::connection_context t_connection_context;
/// Construct a connection with the given io_service.
diff --git a/contrib/epee/include/net/abstract_tcp_server2.inl b/contrib/epee/include/net/abstract_tcp_server2.inl
index b71607ec..257c1f75 100644
--- a/contrib/epee/include/net/abstract_tcp_server2.inl
+++ b/contrib/epee/include/net/abstract_tcp_server2.inl
@@ -30,6 +30,7 @@
// SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
//
+
//#include "net_utils_base.h"
#include "misc_language.h"
#include "net/local_ip.h"
@@ -51,8 +52,9 @@
#include "../../../../src/cryptonote_core/cryptonote_core.h" // e.g. for the send_stop_signal()
-#undef RYO_DEFAULT_LOG_CATEGORY
-#define RYO_DEFAULT_LOG_CATEGORY "net"
+#include "common/gulps.hpp"
+
+
#define DEFAULT_TIMEOUT_MS_LOCAL boost::posix_time::milliseconds(120000) // 2 minutes
#define DEFAULT_TIMEOUT_MS_REMOTE boost::posix_time::milliseconds(10000) // 10 seconds
@@ -83,7 +85,7 @@ connection::connection(boost::asio::io_service &io_service,
m_timer(io_service),
m_local(false)
{
- MDEBUG("test, connection constructor set m_connection_type=" << m_connection_type);
+ GULPSF_LOG_L1("test, connection constructor set m_connection_type={}", m_connection_type);
}
PRAGMA_WARNING_DISABLE_VS(4355)
//---------------------------------------------------------------------------------
@@ -92,11 +94,11 @@ connection::~connection() noexcept(false)
{
if(!m_was_shutdown)
{
- _dbg3("[sock " << socket_.native_handle() << "] Socket destroyed without shutdown.");
+ GULPS_LOG_L2("[sock ", socket_.native_handle() , "] Socket destroyed without shutdown.");
shutdown();
}
- _dbg3("[sock " << socket_.native_handle() << "] Socket destroyed");
+ GULPS_LOG_L2("[sock ", socket_.native_handle(), "] Socket destroyed");
}
//---------------------------------------------------------------------------------
template
@@ -122,7 +124,7 @@ boost::shared_ptr> connection
template
bool connection::start(bool is_income, bool is_multithreaded)
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
// Use safe_shared_from_this, because of this is public method and it can be called on the object being deleted
auto self = safe_shared_from_this();
@@ -133,11 +135,11 @@ bool connection::start(bool is_income, bool is_multithreaded
boost::system::error_code ec;
auto remote_ep = socket_.remote_endpoint(ec);
- CHECK_AND_NO_ASSERT_MES(!ec, false, "Failed to get remote endpoint: " << ec.message() << ':' << ec.value());
- CHECK_AND_NO_ASSERT_MES(remote_ep.address().is_v4(), false, "IPv6 not supported here");
+ GULPS_CHECK_AND_NO_ASSERT_MES(!ec, false, "Failed to get remote endpoint: " , ec.message() , ":" , ec.value());
+ GULPS_CHECK_AND_NO_ASSERT_MES(remote_ep.address().is_v4(), false, "IPv6 not supported here");
auto local_ep = socket_.local_endpoint(ec);
- CHECK_AND_NO_ASSERT_MES(!ec, false, "Failed to get local endpoint: " << ec.message() << ':' << ec.value());
+ GULPS_CHECK_AND_NO_ASSERT_MES(!ec, false, "Failed to get local endpoint: " , ec.message() , ":" , ec.value());
context = boost::value_initialized();
const unsigned long ip_{boost::asio::detail::socket_ops::host_to_network_long(remote_ep.address().to_v4().to_ulong())};
@@ -149,11 +151,11 @@ bool connection::start(bool is_income, bool is_multithreaded
random_uuid = crypto::rand();
context.set_details(random_uuid, epee::net_utils::ipv4_network_address(ip_, remote_ep.port()), is_income);
- _dbg3("[sock " << socket_.native_handle() << "] new connection from " << print_connection_context_short(context) << " to " << local_ep.address().to_string() << ':' << local_ep.port() << ", total sockets objects " << m_ref_sock_count);
+ GULPS_LOG_L3("[sock ", socket_.native_handle(), "] new connection from ", print_connection_context_short(context), " to ", local_ep.address().to_string(), ":", local_ep.port(), ", total sockets objects ", &m_ref_sock_count);
if(m_pfilter && !m_pfilter->is_remote_host_allowed(context.m_remote_address))
{
- _dbg2("[sock " << socket_.native_handle() << "] host denied " << context.m_remote_address.host_str() << ", shutdowning connection");
+ GULPS_LOG_L1("[sock ", socket_.native_handle(), "] host denied " );
close();
return false;
}
@@ -175,7 +177,7 @@ bool connection::start(bool is_income, bool is_multithreaded
boost::asio::detail::socket_option::integer
optionTos(tos);
socket_.set_option(optionTos);
-//_dbg1("Set ToS flag to " << tos);
+//GULPSF_LOG_L1("Set ToS flag to {}", tos);
#endif
boost::asio::ip::tcp::no_delay noDelayOption(false);
@@ -183,72 +185,72 @@ bool connection::start(bool is_income, bool is_multithreaded
return true;
- CATCH_ENTRY_L0("connection::start()", false);
+ GULPS_CATCH_ENTRY_L0("connection::start()", false);
}
//---------------------------------------------------------------------------------
template
bool connection::request_callback()
{
- TRY_ENTRY();
- _dbg2("[" << print_connection_context_short(context) << "] request_callback");
+ GULPS_TRY_ENTRY();
+ GULPSF_LOG_L1("[{}] request_callback", print_connection_context_short(context) );
// Use safe_shared_from_this, because of this is public method and it can be called on the object being deleted
auto self = safe_shared_from_this();
if(!self)
return false;
strand_.post(boost::bind(&connection::call_back_starter, self));
- CATCH_ENTRY_L0("connection::request_callback()", false);
+ GULPS_CATCH_ENTRY_L0("connection::request_callback()", false);
return true;
}
//---------------------------------------------------------------------------------
template
boost::asio::io_service &connection::get_io_service()
{
- return socket_.get_io_service();
+ return GET_IO_SERVICE(socket_);
}
//---------------------------------------------------------------------------------
template
bool connection::add_ref()
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
// Use safe_shared_from_this, because of this is public method and it can be called on the object being deleted
auto self = safe_shared_from_this();
if(!self)
return false;
- //_dbg3("[sock " << socket_.native_handle() << "] add_ref, m_peer_number=" << mI->m_peer_number);
+ //GULPSF_LOG_L2("[sock {}] add_ref, m_peer_number={}", socket_.native_handle() , mI->m_peer_number);
CRITICAL_REGION_LOCAL(self->m_self_refs_lock);
- //_dbg3("[sock " << socket_.native_handle() << "] add_ref 2, m_peer_number=" << mI->m_peer_number);
+ //GULPSF_LOG_L2("[sock {}] add_ref 2, m_peer_number={}", socket_.native_handle() , mI->m_peer_number);
if(m_was_shutdown)
return false;
m_self_refs.push_back(self);
return true;
- CATCH_ENTRY_L0("connection::add_ref()", false);
+ GULPS_CATCH_ENTRY_L0("connection::add_ref()", false);
}
//---------------------------------------------------------------------------------
template
bool connection::release()
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
boost::shared_ptr> back_connection_copy;
- LOG_TRACE_CC(context, "[sock " << socket_.native_handle() << "] release");
+ GULPS_LOG_L2(context, "[sock ", socket_.native_handle() , "] release");
CRITICAL_REGION_BEGIN(m_self_refs_lock);
- CHECK_AND_ASSERT_MES(m_self_refs.size(), false, "[sock " << socket_.native_handle() << "] m_self_refs empty at connection::release() call");
+ GULPS_CHECK_AND_ASSERT_MES(m_self_refs.size(), false, "[sock " , socket_.native_handle() , "] m_self_refs empty at connection::release() call");
//erasing from container without additional copy can cause start deleting object, including m_self_refs
back_connection_copy = m_self_refs.back();
m_self_refs.pop_back();
CRITICAL_REGION_END();
return true;
- CATCH_ENTRY_L0("connection::release()", false);
+ GULPS_CATCH_ENTRY_L0("connection::release()", false);
}
//---------------------------------------------------------------------------------
template
void connection::call_back_starter()
{
- TRY_ENTRY();
- _dbg2("[" << print_connection_context_short(context) << "] fired_callback");
+ GULPS_TRY_ENTRY();
+ GULPSF_LOG_L1("[{}] fired_callback", print_connection_context_short(context) );
m_protocol_handler.handle_qued_callback();
- CATCH_ENTRY_L0("connection::call_back_starter()", void());
+ GULPS_CATCH_ENTRY_L0("connection::call_back_starter()", void());
}
//---------------------------------------------------------------------------------
template
@@ -268,17 +270,16 @@ void connection::save_dbg_log()
address = endpoint.address().to_string();
port = boost::lexical_cast(endpoint.port());
}
- MDEBUG(" connection type " << to_string(m_connection_type) << " "
- << socket_.local_endpoint().address().to_string() << ":" << socket_.local_endpoint().port()
- << " <--> " << address << ":" << port);
+ GULPSF_LOG_L1(" connection type {} {}:{} <--> {}:{}", to_string(m_connection_type) , socket_.local_endpoint().address().to_string() , socket_.local_endpoint().port()
+ , address , port);
}
//---------------------------------------------------------------------------------
template
void connection::handle_read(const boost::system::error_code &e,
std::size_t bytes_transferred)
{
- TRY_ENTRY();
- //_info("[sock " << socket_.native_handle() << "] Async read calledback.");
+ GULPS_TRY_ENTRY();
+ //GULPS_INFO("[sock " << socket_.native_handle() << "] Async read calledback.");
if(!e)
{
@@ -299,7 +300,7 @@ void connection::handle_read(const boost::system::error_code
{
do // keep sleeping if we should sleep
{
- { //_scope_dbg1("CRITICAL_REGION_LOCAL");
+ { //_scopeGULPSF_LOG_L1("CRITICAL_REGION_LOCAL");
CRITICAL_REGION_LOCAL(epee::net_utils::network_throttle_manager::m_lock_get_global_throttle_in);
delay = epee::net_utils::network_throttle_manager::get_global_throttle_in().get_sleep_time_after_tick(bytes_transferred);
}
@@ -314,14 +315,14 @@ void connection::handle_read(const boost::system::error_code
} while(delay > 0);
} // any form of sleeping
- //_info("[sock " << socket_.native_handle() << "] RECV " << bytes_transferred);
+ //GULPS_INFO("[sock " << socket_.native_handle() << "] RECV " << bytes_transferred);
logger_handle_net_read(bytes_transferred);
context.m_last_recv = time(NULL);
context.m_recv_cnt += bytes_transferred;
bool recv_res = m_protocol_handler.handle_recv(buffer_.data(), bytes_transferred);
if(!recv_res)
{
- //_info("[sock " << socket_.native_handle() << "] protocol_want_close");
+ //GULPS_INFO("[sock " << socket_.native_handle() << "] protocol_want_close");
//some error in protocol, protocol handler ask to close connection
boost::interprocess::ipcdetail::atomic_write32(&m_want_close_connection, 1);
@@ -341,15 +342,15 @@ void connection::handle_read(const boost::system::error_code
boost::bind(&connection::handle_read, connection::shared_from_this(),
boost::asio::placeholders::error,
boost::asio::placeholders::bytes_transferred)));
- //_info("[sock " << socket_.native_handle() << "]Async read requested.");
+ //GULPS_INFO("[sock " << socket_.native_handle() << "]Async read requested.");
}
}
else
{
- _dbg3("[sock " << socket_.native_handle() << "] Some not success at read: " << e.message() << ':' << e.value());
+ GULPS_LOG_L2("[sock ", socket_.native_handle(), "] Some not success at read: ", e.message(), ":", e.value());
if(e.value() != 2)
{
- _dbg3("[sock " << socket_.native_handle() << "] Some problems at read: " << e.message() << ':' << e.value());
+ GULPS_LOG_L2("[sock ", socket_.native_handle(), "] Some problems at read: " , e.message(), ":" , e.value());
shutdown();
}
}
@@ -357,17 +358,17 @@ void connection::handle_read(const boost::system::error_code
// means that all shared_ptr references to the connection object will
// disappear and the object will be destroyed automatically after this
// handler returns. The connection class's destructor closes the socket.
- CATCH_ENTRY_L0("connection::handle_read", void());
+ GULPS_CATCH_ENTRY_L0("connection::handle_read", void());
}
//---------------------------------------------------------------------------------
template
bool connection::call_run_once_service_io()
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
if(!m_is_multithreaded)
{
//single thread model, we can wait in blocked call
- size_t cnt = socket_.get_io_service().run_one();
+ size_t cnt = GET_IO_SERVICE(socket_).run_one();
if(!cnt) //service is going to quit
return false;
}
@@ -378,19 +379,19 @@ bool connection::call_run_once_service_io()
//if no handlers were called
//TODO: Maybe we need to have have critical section + event + callback to upper protocol to
//ask it inside(!) critical region if we still able to go in event wait...
- size_t cnt = socket_.get_io_service().poll_one();
+ size_t cnt = GET_IO_SERVICE(socket_).poll_one();
if(!cnt)
misc_utils::sleep_no_w(0);
}
return true;
- CATCH_ENTRY_L0("connection::call_run_once_service_io", false);
+ GULPS_CATCH_ENTRY_L0("connection::call_run_once_service_io", false);
}
//---------------------------------------------------------------------------------
template
bool connection::do_send(const void *ptr, size_t cb)
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
// Use safe_shared_from_this, because of this is public method and it can be called on the object being deleted
auto self = safe_shared_from_this();
@@ -406,7 +407,7 @@ bool connection::do_send(const void *ptr, size_t cb)
const t_safe chunksize_max = chunksize_good * 2;
const bool allow_split = (m_connection_type == e_connection_type_RPC) ? false : true; // do not split RPC data
- CHECK_AND_ASSERT_MES(!(chunksize_max < 0), false, "Negative chunksize_max"); // make sure it is unsigned before removin sign with cast:
+ GULPS_CHECK_AND_ASSERT_MES(!(chunksize_max < 0), false, "Negative chunksize_max"); // make sure it is unsigned before removin sign with cast:
long long unsigned int chunksize_max_unsigned = static_cast(chunksize_max);
if(allow_split && (cb > chunksize_max_unsigned))
@@ -414,7 +415,7 @@ bool connection::do_send(const void *ptr, size_t cb)
{ // LOCK: chunking
epee::critical_region_t send_guard(m_chunking_lock); // *** critical ***
- MDEBUG("do_send() will SPLIT into small chunks, from packet=" << cb << " B for ptr=" << ptr);
+ GULPSF_LOG_L1("do_send() will SPLIT into small chunks, from packet={} B for ptr={}", cb , ptr);
t_safe all = cb; // all bytes to send
t_safe pos = 0; // current sending position
// 01234567890
@@ -430,40 +431,39 @@ bool connection::do_send(const void *ptr, size_t cb)
{
t_safe lenall = all - pos; // length from here to end
t_safe len = std::min(chunksize_good, lenall); // take a smaller part
- CHECK_AND_ASSERT_MES(len <= chunksize_good, false, "len too large");
+ GULPS_CHECK_AND_ASSERT_MES(len <= chunksize_good, false, "len too large");
// pos=8; len=4; all=10; len=3;
- CHECK_AND_ASSERT_MES(!(len < 0), false, "negative len"); // check before we cast away sign:
+ GULPS_CHECK_AND_ASSERT_MES(!(len < 0), false, "negative len"); // check before we cast away sign:
unsigned long long int len_unsigned = static_cast(len);
- CHECK_AND_ASSERT_MES(len > 0, false, "len not strictly positive"); // (redundant)
- CHECK_AND_ASSERT_MES(len_unsigned < std::numeric_limits::max(), false, "Invalid len_unsigned"); // yeap we want strong < then max size, to be sure
+ GULPS_CHECK_AND_ASSERT_MES(len > 0, false, "len not strictly positive"); // (redundant)
+ GULPS_CHECK_AND_ASSERT_MES(len_unsigned < std::numeric_limits::max(), false, "Invalid len_unsigned"); // yeap we want strong < then max size, to be sure
void *chunk_start = ((char *)ptr) + pos;
- MDEBUG("chunk_start=" << chunk_start << " ptr=" << ptr << " pos=" << pos);
- CHECK_AND_ASSERT_MES(chunk_start >= ptr, false, "Pointer wraparound"); // not wrapped around address?
+ GULPSF_LOG_L1("chunk_start={} ptr={} pos={}", chunk_start , ptr , pos);
+ GULPS_CHECK_AND_ASSERT_MES(chunk_start >= ptr, false, "Pointer wraparound"); // not wrapped around address?
//std::memcpy( (void*)buf, chunk_start, len);
- MDEBUG("part of " << lenall << ": pos=" << pos << " len=" << len);
+ GULPSF_LOG_L1("part of {}: pos={} len={}", lenall , pos , len);
bool ok = do_send_chunk(chunk_start, len); // <====== ***
all_ok = all_ok && ok;
if(!all_ok)
{
- MDEBUG("do_send() DONE ***FAILED*** from packet=" << cb << " B for ptr=" << ptr);
- MDEBUG("do_send() SEND was aborted in middle of big package - this is mostly harmless "
- << " (e.g. peer closed connection) but if it causes trouble tell us at https://github.com/ryo-currency/ryo. " << cb);
+ GULPSF_LOG_L1("do_send() DONE ***FAILED*** from packet={} B for ptr={}", cb , ptr);
+ GULPSF_LOG_L1("do_send() SEND was aborted in middle of big package - this is mostly harmless (e.g. peer closed connection) but if it causes trouble tell us at https://github.com/ryo-currency/ryo. {}", cb);
return false; // partial failure in sending
}
pos = pos + len;
- CHECK_AND_ASSERT_MES(pos > 0, false, "pos <= 0");
+ GULPS_CHECK_AND_ASSERT_MES(pos > 0, false, "pos <= 0");
// (in catch block, or uniq pointer) delete buf;
} // each chunk
- MDEBUG("do_send() DONE SPLIT from packet=" << cb << " B for ptr=" << ptr);
+ GULPSF_LOG_L1("do_send() DONE SPLIT from packet={} B for ptr={}", cb , ptr);
- MDEBUG("do_send() m_connection_type = " << m_connection_type);
+ GULPSF_LOG_L1("do_send() m_connection_type = {}", m_connection_type);
return all_ok; // done - e.g. queued - all the chunks of current do_send call
} // LOCK: chunking
@@ -473,14 +473,14 @@ bool connection::do_send(const void *ptr, size_t cb)
return do_send_chunk(ptr, cb); // just send as 1 big chunk
}
- CATCH_ENTRY_L0("connection::do_send", false);
+ GULPS_CATCH_ENTRY_L0("connection::do_send", false);
} // do_send()
//---------------------------------------------------------------------------------
template
bool connection::do_send_chunk(const void *ptr, size_t cb)
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
// Use safe_shared_from_this, because of this is public method and it can be called on the object being deleted
auto self = safe_shared_from_this();
if(!self)
@@ -493,7 +493,7 @@ bool connection::do_send_chunk(const void *ptr, size_t cb)
context.m_current_speed_up = m_throttle_speed_out.get_current_speed();
}
- //_info("[sock " << socket_.native_handle() << "] SEND " << cb);
+ //GULPS_INFO("[sock " << socket_.native_handle() << "] SEND " << cb);
context.m_last_send = time(NULL);
context.m_send_cnt += cb;
//some data should be wrote to stream
@@ -511,20 +511,20 @@ bool connection::do_send_chunk(const void *ptr, size_t cb)
retry++;
/* if ( ::cryptonote::core::get_is_stopping() ) { // TODO re-add fast stop
- _fact("ABORT queue wait due to stopping");
+ GULPS_LOG_L1("ABORT queue wait due to stopping");
return false; // aborted
}*/
long int ms = 250 + (rand() % 50);
- MDEBUG("Sleeping because QUEUE is FULL, in " << __FUNCTION__ << " for " << ms << " ms before packet_size=" << cb); // XXX debug sleep
+ GULPSF_LOG_L1("Sleeping because QUEUE is FULL, in {} for {} ms before packet_size={}", __FUNCTION__ , ms , cb); // XXX debug sleep
m_send_que_lock.unlock();
boost::this_thread::sleep(boost::posix_time::milliseconds(ms));
m_send_que_lock.lock();
- _dbg1("sleep for queue: " << ms);
+ GULPSF_LOG_L1("sleep for queue: {}", ms);
if(retry > retry_limit)
{
- MWARNING("send que size is more than ABSTRACT_SERVER_SEND_QUE_MAX_COUNT(" << ABSTRACT_SERVER_SEND_QUE_MAX_COUNT << "), shutting down connection");
+ GULPSF_WARN("send que size is more than ABSTRACT_SERVER_SEND_QUE_MAX_COUNT({}), shutting down connection", ABSTRACT_SERVER_SEND_QUE_MAX_COUNT );
shutdown();
return false;
}
@@ -536,42 +536,42 @@ bool connection::do_send_chunk(const void *ptr, size_t cb)
if(m_send_que.size() > 1)
{ // active operation should be in progress, nothing to do, just wait last operation callback
auto size_now = cb;
- MDEBUG("do_send() NOW just queues: packet=" << size_now << " B, is added to queue-size=" << m_send_que.size());
+ GULPSF_LOG_L1("do_send() NOW just queues: packet={} B, is added to queue-size={}", size_now , m_send_que.size());
//do_send_handler_delayed( ptr , size_now ); // (((H))) // empty function
- LOG_TRACE_CC(context, "[sock " << socket_.native_handle() << "] Async send requested " << m_send_que.front().size());
+ GULPS_LOG_L2(context, "[sock ", socket_.native_handle(), "] Async send requested ", m_send_que.front().size());
}
else
{ // no active operation
if(m_send_que.size() != 1)
{
- _erro("Looks like no active operations, but send que size != 1!!");
+ GULPS_ERROR("Looks like no active operations, but send que size != 1!!");
return false;
}
auto size_now = m_send_que.front().size();
- MDEBUG("do_send() NOW SENSD: packet=" << size_now << " B");
+ GULPSF_LOG_L1("do_send() NOW SENSD: packet={} B", size_now );
if(speed_limit_is_enabled())
do_send_handler_write(ptr, size_now); // (((H)))
- CHECK_AND_ASSERT_MES(size_now == m_send_que.front().size(), false, "Unexpected queue size");
+ GULPS_CHECK_AND_ASSERT_MES(size_now == m_send_que.front().size(), false, "Unexpected queue size");
reset_timer(get_default_time(), false);
boost::asio::async_write(socket_, boost::asio::buffer(m_send_que.front().data(), size_now),
//strand_.wrap(
boost::bind(&connection::handle_write, self, _1, _2)
//)
);
- //_dbg3("(chunk): " << size_now);
+ //GULPSF_LOG_L2("(chunk): {}", size_now);
//logger_handle_net_write(size_now);
- //_info("[sock " << socket_.native_handle() << "] Async send requested " << m_send_que.front().size());
+ //GULPS_INFO("[sock " << socket_.native_handle() << "] Async send requested " << m_send_que.front().size());
}
//do_send_handler_stop( ptr , cb ); // empty function
return true;
- CATCH_ENTRY_L0("connection::do_send", false);
+ GULPS_CATCH_ENTRY_L0("connection::do_send", false);
} // do_send_chunk
//---------------------------------------------------------------------------------
template
@@ -598,11 +598,11 @@ void connection::reset_timer(boost::posix_time::milliseconds
{
if(m_connection_type != e_connection_type_RPC)
return;
- MTRACE("Setting " << ms << " expiry");
+ GULPS_LOG_L2("Setting ", ms, " expiry");
auto self = safe_shared_from_this();
if(!self)
{
- MERROR("Resetting timer on a dead object");
+ GULPS_ERROR("Resetting timer on a dead object");
return;
}
if(add)
@@ -611,7 +611,7 @@ void connection::reset_timer(boost::posix_time::milliseconds
m_timer.async_wait([=](const boost::system::error_code &ec) {
if(ec == boost::asio::error::operation_aborted)
return;
- MDEBUG(context << "connection timeout, closing");
+ GULPS_LOG_L1(context, "connection timeout, closing");
self->close();
});
}
@@ -631,8 +631,8 @@ bool connection::shutdown()
template
bool connection::close()
{
- TRY_ENTRY();
- //_info("[sock " << socket_.native_handle() << "] Que Shutdown called.");
+ GULPS_TRY_ENTRY();
+ //GULPS_INFO("[sock " << socket_.native_handle() << "] Que Shutdown called.");
m_timer.cancel();
size_t send_que_size = 0;
CRITICAL_REGION_BEGIN(m_send_que_lock);
@@ -645,7 +645,7 @@ bool connection::close()
}
return true;
- CATCH_ENTRY_L0("connection::close", false);
+ GULPS_CATCH_ENTRY_L0("connection::close", false);
}
//---------------------------------------------------------------------------------
template
@@ -657,12 +657,12 @@ bool connection::cancel()
template
void connection::handle_write(const boost::system::error_code &e, size_t cb)
{
- TRY_ENTRY();
- LOG_TRACE_CC(context, "[sock " << socket_.native_handle() << "] Async send calledback " << cb);
+ GULPS_TRY_ENTRY();
+ GULPS_LOG_L2(context, "[sock ", socket_.native_handle(), "] Async send calledback ", cb);
if(e)
{
- _dbg1("[sock " << socket_.native_handle() << "] Some problems at write: " << e.message() << ':' << e.value());
+ GULPS_LOG_L1("[sock ", socket_.native_handle(), "] Some problems at write: ", e.message(), ":", e.value());
shutdown();
return;
}
@@ -678,7 +678,7 @@ void connection::handle_write(const boost::system::error_cod
CRITICAL_REGION_BEGIN(m_send_que_lock);
if(m_send_que.empty())
{
- _erro("[sock " << socket_.native_handle() << "] m_send_que.size() == 0 at handle_write!");
+ GULPS_ERROR("[sock ", socket_.native_handle(), "], m_send_que.size() == 0 at handle_write!");
return;
}
@@ -695,17 +695,16 @@ void connection::handle_write(const boost::system::error_cod
//have more data to send
reset_timer(get_default_time(), false);
auto size_now = m_send_que.front().size();
- MDEBUG("handle_write() NOW SENDS: packet=" << size_now << " B"
- << ", from queue size=" << m_send_que.size());
+ GULPS_LOG_L1("handle_write NOW SENDS: packet=", size_now, " B, from queue size=", m_send_que.size());
if(speed_limit_is_enabled())
do_send_handler_write_from_queue(e, m_send_que.front().size(), m_send_que.size()); // (((H)))
- CHECK_AND_ASSERT_MES(size_now == m_send_que.front().size(), void(), "Unexpected queue size");
+ GULPS_CHECK_AND_ASSERT_MES(size_now == m_send_que.front().size(), void(), "Unexpected queue size");
boost::asio::async_write(socket_, boost::asio::buffer(m_send_que.front().data(), size_now),
// strand_.wrap(
boost::bind(&connection::handle_write, connection::shared_from_this(), _1, _2)
// )
);
- //_dbg3("(normal)" << size_now);
+ //GULPSF_LOG_L2("(normal){}", size_now);
}
CRITICAL_REGION_END();
@@ -713,7 +712,7 @@ void connection::handle_write(const boost::system::error_cod
{
shutdown();
}
- CATCH_ENTRY_L0("connection::handle_write", void());
+ GULPS_CATCH_ENTRY_L0("connection::handle_write", void());
}
//---------------------------------------------------------------------------------
@@ -721,7 +720,7 @@ template
void connection::setRpcStation()
{
m_connection_type = e_connection_type_RPC;
- MDEBUG("set m_connection_type = RPC ");
+ GULPS_LOG_L1("set m_connection_type = RPC ");
}
template
@@ -779,7 +778,7 @@ void boosted_tcp_server::create_server_type_map()
template
bool boosted_tcp_server::init_server(uint32_t port, const std::string address)
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
m_stop_signal_sent = false;
m_port = port;
m_address = address;
@@ -793,7 +792,7 @@ bool boosted_tcp_server::init_server(uint32_t port, const st
acceptor_.listen();
boost::asio::ip::tcp::endpoint binded_endpoint = acceptor_.local_endpoint();
m_port = binded_endpoint.port();
- MDEBUG("start accept");
+ GULPS_LOG_L1("start accept");
new_connection_.reset(new connection(io_service_, m_config, m_sock_count, m_sock_number, m_pfilter, m_connection_type));
acceptor_.async_accept(new_connection_->socket(),
boost::bind(&boosted_tcp_server::handle_accept, this,
@@ -803,12 +802,12 @@ bool boosted_tcp_server::init_server(uint32_t port, const st
}
catch(const std::exception &e)
{
- MFATAL("Error starting server: " << e.what());
+ GULPS_ERROR("Error starting server: ", e.what());
return false;
}
catch(...)
{
- MFATAL("Error starting server");
+ GULPS_ERROR("Error starting server");
return false;
}
}
@@ -822,7 +821,7 @@ bool boosted_tcp_server::init_server(const std::string port,
if(port.size() && !string_tools::get_xtype_from_string(p, port))
{
- MERROR("Failed to convert port no = " << port);
+ GULPSF_ERROR("Failed to convert port no = {}", port);
return false;
}
return this->init_server(p, address);
@@ -832,12 +831,12 @@ POP_WARNINGS
template
bool boosted_tcp_server::worker_thread()
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
uint32_t local_thr_index = boost::interprocess::ipcdetail::atomic_inc32(&m_thread_index);
std::string thread_name = std::string("[") + m_thread_name_prefix;
thread_name += boost::to_string(local_thr_index) + "]";
- MLOG_SET_THREAD_NAME(thread_name);
- // _fact("Thread name: " << m_thread_name_prefix);
+ GULPS_SET_THREAD_NAME(thread_name);
+ // GULPS_LOG_L1("Thread name: ", m_thread_name_prefix);
while(!m_stop_signal_sent)
{
try
@@ -846,16 +845,16 @@ bool boosted_tcp_server::worker_thread()
}
catch(const std::exception &ex)
{
- _erro("Exception at server worker thread, what=" << ex.what());
+ GULPS_ERROR("Exception at server worker thread, what=", ex.what());
}
catch(...)
{
- _erro("Exception at server worker thread, unknown execption");
+ GULPS_ERROR("Exception at server worker thread, unknown execption");
}
}
- //_info("Worker thread finished");
+ //GULPS_INFO("Worker thread finished");
return true;
- CATCH_ENTRY_L0("boosted_tcp_server::worker_thread", false);
+ GULPS_CATCH_ENTRY_L0("boosted_tcp_server::worker_thread", false);
}
//---------------------------------------------------------------------------------
template
@@ -866,7 +865,7 @@ void boosted_tcp_server::set_threads_prefix(const std::strin
if(it == server_type_map.end())
throw std::runtime_error("Unknown prefix/server type:" + std::string(prefix_name));
auto connection_type = it->second; // the value of type
- MINFO("Set server type to: " << connection_type << " from name: " << m_thread_name_prefix << ", prefix_name = " << prefix_name);
+ GULPSF_INFO("Set server type to: {} from name: {}, prefix_name = {}", connection_type , m_thread_name_prefix , prefix_name);
}
//---------------------------------------------------------------------------------
template
@@ -878,10 +877,10 @@ void boosted_tcp_server::set_connection_filter(i_connection_
template
bool boosted_tcp_server::run_server(size_t threads_count, bool wait, const boost::thread::attributes &attrs)
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
m_threads_count = threads_count;
m_main_thread_id = boost::this_thread::get_id();
- MLOG_SET_THREAD_NAME("[SRV_MAIN]");
+ GULPS_SET_THREAD_NAME("[SRV_MAIN]");
while(!m_stop_signal_sent)
{
@@ -891,51 +890,51 @@ bool boosted_tcp_server::run_server(size_t threads_count, bo
{
boost::shared_ptr thread(new boost::thread(
attrs, boost::bind(&boosted_tcp_server::worker_thread, this)));
- _note("Run server thread name: " << m_thread_name_prefix);
+ GULPS_LOG_L1("Run server thread name: ", m_thread_name_prefix);
m_threads.push_back(thread);
}
CRITICAL_REGION_END();
// Wait for all threads in the pool to exit.
if(wait)
{
- _fact("JOINING all threads");
+ GULPS_LOG_L1("JOINING all threads");
for(std::size_t i = 0; i < m_threads.size(); ++i)
{
m_threads[i]->join();
}
- _fact("JOINING all threads - almost");
+ GULPS_LOG_L1("JOINING all threads - almost");
m_threads.clear();
- _fact("JOINING all threads - DONE");
+ GULPS_LOG_L1("JOINING all threads - DONE");
}
else
{
- _dbg1("Reiniting OK.");
+ GULPS_LOG_L1("Reiniting OK.");
return true;
}
if(wait && !m_stop_signal_sent)
{
//some problems with the listening socket ?..
- _dbg1("Net service stopped without stop request, restarting...");
+ GULPS_LOG_L1("Net service stopped without stop request, restarting...");
if(!this->init_server(m_port, m_address))
{
- _dbg1("Reiniting service failed, exit.");
+ GULPS_LOG_L1("Reiniting service failed, exit.");
return false;
}
else
{
- _dbg1("Reiniting OK.");
+ GULPS_LOG_L1("Reiniting OK.");
}
}
}
return true;
- CATCH_ENTRY_L0("boosted_tcp_server::run_server", false);
+ GULPS_CATCH_ENTRY_L0("boosted_tcp_server::run_server", false);
}
//---------------------------------------------------------------------------------
template
bool boosted_tcp_server::is_thread_worker()
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
CRITICAL_REGION_LOCAL(m_threads_lock);
BOOST_FOREACH(boost::shared_ptr &thp, m_threads)
{
@@ -945,31 +944,31 @@ bool boosted_tcp_server::is_thread_worker()
if(m_threads_count == 1 && boost::this_thread::get_id() == m_main_thread_id)
return true;
return false;
- CATCH_ENTRY_L0("boosted_tcp_server::is_thread_worker", false);
+ GULPS_CATCH_ENTRY_L0("boosted_tcp_server::is_thread_worker", false);
}
//---------------------------------------------------------------------------------
template
bool boosted_tcp_server::timed_wait_server_stop(uint64_t wait_mseconds)
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
boost::chrono::milliseconds ms(wait_mseconds);
for(std::size_t i = 0; i < m_threads.size(); ++i)
{
if(m_threads[i]->joinable() && !m_threads[i]->try_join_for(ms))
{
- _dbg1("Interrupting thread " << m_threads[i]->native_handle());
+ GULPS_LOG_L1("Interrupting thread ", m_threads[i]->get_id());
m_threads[i]->interrupt();
}
}
return true;
- CATCH_ENTRY_L0("boosted_tcp_server::timed_wait_server_stop", false);
+ GULPS_CATCH_ENTRY_L0("boosted_tcp_server::timed_wait_server_stop", false);
}
//---------------------------------------------------------------------------------
template
void boosted_tcp_server::send_stop_signal()
{
m_stop_signal_sent = true;
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
connections_mutex.lock();
for(auto &c : connections_)
{
@@ -978,7 +977,7 @@ void boosted_tcp_server::send_stop_signal()
connections_.clear();
connections_mutex.unlock();
io_service_.stop();
- CATCH_ENTRY_L0("boosted_tcp_server::send_stop_signal()", void());
+ GULPS_CATCH_ENTRY_L0("boosted_tcp_server::send_stop_signal()", void());
}
//---------------------------------------------------------------------------------
template
@@ -990,13 +989,13 @@ bool boosted_tcp_server::is_stop_signal_sent()
template
void boosted_tcp_server::handle_accept(const boost::system::error_code &e)
{
- MDEBUG("handle_accept");
- TRY_ENTRY();
+ GULPS_LOG_L1("handle_accept");
+ GULPS_TRY_ENTRY();
if(!e)
{
if(m_connection_type == e_connection_type_RPC)
{
- MDEBUG("New server for RPC connections");
+ GULPS_LOG_L1("New server for RPC connections");
new_connection_->setRpcStation(); // hopefully this is not needed actually
}
connection_ptr conn(std::move(new_connection_));
@@ -1013,20 +1012,20 @@ void boosted_tcp_server::handle_accept(const boost::system::
}
else
{
- _erro("Some problems at accept: " << e.message() << ", connections_count = " << m_sock_count);
+ GULPSF_ERROR("Some problems at accept: {}, connections_count = {}", e.message() , m_sock_count);
}
- CATCH_ENTRY_L0("boosted_tcp_server::handle_accept", void());
+ GULPS_CATCH_ENTRY_L0("boosted_tcp_server::handle_accept", void());
}
//---------------------------------------------------------------------------------
template
bool boosted_tcp_server::connect(const std::string &adr, const std::string &port, uint32_t conn_timeout, t_connection_context &conn_context, const std::string &bind_ip)
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
connection_ptr new_connection_l(new connection(io_service_, m_config, m_sock_count, m_sock_number, m_pfilter, m_connection_type));
connections_mutex.lock();
connections_.insert(new_connection_l);
- MDEBUG("connections_ size now " << connections_.size());
+ GULPSF_LOG_L1("connections_ size now {}", connections_.size());
connections_mutex.unlock();
epee::misc_utils::auto_scope_leave_caller scope_exit_handler = epee::misc_utils::create_scope_leave_handler([&]() { CRITICAL_REGION_LOCAL(connections_mutex); connections_.erase(new_connection_l); });
boost::asio::ip::tcp::socket &sock_ = new_connection_l->socket();
@@ -1038,7 +1037,7 @@ bool boosted_tcp_server::connect(const std::string &adr, con
boost::asio::ip::tcp::resolver::iterator end;
if(iterator == end)
{
- _erro("Failed to resolve " << adr);
+ GULPSF_ERROR("Failed to resolve {}", adr);
return false;
}
//////////////////////////////////////////////////////////////////////////
@@ -1091,7 +1090,7 @@ bool boosted_tcp_server::connect(const std::string &adr, con
{
//timeout
sock_.close();
- _dbg3("Failed to connect to " << adr << ":" << port << ", because of timeout (" << conn_timeout << ")");
+ GULPSF_LOG_L2("Failed to connect to {}:{}, because of timeout ({})", adr , port , conn_timeout );
return false;
}
}
@@ -1099,13 +1098,13 @@ bool boosted_tcp_server::connect(const std::string &adr, con
if(ec || !sock_.is_open())
{
- _dbg3("Some problems at connect, message: " << ec.message());
+ GULPSF_LOG_L2("Some problems at connect, message: {}", ec.message());
if(sock_.is_open())
sock_.close();
return false;
}
- _dbg3("Connected success to " << adr << ':' << port);
+ GULPSF_LOG_L2("Connected success to {}:{}", adr , port);
// start adds the connection to the config object's list, so we don't need to have it locally anymore
connections_mutex.lock();
@@ -1119,25 +1118,25 @@ bool boosted_tcp_server::connect(const std::string &adr, con
}
else
{
- _erro("[sock " << new_connection_l->socket().native_handle() << "] Failed to start connection, connections_count = " << m_sock_count);
+ GULPSF_ERROR("[sock {}] Failed to start connection, connections_count = {}", new_connection_l->socket().native_handle() , m_sock_count);
}
new_connection_l->save_dbg_log();
return r;
- CATCH_ENTRY_L0("boosted_tcp_server::connect", false);
+ GULPS_CATCH_ENTRY_L0("boosted_tcp_server::connect", false);
}
//---------------------------------------------------------------------------------
template
template
bool boosted_tcp_server::connect_async(const std::string &adr, const std::string &port, uint32_t conn_timeout, const t_callback &cb, const std::string &bind_ip)
{
- TRY_ENTRY();
+ GULPS_TRY_ENTRY();
connection_ptr new_connection_l(new connection(io_service_, m_config, m_sock_count, m_sock_number, m_pfilter, m_connection_type));
connections_mutex.lock();
connections_.insert(new_connection_l);
- MDEBUG("connections_ size now " << connections_.size());
+ GULPSF_LOG_L1("connections_ size now {}", connections_.size());
connections_mutex.unlock();
epee::misc_utils::auto_scope_leave_caller scope_exit_handler = epee::misc_utils::create_scope_leave_handler([&]() { CRITICAL_REGION_LOCAL(connections_mutex); connections_.erase(new_connection_l); });
boost::asio::ip::tcp::socket &sock_ = new_connection_l->socket();
@@ -1149,7 +1148,7 @@ bool boosted_tcp_server::connect_async(const std::string &ad
boost::asio::ip::tcp::resolver::iterator end;
if(iterator == end)
{
- _erro("Failed to resolve " << adr);
+ GULPSF_ERROR("Failed to resolve {}", adr);
return false;
}
//////////////////////////////////////////////////////////////////////////
@@ -1168,7 +1167,7 @@ bool boosted_tcp_server::connect_async(const std::string &ad
sh_deadline->async_wait([=](const boost::system::error_code &error) {
if(error != boost::asio::error::operation_aborted)
{
- _dbg3("Failed to connect to " << adr << ':' << port << ", because of timeout (" << conn_timeout << ")");
+ GULPSF_LOG_L2("Failed to connect to {}:{}, because of timeout ({})", adr , port , conn_timeout );
new_connection_l->socket().close();
}
});
@@ -1185,7 +1184,7 @@ bool boosted_tcp_server::connect_async(const std::string &ad
}
else
{
- _dbg3("[sock " << new_connection_l->socket().native_handle() << "] Connected success to " << adr << ':' << port << " from " << lep.address().to_string() << ':' << lep.port());
+ GULPSF_LOG_L2("[sock {}] Connected success to {}:{} from {}:{}", new_connection_l->socket().native_handle() , adr , port , lep.address().to_string() , lep.port());
// start adds the connection to the config object's list, so we don't need to have it locally anymore
connections_mutex.lock();
@@ -1199,19 +1198,19 @@ bool boosted_tcp_server::connect_async(const std::string &ad
}
else
{
- _dbg3("[sock " << new_connection_l->socket().native_handle() << "] Failed to start connection to " << adr << ':' << port);
+ GULPSF_LOG_L2("[sock {}] Failed to start connection to {}:{}", new_connection_l->socket().native_handle() , adr , port);
cb(conn_context, boost::asio::error::fault);
}
}
}
else
{
- _dbg3("[sock " << new_connection_l->socket().native_handle() << "] Failed to connect to " << adr << ':' << port << " from " << lep.address().to_string() << ':' << lep.port() << ": " << ec_.message() << ':' << ec_.value());
+ GULPSF_LOG_L2("[sock {}] Failed to connect to {}:{} from {}:{}: {}:{}", new_connection_l->socket().native_handle() , adr , port , lep.address().to_string() , lep.port() , ec_.message() , ec_.value());
cb(conn_context, ec_);
}
});
return true;
- CATCH_ENTRY_L0("boosted_tcp_server::connect_async", false);
+ GULPS_CATCH_ENTRY_L0("boosted_tcp_server::connect_async", false);
}
} // namespace
diff --git a/contrib/epee/include/net/abstract_tcp_server_cp.h b/contrib/epee/include/net/abstract_tcp_server_cp.h
index fb179abf..92ac9e0b 100644
--- a/contrib/epee/include/net/abstract_tcp_server_cp.h
+++ b/contrib/epee/include/net/abstract_tcp_server_cp.h
@@ -33,7 +33,6 @@
#include
#include
-#include "misc_log_ex.h"
//#include "threads_helper.h"
#include "syncobj.h"
#define ENABLE_PROFILING
@@ -41,8 +40,9 @@
#include "pragma_comp_defs.h"
#include "profile_tools.h"
-#undef RYO_DEFAULT_LOG_CATEGORY
-#define RYO_DEFAULT_LOG_CATEGORY "net"
+#include "common/gulps.hpp"
+
+
#define LEVIN_DEFAULT_DATA_BUFF_SIZE 2000
@@ -54,6 +54,7 @@ namespace net_utils
template
class cp_server_impl //: public abstract_handler
{
+ GULPS_CAT_MAJOR("epee_tcp_srv");
public:
cp_server_impl(/*abstract_handler* phandler = NULL*/);
virtual ~cp_server_impl();
@@ -161,7 +162,7 @@ class cp_server_impl //: public abstract_handler
if(WSA_IO_PENDING == err)
return true;
}
- LOG_ERROR("BIG FAIL: WSASend error code not correct, res=" << res << " last_err=" << err);
+ GULPSF_ERROR("BIG FAIL: WSASend error code not correct, res={} las_err={}", res, err);
::InterlockedExchange(&m_psend_data->m_is_in_use, 0);
query_shutdown();
//closesocket(m_psend_data);
@@ -173,7 +174,7 @@ class cp_server_impl //: public abstract_handler
if(!bytes_sent || bytes_sent != cb)
{
int err = ::WSAGetLastError();
- LOG_ERROR("BIG FAIL: WSASend immediatly complete? but bad results, res=" << res << " last_err=" << err);
+ GULPSF_ERROR("BIG FAIL: WSASend immediatly complete? but bad results, res={} last_err={}", res, err);
query_shutdown();
return false;
}
@@ -192,7 +193,7 @@ class cp_server_impl //: public abstract_handler
delete m_psend_data;
m_psend_data = (io_data_base *)new char[sizeof(io_data_base) + new_size - 1];
m_psend_data->TotalBuffBytes = new_size;
- LOG_PRINT("Connection buffer resized up to " << new_size, LOG_LEVEL_3);
+ GULPS_PRINT_L3("Connection buffer resized up to ", new_size);
return true;
}
diff --git a/contrib/epee/include/net/abstract_tcp_server_cp.inl b/contrib/epee/include/net/abstract_tcp_server_cp.inl
index 9975fade..b812469f 100644
--- a/contrib/epee/include/net/abstract_tcp_server_cp.inl
+++ b/contrib/epee/include/net/abstract_tcp_server_cp.inl
@@ -26,8 +26,9 @@
#pragma comment(lib, "Ws2_32.lib")
-#undef RYO_DEFAULT_LOG_CATEGORY
-#define RYO_DEFAULT_LOG_CATEGORY "net"
+#include "common/gulps.hpp"
+
+
namespace epee
{
@@ -54,7 +55,7 @@ bool cp_server_impl::init_server(int port_no)
int err = ::WSAStartup(MAKEWORD(2, 2), &wsad);
if(err != 0 || LOBYTE(wsad.wVersion) != 2 || HIBYTE(wsad.wVersion) != 2)
{
- LOG_ERROR("Could not find a usable WinSock DLL, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"");
+ GULPS_LOG_ERRORF("Could not find a usable WinSock DLL, err = {} '{}'", err , socket_errors::get_socket_error_text(err) );
return false;
}
@@ -64,7 +65,7 @@ bool cp_server_impl::init_server(int port_no)
if(INVALID_SOCKET == m_listen_socket)
{
err = ::WSAGetLastError();
- LOG_ERROR("Failed to create socket, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"");
+ GULPS_LOG_ERRORF("Failed to create socket, err = {} '{}'", err , socket_errors::get_socket_error_text(err) );
return false;
}
@@ -73,7 +74,7 @@ bool cp_server_impl::init_server(int port_no)
if(SOCKET_ERROR == err)
{
err = ::WSAGetLastError();
- LOG_PRINT("Failed to setsockopt(SO_REUSEADDR), err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"", LOG_LEVEL_1);
+ GULPSF_LOG_L1("Failed to setsockopt(SO_REUSEADDR), err = {} '{}'", err , socket_errors::get_socket_error_text(err) );
deinit_server();
return false;
}
@@ -88,7 +89,7 @@ bool cp_server_impl::init_server(int port_no)
if(SOCKET_ERROR == err)
{
err = ::WSAGetLastError();
- LOG_PRINT("Failed to Bind, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"", LOG_LEVEL_1);
+ GULPSF_LOG_L1("Failed to Bind, err = {} '{}'", err , socket_errors::get_socket_error_text(err) );
deinit_server();
return false;
}
@@ -97,7 +98,7 @@ bool cp_server_impl::init_server(int port_no)
if(INVALID_HANDLE_VALUE == m_completion_port)
{
err = ::WSAGetLastError();
- LOG_PRINT("Failed to CreateIoCompletionPort, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"", LOG_LEVEL_1);
+ GULPSF_LOG_L1("Failed to CreateIoCompletionPort, err = {} '{}'", err , socket_errors::get_socket_error_text(err) );
deinit_server();
return false;
}
@@ -123,7 +124,7 @@ static int CALLBACK CPConditionFunc(
return CF_REJECT;*/
/*if(pthis->get_active_connections_num()>=FD_SETSIZE-1)
{
- LOG_PRINT("Maximum connections count overfull.", LOG_LEVEL_2);
+ GULPS_LOG_L2("Maximum connections count overfull.");
return CF_REJECT;
}*/
@@ -150,7 +151,7 @@ unsigned CALLBACK cp_server_impl::worker_thread(void *param)
template
bool cp_server_impl::worker_thread_member()
{
- LOG_PRINT("Worker thread STARTED", LOG_LEVEL_1);
+ GULPS_LOG_L1("Worker thread STARTED");
bool stop_handling = false;
while(!stop_handling)
{
@@ -166,7 +167,7 @@ bool cp_server_impl::worker_thread_member()
{
// check return code for error
int err = GetLastError();
- LOG_PRINT("GetQueuedCompletionStatus failed with error " << err << " " << log_space::get_win32_err_descr(err), LOG_LEVEL_1);
+ GULPSF_LOG_L1("GetQueuedCompletionStatus failed with error {} {}", err , log_space::get_win32_err_descr(err));
if(pio_data)
::InterlockedExchange(&pio_data->m_is_in_use, 0);
@@ -185,13 +186,13 @@ bool cp_server_impl::worker_thread_member()
}
if(!pconnection || !pio_data)
{
- LOG_PRINT("BIG FAIL: pconnection or pio_data is empty: pconnection=" << pconnection << " pio_data=" << pio_data, LOG_LEVEL_0);
+ GULPSF_PRINT("BIG FAIL: pconnection or pio_data is empty: pconnection={} pio_data={}", pconnection, pio_data);
break;
}
if(::InterlockedCompareExchange(&pconnection->m_connection_shutwoned, 0, 0))
{
- LOG_ERROR("InterlockedCompareExchange(&pconnection->m_connection_shutwoned, 0, 0)");
+ GULPS_LOG_ERROR("InterlockedCompareExchange(&pconnection->m_connection_shutwoned, 0, 0)");
//DebugBreak();
}
@@ -199,7 +200,7 @@ bool cp_server_impl::worker_thread_member()
{
if(!pconnection)
{
- LOG_ERROR("op_type=op_type_stop, but pconnection is empty!!!");
+ GULPS_LOG_ERROR("op_type=op_type_stop, but pconnection is empty!!!");
continue;
}
shutdown_connection(pconnection);
@@ -233,7 +234,7 @@ bool cp_server_impl::worker_thread_member()
int res = 0;
while(true)
{
- LOG_PRINT("Prepearing data for WSARecv....", LOG_LEVEL_3);
+ GULPS_LOG_L3("Prepearing data for WSARecv....");
ZeroMemory(&pio_data->m_overlapped, sizeof(OVERLAPPED));
pio_data->DataBuf.len = pio_data->TotalBuffBytes;
pio_data->DataBuf.buf = pio_data->Buffer;
@@ -242,7 +243,7 @@ bool cp_server_impl::worker_thread_member()
DWORD bytes_recvd = 0;
DWORD flags = 0;
- LOG_PRINT("Calling WSARecv....", LOG_LEVEL_3);
+ GULPS_LOG_L3("Calling WSARecv....");
::InterlockedExchange(&pio_data->m_is_in_use, 1);
res = WSARecv(pconnection->m_sock, &(pio_data->DataBuf), 1, &bytes_recvd, &flags, &(pio_data->m_overlapped), NULL);
if(res == SOCKET_ERROR)
@@ -250,10 +251,10 @@ bool cp_server_impl::worker_thread_member()
int err = ::WSAGetLastError();
if(WSA_IO_PENDING == err)
{ //go pending, ok
- LOG_PRINT("WSARecv return WSA_IO_PENDING", LOG_LEVEL_3);
+ GULPS_LOG_L3("WSARecv return WSA_IO_PENDING");
break;
}
- LOG_ERROR("BIG FAIL: WSARecv error code not correct, res=" << res << " last_err=" << err);
+ GULPS_LOG_ERRORF("BIG FAIL: WSARecv error code not correct, res={} last_err={}", res, err );
::InterlockedExchange(&pio_data->m_is_in_use, 0);
pconnection->query_shutdown();
break;
@@ -264,14 +265,14 @@ bool cp_server_impl::worker_thread_member()
if(!bytes_recvd)
{
::InterlockedExchange(&pio_data->m_is_in_use, 0);
- LOG_PRINT("WSARecv return 0, bytes_recvd=0, graceful close.", LOG_LEVEL_3);
+ GULPS_LOG_L3("WSARecv return 0, bytes_recvd=0, graceful close.");
int err = ::WSAGetLastError();
- //LOG_ERROR("BIG FAIL: WSARecv error code not correct, res=" << res << " last_err=" << err);
+ //GULPS_LOG_ERRORF("BIG FAIL: WSARecv error code not correct, res={} last_err={}", res, err );
//pconnection->query_shutdown();
break;
}else
{
- LOG_PRINT("WSARecv return immediatily 0, bytes_recvd=" << bytes_recvd, LOG_LEVEL_3);
+ GULPSF_LOG_L3("WSARecv return immediatily 0, bytes_recvd={}", bytes_recvd);
//pconnection->m_tprotocol_handler.handle_recv(pio_data->Buffer, bytes_recvd);
}
}*/
@@ -279,7 +280,7 @@ bool cp_server_impl::worker_thread_member()
}
}
- LOG_PRINT("Worker thread STOPED", LOG_LEVEL_1);
+ GULPS_LOG_L1("Worker thread STOPED");
::InterlockedDecrement(&m_worker_thread_counter);
return true;
}
@@ -291,19 +292,19 @@ bool cp_server_impl::shutdown_connection(connection *pconn
if(!pconn)
{
- LOG_ERROR("Attempt to remove null pptr connection!");
+ GULPS_LOG_ERROR("Attempt to remove null pptr connection!");
return false;
}
else
{
- LOG_PRINT("Shutting down connection (" << pconn << ")", LOG_LEVEL_3);
+ GULPSF_LOG_L3("Shutting down connection ({})", pconn );
}
m_connections_lock.lock();
connections_container::iterator it = m_connections.find(pconn->m_sock);
m_connections_lock.unlock();
if(it == m_connections.end())
{
- LOG_ERROR("Failed to find closing socket=" << pconn->m_sock);
+ GULPS_LOG_ERRORF("Failed to find closing socket={}", pconn->m_sock);
return false;
}
SOCKET sock = it->second->m_sock;
@@ -313,7 +314,7 @@ bool cp_server_impl::shutdown_connection(connection *pconn
}
size_t close_sock_wait_count = 0;
{
- LOG_PRINT("Entered to 'in_use wait zone'", LOG_LEVEL_3);
+ GULPS_LOG_L3("Entered to 'in_use wait zone'");
PROFILE_FUNC("[shutdown_connection] wait for in_use");
while(::InterlockedCompareExchange(&it->second->m_precv_data->m_is_in_use, 1, 1))
{
@@ -321,14 +322,14 @@ bool cp_server_impl::shutdown_connection(connection *pconn
Sleep(100);
close_sock_wait_count++;
}
- LOG_PRINT("First step to 'in_use wait zone'", LOG_LEVEL_3);
+ GULPS_LOG_L3("First step to 'in_use wait zone'");
while(::InterlockedCompareExchange(&it->second->m_psend_data->m_is_in_use, 1, 1))
{
Sleep(100);
close_sock_wait_count++;
}
- LOG_PRINT("Leaved 'in_use wait zone'", LOG_LEVEL_3);
+ GULPS_LOG_L3("Leaved 'in_use wait zone'");
}
::closesocket(it->second->m_sock);
@@ -337,7 +338,7 @@ bool cp_server_impl::shutdown_connection(connection *pconn
m_connections_lock.lock();
m_connections.erase(it);
m_connections_lock.unlock();
- LOG_PRINT("Socked " << sock << " closed, wait_count=" << close_sock_wait_count, LOG_LEVEL_2);
+ GULPSF_LOG_L2("Socked {} closed, wait_count={}", sock , close_sock_wait_count);
return true;
}
//-------------------------------------------------------------
@@ -348,7 +349,7 @@ bool cp_server_impl::run_server(int threads_count = 0)
if(SOCKET_ERROR == err)
{
err = ::WSAGetLastError();
- LOG_ERROR("Failed to listen, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"");
+ GULPS_LOG_ERRORF("Failed to listen, err = {} '{}'", err , socket_errors::get_socket_error_text(err) );
return false;
}
@@ -366,7 +367,7 @@ bool cp_server_impl::run_server(int threads_count = 0)
//::CloseHandle(h_thread);
}
- LOG_PRINT("Numbers of worker threads started: " << threads_count, LOG_LEVEL_1);
+ GULPSF_LOG_L1("Numbers of worker threads started: {}", threads_count);
m_stop = false;
while(!m_stop)
@@ -387,7 +388,7 @@ bool cp_server_impl::run_server(int threads_count = 0)
if(SOCKET_ERROR == select_res)
{
err = ::WSAGetLastError();
- LOG_ERROR("Failed to select, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"");
+ GULPS_LOG_ERRORF("Failed to select, err = {} '{}'", err , socket_errors::get_socket_error_text(err) );
return false;
}
if(!select_res)
@@ -410,17 +411,17 @@ bool cp_server_impl::run_server(int threads_count = 0)
if(m_stop)
break;
int err = ::WSAGetLastError();
- LOG_PRINT("Failed to WSAAccept, err = " << err << " \"" << socket_errors::get_socket_error_text(err) << "\"", LOG_LEVEL_2);
+ GULPSF_LOG_L2("Failed to WSAAccept, err = {} '{}'", err , socket_errors::get_socket_error_text(err) );
continue;
}
- LOG_PRINT("Accepted connection (new socket=" << new_sock << ")", LOG_LEVEL_2);
+ GULPSF_LOG_L2("Accepted connection (new socket={})", new_sock );
{
PROFILE_FUNC("[run_server] Add new connection");
add_new_connection(new_sock, adr_from.sin_addr.s_addr, adr_from.sin_port);
}
}
}
- LOG_PRINT("Closing connections(" << m_connections.size() << ") and waiting...", LOG_LEVEL_2);
+ GULPSF_LOG_L2("Closing connections({}) and waiting...", m_connections.size() );
m_connections_lock.lock();
for(connections_container::iterator it = m_connections.begin(); it != m_connections.end(); it++)
{
@@ -434,9 +435,9 @@ bool cp_server_impl::run_server(int threads_count = 0)
::Sleep(100);
wait_count++;
}
- LOG_PRINT("Connections closed OK (wait_count=" << wait_count << ")", LOG_LEVEL_2);
+ GULPSF_LOG_L2("Connections closed OK (wait_count={})", wait_count );
- LOG_PRINT("Stopping worker threads(" << m_worker_thread_counter << ").", LOG_LEVEL_2);
+ GULPSF_LOG_L2("Stopping worker threads({}).", m_worker_thread_counter );
for(int i = 0; i < m_worker_thread_counter; i++)
{
::PostQueuedCompletionStatus(m_completion_port, 0, 0, 0);
@@ -449,7 +450,7 @@ bool cp_server_impl::run_server(int threads_count = 0)
wait_count++;
}
- LOG_PRINT("Net Server STOPPED, wait_count = " << wait_count, LOG_LEVEL_1);
+ GULPSF_LOG_L1("Net Server STOPPED, wait_count = {}", wait_count);
return true;
}
//-------------------------------------------------------------
@@ -458,7 +459,7 @@ bool cp_server_impl::add_new_connection(SOCKET new_sock, const networ
{
PROFILE_FUNC("[add_new_connection]");
- LOG_PRINT("Add new connection zone: entering lock", LOG_LEVEL_3);
+ GULPS_LOG_L3("Add new connection zone: entering lock");
m_connections_lock.lock();
boost::shared_ptr> ptr;
@@ -466,7 +467,7 @@ bool cp_server_impl::add_new_connection(SOCKET new_sock, const networ
connection &conn = *ptr.get();
m_connections[new_sock] = ptr;
- LOG_PRINT("Add new connection zone: leaving lock", LOG_LEVEL_3);
+ GULPS_LOG_L3("Add new connection zone: leaving lock");
m_connections_lock.unlock();
conn.init_buffers();
conn.m_sock = new_sock;
@@ -480,7 +481,7 @@ bool cp_server_impl::add_new_connection(SOCKET new_sock, const networ
//if(NULL == ::CreateIoCompletionPort((HANDLE)new_sock, m_completion_port, (ULONG_PTR)&conn, 0))
//{
// int err = ::GetLastError();
- // LOG_PRINT("Failed to CreateIoCompletionPort(associate socket and completion port), err = " << err << " \"" << socket_errors::get_socket_error_text(err) <<"\"", LOG_LEVEL_2);
+ // GULPSF_LOG_L2("Failed to CreateIoCompletionPort(associate socket and completion port), err = {} '{}'", err , socket_errors::get_socket_error_text(err) );
// return false;
//}
@@ -512,7 +513,7 @@ bool cp_server_impl
 ](https://ryo-currency.com/ryo-serious-competitor-to-monero)
-Copyright (c) 2018, Ryo Currency Project
-
-Copyright (c) 2014-2017, The Monero Project
-
-Copyright (c) 2012-2013, The Cryptonote developers
-
-Copyright (c) 2017, Sumokoin.org
-
-
-## Development Resources
-
-- Web: [ryo-currency.com](https://ryo-currency.com)
+Ryo is one of very few cryptonote currencies that does actual, rapid development. Its team is led by fireice_uk, mosu_forge and psychocrypt who are the developers of [Cryptonight-GPU](https://medium.com/@crypto_ryo/cryptonight-gpu-fpga-proof-pow-algorithm-based-on-floating-point-instructions-92524debf8e8) and [Cryptonight-Heavy](https://github.com/ryo-currency/ryo-writeups/blob/master/cn-heavy.md) mining algorithms, GUI Wallet with built-in GPU solo mining feature called [Ryo Wallet Atom](https://ryo-currency.com/atom) and [Xmr-Stak](https://github.com/fireice-uk/xmr-stak/releases) miner.
+- Website: [ryo-currency.com](https://ryo-currency.com)
- Mail: [contact@ryo-currency.com](mailto:contact@ryo-currency.com)
-Please note that code is developed on the [dev branch](https://github.com/ryo-currency/ryo-currency/tree/dev), if you want to check out the latest updates, before they are merged on main branch, please refer there. Master branch will always point to a version that we consider stable, so you can download the code by simply typing `git clone https://github.com/ryo-currency/ryo-currency.git`
+## Contents
+| | |
+| --- | --- |
+| 1. [Introduction](#introduction) | 7. [Community](#community) |
+| 2. [Check Development and get release binaries](#check-development-and-get-release-binaries) | 8. [Compiling Ryo from source](doc/compiling.md) |
+| 3. [Project Roadmap](#project-roadmap) | 9. [Debugging](doc/debugging.md) |
+| 4. [Features](#features) | 10. [LMDB](doc/lmdb.md) |
+| 5. [Research and contributing](#research-and-contributing) | 11. [Using Ryo with TOR and Readline](doc/tor_readline.md) |
+| 6. [Coin Supply & Emission](#coin-supply--emission) | 12. [Licensing details](#licensing-details) |
+
## Introduction
+Ryo (両 in Japanese: one syllable) is the most **secure, private and untraceable cryptocurrency out there**. Ryo originated from the [_Tael_](https://en.wikipedia.org/wiki/Ry%C5%8D), an ancient Far East unit of weight standard used for exchanging gold and silver. Based on the foundations of Monero, Ryo emerged and is poised to dominate the privacy conscious crypto scene. Ryo is a fork of Sumokoin. You can read all fork-related information [here](doc/sumokoin.md).
-Ryo (両 in Japanese: one syllable) is the most **secure, private and untraceable cryptocurrency out there**. Ryo originated from the _Tael_, an ancient Far East unit of weight standard used for exchanging gold and silver. Based on the foundations of Monero, Ryo emerged and is poised to dominate the privacy conscious crypto scene. Backed by a full featured and balanced development team headed by the legendary fireice_uk and psychocrypt.
+## Check Development and get release binaries
+[
](https://ryo-currency.com/ryo-serious-competitor-to-monero)
-Copyright (c) 2018, Ryo Currency Project
-
-Copyright (c) 2014-2017, The Monero Project
-
-Copyright (c) 2012-2013, The Cryptonote developers
-
-Copyright (c) 2017, Sumokoin.org
-
-
-## Development Resources
-
-- Web: [ryo-currency.com](https://ryo-currency.com)
+Ryo is one of very few cryptonote currencies that does actual, rapid development. Its team is led by fireice_uk, mosu_forge and psychocrypt who are the developers of [Cryptonight-GPU](https://medium.com/@crypto_ryo/cryptonight-gpu-fpga-proof-pow-algorithm-based-on-floating-point-instructions-92524debf8e8) and [Cryptonight-Heavy](https://github.com/ryo-currency/ryo-writeups/blob/master/cn-heavy.md) mining algorithms, GUI Wallet with built-in GPU solo mining feature called [Ryo Wallet Atom](https://ryo-currency.com/atom) and [Xmr-Stak](https://github.com/fireice-uk/xmr-stak/releases) miner.
+- Website: [ryo-currency.com](https://ryo-currency.com)
- Mail: [contact@ryo-currency.com](mailto:contact@ryo-currency.com)
-Please note that code is developed on the [dev branch](https://github.com/ryo-currency/ryo-currency/tree/dev), if you want to check out the latest updates, before they are merged on main branch, please refer there. Master branch will always point to a version that we consider stable, so you can download the code by simply typing `git clone https://github.com/ryo-currency/ryo-currency.git`
+## Contents
+| | |
+| --- | --- |
+| 1. [Introduction](#introduction) | 7. [Community](#community) |
+| 2. [Check Development and get release binaries](#check-development-and-get-release-binaries) | 8. [Compiling Ryo from source](doc/compiling.md) |
+| 3. [Project Roadmap](#project-roadmap) | 9. [Debugging](doc/debugging.md) |
+| 4. [Features](#features) | 10. [LMDB](doc/lmdb.md) |
+| 5. [Research and contributing](#research-and-contributing) | 11. [Using Ryo with TOR and Readline](doc/tor_readline.md) |
+| 6. [Coin Supply & Emission](#coin-supply--emission) | 12. [Licensing details](#licensing-details) |
+
## Introduction
+Ryo (両 in Japanese: one syllable) is the most **secure, private and untraceable cryptocurrency out there**. Ryo originated from the [_Tael_](https://en.wikipedia.org/wiki/Ry%C5%8D), an ancient Far East unit of weight standard used for exchanging gold and silver. Based on the foundations of Monero, Ryo emerged and is poised to dominate the privacy conscious crypto scene. Ryo is a fork of Sumokoin. You can read all fork-related information [here](doc/sumokoin.md).
-Ryo (両 in Japanese: one syllable) is the most **secure, private and untraceable cryptocurrency out there**. Ryo originated from the _Tael_, an ancient Far East unit of weight standard used for exchanging gold and silver. Based on the foundations of Monero, Ryo emerged and is poised to dominate the privacy conscious crypto scene. Backed by a full featured and balanced development team headed by the legendary fireice_uk and psychocrypt.
+## Check Development and get release binaries
+[ ](https://github.com/ryo-currency/ryo-currency/commits/dev)
-Our blockchain ensures the highest level of privacy out there by
-from the get-go having(1) **Ring Confidential Transactions (RingCT)** (2) and hardcoding **minimum transaction _mixin_ to 12**. These settings significantly reduce the chance of being identified, traced or attacked by blockchain statistical analysis.
+Please note that code is developed on the [dev branch](https://github.com/ryo-currency/ryo-currency/tree/dev), if you want to check out the latest updates, before they are merged on main branch, please refer there. Master branch will always point to a version that we consider stable, so you can download the code by simply typing `git clone https://github.com/ryo-currency/ryo-currency.git`
-Ryo has a very high privacy setting that is suitable for all high confidential transactions as well as for storage of value without being traced, monitored or identified. We call this **true fungibility**. This means that each coin is **equal** and **interchangable**; it is highly unlikely that any coin can ever by blacklisted due to previous transactions. Over the course of many years these characteristics will pay off as crypto attacks become more sophisticated with much greater computation power in the future.
+Along with each release you can find our [precompiled binaries](https://github.com/ryo-currency/ryo-currency/releases).
+To verify that the downloaded binaries are created by one of our developer please verify the checksums.
+The authenticity of the checksums can be verified with the [PGP-key's](doc/pgp_keys.md).
+
+
+## Project Roadmap
+The Ryo dev team has several vectors of development, and it has already brought results that we can see.
+[
](https://github.com/ryo-currency/ryo-currency/commits/dev)
-Our blockchain ensures the highest level of privacy out there by
-from the get-go having(1) **Ring Confidential Transactions (RingCT)** (2) and hardcoding **minimum transaction _mixin_ to 12**. These settings significantly reduce the chance of being identified, traced or attacked by blockchain statistical analysis.
+Please note that code is developed on the [dev branch](https://github.com/ryo-currency/ryo-currency/tree/dev), if you want to check out the latest updates, before they are merged on main branch, please refer there. Master branch will always point to a version that we consider stable, so you can download the code by simply typing `git clone https://github.com/ryo-currency/ryo-currency.git`
-Ryo has a very high privacy setting that is suitable for all high confidential transactions as well as for storage of value without being traced, monitored or identified. We call this **true fungibility**. This means that each coin is **equal** and **interchangable**; it is highly unlikely that any coin can ever by blacklisted due to previous transactions. Over the course of many years these characteristics will pay off as crypto attacks become more sophisticated with much greater computation power in the future.
+Along with each release you can find our [precompiled binaries](https://github.com/ryo-currency/ryo-currency/releases).
+To verify that the downloaded binaries are created by one of our developer please verify the checksums.
+The authenticity of the checksums can be verified with the [PGP-key's](doc/pgp_keys.md).
+
+
+## Project Roadmap
+The Ryo dev team has several vectors of development, and it has already brought results that we can see.
+[ ](https://ryo-currency.com#roadmap)
+Navigate to Ryo official website to explore development track record and [roadmap](https://ryo-currency.com#roadmap) details.
+
+
+## Features
+We have a solid track record and unique features that are not copied from other projects:
+
+
+[
](https://ryo-currency.com#roadmap)
+Navigate to Ryo official website to explore development track record and [roadmap](https://ryo-currency.com#roadmap) details.
+
+
+## Features
+We have a solid track record and unique features that are not copied from other projects:
+
+
+[ ](https://github.com/ryo-currency/ryo-currency/pull/206)
+### Core:
+- **Built-in elliptic curve library**. This library significantly increases wallet scan speeds compared to other CN projects.
+- **[Cryptonight-GPU mining algorithm](https://medium.com/@crypto_ryo/cryptonight-gpu-fpga-proof-pow-algorithm-based-on-floating-point-instructions-92524debf8e8)**. ASIC/FPGA/BOTNET resistant mining algorithm. GPU friendly and suitable for both AMD and Nvidia cards.
+- **Uniform payment ID-s**. Our uniform payment ID system, makes transactions that use payment ID-s untraceable and hides the very fact that you use ID-s.
+- **Default ring size of transactions set to 25**. Increased default ring size significantly reduces the chance of being identified, traced or attacked by blockchain statistical analysis.
+- **QWMA mining difficulty algorithm**. Reworked network difficulty adjustment algorithm, to make it more adaptive to network hashrate fluctuations thus bringing more stabillity.
+- **[Poisson probability check](https://github.com/ryo-currency/ryo-writeups/blob/master/poisson-writeup.md)**. This feature stops Verge-like offline timestamp attacks.
+- **(Optional) Short address format**. Short address format for users who don't need viewkey.
+- **CRC-12 mnemonic seed validation** / **Non-latin characters support** / **Varios critical bugfixes**
+
+### Infrastructure
+- **[Ryo Wallet Atom](https://ryo-currency.com/atom)**. Modern, intuitive and rich with feature GUI wallet. Available for Windows, Linux and MacOSX.
+- **[Quasar Web wallet](https://ryowebwallet.com)**. Ultra-fast WEB based wallet that shares same design with Atom wallet.
+- **[Solo mining in GUI wallet](https://solo-pool.ryoblocks.com/getting-started)**. Built-in pool software with workers support, statistics and charts display.
+- **[Woo commerce plugin](https://github.com/ryo-currency/ryo-payments-woocommerce-gateway)**. Plug-in for web developers, to implement accepting Ryo on website.
+- **[Ryo Business room](https://ryo-currency.com/ryo-business-room)**. Business community of people fostering ecosystem development.
+
+GUI wallet | Web wallet | Cli wallet | Mobile | Hardware
+--- | --- | --- | --- | ---
+[v. 1.4.0](https://github.com/ryo-currency/ryo-wallet/releases/latest) | [Ryowebwallet](https://www.ryowebwallet.com/wallet-select) | [v. 0.4.1.0](https://github.com/ryo-currency/ryo-currency/releases/latest) | Developing | Planned
+
+## Research and contributing
+With privacy and security as the core foundation of Ryo, we invest time and effort into security research as well as investigate and analyze issues with the Cryptonote protocol in order to bring true default anonymity for users.
+- [Hiding your IP while using Ryo or other Cryptonotes](https://www.reddit.com/r/ryocurrency/comments/a4mppi/hiding_your_ip_while_using_ryo_or_other/)
+- [Tracing Cryptonote ring signatures using external metadata](https://medium.com/@crypto_ryo/tracing-cryptonote-ring-signatures-using-external-metadata-8e4866810006).
+- [How buying pot with Monero will get you busted — Knacc attack on Cryptonote coins](https://medium.com/@crypto_ryo/how-buying-pot-with-monero-will-get-you-busted-knacc-attack-on-cryptonote-coins-b157cd97e82f).
+- [On-chain tracking of Monero and other Cryptonotes](https://medium.com/@crypto_ryo/on-chain-tracking-of-monero-and-other-cryptonotes-e0afc6752527).
+You can find all write-ups in our [Ryo library](https://ryo-currency.com/library/) on the website.
+
+Although Ryo Currency code in main repository is source available until February 2020, we have contributed back bug fixes and features to Monero project:
+- [Add Unicode input line](https://github.com/monero-project/monero/pull/4390).
+- [Fix for a wallet caching bug](https://github.com/monero-project/monero/pull/4247).
+Loki Project decided to use own version of wallet, based on Ryo Wallet Atom [(libre repository)](https://github.com/ryo-currency/ryo-wallet-libre) as official GUI wallet. Triton Project uses GUI wallet that is based on Ryo Wallet Atom too.
+
## Coin Supply & Emission
-
-- **Total supply**: **80,188,888** coins in 20 years, then **263,000** coins will be emitted yearly to account for inflation.
+- **Total supply**: **88,188,888** coins in 20 years, then **263,000** coins will be emitted yearly to account for inflation.
- More than **80 million coins are available** for community mining.
-- 8,790,000 Ryo coins were burned to get rid of the original Sumokoin premine. Additionally, 100,000 coins were premined and instantly unlocked to Sumokoin devs in 2017.
+- 8,790,000 Ryo coins were burned to get rid of the original Sumokoin premine. (You can check [burned premine keyimages](https://github.com/ryo-currency/ryo-currency/tree/master/utils/burned_premine_keyimages)). Additionally, 100,000 coins were premined and instantly unlocked to Sumokoin devs in 2017. The pre-mined coins have been [frozen/burned](https://github.com/ryo-currency/ryo-currency/blob/917dbb993178bb8a2ea571f214b15adcbb7c708f/src/blockchain_db/blockchain_db.cpp#L364) as announced on [reddit](https://www.reddit.com/r/ryocurrency/comments/8nb8eq/direction_for_ryo/). This can be verified using [those](/doc/verify_premine_burn_instructions.md) instructions.
-The pre-mined coins have been frozen/burned in commit [c3a3cb6](https://github.com/ryo-currency/ryo-emergency/commit/c3a3cb620488e88be7c52e017072261a3063b872)/ [blockchain_db/blockchain_db.cpp#L250-L258](https://github.com/ryo-currency/ryo-emergency/blob/c3a3cb620488e88be7c52e017072261a3063b872/src/blockchain_db/blockchain_db.cpp#L250-L258) as announced on [reddit](https://www.reddit.com/r/ryocurrency/comments/8nb8eq/direction_for_ryo/).
+- After 2 rounds of community debates [(pt1](https://www.reddit.com/r/ryocurrency/comments/8xsyqo/community_debate_lets_talk_about_the_development/e26i1vw/) / [pt2)](https://github.com/ryo-currency/ryo-writeups/blob/master/dev-fund.md) **8,000,000** Ryo coins were introduced as development fund which is located in 2/3 multisig wallet and emitted on weekly basis next 6 years. In an effort to provide transparency to the community on how the development fund is allocated, Ryo dev team built the following [dev-fund explorer page](https://ryo-currency.com/dev-fund/).
- **Coin symbol**: **RYO**
+- **Hash algorithm**: CryptoNight-GPU (ASIC/FPGA/Botnet resistant Proof-Of-Work)
+- **Total supply**: **88,188,888** coins in 20 years (including 8M dev. fund). Then 263,000 coins each year for inflation.
+- **Block time**: **240 seconds** (difficulty is adjusted every block)
- **Coin Units**:
+ 1 nanoRyo = 0.000000001 **RYO** (10-9-_the smallest coin unit_)
+ 1 microRyo = 0.000001 **RYO** (10-6)
+ 1 milliRyo = 0.001 **RYO** (10-3)
-- **Hash algorithm**: CryptoNight Heavy (Proof-Of-Work)
-- **Emission scheme**: Ryo's block reward changes _every 6-months_ according to the following "Camel" distribution*. Our emission scheme is inspired by real-world mining production comparable to crude oil, coal and gas which is often slow at first, accelerated in the next few years before declining and becoming depleted. However, the emission path of Ryo is generally not that far apart from Bitcoin.
-
-
-
-
-
-
-
-\* The emulated algorithm of Ryo block-reward emission can be found in Python and C++ scripts at [scripts](scripts) directory.
-
-## I have Sumokoin, how can i claim my Ryo?
-- You can claim your Ryo, if you had Sumokoin before they forked at block #137500. Ryo Currency as a chain fork kept all the transactions -and thus coins you had in your wallet- up and until Sumokoin forked at block #137500. To further secure your Ryo, we're going to tie the coins to a block after the fork.
-- First, install the latest Ryo wallet. Run it and generate a new wallet. Write down the seeds. Copy the MAIN ADDRESS under the RECEIVE tab. Then from the Ryo gui, click SETTINGS » NEW WALLET and restore your Ryo from the same seeds used for your old Sumokoin wallet in the Ryo GUI.
-- Send all your coins to the new Ryo MAIN ADDRESS you copied before.
-After this, you can safely transact Sumokoin, it's important to first move your Ryo, before you move your Sumokoin.
-- If you are comfortable using the CLI, you can just SWEEP ALL Ryo to yourself instead of all the above.
-
-## About this Project
-
-This is the core implementation of Ryo. It is open source and completely free to use without restrictions, except for those specified in the license agreement below. There are no restrictions on anyone creating an alternative implementation of Ryo that uses the protocol and network in a compatible manner.
-
-## Precompiled binaries
-
-Along with each release you can find our [precompiled binaries](https://github.com/ryo-currency/ryo-currency/releases).
-To verify that the downloaded binaries are created by one of our developer please verify the checksums.
-The authenticity of the checksums can by verified with the [PGP-key's](docs/pgp_keys.md).
-
-## Compiling Ryo from source
-
-### Dependencies
-
-The following table summarizes the tools and libraries required to build. A
-few of the libraries are also included in this repository (marked as
-"Vendored"). By default, the build uses the library installed on the system,
-and ignores the vendored sources. However, if no library is found installed on
-the system, then the vendored source will be built and used. The vendored
-sources are also used for statically-linked builds because distribution
-packages often include only shared library binaries (`.so`) but not static
-library archives (`.a`).
-
-| Dep | Min. version | Vendored | Debian/Ubuntu pkg | Arch pkg | Fedora | Optional | Purpose |
-| ------------ | ------------- | -------- | ------------------ | ------------ | ----------------- | -------- | -------------- |
-| GCC | 4.7.3 | NO | `build-essential` | `base-devel` | `gcc` | NO | |
-| CMake | 3.0.0 | NO | `cmake` | `cmake` | `cmake` | NO | |
-| pkg-config | any | NO | `pkg-config` | `base-devel` | `pkgconf` | NO | |
-| Boost | 1.58 | NO | `libboost-all-dev` | `boost` | `boost-devel` | NO | C++ libraries |
-| OpenSSL | basically any | NO | `libssl-dev` | `openssl` | `openssl-devel` | NO | sha256 sum |
-| libzmq | 3.0.0 | NO | `libzmq3-dev` | `zeromq` | `cppzmq-devel` | NO | ZeroMQ library |
-| libunbound | 1.4.16 | YES | `libunbound-dev` | `unbound` | `unbound-devel` | NO | DNS resolver |
-| libsodium | ? | NO | `libsodium-dev` | ? | `libsodium-devel` | NO | libsodium |
-| libminiupnpc | 2.0 | YES | `libminiupnpc-dev` | `miniupnpc` | `miniupnpc-devel` | YES | NAT punching |
-| libunwind | any | NO | `libunwind8-dev` | `libunwind` | `libunwind-devel` | YES | Stack traces |
-| liblzma | any | NO | `liblzma-dev` | `xz` | `xz-devel` | YES | For libunwind |
-| libreadline | 6.3.0 | NO | `libreadline6-dev` | `readline` | `readline-devel` | YES | Input editing |
-| ldns | 1.6.17 | NO | `libldns-dev` | `ldns` | `ldns-devel` | YES | SSL toolkit |
-| expat | 1.1 | NO | `libexpat1-dev` | `expat` | `expat-devel` | YES | XML parsing |
-| GTest | 1.5 | YES | `libgtest-dev`^ | `gtest` | `gtest-devel` | YES | Test suite |
-| Doxygen | any | NO | `doxygen` | `doxygen` | `doxygen` | YES | Documentation |
-| Graphviz | any | NO | `graphviz` | `graphviz` | `graphviz` | YES | Documentation |
-
-
-[^] On Debian/Ubuntu `libgtest-dev` only includes sources and headers. You must
-build the library binary manually. This can be done with the following command ```sudo apt-get install libgtest-dev && cd /usr/src/gtest && sudo cmake . && sudo make && sudo mv libg* /usr/lib/ ```
-
-### Cloning the repository
-
-Clone recursively to pull-in needed submodule(s):
-
-`$ git clone https://github.com/ryo-currency/ryo-currency.git`
-
-If you already have a repo cloned, initialize and update:
-
-`$ cd ryo-currency`
-
-### Build instructions
-
-Ryo uses the CMake build system and a top-level [Makefile](Makefile) that
-invokes cmake commands as needed.
-
-#### On Linux and OS X
-
-* Install the dependencies
-* Change to the root of the source code directory, change to the most recent release branch, and build:
-
- cd ryo-currency
- git checkout tags/0.2.0
- make
-
- *Optional*: If your machine has several cores and enough memory, enable
- parallel build by running `make -j
](https://github.com/ryo-currency/ryo-currency/pull/206)
+### Core:
+- **Built-in elliptic curve library**. This library significantly increases wallet scan speeds compared to other CN projects.
+- **[Cryptonight-GPU mining algorithm](https://medium.com/@crypto_ryo/cryptonight-gpu-fpga-proof-pow-algorithm-based-on-floating-point-instructions-92524debf8e8)**. ASIC/FPGA/BOTNET resistant mining algorithm. GPU friendly and suitable for both AMD and Nvidia cards.
+- **Uniform payment ID-s**. Our uniform payment ID system, makes transactions that use payment ID-s untraceable and hides the very fact that you use ID-s.
+- **Default ring size of transactions set to 25**. Increased default ring size significantly reduces the chance of being identified, traced or attacked by blockchain statistical analysis.
+- **QWMA mining difficulty algorithm**. Reworked network difficulty adjustment algorithm, to make it more adaptive to network hashrate fluctuations thus bringing more stabillity.
+- **[Poisson probability check](https://github.com/ryo-currency/ryo-writeups/blob/master/poisson-writeup.md)**. This feature stops Verge-like offline timestamp attacks.
+- **(Optional) Short address format**. Short address format for users who don't need viewkey.
+- **CRC-12 mnemonic seed validation** / **Non-latin characters support** / **Varios critical bugfixes**
+
+### Infrastructure
+- **[Ryo Wallet Atom](https://ryo-currency.com/atom)**. Modern, intuitive and rich with feature GUI wallet. Available for Windows, Linux and MacOSX.
+- **[Quasar Web wallet](https://ryowebwallet.com)**. Ultra-fast WEB based wallet that shares same design with Atom wallet.
+- **[Solo mining in GUI wallet](https://solo-pool.ryoblocks.com/getting-started)**. Built-in pool software with workers support, statistics and charts display.
+- **[Woo commerce plugin](https://github.com/ryo-currency/ryo-payments-woocommerce-gateway)**. Plug-in for web developers, to implement accepting Ryo on website.
+- **[Ryo Business room](https://ryo-currency.com/ryo-business-room)**. Business community of people fostering ecosystem development.
+
+GUI wallet | Web wallet | Cli wallet | Mobile | Hardware
+--- | --- | --- | --- | ---
+[v. 1.4.0](https://github.com/ryo-currency/ryo-wallet/releases/latest) | [Ryowebwallet](https://www.ryowebwallet.com/wallet-select) | [v. 0.4.1.0](https://github.com/ryo-currency/ryo-currency/releases/latest) | Developing | Planned
+
+## Research and contributing
+With privacy and security as the core foundation of Ryo, we invest time and effort into security research as well as investigate and analyze issues with the Cryptonote protocol in order to bring true default anonymity for users.
+- [Hiding your IP while using Ryo or other Cryptonotes](https://www.reddit.com/r/ryocurrency/comments/a4mppi/hiding_your_ip_while_using_ryo_or_other/)
+- [Tracing Cryptonote ring signatures using external metadata](https://medium.com/@crypto_ryo/tracing-cryptonote-ring-signatures-using-external-metadata-8e4866810006).
+- [How buying pot with Monero will get you busted — Knacc attack on Cryptonote coins](https://medium.com/@crypto_ryo/how-buying-pot-with-monero-will-get-you-busted-knacc-attack-on-cryptonote-coins-b157cd97e82f).
+- [On-chain tracking of Monero and other Cryptonotes](https://medium.com/@crypto_ryo/on-chain-tracking-of-monero-and-other-cryptonotes-e0afc6752527).
+You can find all write-ups in our [Ryo library](https://ryo-currency.com/library/) on the website.
+
+Although Ryo Currency code in main repository is source available until February 2020, we have contributed back bug fixes and features to Monero project:
+- [Add Unicode input line](https://github.com/monero-project/monero/pull/4390).
+- [Fix for a wallet caching bug](https://github.com/monero-project/monero/pull/4247).
+Loki Project decided to use own version of wallet, based on Ryo Wallet Atom [(libre repository)](https://github.com/ryo-currency/ryo-wallet-libre) as official GUI wallet. Triton Project uses GUI wallet that is based on Ryo Wallet Atom too.
+
## Coin Supply & Emission
-
-- **Total supply**: **80,188,888** coins in 20 years, then **263,000** coins will be emitted yearly to account for inflation.
+- **Total supply**: **88,188,888** coins in 20 years, then **263,000** coins will be emitted yearly to account for inflation.
- More than **80 million coins are available** for community mining.
-- 8,790,000 Ryo coins were burned to get rid of the original Sumokoin premine. Additionally, 100,000 coins were premined and instantly unlocked to Sumokoin devs in 2017.
+- 8,790,000 Ryo coins were burned to get rid of the original Sumokoin premine. (You can check [burned premine keyimages](https://github.com/ryo-currency/ryo-currency/tree/master/utils/burned_premine_keyimages)). Additionally, 100,000 coins were premined and instantly unlocked to Sumokoin devs in 2017. The pre-mined coins have been [frozen/burned](https://github.com/ryo-currency/ryo-currency/blob/917dbb993178bb8a2ea571f214b15adcbb7c708f/src/blockchain_db/blockchain_db.cpp#L364) as announced on [reddit](https://www.reddit.com/r/ryocurrency/comments/8nb8eq/direction_for_ryo/). This can be verified using [those](/doc/verify_premine_burn_instructions.md) instructions.
-The pre-mined coins have been frozen/burned in commit [c3a3cb6](https://github.com/ryo-currency/ryo-emergency/commit/c3a3cb620488e88be7c52e017072261a3063b872)/ [blockchain_db/blockchain_db.cpp#L250-L258](https://github.com/ryo-currency/ryo-emergency/blob/c3a3cb620488e88be7c52e017072261a3063b872/src/blockchain_db/blockchain_db.cpp#L250-L258) as announced on [reddit](https://www.reddit.com/r/ryocurrency/comments/8nb8eq/direction_for_ryo/).
+- After 2 rounds of community debates [(pt1](https://www.reddit.com/r/ryocurrency/comments/8xsyqo/community_debate_lets_talk_about_the_development/e26i1vw/) / [pt2)](https://github.com/ryo-currency/ryo-writeups/blob/master/dev-fund.md) **8,000,000** Ryo coins were introduced as development fund which is located in 2/3 multisig wallet and emitted on weekly basis next 6 years. In an effort to provide transparency to the community on how the development fund is allocated, Ryo dev team built the following [dev-fund explorer page](https://ryo-currency.com/dev-fund/).
- **Coin symbol**: **RYO**
+- **Hash algorithm**: CryptoNight-GPU (ASIC/FPGA/Botnet resistant Proof-Of-Work)
+- **Total supply**: **88,188,888** coins in 20 years (including 8M dev. fund). Then 263,000 coins each year for inflation.
+- **Block time**: **240 seconds** (difficulty is adjusted every block)
- **Coin Units**:
+ 1 nanoRyo = 0.000000001 **RYO** (10-9-_the smallest coin unit_)
+ 1 microRyo = 0.000001 **RYO** (10-6)
+ 1 milliRyo = 0.001 **RYO** (10-3)
-- **Hash algorithm**: CryptoNight Heavy (Proof-Of-Work)
-- **Emission scheme**: Ryo's block reward changes _every 6-months_ according to the following "Camel" distribution*. Our emission scheme is inspired by real-world mining production comparable to crude oil, coal and gas which is often slow at first, accelerated in the next few years before declining and becoming depleted. However, the emission path of Ryo is generally not that far apart from Bitcoin.
-
-
-
-
-
-
-
-\* The emulated algorithm of Ryo block-reward emission can be found in Python and C++ scripts at [scripts](scripts) directory.
-
-## I have Sumokoin, how can i claim my Ryo?
-- You can claim your Ryo, if you had Sumokoin before they forked at block #137500. Ryo Currency as a chain fork kept all the transactions -and thus coins you had in your wallet- up and until Sumokoin forked at block #137500. To further secure your Ryo, we're going to tie the coins to a block after the fork.
-- First, install the latest Ryo wallet. Run it and generate a new wallet. Write down the seeds. Copy the MAIN ADDRESS under the RECEIVE tab. Then from the Ryo gui, click SETTINGS » NEW WALLET and restore your Ryo from the same seeds used for your old Sumokoin wallet in the Ryo GUI.
-- Send all your coins to the new Ryo MAIN ADDRESS you copied before.
-After this, you can safely transact Sumokoin, it's important to first move your Ryo, before you move your Sumokoin.
-- If you are comfortable using the CLI, you can just SWEEP ALL Ryo to yourself instead of all the above.
-
-## About this Project
-
-This is the core implementation of Ryo. It is open source and completely free to use without restrictions, except for those specified in the license agreement below. There are no restrictions on anyone creating an alternative implementation of Ryo that uses the protocol and network in a compatible manner.
-
-## Precompiled binaries
-
-Along with each release you can find our [precompiled binaries](https://github.com/ryo-currency/ryo-currency/releases).
-To verify that the downloaded binaries are created by one of our developer please verify the checksums.
-The authenticity of the checksums can by verified with the [PGP-key's](docs/pgp_keys.md).
-
-## Compiling Ryo from source
-
-### Dependencies
-
-The following table summarizes the tools and libraries required to build. A
-few of the libraries are also included in this repository (marked as
-"Vendored"). By default, the build uses the library installed on the system,
-and ignores the vendored sources. However, if no library is found installed on
-the system, then the vendored source will be built and used. The vendored
-sources are also used for statically-linked builds because distribution
-packages often include only shared library binaries (`.so`) but not static
-library archives (`.a`).
-
-| Dep | Min. version | Vendored | Debian/Ubuntu pkg | Arch pkg | Fedora | Optional | Purpose |
-| ------------ | ------------- | -------- | ------------------ | ------------ | ----------------- | -------- | -------------- |
-| GCC | 4.7.3 | NO | `build-essential` | `base-devel` | `gcc` | NO | |
-| CMake | 3.0.0 | NO | `cmake` | `cmake` | `cmake` | NO | |
-| pkg-config | any | NO | `pkg-config` | `base-devel` | `pkgconf` | NO | |
-| Boost | 1.58 | NO | `libboost-all-dev` | `boost` | `boost-devel` | NO | C++ libraries |
-| OpenSSL | basically any | NO | `libssl-dev` | `openssl` | `openssl-devel` | NO | sha256 sum |
-| libzmq | 3.0.0 | NO | `libzmq3-dev` | `zeromq` | `cppzmq-devel` | NO | ZeroMQ library |
-| libunbound | 1.4.16 | YES | `libunbound-dev` | `unbound` | `unbound-devel` | NO | DNS resolver |
-| libsodium | ? | NO | `libsodium-dev` | ? | `libsodium-devel` | NO | libsodium |
-| libminiupnpc | 2.0 | YES | `libminiupnpc-dev` | `miniupnpc` | `miniupnpc-devel` | YES | NAT punching |
-| libunwind | any | NO | `libunwind8-dev` | `libunwind` | `libunwind-devel` | YES | Stack traces |
-| liblzma | any | NO | `liblzma-dev` | `xz` | `xz-devel` | YES | For libunwind |
-| libreadline | 6.3.0 | NO | `libreadline6-dev` | `readline` | `readline-devel` | YES | Input editing |
-| ldns | 1.6.17 | NO | `libldns-dev` | `ldns` | `ldns-devel` | YES | SSL toolkit |
-| expat | 1.1 | NO | `libexpat1-dev` | `expat` | `expat-devel` | YES | XML parsing |
-| GTest | 1.5 | YES | `libgtest-dev`^ | `gtest` | `gtest-devel` | YES | Test suite |
-| Doxygen | any | NO | `doxygen` | `doxygen` | `doxygen` | YES | Documentation |
-| Graphviz | any | NO | `graphviz` | `graphviz` | `graphviz` | YES | Documentation |
-
-
-[^] On Debian/Ubuntu `libgtest-dev` only includes sources and headers. You must
-build the library binary manually. This can be done with the following command ```sudo apt-get install libgtest-dev && cd /usr/src/gtest && sudo cmake . && sudo make && sudo mv libg* /usr/lib/ ```
-
-### Cloning the repository
-
-Clone recursively to pull-in needed submodule(s):
-
-`$ git clone https://github.com/ryo-currency/ryo-currency.git`
-
-If you already have a repo cloned, initialize and update:
-
-`$ cd ryo-currency`
-
-### Build instructions
-
-Ryo uses the CMake build system and a top-level [Makefile](Makefile) that
-invokes cmake commands as needed.
-
-#### On Linux and OS X
-
-* Install the dependencies
-* Change to the root of the source code directory, change to the most recent release branch, and build:
-
- cd ryo-currency
- git checkout tags/0.2.0
- make
-
- *Optional*: If your machine has several cores and enough memory, enable
- parallel build by running `make -j