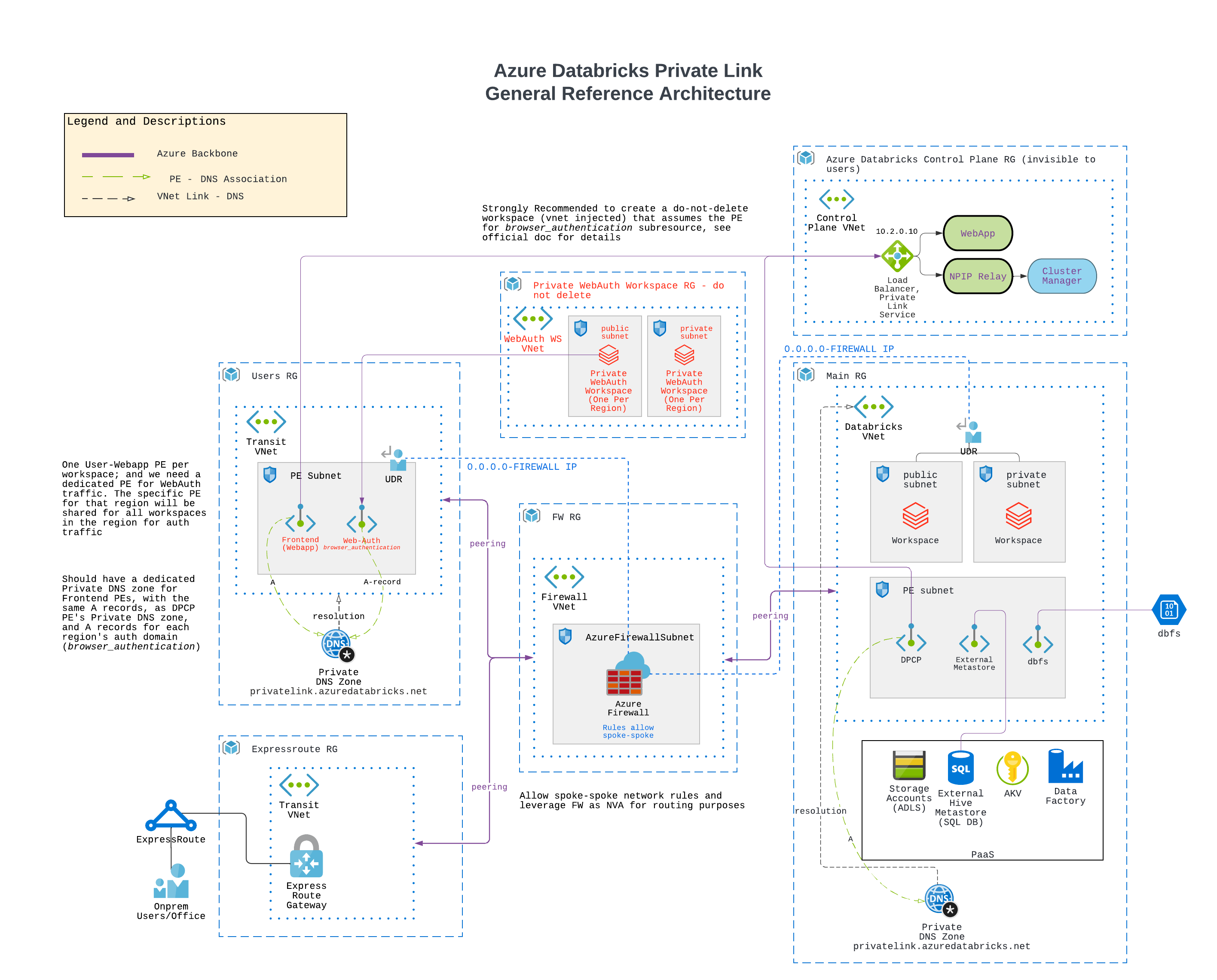
Azure Databricks with Private Links (incl. web-auth PE) and Hub-Spoke Firewall structure (data exfiltration protection).
Include:
- Hub-Spoke networking with egress firewall to control all outbound traffic, e.g. to pypi.org.
- Private Link connection for backend traffic from data plane to control plane.
- Private Link connection from user client to webapp service.
- Private Link connection from data plane to dbfs storage.
- Private Endpoint for web-auth traffic.
With this deployment, traffic from user client to webapp (notebook UI), backend traffic from data plane to control plane will be through private endpoints. This terraform sample will create:
- Resource group with random prefix
- Tags, including
Owner, which is taken fromaz account show --query user - VNet with public and private subnet and subnet to host private endpoints
- Databricks workspace with private link to control plane, user to webapp and private link to dbfs
Note
You can customize this module by adding, deleting or updating the Azure resources to adapt the module to your requirements. A deployment example using this module can be found in examples/adb-with-private-links-exfiltration-protection
- Reference this module using one of the different module source types
- Add a
variables.tfwith the same content in variables.tf - Add a
terraform.tfvarsfile and provide values to each defined variable - Add a
output.tffile. - (Optional) Configure your remote backend
- Run
terraform initto initialize terraform and get provider ready. - Run
terraform applyto create the resources.
| Name | Version |
|---|---|
| azurerm | >=4.0.0 |
| Name | Version |
|---|---|
| azurerm | >=4.0.0 |
| external | n/a |
| http | n/a |
| random | n/a |
No modules.
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| dbfs_prefix | Prefix for DBFS storage account name | string |
"dbfs" |
no |
| firewallfqdn | Additional list of fully qualified domain names to add to firewall rules | list(any) |
n/a | yes |
| hubcidr | CIDR for Hub VNet | string |
"10.178.0.0/20" |
no |
| metastoreip | IP Address of built-in Hive Metastore in the target region | string |
n/a | yes |
| private_subnet_endpoints | The list of Service endpoints to associate with the private subnet. | list(string) |
[] |
no |
| rglocation | Location of resource group to create | string |
"southeastasia" |
no |
| spokecidr | CIDR for Spoke VNet | string |
"10.179.0.0/20" |
no |
| tags | map of tags to add to all resources | map(any) |
{} |
no |
| test_vm_password | Password for Test VM | string |
"TesTed567!!!" |
no |
| workspace_prefix | Prefix to use for Workspace name | string |
"adb" |
no |
| Name | Description |
|---|---|
| arm_client_id | Depricated. Client ID for current user/service principal |
| arm_subscription_id | Depricated. Azure Subscription ID for current user/service principal |
| arm_tenant_id | Depricated. Azure Tenant ID for current user/service principal |
| azure_region | Depricated. Geo location of created resources |
| azure_resource_group_id | ID of the created Azure resource group |
| databricks_azure_workspace_resource_id | Depricated. The ID of the Databricks Workspace in the Azure management plane. |
| my_ip_addr | Depricated. IP address of caller |
| resource_group | Name of created resource group |
| test_vm_public_ip | Public IP of the created virtual machine |
| workspace_id | The Databricks workspace ID |
| workspace_url | The workspace URL which is of the format 'adb-{workspaceId}.{random}.azuredatabricks.net' |