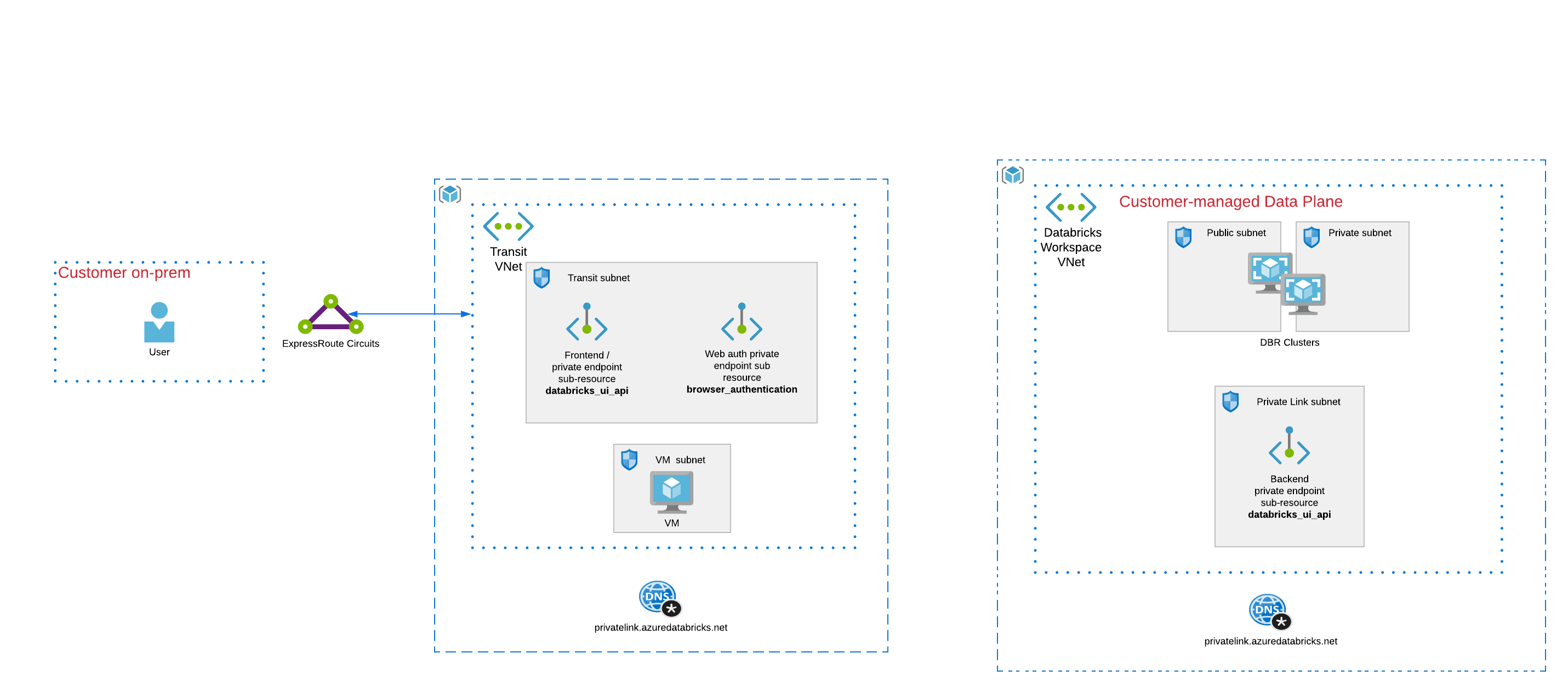
This example contains Terraform code used to deploy an Azure Databricks workspace with Azure Private Link, using the standard deployment approach.
It is using the adb-with-private-link-standard module.
This example can be used to deploy the following:
- Two seperate VNets are used:
- A transit VNet
- A customer Data Plane VNet
- A private endpoint is used for back-end connectivity and deployed in the customer Data Plane VNet.
- A private endpoint is used for front-end connectivity and deployed in the transit VNet.
- A private endpoint is used for web authentication and deployed in the transit VNet.
- A dedicated Databricks workspace, called Web Auth workspace, is used for web authentication traffic. This workspace is configured with the sub resource browser_authentication and deployed using subnets in the transit VNet.
- Update
terraform.tfvarsfile and provide values to each defined variable - (Optional) Configure your remote backend
- Run
terraform initto initialize terraform and get provider ready. - Run
terraform applyto create the resources.
Public access to the workspace deployed here is not allowed by default. If you can establish a direct network connection to the VNet into which the workspace is deployed then you should be able to browse the workspace directly. Alternatively, a virtual machine is created as part of this deployment allowing you to connect to the workspace in case you don't have direct network path to the VNet in which the workspace is deployed. You can use the test_vm_public_ip and test_vm_password to log into this VM (password value is marked as sensitive but can be found in the teraform.tfstate file). By default, access to this machine is only allowed from the deployer's public IP address. To allow access from other sources, extra rules can be added to the Network Security Group created for the VM as part of this deployment.