

diff --git a/docs/hub/security-sso-azure-saml.md b/docs/hub/security-sso-azure-saml.md
index 1237171b7..578afce84 100644
--- a/docs/hub/security-sso-azure-saml.md
+++ b/docs/hub/security-sso-azure-saml.md
@@ -1,11 +1,11 @@
# How to configure SAML SSO with Azure
-In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.
- This feature is part of the Enterprise Hub.
+ This feature is part of the Enterprise Hub.
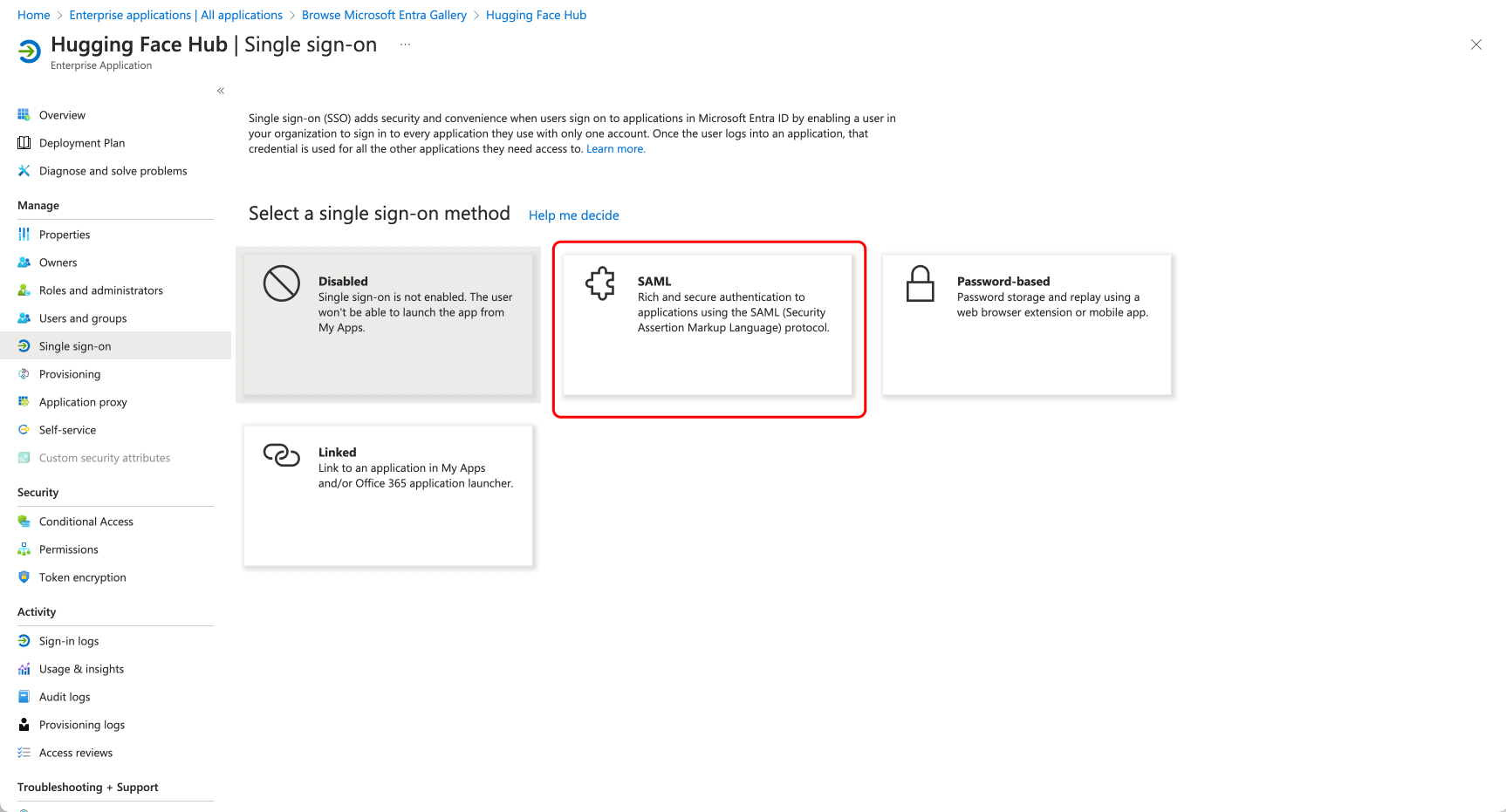
### Step 1: Create a new application in your Identity Provider
@@ -30,7 +30,6 @@ Then select "Single Sign-On", and select SAML
-
### Step 2: Configure your application on Azure
Open a new tab/window in your browser and navigate to the SSO section of your organization's settings. Select the SAML protocol.
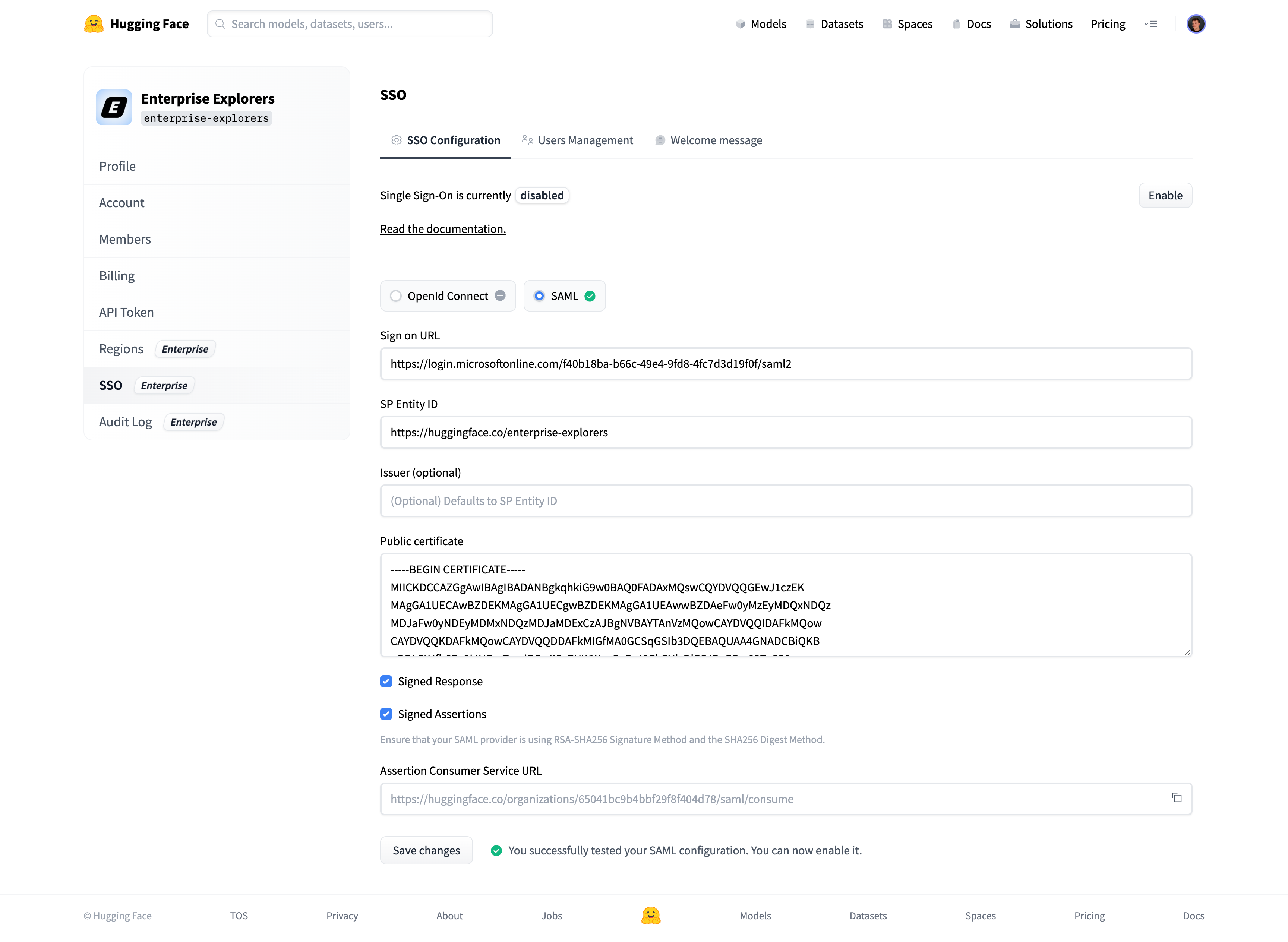
@@ -49,7 +48,6 @@ Copy the "SP Entity Id" from the organization's settings on Hugging Face, and pa
Copy the "Assertion Consumer Service URL" from the organization's settings on Hugging Face, and paste it in the "Reply URL" field on Azure (2).
-
The URL looks like this: `https://huggingface.co/organizations/[organizationIdentifier]/saml/consume`.
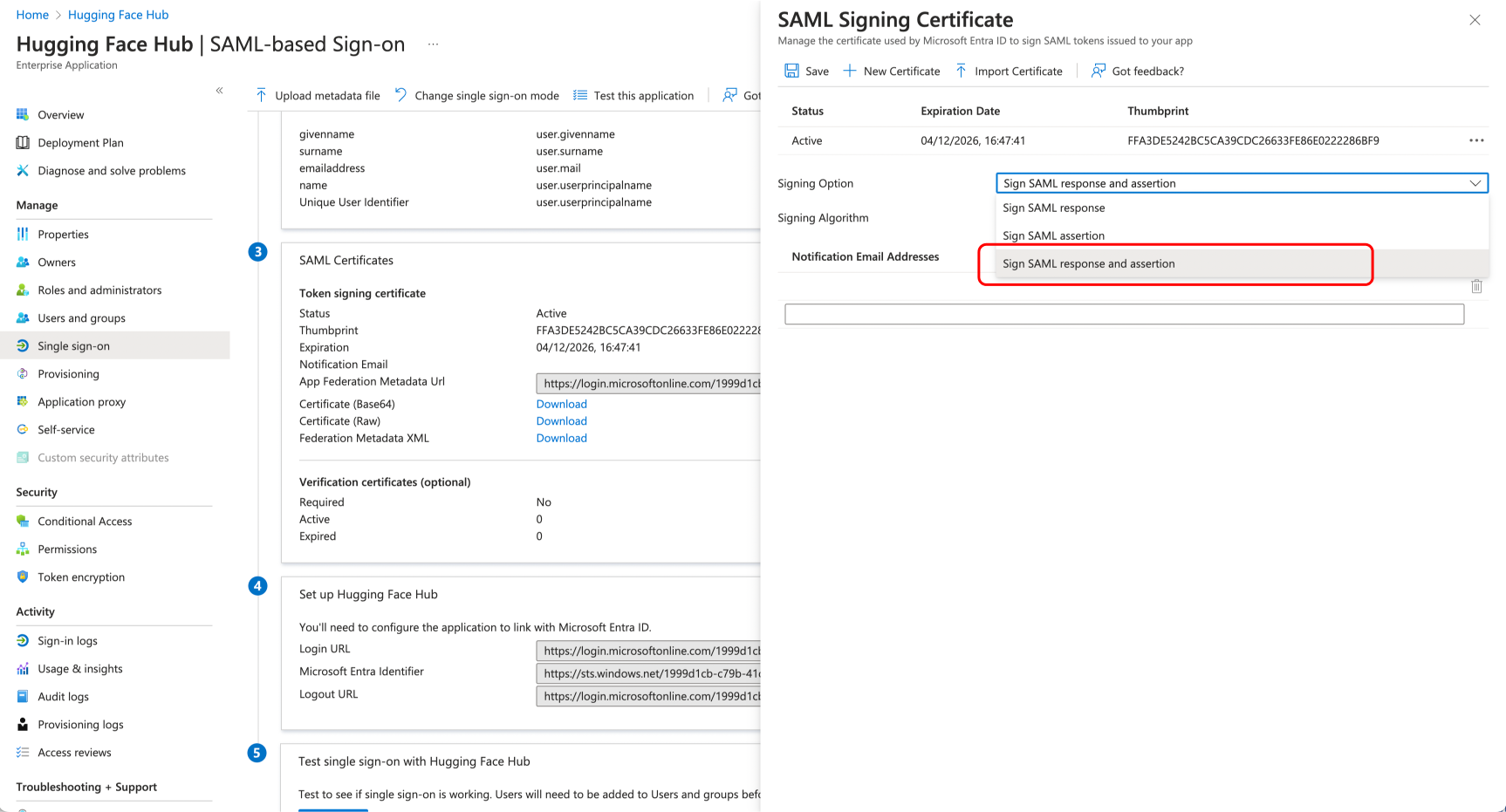
@@ -62,20 +60,20 @@ Then under "SAML Certificates", verify that "Signin Option" is set to "Sign SAML

diff --git a/docs/hub/security-sso-okta-oidc.md b/docs/hub/security-sso-okta-oidc.md
index adcb0821b..92d65bcf0 100644
--- a/docs/hub/security-sso-okta-oidc.md
+++ b/docs/hub/security-sso-okta-oidc.md
@@ -1,9 +1,9 @@
# How to configure OIDC SSO with Okta
-In this guide, we will use Okta as the SSO provider and with the Open ID Connect (OIDC) protocol as our preferred identity protocol.
+In this guide, we will use Okta as the SSO provider and with the Open ID Connect (OIDC) protocol as our preferred identity protocol.
- This feature is part of the Enterprise Hub.
+ This feature is part of the Enterprise Hub.
### Step 1: Create a new application in your Identity Provider
@@ -26,7 +26,6 @@ Then choose an “OIDC - OpenID Connect” application, select the application t
Open a new tab/window in your browser and navigate to the SSO section of your organization's settings. Select the OIDC protocol.
-
-
Save your new application.
### Step 3: Finalize configuration on Hugging Face
In your Okta application, under "General", find the following fields:
+
- Client ID
- Client secret
- Issuer URL
-You will need these to finalize the SSO setup on Hugging Face.
-
+ You will need these to finalize the SSO setup on Hugging Face.
The Okta Issuer URL is generally a URL like `https://tenantId.okta.com`; you can refer to their [guide](https://support.okta.com/help/s/article/What-is-theIssuerlocated-under-the-OpenID-Connect-ID-Token-app-settings-used-for?language=en_US) for more details.
-
-
In the SSO section of your organization's settings on Hugging Face, copy-paste these values from Okta:
- Client ID
@@ -82,7 +78,6 @@ You should be redirected to your SSO provider (IdP) login prompt. Once logged in
A green check mark near the OIDC selector will attest that the test was successful.
-


diff --git a/docs/hub/security-sso-okta-saml.md b/docs/hub/security-sso-okta-saml.md
index 2cab374de..d6e194d10 100644
--- a/docs/hub/security-sso-okta-saml.md
+++ b/docs/hub/security-sso-okta-saml.md
@@ -1,11 +1,11 @@
# How to configure SAML SSO with Okta
-In this guide, we will use Okta as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+In this guide, we will use Okta as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.
- This feature is part of the Enterprise Hub.
+ This feature is part of the Enterprise Hub.
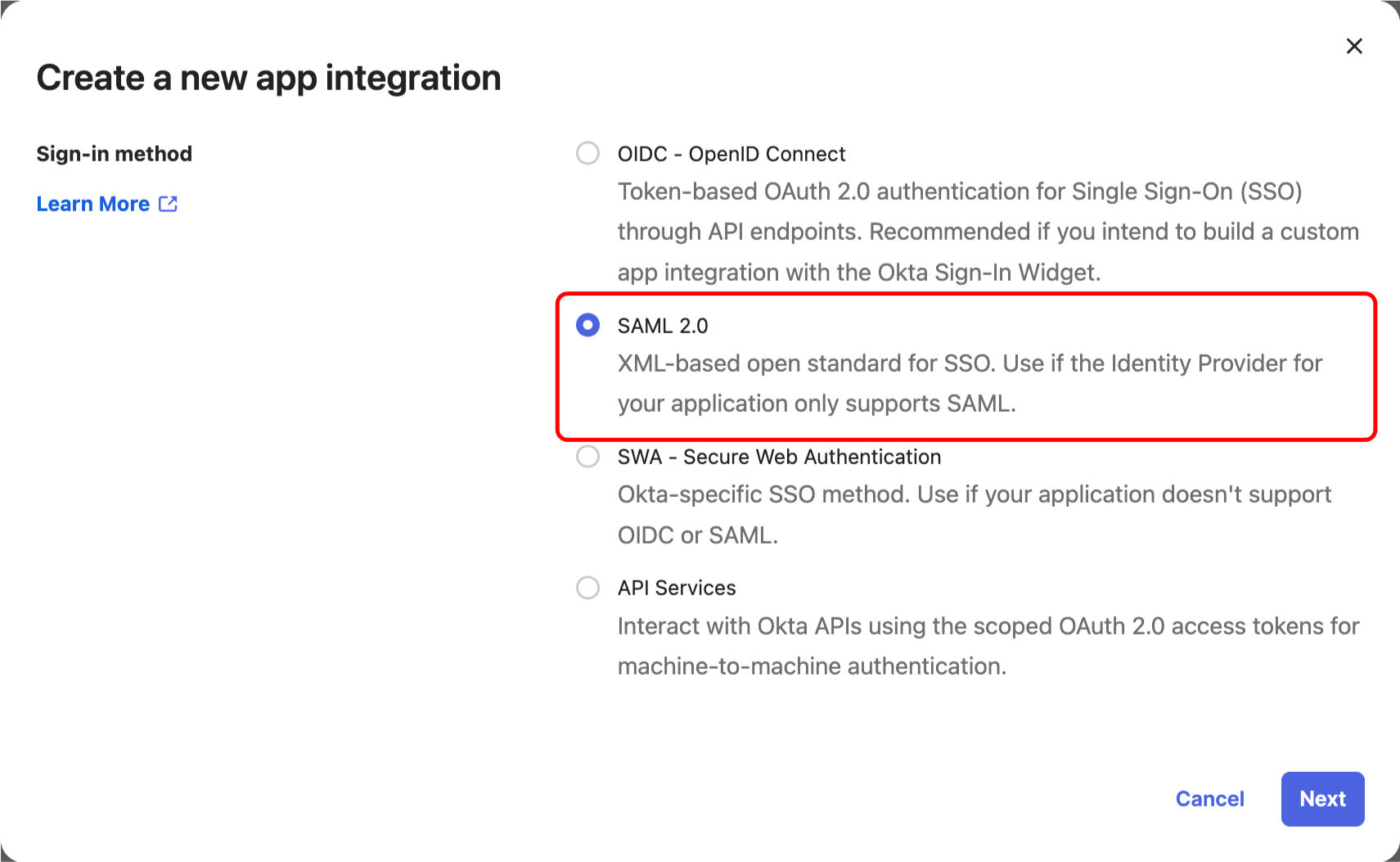
### Step 1: Create a new application in your Identity Provider
@@ -20,12 +20,10 @@ Navigate to "Admin/Applications" and click the "Create App Integration" button.
Then choose an "SAML 2.0" application and click "Create".
-
-
### Step 2: Configure your application on Okta
Open a new tab/window in your browser and navigate to the SSO section of your organization's settings. Select the SAML protocol.
@@ -49,21 +47,20 @@ The URL looks like this: `https://huggingface.co/organizations/[organizationIden
On Okta, set the following settings:
-* Set Audience URI (SP Entity Id) to match the "SP Entity ID" value on Hugging Face.
-* Set Name ID format to EmailAddress.
-* Under "Show Advanced Settings", verify that Response and Assertion Signature are set to: Signed.
-
+- Set Audience URI (SP Entity Id) to match the "SP Entity ID" value on Hugging Face.
+- Set Name ID format to EmailAddress.
+- Under "Show Advanced Settings", verify that Response and Assertion Signature are set to: Signed.
Save your new application.
### Step 3: Finalize configuration on Hugging Face
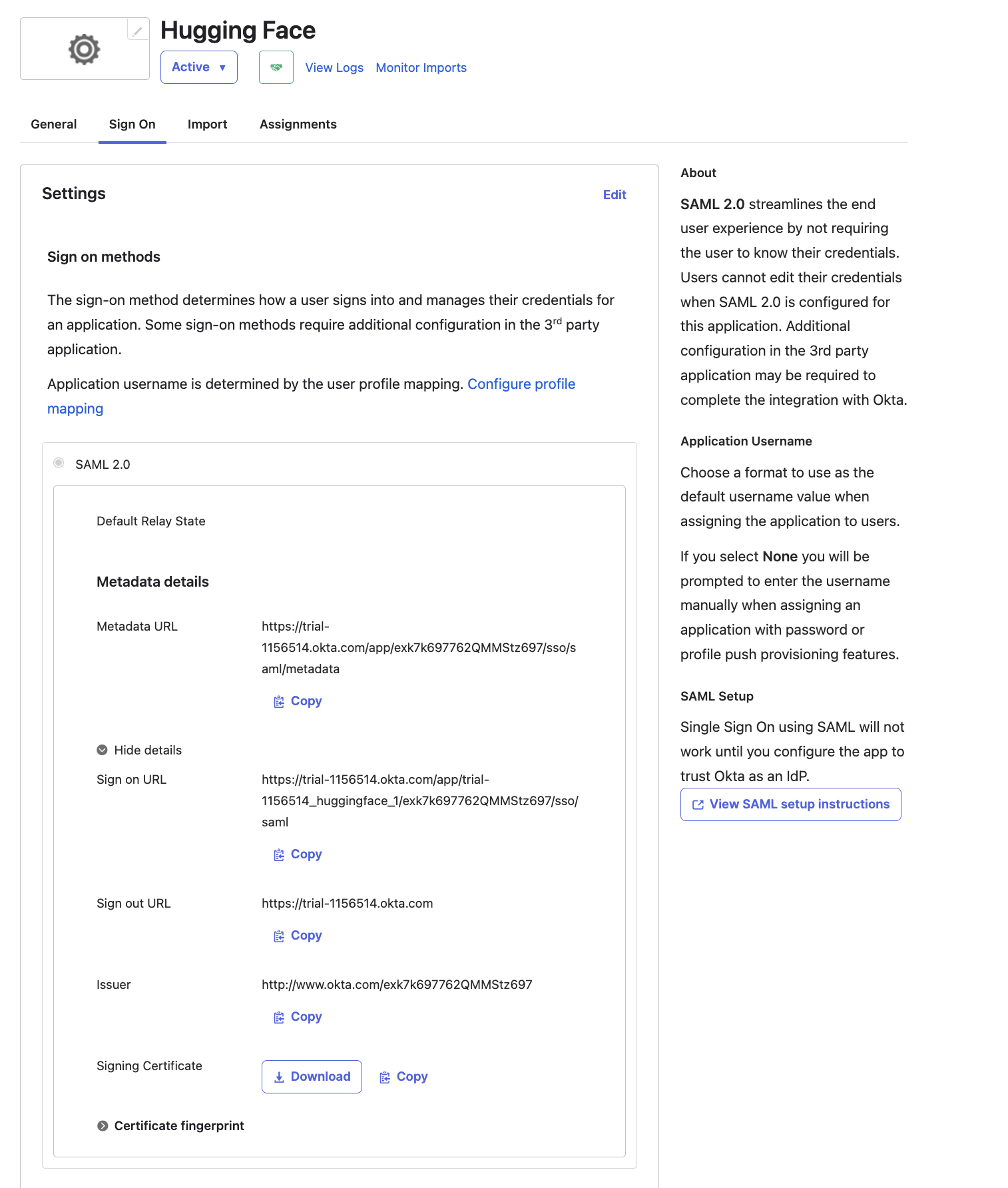
In your Okta application, under "Sign On/Settings/More details", find the following fields:
+
- Sign-on URL
- Public certificate
- SP Entity ID
-You will need them to finalize the SSO setup on Hugging Face.
-
+ You will need them to finalize the SSO setup on Hugging Face.
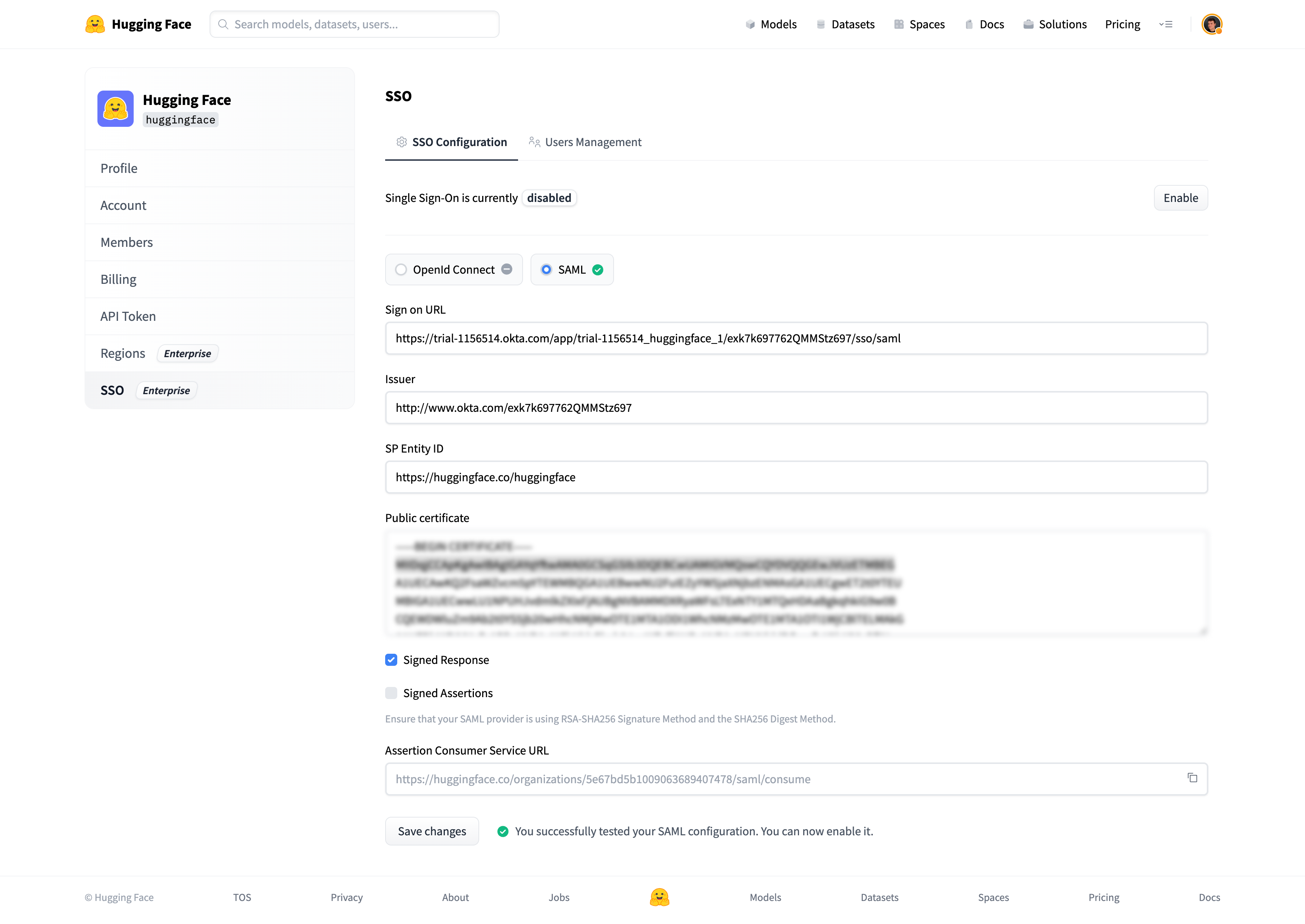
@@ -94,7 +91,6 @@ You should be redirected to your SSO provider (IdP) login prompt. Once logged in
A green check mark near the SAML selector will attest that the test was successful.
-
diff --git a/docs/hub/security-sso.md b/docs/hub/security-sso.md
index 1ea4a7dde..c3318f2ce 100644
--- a/docs/hub/security-sso.md
+++ b/docs/hub/security-sso.md
@@ -5,7 +5,7 @@ The Hugging Face Hub gives you the ability to implement mandatory Single Sign-On
We support both SAML 2.0 and OpenID Connect (OIDC) protocols.
-This feature is part of the Enterprise Hub.
+This feature is part of the Enterprise Hub.
## How does it work?
@@ -73,12 +73,11 @@ If there is no match, a user will be assigned the default role for your organiza
Role synchronization is performed on login.
-
#### External Collaborators
This enables certain users within your organization to access resources without completing the Single Sign-On (SSO) flow described before. This can be helpful when you work with external parties who aren't part of your organization's Identity Provider (IdP) but require access to specific resources.
-To add a user as an "External Collaborator" visit the `SSO/Users Management` section in your organization's settings. Once added, these users won't need to go through the SSO process.
+To add a user as an "External Collaborator" visit the `SSO/Users Management` section in your organization's settings. Once added, these users won't need to go through the SSO process.
-However, they will still be subject to your organization's access controls ([Resource Groups](./security-resource-groups)).
+However, they will still be subject to your organization's access controls ([Resource Groups](./security-resource-groups)).
It's crucial to manage their access carefully to maintain your organization's data security.
diff --git a/docs/hub/storage-regions.md b/docs/hub/storage-regions.md
index d6a8dd3da..f07882307 100644
--- a/docs/hub/storage-regions.md
+++ b/docs/hub/storage-regions.md
@@ -1,7 +1,7 @@
# Storage Regions on the Hub
-This feature is part of the Enterprise Hub.
+This feature is part of the Enterprise Hub.
Regions allow you to specify where your organization's models and datasets are stored.


 -
## Viewing members' email address
-
## Viewing members' email address


 -
Copy the "Redirection URI" from the organization's settings on Hugging Face and paste it into the "Redirect URI" field on Azure Entra ID. Make sure you select "Web" in the dropdown menu.
The URL looks like this: `https://huggingface.co/organizations/[organizationIdentifier]/oidc/consume`.
@@ -57,6 +54,7 @@ Save your new application.
### Step 3: Finalize configuration on Hugging Face
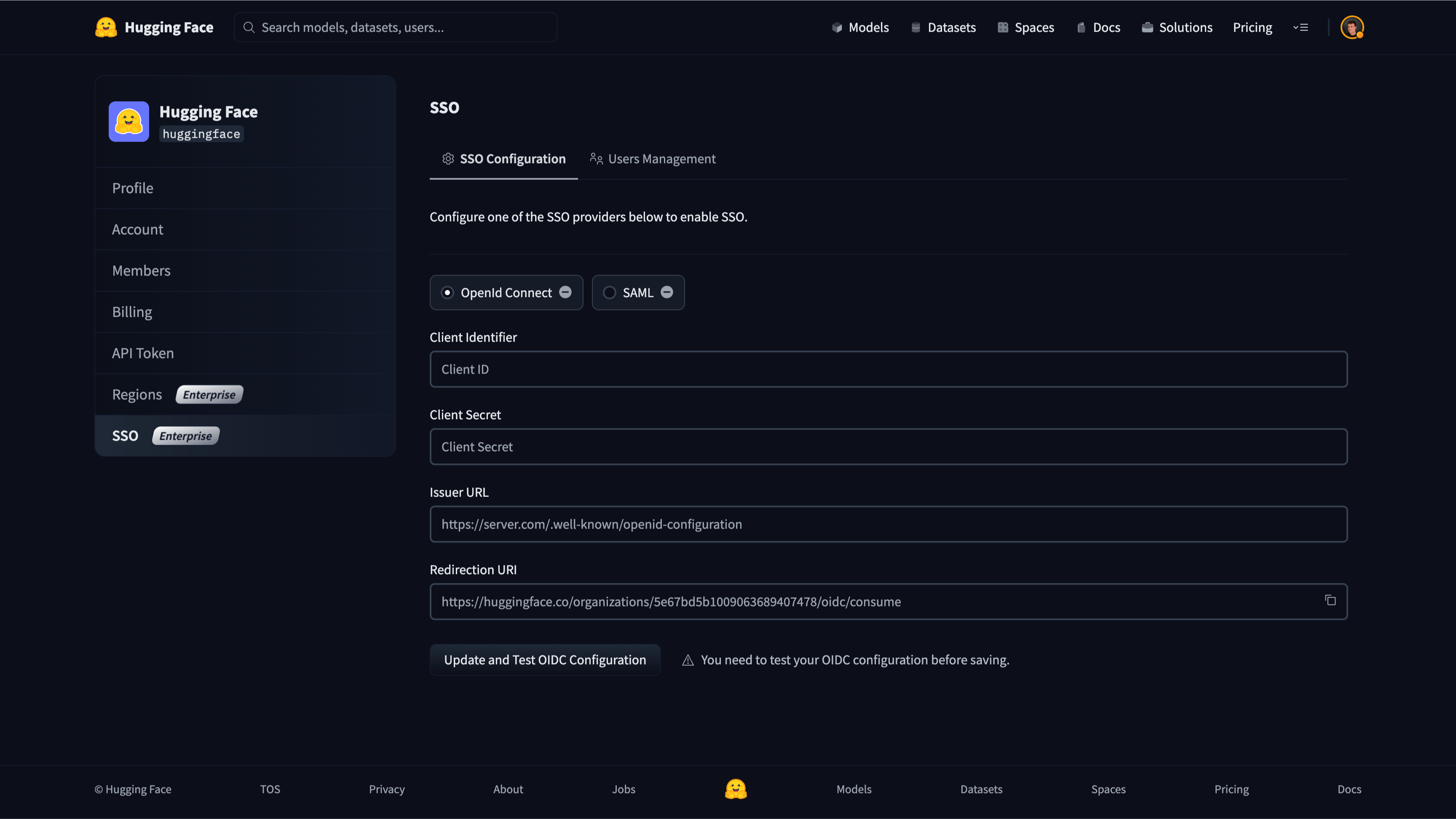
We will need to collect the following information to finalize the setup on Hugging Face:
+
- The Client ID of the OIDC app
- A Client secret of the OIDC app
- The Issuer URL of the OIDC app
@@ -99,14 +97,12 @@ Once you have created the secret, copy the secret value and paste it into the "C
-
Copy the "Redirection URI" from the organization's settings on Hugging Face and paste it into the "Redirect URI" field on Azure Entra ID. Make sure you select "Web" in the dropdown menu.
The URL looks like this: `https://huggingface.co/organizations/[organizationIdentifier]/oidc/consume`.
@@ -57,6 +54,7 @@ Save your new application.
### Step 3: Finalize configuration on Hugging Face
We will need to collect the following information to finalize the setup on Hugging Face:
+
- The Client ID of the OIDC app
- A Client secret of the OIDC app
- The Issuer URL of the OIDC app
@@ -99,14 +97,12 @@ Once you have created the secret, copy the secret value and paste it into the "C
 -
You can now click "Update and Test OIDC configuration" to save the settings.
You should be redirected to your SSO provider (IdP) login prompt. Once logged in, you'll be redirected to your organization's settings page.
A green check mark near the OIDC selector will attest that the test was successful.
-
-
You can now click "Update and Test OIDC configuration" to save the settings.
You should be redirected to your SSO provider (IdP) login prompt. Once logged in, you'll be redirected to your organization's settings page.
A green check mark near the OIDC selector will attest that the test was successful.
-

 diff --git a/docs/hub/security-sso-azure-saml.md b/docs/hub/security-sso-azure-saml.md
index 1237171b7..578afce84 100644
--- a/docs/hub/security-sso-azure-saml.md
+++ b/docs/hub/security-sso-azure-saml.md
@@ -1,11 +1,11 @@
# How to configure SAML SSO with Azure
-In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.
diff --git a/docs/hub/security-sso-azure-saml.md b/docs/hub/security-sso-azure-saml.md
index 1237171b7..578afce84 100644
--- a/docs/hub/security-sso-azure-saml.md
+++ b/docs/hub/security-sso-azure-saml.md
@@ -1,11 +1,11 @@
# How to configure SAML SSO with Azure
-In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+In this guide, we will use Azure as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.



 diff --git a/docs/hub/security-sso-okta-oidc.md b/docs/hub/security-sso-okta-oidc.md
index adcb0821b..92d65bcf0 100644
--- a/docs/hub/security-sso-okta-oidc.md
+++ b/docs/hub/security-sso-okta-oidc.md
@@ -1,9 +1,9 @@
# How to configure OIDC SSO with Okta
-In this guide, we will use Okta as the SSO provider and with the Open ID Connect (OIDC) protocol as our preferred identity protocol.
+In this guide, we will use Okta as the SSO provider and with the Open ID Connect (OIDC) protocol as our preferred identity protocol.
diff --git a/docs/hub/security-sso-okta-oidc.md b/docs/hub/security-sso-okta-oidc.md
index adcb0821b..92d65bcf0 100644
--- a/docs/hub/security-sso-okta-oidc.md
+++ b/docs/hub/security-sso-okta-oidc.md
@@ -1,9 +1,9 @@
# How to configure OIDC SSO with Okta
-In this guide, we will use Okta as the SSO provider and with the Open ID Connect (OIDC) protocol as our preferred identity protocol.
+In this guide, we will use Okta as the SSO provider and with the Open ID Connect (OIDC) protocol as our preferred identity protocol.
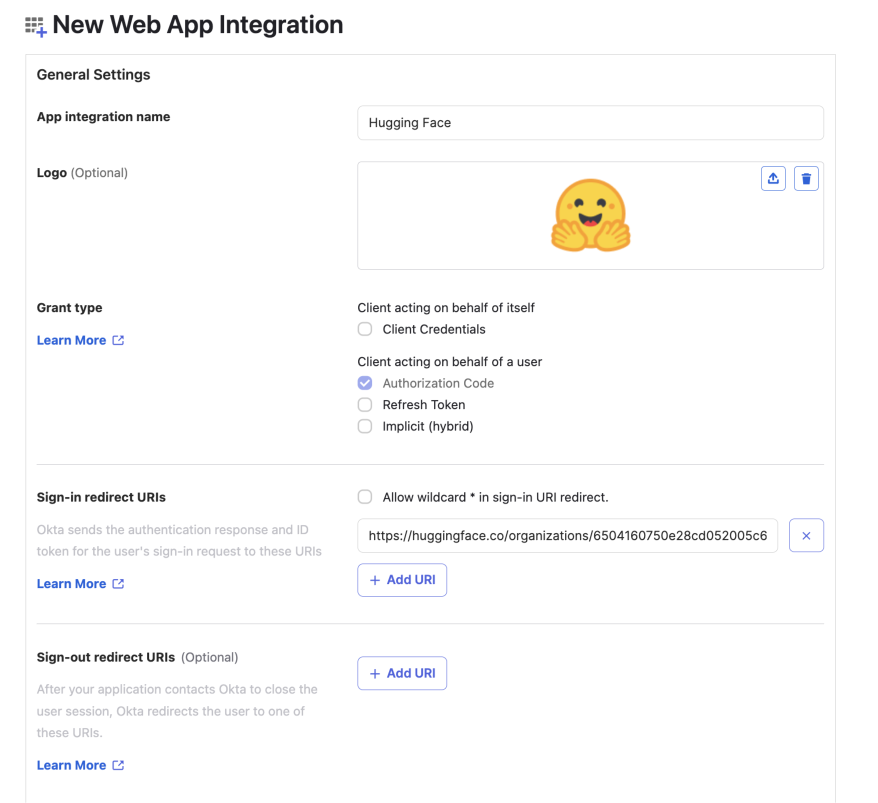
 @@ -46,26 +45,23 @@ You can leave the optional Sign-out redirect URIs blank.
@@ -46,26 +45,23 @@ You can leave the optional Sign-out redirect URIs blank.


 diff --git a/docs/hub/security-sso-okta-saml.md b/docs/hub/security-sso-okta-saml.md
index 2cab374de..d6e194d10 100644
--- a/docs/hub/security-sso-okta-saml.md
+++ b/docs/hub/security-sso-okta-saml.md
@@ -1,11 +1,11 @@
# How to configure SAML SSO with Okta
-In this guide, we will use Okta as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+In this guide, we will use Okta as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.
diff --git a/docs/hub/security-sso-okta-saml.md b/docs/hub/security-sso-okta-saml.md
index 2cab374de..d6e194d10 100644
--- a/docs/hub/security-sso-okta-saml.md
+++ b/docs/hub/security-sso-okta-saml.md
@@ -1,11 +1,11 @@
# How to configure SAML SSO with Okta
-In this guide, we will use Okta as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
+In this guide, we will use Okta as the SSO provider and with the Security Assertion Markup Language (SAML) protocol as our preferred identity protocol.
We currently support SP-initiated and IdP-initiated authentication. User provisioning is not yet supported at this time.

 @@ -94,7 +91,6 @@ You should be redirected to your SSO provider (IdP) login prompt. Once logged in
A green check mark near the SAML selector will attest that the test was successful.
-
@@ -94,7 +91,6 @@ You should be redirected to your SSO provider (IdP) login prompt. Once logged in
A green check mark near the SAML selector will attest that the test was successful.
-

 diff --git a/docs/hub/security-sso.md b/docs/hub/security-sso.md
index 1ea4a7dde..c3318f2ce 100644
--- a/docs/hub/security-sso.md
+++ b/docs/hub/security-sso.md
@@ -5,7 +5,7 @@ The Hugging Face Hub gives you the ability to implement mandatory Single Sign-On
We support both SAML 2.0 and OpenID Connect (OIDC) protocols.
diff --git a/docs/hub/security-sso.md b/docs/hub/security-sso.md
index 1ea4a7dde..c3318f2ce 100644
--- a/docs/hub/security-sso.md
+++ b/docs/hub/security-sso.md
@@ -5,7 +5,7 @@ The Hugging Face Hub gives you the ability to implement mandatory Single Sign-On
We support both SAML 2.0 and OpenID Connect (OIDC) protocols.