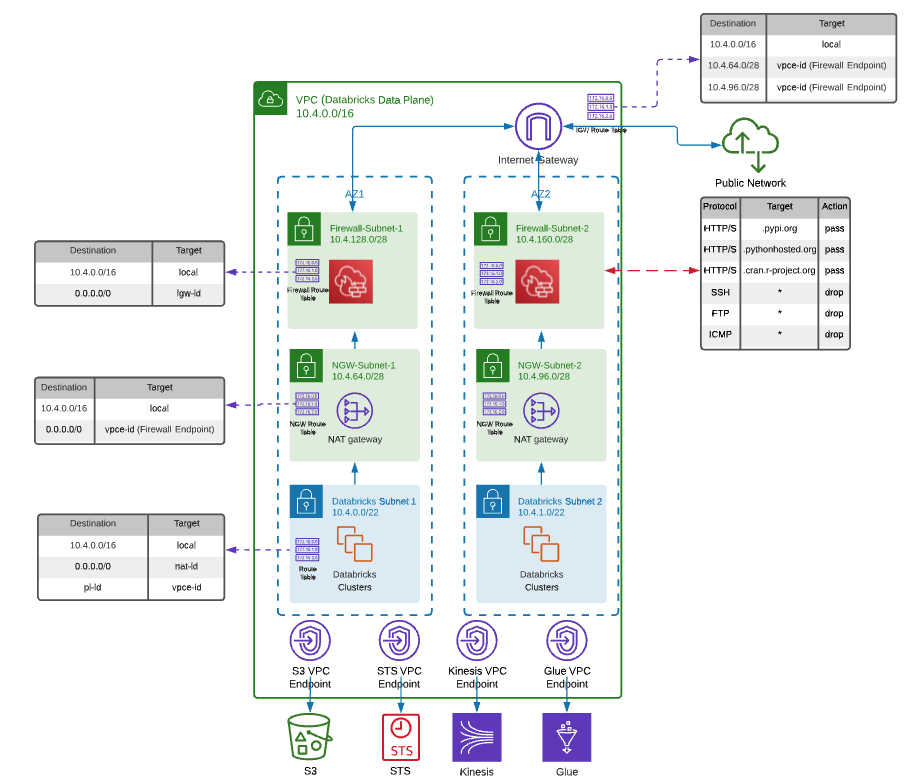
This template provides an example deployment of AWS Databricks E2 workspace with an AWS Firewall.
Note
The following Terraform guide provides step-by-step instructions for this deployment.
Resources to be created:
- VPC and VPC endpoints
- AWS NAT Gateway and Internet Gateway
- AWS Network Firewall
- S3 Root bucket
- Cross-account IAM role
- Databricks E2 workspace
Note
You can customize this module by adding, deleting or updating the Azure resources to adapt the module to your requirements. A deployment example using this module can be found in examples/aws-workspace-with-firewall If you are using AWS Firewall to block most traffic but allow the URLs that Databricks needs to connect to, please update the configuration based on your region. You can get the configuration details for your region from Firewall Appliance document.
- Reference this module using one of the different module source types
- Add a
variables.tfwith the same content in variables.tf - Add a
terraform.tfvarsfile and provide values to each defined variable - Configure the following environment variables:
- TF_VAR_databricks_account_client_id, set to the value of application ID of your Databricks account-level service principal with admin permission.
- TF_VAR_databricks_account_client_secret, set to the value of the client secret for your Databricks account-level service principal.
- TF_VAR_databricks_account_id, set to the value of the ID of your Databricks account. You can find this value in the corner of your Databricks account console.
- Add a
output.tffile. - (Optional) Configure your remote backend
- Run
terraform initto initialize terraform and get provider ready. - Run
terraform applyto create the resources.