diff --git a/docs/hub/enterprise-hub-datasets.md b/docs/hub/enterprise-hub-datasets.md
index 4863e7391..5a224a8de 100644
--- a/docs/hub/enterprise-hub-datasets.md
+++ b/docs/hub/enterprise-hub-datasets.md
@@ -1,14 +1,14 @@
# Datasets
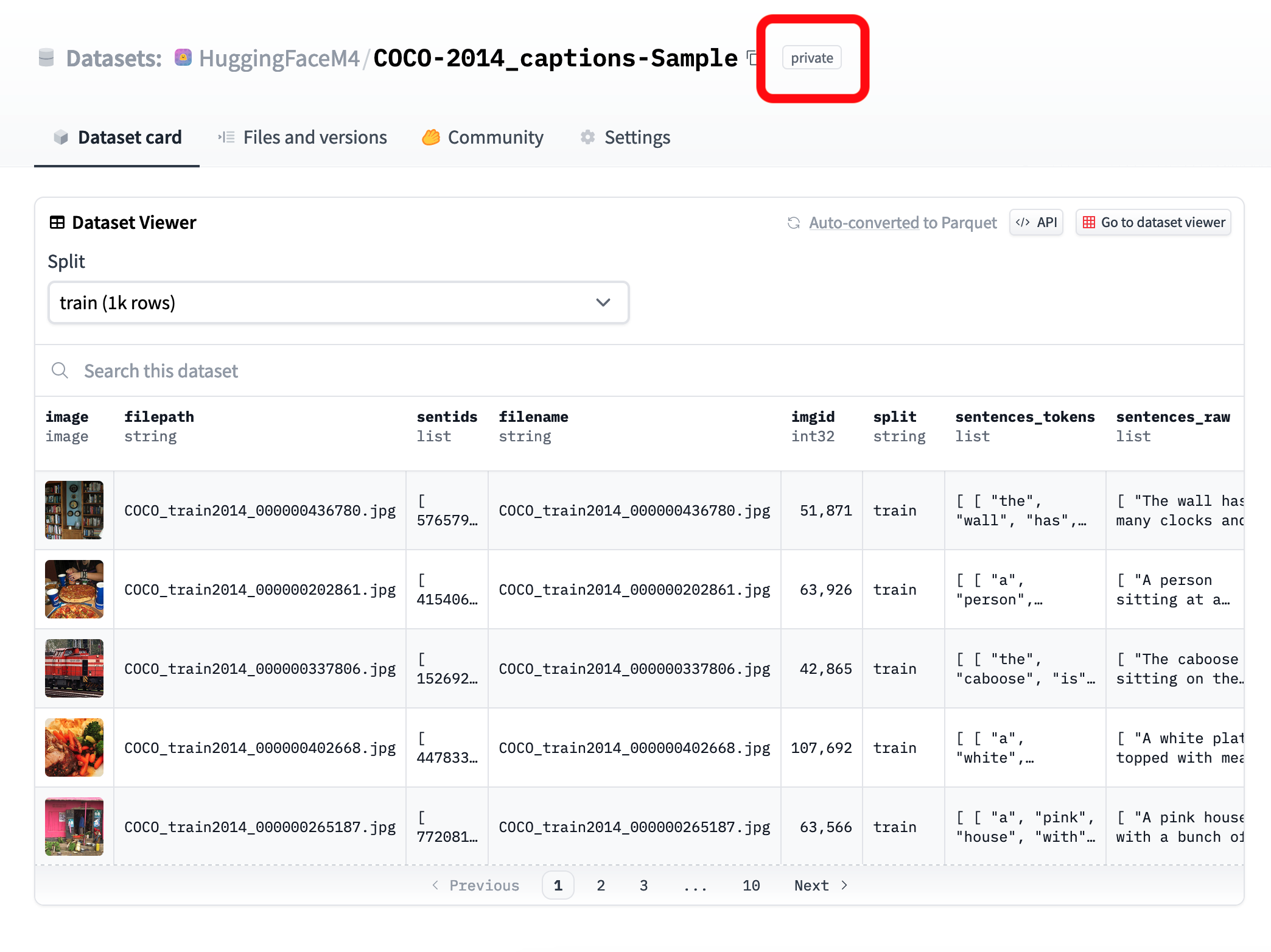
-The Dataset Viewer is enabled on private datasets owned by an Enterprise Hub organization.
+The Dataset Viewer is enabled on private datasets owned by an Enterprise Hub organization.
The Dataset Viewer allows teams to understand their data and to help them build better data processing and filtering for AI. The Viewer allows to explore the datasets content, inspect data distributions, filter by values and even search for keywords. It also includes the datasets conversion to Parquet which can be used for programmatic data visualization.
-See [Dataset Viewer](./datasets-viewer) for more information.
+[More information about the Dataset Viewer →](./datasets-viewer)
diff --git a/docs/hub/enterprise-hub-resource-groups.md b/docs/hub/enterprise-hub-resource-groups.md
index e2dd79f3b..036c93e5d 100644
--- a/docs/hub/enterprise-hub-resource-groups.md
+++ b/docs/hub/enterprise-hub-resource-groups.md
@@ -1,9 +1,32 @@
# Resource groups
-This feature is part of the Enterprise Hub.
+This feature is part of the Enterprise Hub.
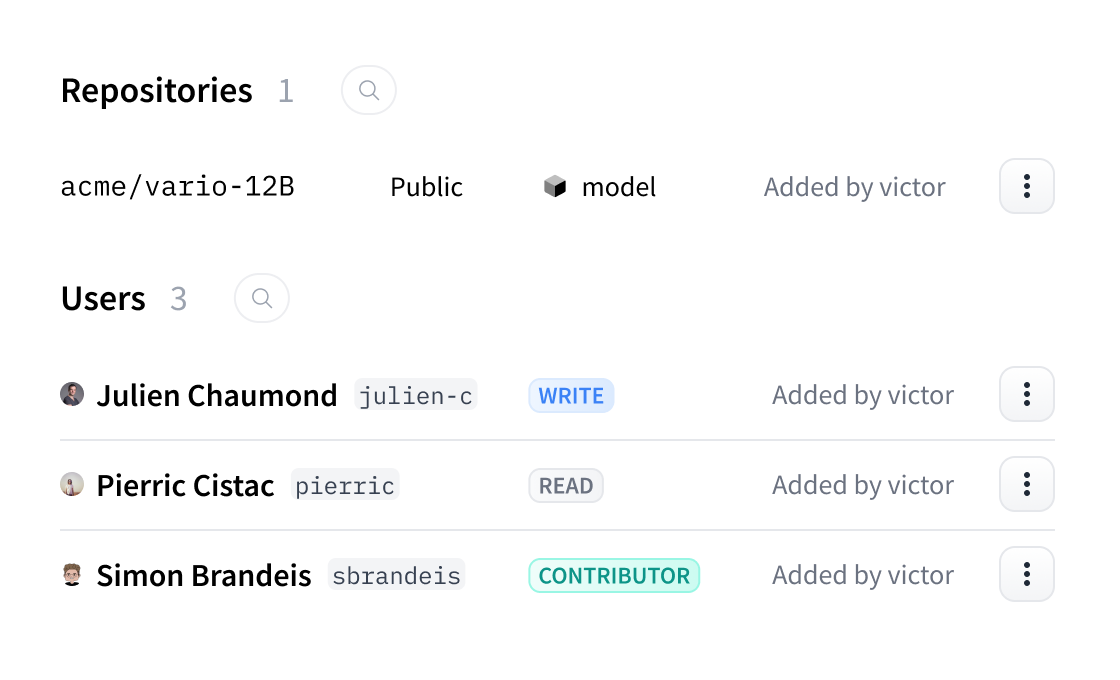
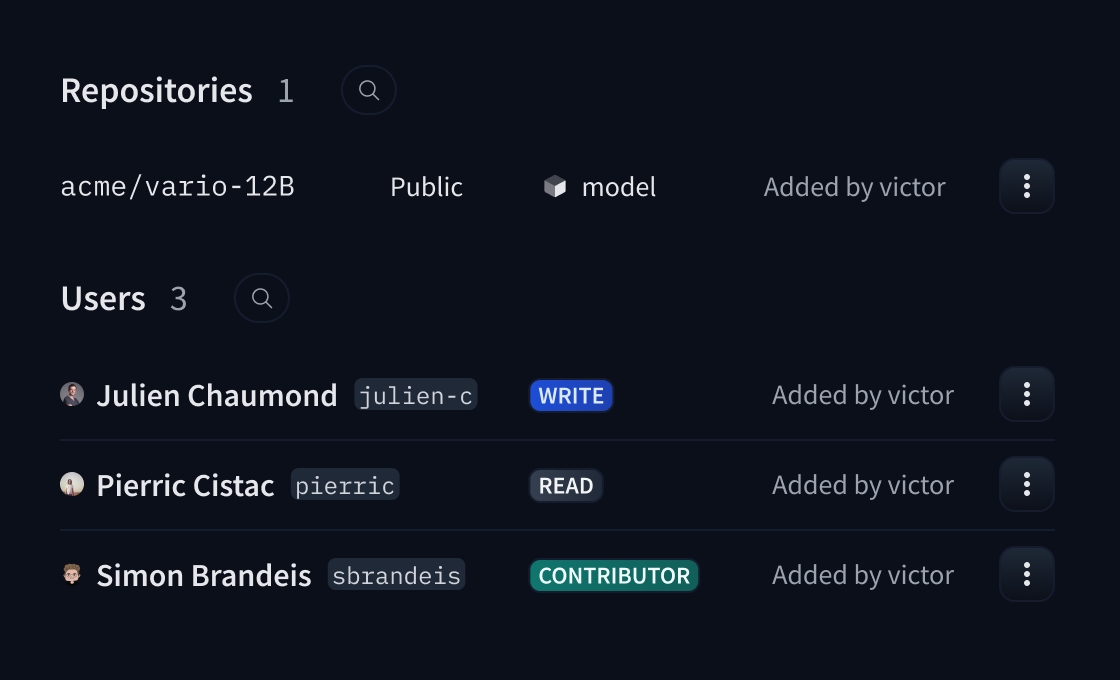
-Resource Groups allow Enterprise Hub organizations to enforce fine-grained access control to their repositories.
+Resource Groups allow organizations to enforce fine-grained access control to their repositories.
-Read the [documentation for Resource Groups under the Security section](./security-resource-groups).
+
+
+
+
+
+This feature allows organization administrators to:
+
+- Group related repositories together for better organization
+- Control member access at a group level rather than individual repository level
+- Assign different permission roles (read, contributor, write, admin) to team members
+- Keep private repositories visible only to authorized group members
+- Enable multiple teams to work independently within the same organization
+
+This Enterprise Hub feature helps organizations manage complex team structures and maintain proper access control over their repositories.
+
+[Getting started with Resource Groups →](./security-resource-groups)
diff --git a/docs/hub/enterprise-hub-tokens-management.md b/docs/hub/enterprise-hub-tokens-management.md
index f3fc9b111..9717fd909 100644
--- a/docs/hub/enterprise-hub-tokens-management.md
+++ b/docs/hub/enterprise-hub-tokens-management.md
@@ -1,59 +1,54 @@
# Tokens Management
-This feature is part of the Enterprise Hub.
+This feature is part of the Enterprise Hub.
-Tokens Management allows organization administrators to control access tokens within their organization, ensuring that only authorized users have access to organization resources.
-
+Tokens Management enables organization administrators to oversee access tokens within their organization, ensuring secure access to organization resources.
## Viewing and Managing Access Tokens
-The token listing feature provides a view of all access tokens within your organization. Administrators can:
+The token listing feature displays all access tokens within your organization. Administrators can:
- Monitor token usage and identify or prevent potential security risks:
- - unauthorized access to private resources ("leak")
- - scopes of access that are too wide
- - improvable token hygienics (tokens that have not been rotated in a long time, for example)
-- Identify inactive or unused tokens that can be revoked
+ - Unauthorized access to private resources ("leaks")
+ - Overly broad access scopes
+ - Suboptimal token hygiene (e.g., tokens that have not been rotated in a long time)
+- Identify and revoke inactive or unused tokens


-
-Fine-grained tokens can be reviewed to see their permissions:
+Fine-grained tokens display their specific permissions:


+## Token Policy
-## Token policy
-
-With Tokens Management, Enterprise org admins can decide which of the following policies they want to enforce:
-
-| **Policy** | **Unscoped (Read/Write) Access Tokens** | **Fine-Grained Tokens** |
-| --- | --- | --- |
-| **Allow access via User Access Tokens (default)** | Authorized | Authorized |
-| **Only access via fine-grained tokens** | Unauthorized | Authorized |
-| **Do not require administrator approval** | Unauthorized | Authorized |
-| **Require administrator approval** | Unauthorized | Unauthorized without an approval (except for admin-created) |
+Enterprise organization administrators can enforce the following policies:
+| **Policy** | **Unscoped (Read/Write) Access Tokens** | **Fine-Grained Tokens** |
+| ------------------------------------------------- | --------------------------------------- | ----------------------------------------------------------- |
+| **Allow access via User Access Tokens (default)** | Authorized | Authorized |
+| **Only access via fine-grained tokens** | Unauthorized | Authorized |
+| **Do not require administrator approval** | Unauthorized | Authorized |
+| **Require administrator approval** | Unauthorized | Unauthorized without an approval (except for admin-created) |


-
## Reviewing Token Authorization
-When your token policy is set to "Require administrator approval", organization administrators can view the details of all fine-grained tokens with access to resources owned by the organization. They can also revoke access to those tokens. Organization administrators will receive an email when an authorization is requested for a fine-grained token.
+When token policy is set to "Require administrator approval", organization administrators can review details of all fine-grained tokens accessing organization-owned resources and revoke access if needed. Administrators receive email notifications for token authorization requests.
-When a token is revoked or denied, the user who created the token will receive an email notification.
+When a token is revoked or denied, the user who created the token receives an email notification.

diff --git a/docs/hub/enterprise-hub.md b/docs/hub/enterprise-hub.md
index 10cc43e3e..f171b3611 100644
--- a/docs/hub/enterprise-hub.md
+++ b/docs/hub/enterprise-hub.md
@@ -1,12 +1,19 @@
# Enterprise Hub
+
+Subscribe to Enterprise Hub to get access to advanced features for your organization.
+
+
Enterprise Hub adds advanced capabilities to organizations, enabling safe, compliant and managed collaboration for companies and teams on Hugging Face.
-
+
+  +
+  +
+
In this section we will document the following Enterprise Hub features:
-- [SSO](./enterprise-sso)
+- [Single Sign-On (SSO)](./enterprise-sso)
- [Audit Logs](./audit-logs)
- [Storage Regions](./storage-regions)
- [Dataset viewer for Private datasets](./enterprise-hub-datasets)
diff --git a/docs/hub/enterprise-sso.md b/docs/hub/enterprise-sso.md
index a115e365e..bbe34fd44 100644
--- a/docs/hub/enterprise-sso.md
+++ b/docs/hub/enterprise-sso.md
@@ -1,7 +1,32 @@
# Single Sign-On (SSO)
-This feature is part of the Enterprise Hub.
+This feature is part of the Enterprise Hub.
-Read the [documentation for SSO under the Security section](./security-sso).
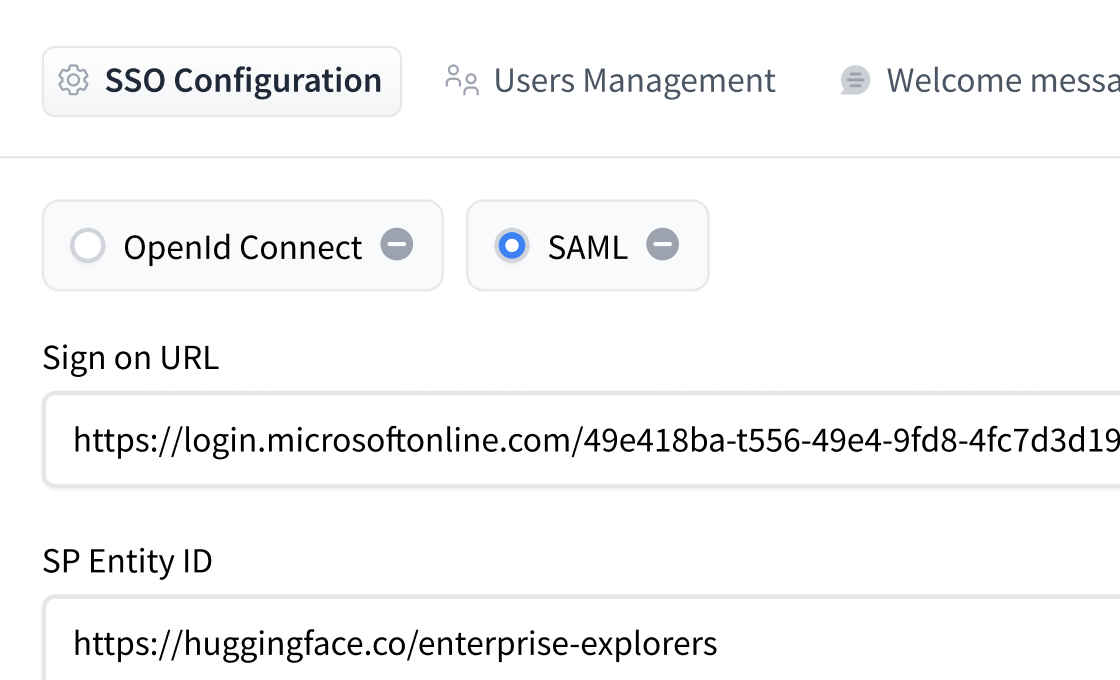
+Single sign-on (SSO) allows organizations to securely manage user authentication through their own identity provider (IdP). Both SAML 2.0 and OpenID Connect (OIDC) protocols are supported.
+
+
+
+
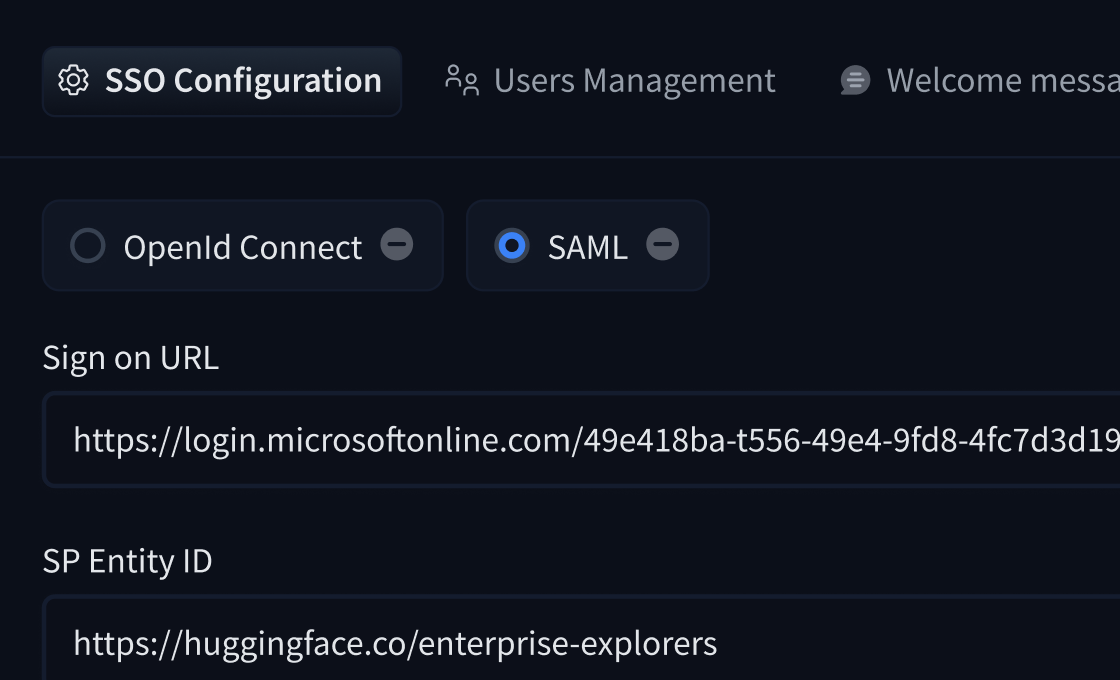
+
+
+This feature allows organizations to:
+
+- Enforce mandatory authentication through your company's IdP
+- Automatically manage user access and roles based on your IdP attributes
+- Support popular providers like Okta, OneLogin, and Azure Active Directory
+- Maintain security while allowing external collaborators when needed
+- Control session timeouts and role mappings
+
+This Enterprise Hub feature helps organizations maintain consistent security policies while giving their teams seamless access to Hugging Face resources.
+
+[Getting started with SSO →](./security-sso)
diff --git a/docs/hub/organizations-security.md b/docs/hub/organizations-security.md
index 8ce6b8c3e..886a4321f 100644
--- a/docs/hub/organizations-security.md
+++ b/docs/hub/organizations-security.md
@@ -10,7 +10,7 @@ You can set up [Single Sign-On (SSO)](./security-sso) to be able to map access c
Advanced and more fine-grained access control can be achieved with [Resource Groups](./security-resource-groups).
-The Resource Group feature is part of the
Enterprise Hub.
+The Resource Group feature is part of the
Enterprise Hub.
@@ -31,25 +31,22 @@ As an organization `admin`, go to the **Members** section of the org settings to
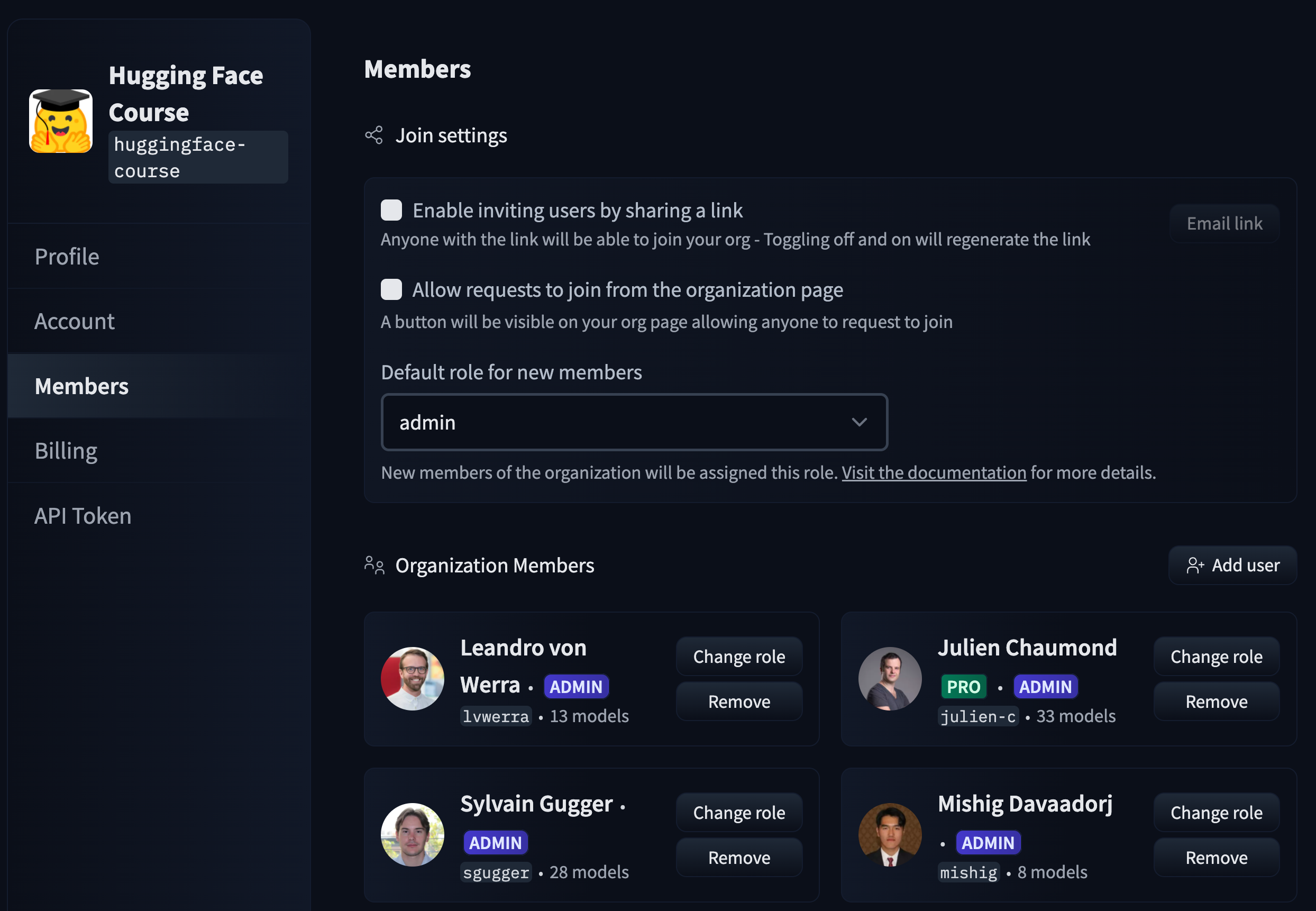
-
## Viewing members' email address
-This feature is part of the Enterprise Hub.
+This feature is part of the Enterprise Hub.
You may be able to view the email addresses of members of your organization. The visibility of the email addresses depends on the organization's SSO configuration, or verified organization status.
- If you [verify a domain for your organization](./organizations-managing#organization-domain-name), you can view members' email addresses for the verified domain.
-- If SSO is configured for your organization, you can view the email address for each of your organization members by setting `Matching email domains` in the SSO configuration
-
+- If SSO is configured for your organization, you can view the email address for each of your organization members by setting `Matching email domains` in the SSO configuration


-
## Managing Access Tokens with access to my organization
-See [Tokens Management](./enterprise-hub-tokens-management)
\ No newline at end of file
+See [Tokens Management](./enterprise-hub-tokens-management)
diff --git a/docs/hub/security-resource-groups.md b/docs/hub/security-resource-groups.md
index b90bae536..3e0677909 100644
--- a/docs/hub/security-resource-groups.md
+++ b/docs/hub/security-resource-groups.md
@@ -1,7 +1,7 @@
# Advanced Access Control in Organizations with Resource Groups
-This feature is part of the Enterprise Hub.
+This feature is part of the Enterprise Hub.
In your Hugging Face organization, you can use Resource Groups to control which members have access to specific repositories.
@@ -55,4 +55,3 @@ Remember that a repository can be part of only one Resource Group. You'll be war
## Programmatic management (API)
Coming soon!
-
diff --git a/docs/hub/security-sso-azure-oidc.md b/docs/hub/security-sso-azure-oidc.md
index 9c4c447df..acbdeafb0 100644
--- a/docs/hub/security-sso-azure-oidc.md
+++ b/docs/hub/security-sso-azure-oidc.md
@@ -1,13 +1,11 @@
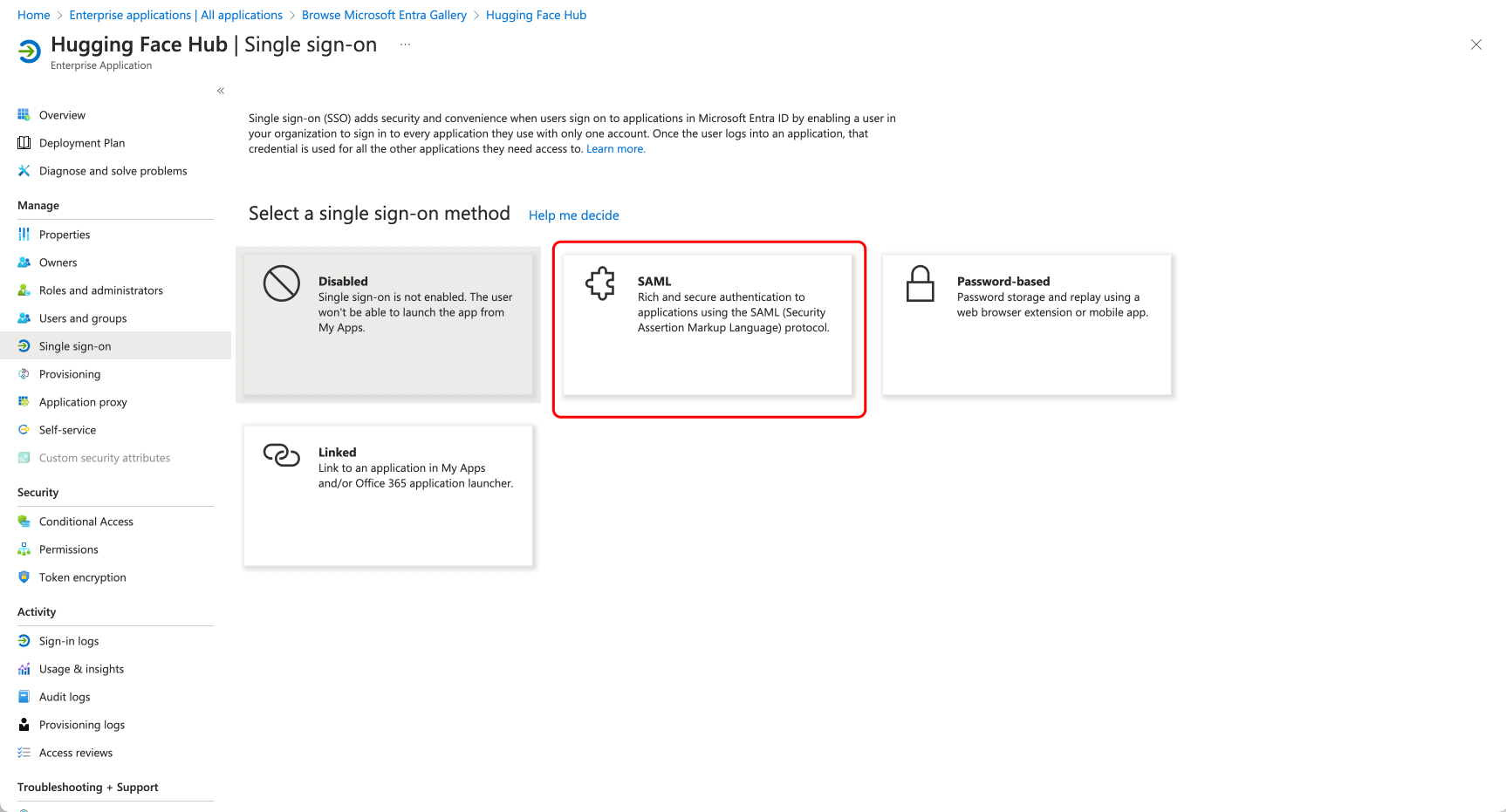
# How to configure OIDC SSO with Azure
-This guide will use Azure as the SSO provider and the Open ID Connect (OIDC) protocol as our preferred identity protocol.
-
+This guide will use Azure as the SSO provider and the Open ID Connect (OIDC) protocol as our preferred identity protocol.
- This feature is part of the Enterprise Hub.
+ This feature is part of the Enterprise Hub.
-
### Step 1: Create a new application in your Identity Provider
Open a new tab/window in your browser and sign in to the Azure portal of your organization.
@@ -44,7 +42,6 @@ Open a new tab/window in your browser and navigate to the SSO section of your or
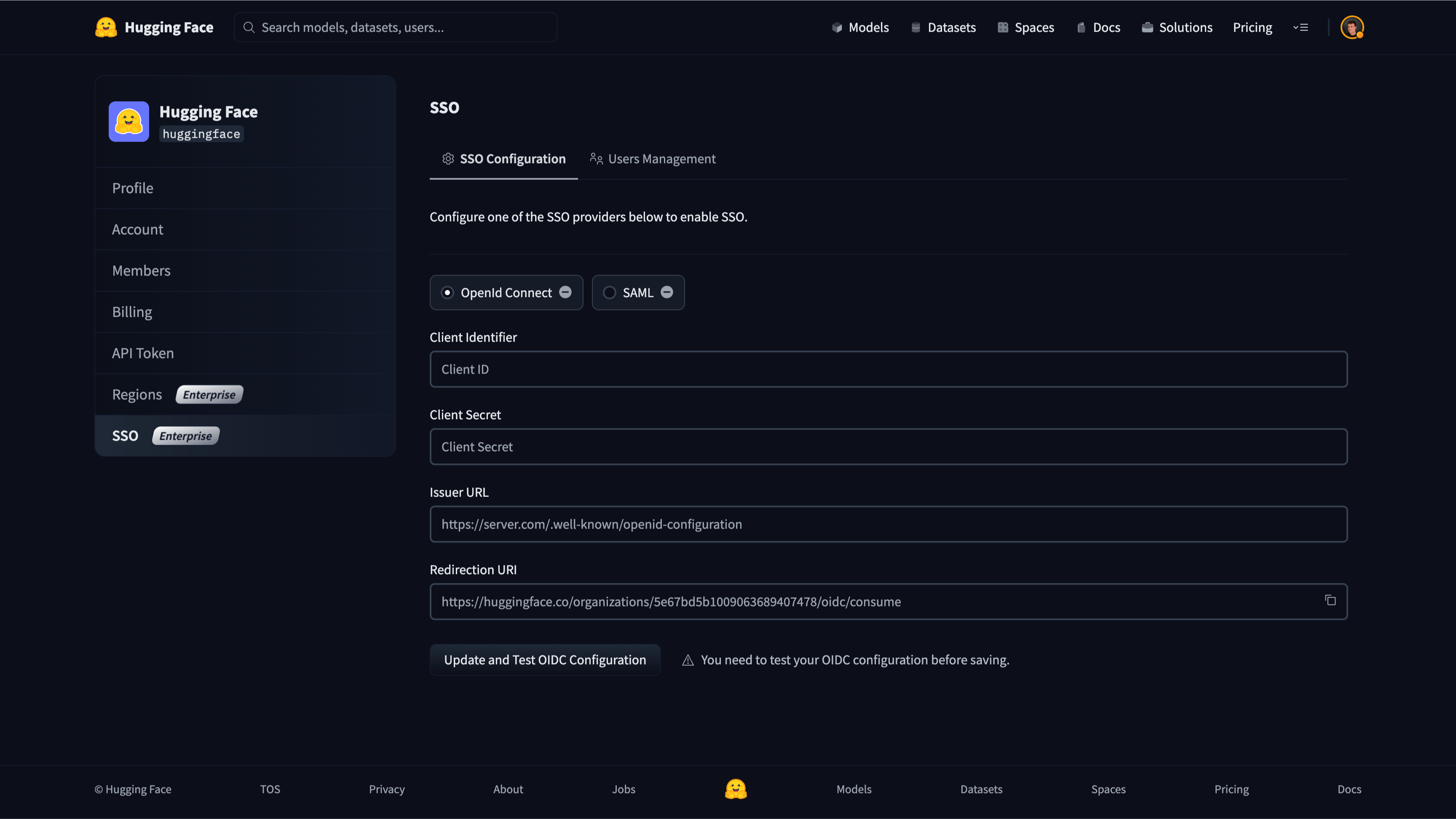
-
Copy the "Redirection URI" from the organization's settings on Hugging Face and paste it into the "Redirect URI" field on Azure Entra ID. Make sure you select "Web" in the dropdown menu.
The URL looks like this: `https://huggingface.co/organizations/[organizationIdentifier]/oidc/consume`.
@@ -57,6 +54,7 @@ Save your new application.
### Step 3: Finalize configuration on Hugging Face
We will need to collect the following information to finalize the setup on Hugging Face:
+
- The Client ID of the OIDC app
- A Client secret of the OIDC app
- The Issuer URL of the OIDC app
@@ -99,14 +97,12 @@ Once you have created the secret, copy the secret value and paste it into the "C
 +
+  +
+ +
+  +
+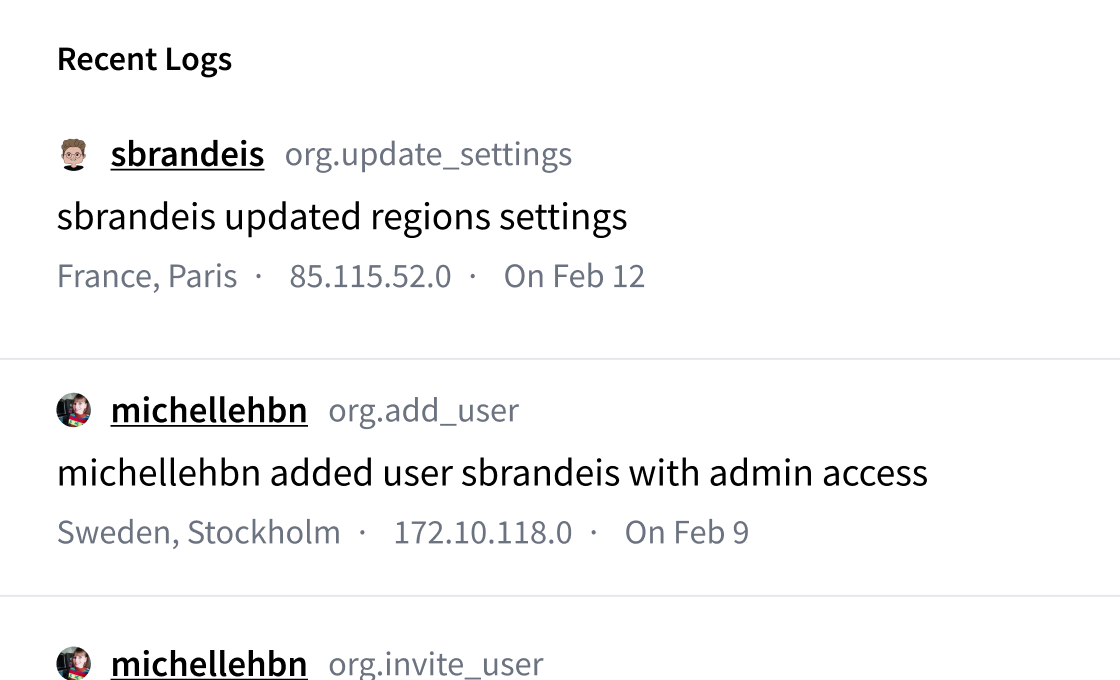 +
+  +
+



 diff --git a/docs/hub/enterprise-hub-resource-groups.md b/docs/hub/enterprise-hub-resource-groups.md
index e2dd79f3b..036c93e5d 100644
--- a/docs/hub/enterprise-hub-resource-groups.md
+++ b/docs/hub/enterprise-hub-resource-groups.md
@@ -1,9 +1,32 @@
# Resource groups
diff --git a/docs/hub/enterprise-hub-resource-groups.md b/docs/hub/enterprise-hub-resource-groups.md
index e2dd79f3b..036c93e5d 100644
--- a/docs/hub/enterprise-hub-resource-groups.md
+++ b/docs/hub/enterprise-hub-resource-groups.md
@@ -1,9 +1,32 @@
# Resource groups
 +
+  +
+





 diff --git a/docs/hub/enterprise-hub.md b/docs/hub/enterprise-hub.md
index 10cc43e3e..f171b3611 100644
--- a/docs/hub/enterprise-hub.md
+++ b/docs/hub/enterprise-hub.md
@@ -1,12 +1,19 @@
# Enterprise Hub
+
diff --git a/docs/hub/enterprise-hub.md b/docs/hub/enterprise-hub.md
index 10cc43e3e..f171b3611 100644
--- a/docs/hub/enterprise-hub.md
+++ b/docs/hub/enterprise-hub.md
@@ -1,12 +1,19 @@
# Enterprise Hub
+ +
+  +
In this section we will document the following Enterprise Hub features:
-- [SSO](./enterprise-sso)
+- [Single Sign-On (SSO)](./enterprise-sso)
- [Audit Logs](./audit-logs)
- [Storage Regions](./storage-regions)
- [Dataset viewer for Private datasets](./enterprise-hub-datasets)
diff --git a/docs/hub/enterprise-sso.md b/docs/hub/enterprise-sso.md
index a115e365e..bbe34fd44 100644
--- a/docs/hub/enterprise-sso.md
+++ b/docs/hub/enterprise-sso.md
@@ -1,7 +1,32 @@
# Single Sign-On (SSO)
+
In this section we will document the following Enterprise Hub features:
-- [SSO](./enterprise-sso)
+- [Single Sign-On (SSO)](./enterprise-sso)
- [Audit Logs](./audit-logs)
- [Storage Regions](./storage-regions)
- [Dataset viewer for Private datasets](./enterprise-hub-datasets)
diff --git a/docs/hub/enterprise-sso.md b/docs/hub/enterprise-sso.md
index a115e365e..bbe34fd44 100644
--- a/docs/hub/enterprise-sso.md
+++ b/docs/hub/enterprise-sso.md
@@ -1,7 +1,32 @@
# Single Sign-On (SSO)
 +
+  +
+





 diff --git a/docs/hub/security-sso-azure-saml.md b/docs/hub/security-sso-azure-saml.md
index 1237171b7..578afce84 100644
--- a/docs/hub/security-sso-azure-saml.md
+++ b/docs/hub/security-sso-azure-saml.md
@@ -1,11 +1,11 @@
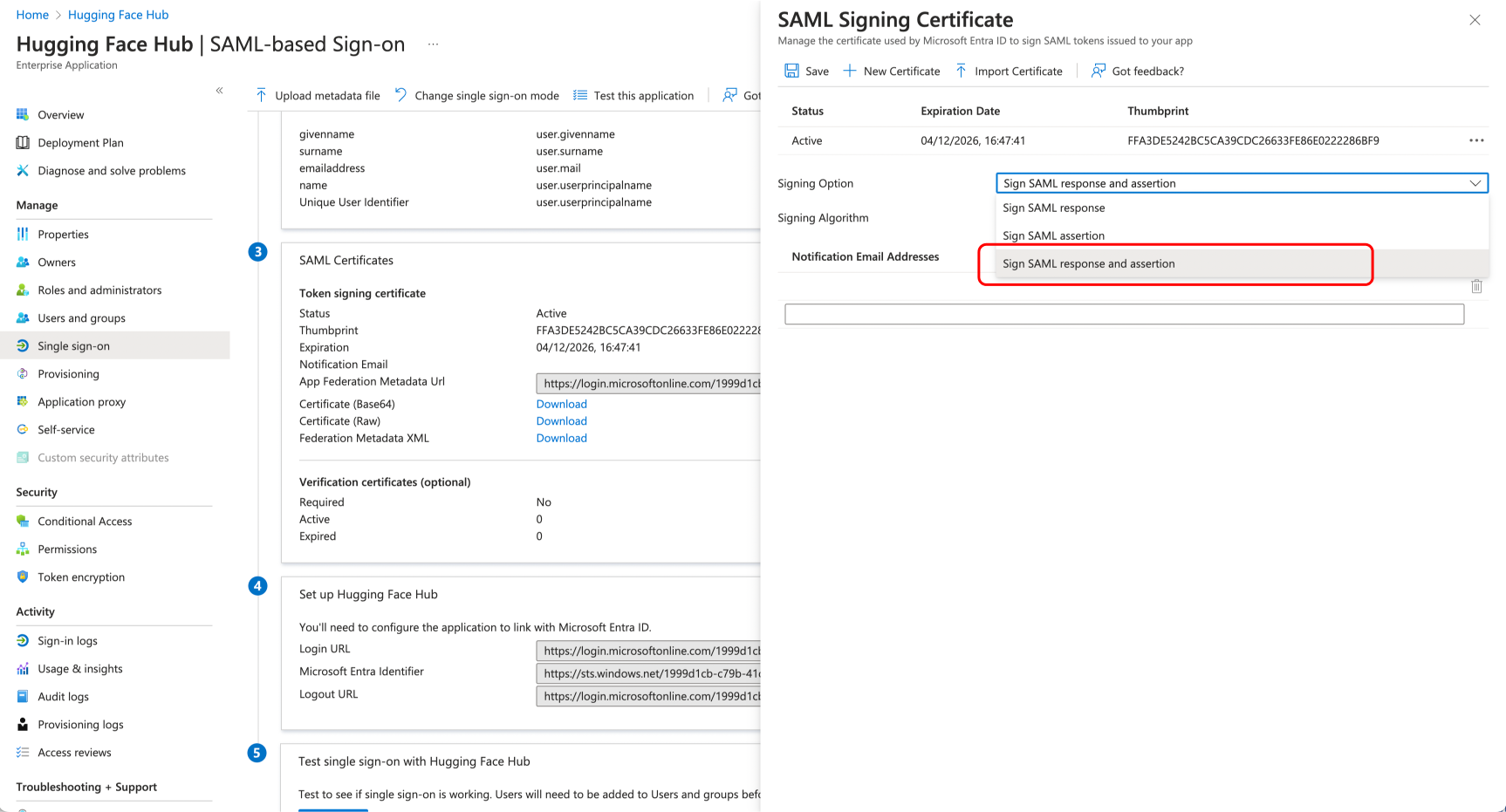
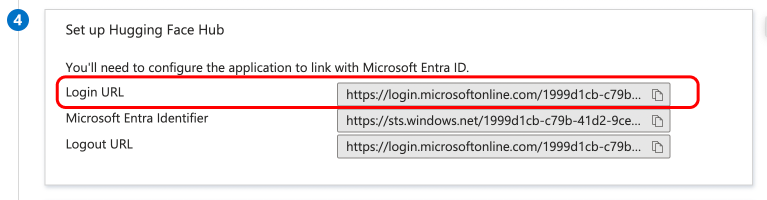
# How to configure SAML SSO with Azure
-In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.
diff --git a/docs/hub/security-sso-azure-saml.md b/docs/hub/security-sso-azure-saml.md
index 1237171b7..578afce84 100644
--- a/docs/hub/security-sso-azure-saml.md
+++ b/docs/hub/security-sso-azure-saml.md
@@ -1,11 +1,11 @@
# How to configure SAML SSO with Azure
-In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.
 diff --git a/docs/hub/security-sso-okta-oidc.md b/docs/hub/security-sso-okta-oidc.md
index adcb0821b..92d65bcf0 100644
--- a/docs/hub/security-sso-okta-oidc.md
+++ b/docs/hub/security-sso-okta-oidc.md
@@ -1,9 +1,9 @@
# How to configure OIDC SSO with Okta
-In this guide, we will use Okta as the SSO provider and with the Open ID Connect (OIDC) protocol as our preferred identity protocol.
+In this guide, we will use Okta as the SSO provider and with the Open ID Connect (OIDC) protocol as our preferred identity protocol.
diff --git a/docs/hub/security-sso-okta-oidc.md b/docs/hub/security-sso-okta-oidc.md
index adcb0821b..92d65bcf0 100644
--- a/docs/hub/security-sso-okta-oidc.md
+++ b/docs/hub/security-sso-okta-oidc.md
@@ -1,9 +1,9 @@
# How to configure OIDC SSO with Okta
-In this guide, we will use Okta as the SSO provider and with the Open ID Connect (OIDC) protocol as our preferred identity protocol.
+In this guide, we will use Okta as the SSO provider and with the Open ID Connect (OIDC) protocol as our preferred identity protocol.
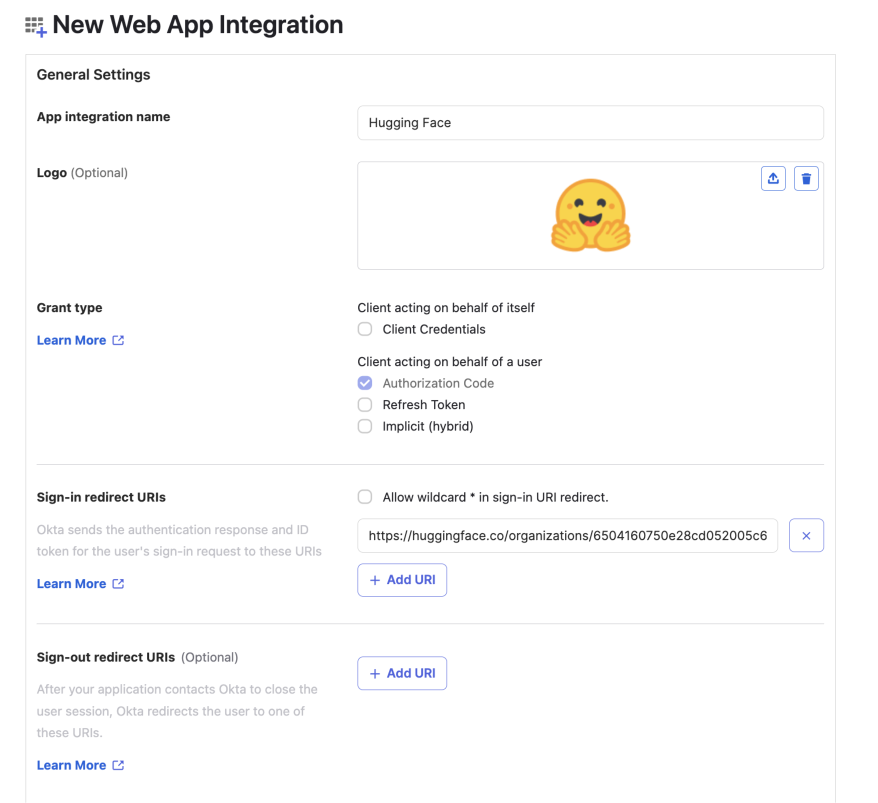
 @@ -46,26 +45,23 @@ You can leave the optional Sign-out redirect URIs blank.
@@ -46,26 +45,23 @@ You can leave the optional Sign-out redirect URIs blank.


 diff --git a/docs/hub/security-sso-okta-saml.md b/docs/hub/security-sso-okta-saml.md
index 2cab374de..d6e194d10 100644
--- a/docs/hub/security-sso-okta-saml.md
+++ b/docs/hub/security-sso-okta-saml.md
@@ -1,11 +1,11 @@
# How to configure SAML SSO with Okta
-In this guide, we will use Okta as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+In this guide, we will use Okta as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.
diff --git a/docs/hub/security-sso-okta-saml.md b/docs/hub/security-sso-okta-saml.md
index 2cab374de..d6e194d10 100644
--- a/docs/hub/security-sso-okta-saml.md
+++ b/docs/hub/security-sso-okta-saml.md
@@ -1,11 +1,11 @@
# How to configure SAML SSO with Okta
-In this guide, we will use Okta as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+In this guide, we will use Okta as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.
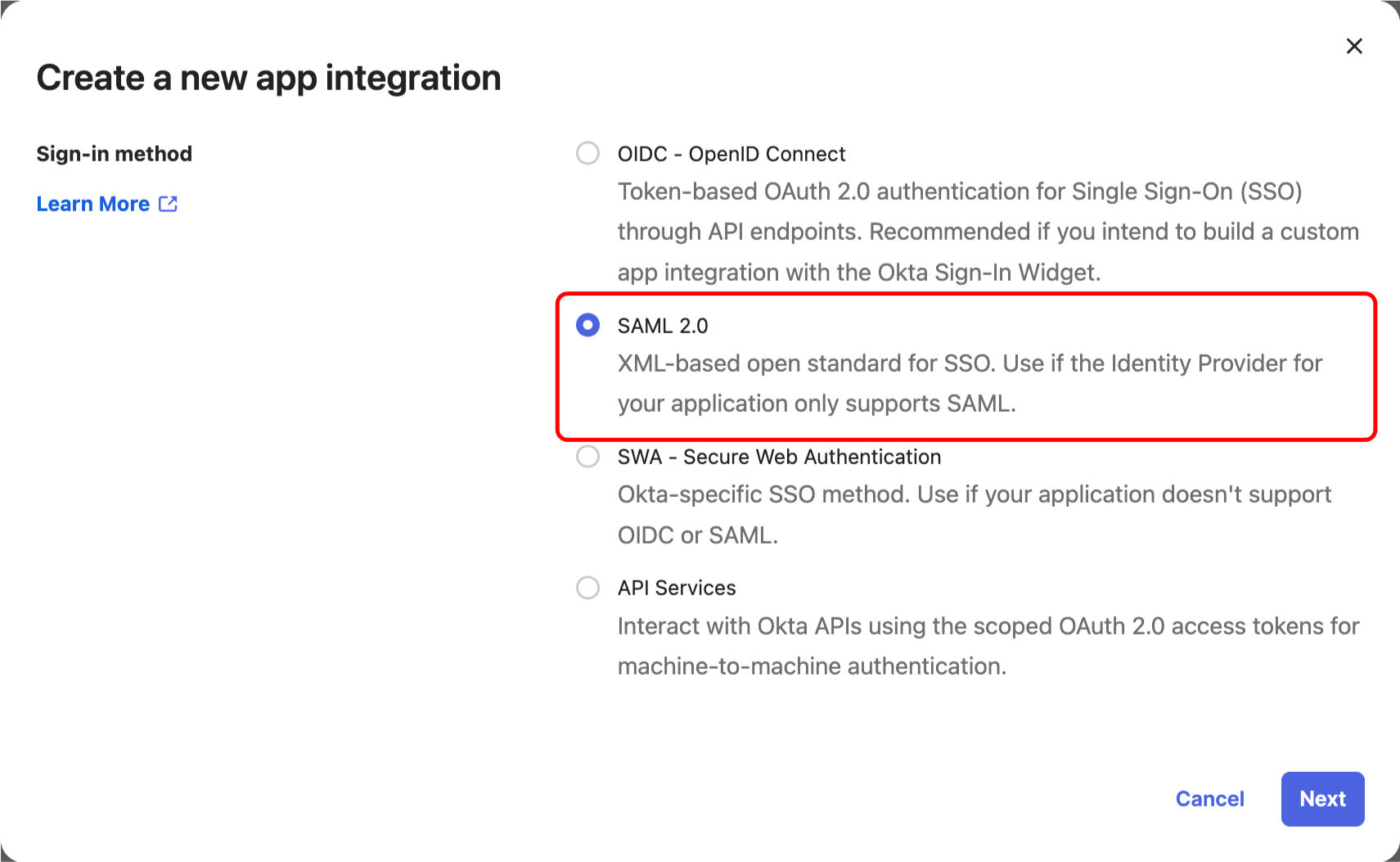
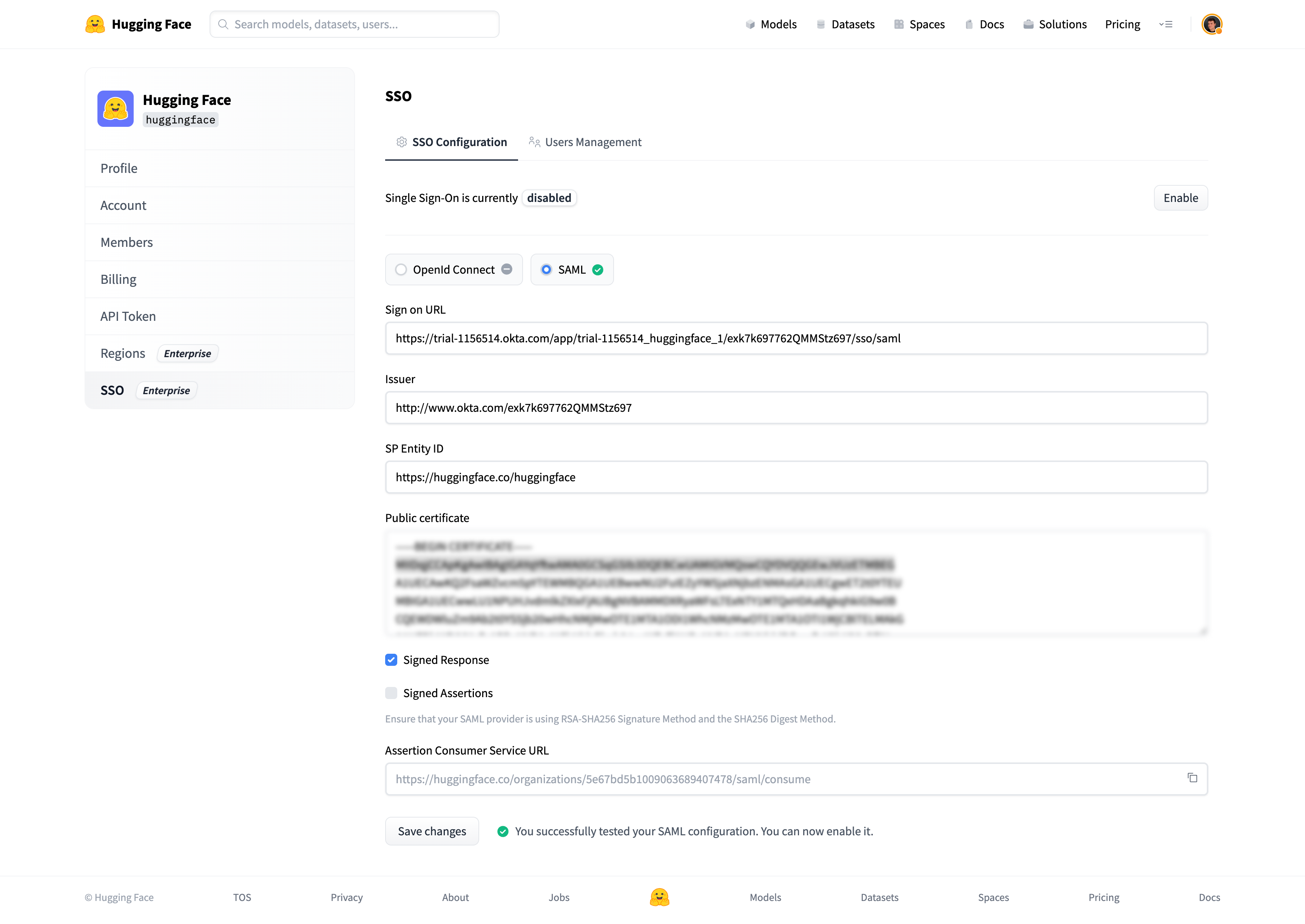
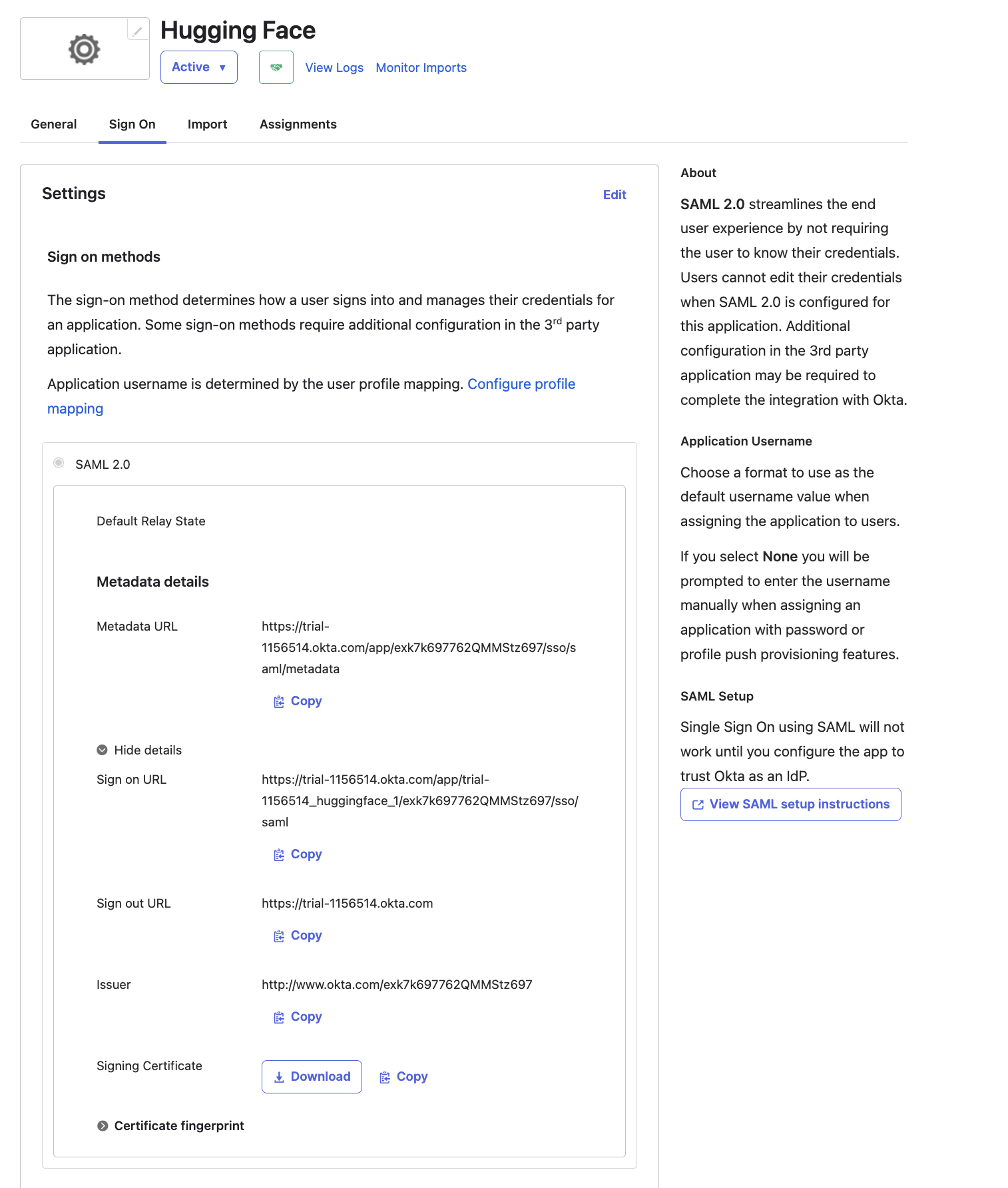 @@ -94,7 +91,6 @@ You should be redirected to your SSO provider (IdP) login prompt. Once logged in
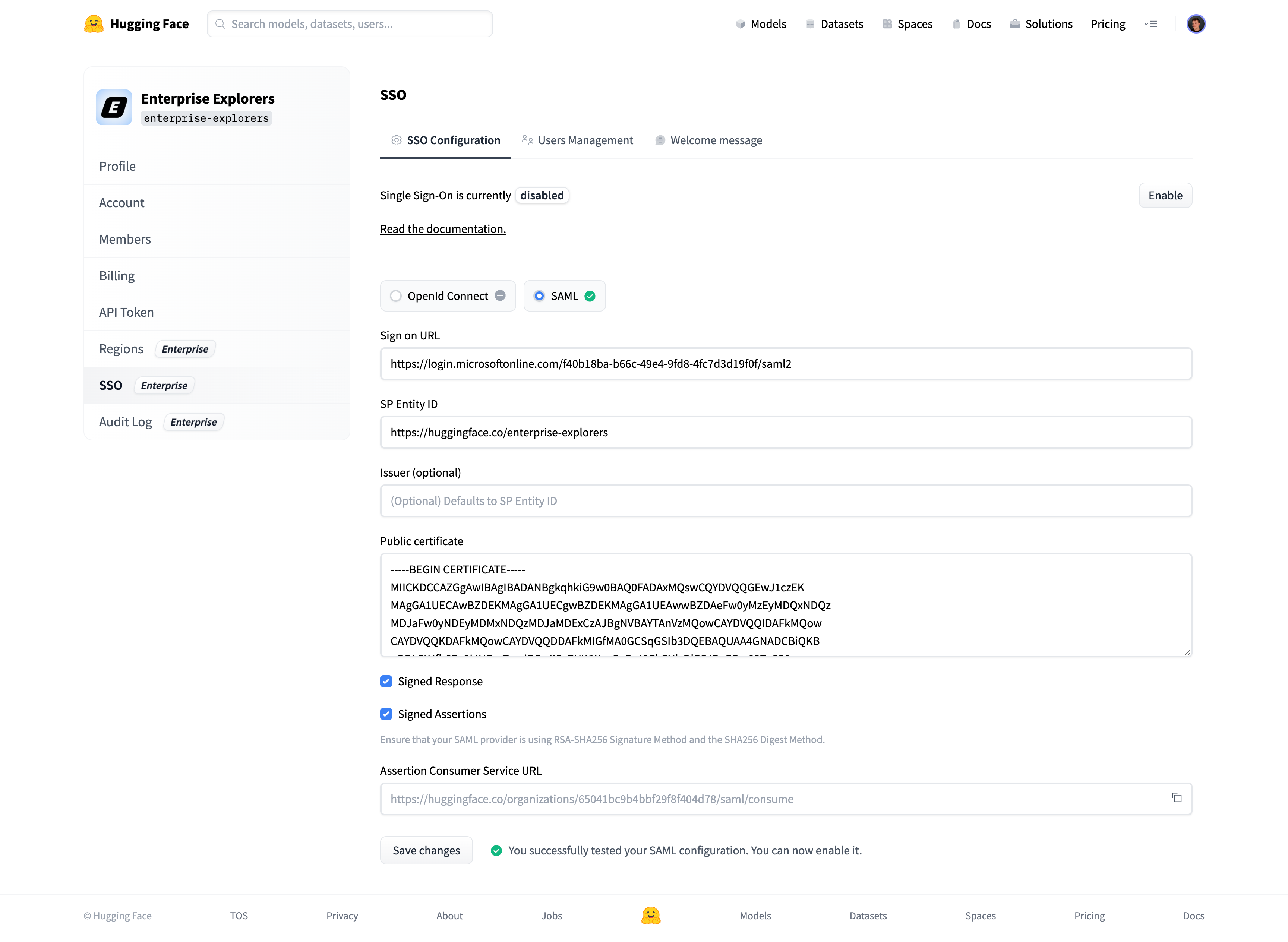
A green check mark near the SAML selector will attest that the test was successful.
-
@@ -94,7 +91,6 @@ You should be redirected to your SSO provider (IdP) login prompt. Once logged in
A green check mark near the SAML selector will attest that the test was successful.
-
 diff --git a/docs/hub/security-sso.md b/docs/hub/security-sso.md
index 1ea4a7dde..c3318f2ce 100644
--- a/docs/hub/security-sso.md
+++ b/docs/hub/security-sso.md
@@ -5,7 +5,7 @@ The Hugging Face Hub gives you the ability to implement mandatory Single Sign-On
We support both SAML 2.0 and OpenID Connect (OIDC) protocols.
diff --git a/docs/hub/security-sso.md b/docs/hub/security-sso.md
index 1ea4a7dde..c3318f2ce 100644
--- a/docs/hub/security-sso.md
+++ b/docs/hub/security-sso.md
@@ -5,7 +5,7 @@ The Hugging Face Hub gives you the ability to implement mandatory Single Sign-On
We support both SAML 2.0 and OpenID Connect (OIDC) protocols.
 +
+  +
+ +
+ +
+ 
 +
+  +
+