diff --git a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.py b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.py
index 322f55a157b7..b16f45fea552 100644
--- a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.py
+++ b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.py
@@ -1,6 +1,7 @@
-import demistomock as demisto
-from CommonServerPython import *
-from CommonServerUserPython import *
+import demistomock as demisto # noqa: F401
+from CommonServerPython import * # noqa: F401
+
+
import boto3
from botocore.config import Config
from botocore.parsers import ResponseParserError
@@ -104,8 +105,8 @@ def aws_session(service='cloudtrail', region=None, roleArn=None, roleSessionName
def handle_returning_date_to_string(date_obj: datetime | str) -> str:
"""Gets date object to string"""
- # if the returning date is a string leave it as is.
- if isinstance(date_obj, str):
+ # if the returning date is a string or None, leave it as is.
+ if date_obj is None or isinstance(date_obj, str):
return date_obj
# if event time is datetime object - convert it to string.
@@ -238,6 +239,40 @@ def describe_trails(args: dict) -> CommandResults:
)
+def get_trail_status(args: dict) -> CommandResults:
+ client = aws_session(
+ region=args.get('region'),
+ roleArn=args.get('roleArn'),
+ roleSessionName=args.get('roleSessionName'),
+ roleSessionDuration=args.get('roleSessionDuration'),
+ )
+
+ kwargs = {'Name': args.get('name')}
+
+ response = client.get_trail_status(**kwargs)
+
+ data = {
+ 'IsLogging': response.get('IsLogging'),
+ 'LatestDeliveryTime': handle_returning_date_to_string(response.get('LatestDeliveryTime')),
+ 'LatestCloudWatchLogsDeliveryError': response.get('LatestCloudWatchLogsDeliveryError'),
+ 'LatestDeliveryErrorDetails': response.get('LatestDeliveryErrorDetails'),
+ 'LatestNotificationError': response.get('LatestNotificationError'),
+ 'LatestNotificationTime': handle_returning_date_to_string(response.get('LatestNotificationTime')),
+ 'StartLoggingTime': handle_returning_date_to_string(response.get('StartLoggingTime')),
+ 'StopLoggingTime': handle_returning_date_to_string(response.get('StopLoggingTime')),
+ 'LatestCloudWatchLogsDeliveryTime': handle_returning_date_to_string(response.get('LatestCloudWatchLogsDeliveryTime')),
+ 'LatestDigestDeliveryTime': handle_returning_date_to_string(response.get('LatestDigestDeliveryTime')),
+ 'LatestDigestDeliveryError': response.get('LatestDigestDeliveryError')
+ }
+
+ return CommandResults(
+ outputs_prefix="AWS.CloudTrail.TrailStatus",
+ outputs_key_field="Name",
+ outputs=data,
+ readable_output=tableToMarkdown('AWS CloudTrail TrailStatus', data),
+ )
+
+
def update_trail(args: dict) -> CommandResults:
client = aws_session(
region=args.get('region'),
@@ -409,6 +444,8 @@ def main():
return_results(stop_logging(args))
if command == 'aws-cloudtrail-lookup-events':
return_results(lookup_events(args))
+ if command == 'aws-cloudtrail-get-trail-status':
+ return_results(get_trail_status(args))
except Exception as e:
err = "Error has occurred in the AWS CloudTrail Integration."
diff --git a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.yml b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.yml
index 96f55b80a2b2..dde5a179614c 100644
--- a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.yml
+++ b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.yml
@@ -371,9 +371,60 @@ script:
- contextPath: AWS.CloudTrail.Events.CloudTrailEvent
description: A JSON string that contains a representation of the event returned.
type: string
+ - arguments:
+ - description: Specifies the names of multiple trails.
+ name: trailNameList
+ - description: Specifies the region of the trail.
+ name: region
+ required: true
+ - description: The The Amazon Resource Name (ARN) of the role to assume.
+ name: roleArn
+ - description: An identifier for the assumed role session.
+ name: roleSessionName
+ - description: The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role.
+ name: roleSessionDuration
+ - description: Specifies the name of the trail.
+ name: name
+ required: true
+ description: Returns a JSON-formatted list of information about the specified trail. Fields include information on delivery errors, Amazon SNS and Amazon S3 errors, and start and stop logging times for each trail.
+ name: aws-cloudtrail-get-trail-status
+ outputs:
+ - contextPath: AWS.CloudTrail.TrailStatus.IsLogging
+ description: Whether the CloudTrail trail is currently logging Amazon Web Services API calls.
+ type: boolean
+ - contextPath: AWS.CloudTrail.TrailStatus.LatestDeliveryError
+ description: Displays any Amazon S3 error that CloudTrail encountered when attempting to deliver log files to the designated bucket.
+ type: string
+ - contextPath: AWS.CloudTrail.TrailStatus.LatestNotificationError
+ description: Displays any Amazon SNS error that CloudTrail encountered when attempting to send a notification.
+ type: string
+ - contextPath: AWS.CloudTrail.TrailStatus.LatestDeliveryTime
+ description: Specifies the date and time that CloudTrail last delivered log files to an account’s Amazon S3 bucket.
+ type: date
+ - contextPath: AWS.CloudTrail.TrailStatus.LatestNotificationTime
+ description: Specifies the date and time of the most recent Amazon SNS notification that CloudTrail has written a new log file to an account’s Amazon S3 bucket.
+ type: date
+ - contextPath: AWS.CloudTrail.TrailStatus.StartLoggingTime
+ description: Specifies the most recent date and time when CloudTrail started recording API calls for an Amazon Web Services account.
+ type: date
+ - contextPath: AWS.CloudTrail.TrailStatus.StopLoggingTime
+ description: Specifies the most recent date and time when CloudTrail stopped recording API calls for an Amazon Web Services account.
+ type: date
+ - contextPath: AWS.CloudTrail.TrailStatus.LatestCloudWatchLogsDeliveryError
+ description: Displays any CloudWatch Logs error that CloudTrail encountered when attempting to deliver logs to CloudWatch Logs.
+ type: string
+ - contextPath: AWS.CloudTrail.TrailStatus.LatestCloudWatchLogsDeliveryTime
+ description: Displays the most recent date and time when CloudTrail delivered logs to CloudWatch Logs.
+ type: date
+ - contextPath: AWS.CloudTrail.TrailStatus.LatestDigestDeliveryTime
+ description: Specifies the date and time that CloudTrail last delivered a digest file to an account’s Amazon S3 bucket.
+ type: date
+ - contextPath: AWS.CloudTrail.TrailStatus.LatestDigestDeliveryError
+ description: Displays any Amazon S3 error that CloudTrail encountered when attempting to deliver a digest file to the designated bucket.
+ type: string
dockerimage: demisto/boto3py3:1.0.0.89556
runonce: false
- script: '-'
+ script: ''
subtype: python3
type: python
tests:
diff --git a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail_description.md b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail_description.md
index 45a7420390ac..a3cec4b1f0cb 100644
--- a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail_description.md
+++ b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail_description.md
@@ -11,4 +11,4 @@ on your AWS environment.
- Attach a Role to the Instance Profile.
- Configure the Necessary IAM Roles that the AWS Integration Can Assume.
-For detailed instructions, see the [AWS Integrations - Authentication](https://xsoar.pan.dev/docs/reference/articles/aws-integrations---authentication).
+For detailed instructions, see the [AWS Integrations - Authentication](https://xsoar.pan.dev/docs/reference/articles/aws-integrations---authentication).
\ No newline at end of file
diff --git a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail_test.py b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail_test.py
index c8b5ace4239f..4c3eee8c0ba4 100644
--- a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail_test.py
+++ b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail_test.py
@@ -93,6 +93,9 @@ def stop_logging(self, **kwargs):
def lookup_events(self, **kwargs):
return None
+ def get_trail_status(self, **kwargs):
+ return {"IsLogging": True}
+
def get_paginator(self, _):
class Paginator:
def paginate(self, **kwargs):
@@ -297,3 +300,20 @@ def test_cloudtrail_lookup_events(mocker, aws_cloudtrail, return_results_func):
command_result: CommandResults = return_results_func.call_args[0][0]
outputs: list[dict] = command_result.outputs
assert outputs[0]["Username"] == "user"
+
+
+def test_cloudtrail_get_trail_status(mocker, aws_cloudtrail, return_results_func):
+ """
+ Given
+ - demisto args
+ When
+ - running aws-cloudtrail-get-trail-status command
+ Then
+ - Ensure the command result is returned as expected
+ """
+ args = {"name": "name"}
+ mock_command(mocker, aws_cloudtrail, "aws-cloudtrail-get-trail-status", args)
+ aws_cloudtrail.main()
+ command_result: CommandResults = return_results_func.call_args[0][0]
+ outputs: dict = command_result.outputs
+ assert "IsLogging" in outputs
diff --git a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/README.md b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/README.md
index d482f8aed812..42c7017dd569 100644
--- a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/README.md
+++ b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/README.md
@@ -1,745 +1,289 @@
-
-AWS CloudTrail is a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account. With CloudTrail, you can log, continuously monitor, and retain account activity related to actions across your AWS infrastructure. CloudTrail provides event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services. This event history simplifies security analysis, resource change tracking, and troubleshooting. For more information, see the AWS CloudTrail documentation.
-Configure AWS CloudTrail on Cortex XSOAR
-
-- Navigate to Settings > Integrations > Servers & Services.
-- Search for AWS - CloudTrail.
-- Click Add instance to create and configure a new integration instance.
-
--
-Name: a textual name for the integration instance.
--
-Default Region:
-- Role Arn
-- Role Session Name
-- Role Session Duration
-
-
-- Click Test to validate the URLs, token, and connection.
-
-Commands
-You can execute these commands from the Cortex XSOAR CLI, as part of an automation, or in a playbook. After you successfully execute a command, a DBot message appears in the War Room with the command details.
-
-- Create a trail: aws-cloudtrail-create-trail
-- Delete a trail: aws-cloudtrail-delete-trail
-- Get the settings of a trail: aws-cloudtrail-describe-trails
-- Update a trail: aws-cloudtrail-update-trail
-- Start recording logs: aws-cloudtrail-start-logging
-- Stop recording logs: aws-cloudtrail-stop-logging
-- Search API activity events: aws-cloudtrail-lookup-events
-
-1. Create a trail
-
-Creates a trail that specifies the settings for delivery of log data to an Amazon S3 bucket. A maximum of five trails can exist in a region, irrespective of the region in which they were created.
-Base Command
-aws-cloudtrail-create-trail
-Input
-
-
-
-| Argument Name |
-Description |
-Required |
-
-
-
-
-| name |
-Specifies the name of the trail |
-Required |
-
-
-| s3BucketName |
-Specifies the name of the Amazon S3 bucket designated for publishing log files |
-Required |
-
-
-| s3KeyPrefix |
-Specifies the Amazon S3 key prefix that comes after the name of the bucket you have designated for log file delivery |
-Optional |
-
-
-| snsTopicName |
-Specifies the name of the Amazon SNS topic defined for notification of log file delivery |
-Optional |
-
-
-| includeGlobalServiceEvents |
-Specifies whether the trail is publishing events from global services, such as IAM, to the log files |
-Optional |
-
-
-| isMultiRegionTrail |
-Specifies whether the trail is created in the current region or in all regions. The default is false. |
-Optional |
-
-
-| enableLogFileValidation |
-Specifies whether log file integrity validation is enabled. The default is false. |
-Optional |
-
-
-| cloudWatchLogsLogGroupArn |
-Specifies a log group name using an Amazon Resource Name (ARN), a unique identifier that represents the log group to which CloudTrail logs will be delivered. Not required unless you specify CloudWatchLogsRoleArn. |
-Optional |
-
-
-| cloudWatchLogsRoleArn |
-Specifies the role for the CloudWatch Logs endpoint to assume to write to a user's log group |
-Optional |
-
-
-| kmsKeyId |
-Specifies the KMS key ID to use to encrypt the logs delivered by CloudTrail. The value can be an alias name prefixed by "alias/", a fully specified ARN to an alias, a fully specified ARN to a key, or a globally unique identifier. |
-Optional |
-
-
-| region |
-The AWS Region, if not specified the default region will be used |
-Optional |
-
-
-| roleArn |
-The Amazon Resource Name (ARN) of the role to assume |
-Optional |
-
-
-| roleSessionName |
-An identifier for the assumed role session |
-Optional |
-
-
-| roleSessionDuration |
-The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. |
-Optional |
-
-
-
-
-Context Output
-
-
-
-| Path |
-Type |
-Description |
-
-
-
-
-| AWS.CloudTrail.Trails.Name |
-string |
-Specifies the name of the trail |
-
-
-| AWS.CloudTrail.Trails.S3BucketName |
-string |
-Specifies the name of the Amazon S3 bucket designated for publishing log files |
-
-
-| AWS.CloudTrail.Trails.IncludeGlobalServiceEvents |
-boolean |
-Specifies whether the trail is publishing events from global services such as IAM to the log files |
-
-
-| AWS.CloudTrail.Trails.IsMultiRegionTrail |
-boolean |
-Specifies whether the trail exists in one region or in all regions |
-
-
-| AWS.CloudTrail.Trails.TrailARN |
-string |
-Specifies the ARN of the trail that was created |
-
-
-| AWS.CloudTrail.Trails.LogFileValidationEnabled |
-boolean |
-Specifies whether log file integrity validation is enabled |
-
-
-| AWS.CloudTrail.Trails.SnsTopicARN |
-string |
-Specifies the ARN of the Amazon SNS topic that CloudTrail uses to send notifications when log files are delivered |
-
-
-| AWS.CloudTrail.Trails.S3KeyPrefix |
-string |
-Specifies the Amazon S3 key prefix that comes after the name of the bucket you have designated for log file delivery |
-
-
-| AWS.CloudTrail.Trails.CloudWatchLogsLogGroupArn |
-string |
-Specifies the Amazon Resource Name (ARN) of the log group to which CloudTrail logs will be delivered |
-
-
-| AWS.CloudTrail.Trails.CloudWatchLogsRoleArn |
-string |
-Specifies the role for the CloudWatch Logs endpoint to assume to write to a user's log group |
-
-
-| AWS.CloudTrail.Trails.KmsKeyId |
-string |
-Specifies the KMS key ID that encrypts the logs delivered by CloudTrail |
-
-
-| AWS.CloudTrail.Trails.HomeRegion |
-string |
-The region in which the trail was created |
-
-
-
-
-Command Example
-!aws-cloudtrail-create-trail name=test s3BucketName=test
-Context Example
-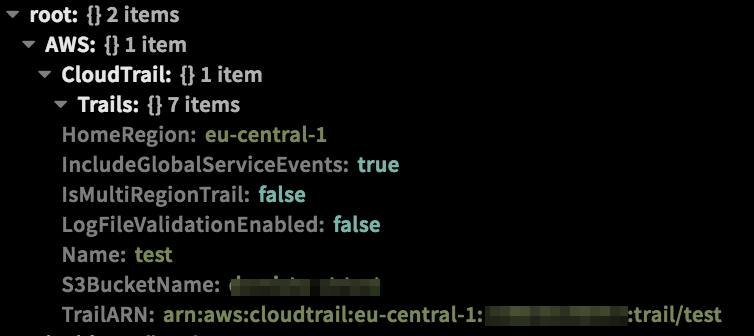
-Human Readable Output
-
-2. Delete a trail
-
-Deletes a trail. This operation must be called from the region in which the trail was created. DeleteTrail cannot be called on the shadow trails (replicated trails in other regions) of a trail that is enabled in all regions.
-Base Command
-aws-cloudtrail-delete-trail
-Input
-
-
-
-| Argument Name |
-Description |
-Required |
-
-
-
-
-| name |
-Specifies the name or the CloudTrail ARN of the trail to be deleted. The format of a trail ARN is: arn:aws:cloudtrail:us-east-1:123456789012:trail/MyTrail |
-Required |
-
-
-
-
-Context Output
-There is no context output for this command.
-Command Example
-!aws-cloudtrail-delete-trail name=test
-Human Readable Output
-
-3. Get the settings of a trail
-
-Retrieves settings for the trail associated with the current region for your account.
-Base Command
-aws-cloudtrail-describe-trails
-Input
-
-
-
-| Argument Name |
-Description |
-Required |
-
-
-
-
-| trailNameList |
-Specifies a list of trail names, trail ARNs, or both, of the trails to describe. If an empty list is specified, information for the trail in the current region is returned. |
-False |
-
-
-| includeShadowTrails |
-Specifies whether to include shadow trails in the response. A shadow trail is the replication in a region of a trail that was created in a different region. The default is "true". |
-Optional |
-
-
-| region |
-The AWS Region, if not specified the default region will be used |
-Optional |
-
-
-| roleArn |
-The Amazon Resource Name (ARN) of the role to assume |
-Optional |
-
-
-| roleSessionName |
-An identifier for the assumed role session |
-Optional |
-
-
-| roleSessionDuration |
-The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. |
-Optional |
-
-
-
-
-Context Output
-
-
-
-| Path |
-Type |
-Description |
-
-
-
-
-| AWS.CloudTrail.Trails.Name |
-string |
-Name of the trail set by calling CreateTrail |
-
-
-| AWS.CloudTrail.Trails.S3BucketName |
-string |
-Name of the Amazon S3 bucket into which CloudTrail delivers your trail files |
-
-
-| AWS.CloudTrail.Trails.S3KeyPrefix |
-string |
-Specifies the Amazon S3 key prefix that comes after the name of the bucket you have designated for log file delivery |
-
-
-| AWS.CloudTrail.Trails.SnsTopicARN |
-string |
-Specifies the ARN of the Amazon SNS topic that CloudTrail uses to send notifications when log files are delivered |
-
-
-| AWS.CloudTrail.Trails.IncludeGlobalServiceEvents |
-boolean |
-Set to "True" to include AWS API calls from AWS global services such as IAM. Otherwise, "False". |
-
-
-| AWS.CloudTrail.Trails.IsMultiRegionTrail |
-boolean |
-Specifies whether the trail belongs only to one region or exists in all regions |
-
-
-| AWS.CloudTrail.Trails.HomeRegion |
-string |
-The region in which the trail was created |
-
-
-| AWS.CloudTrail.Trails.TrailARN |
-string |
-Specifies the ARN of the trail |
-
-
-| AWS.CloudTrail.Trails.LogFileValidationEnabled |
-boolean |
-Specifies whether log file validation is enabled |
-
-
-| AWS.CloudTrail.Trails.CloudWatchLogsLogGroupArn |
-string |
-Specifies an Amazon Resource Name (ARN), a unique identifier that represents the log group to which CloudTrail logs will be delivered |
-
-
-| AWS.CloudTrail.Trails.CloudWatchLogsRoleArn |
-string |
-Specifies the role for the CloudWatch Logs endpoint to assume to write to a user's log group |
-
-
-| AWS.CloudTrail.KmsKeyId |
-string |
-Specifies the KMS key ID that encrypts the logs delivered by CloudTrail |
-
-
-| AWS.CloudTrail.HasCustomEventSelectors |
-boolean |
-Specifies if the trail has custom event selectors |
-
-
-
-
-Command Example
-!aws-cloudtrail-describe-trails
-Context Example
-
-Human Readable Output
-
-4. Update a trail
-
-Updates the settings that specify delivery of log files. Changes to a trail do not require stopping the CloudTrail service.
-Base Command
-aws-cloudtrail-update-trail
-Input
-
-
-
-| Argument Name |
-Description |
-Required |
-
-
-
-
-| name |
-Specifies the name of the trail or trail ARN |
-Required |
-
-
-| s3BucketName |
-Specifies the name of the Amazon S3 bucket designated for publishing log files |
-Optional |
-
-
-| s3KeyPrefix |
-Specifies the Amazon S3 key prefix that comes after the name of the bucket you have designated for log file delivery |
-Optional |
-
-
-| snsTopicName |
-Specifies the name of the Amazon SNS topic defined for notification of log file delivery |
-Optional |
-
-
-| includeGlobalServiceEvents |
-Specifies whether the trail is publishing events from global services such as IAM to the log files |
-Optional |
-
-
-| isMultiRegionTrail |
-Specifies whether the trail applies only to the current region or to all regions. The default is false. If the trail exists only in the current region and this value is set to true, shadow trails (replications of the trail) will be created in the other regions. If the trail exists in all regions and this value is set to false, the trail will remain in the region where it was created, and its shadow trails in other regions will be deleted. |
-Optional |
-
-
-| enableLogFileValidation |
-Specifies whether log file validation is enabled. The default is false. |
-Optional |
-
-
-| cloudWatchLogsLogGroupArn |
-Specifies a log group name using an Amazon Resource Name (ARN), a unique identifier that represents the log group to which CloudTrail logs will be delivered. Not required unless you specify CloudWatchLogsRoleArn. |
-Optional |
-
-
-| cloudWatchLogsRoleArn |
-Specifies the role for the CloudWatch Logs endpoint to assume to write to a user's log group |
-Optional |
-
-
-| kmsKeyId |
-Specifies the KMS key ID to use to encrypt the logs delivered by CloudTrail |
-Optional |
-
-
-| region |
-The AWS Region, if not specified the default region will be used |
-Optional |
-
-
-| roleArn |
-The Amazon Resource Name (ARN) of the role to assume |
-Optional |
-
-
-| roleSessionName |
-An identifier for the assumed role session |
-Optional |
-
-
-| roleSessionDuration |
-The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. |
-Optional |
-
-
-
-
-Context Output
-
-
-
-| Path |
-Type |
-Description |
-
-
-
-
-| AWS.CloudTrail.Trails.Name |
-string |
-Specifies the name of the trail |
-
-
-| AWS.CloudTrail.Trails.S3BucketName |
-string |
-Specifies the name of the Amazon S3 bucket designated for publishing log files |
-
-
-| AWS.CloudTrail.Trails.IncludeGlobalServiceEvents |
-boolean |
-Specifies whether the trail is publishing events from global services such as IAM to the log files |
-
-
-| AWS.CloudTrail.Trails.IsMultiRegionTrail |
-boolean |
-Specifies whether the trail exists in one region or in all regions |
-
-
-| AWS.CloudTrail.Trails.TrailARN |
-string |
-Specifies the ARN of the trail that was created |
-
-
-| AWS.CloudTrail.Trails.LogFileValidationEnabled |
-boolean |
-Specifies whether log file integrity validation is enabled |
-
-
-| AWS.CloudTrail.Trails.SnsTopicARN |
-string |
-Specifies the ARN of the Amazon SNS topic that CloudTrail uses to send notifications when log files are delivered |
-
-
-| AWS.CloudTrail.Trails.S3KeyPrefix |
-string |
-Specifies the Amazon S3 key prefix that comes after the name of the bucket you have designated for log file delivery |
-
-
-| AWS.CloudTrail.Trails.CloudWatchLogsLogGroupArn |
-string |
-Specifies the Amazon Resource Name (ARN) of the log group to which CloudTrail logs will be delivered |
-
-
-| AWS.CloudTrail.Trails.CloudWatchLogsRoleArn |
-string |
-Specifies the role for the CloudWatch Logs endpoint to assume to write to a user's log group |
-
-
-| AWS.CloudTrail.Trails.KmsKeyId |
-string |
-Specifies the KMS key ID that encrypts the logs delivered by CloudTrail |
-
-
-| AWS.CloudTrail.Trails.HomeRegion |
-string |
-The region in which the trail was created |
-
-
-
-
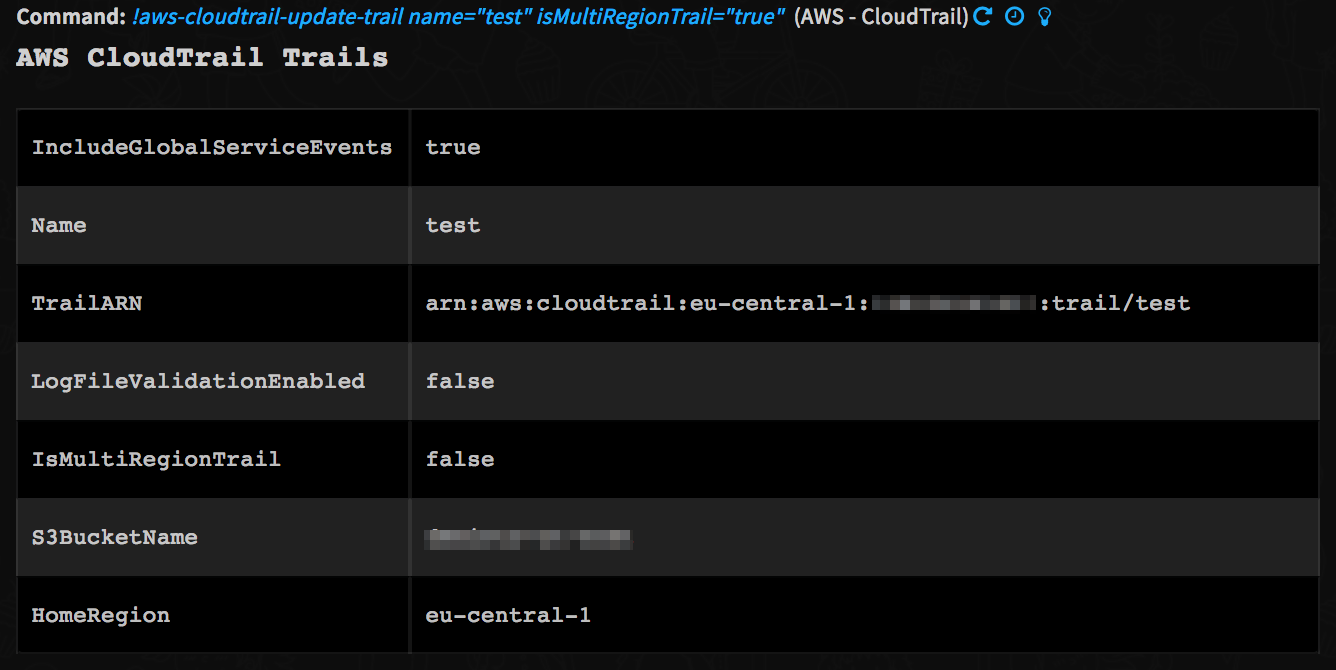
-Command Example
-!aws-cloudtrail-update-trail name=test isMultiRegionTrail=true
-Context Example
-
-Human Readable Output
-
-5. Start recording logs
-
-Starts the recording of AWS API calls and log file delivery for a trail. For a trail that is enabled in all regions, this operation must be called from the region in which the trail was created. This operation cannot be called on the shadow trails (replicated trails in other regions) of a trail that is enabled in all regions.
-Base Command
-aws-cloudtrail-start-logging
-Input
-
-
-
-| Argument Name |
-Description |
-Required |
-
-
-
-
-| name |
-Specifies the name or the CloudTrail ARN of the trail for which CloudTrail logs AWS API calls |
-Required |
-
-
-| region |
-The AWS Region, if not specified the default region will be used |
-Optional |
-
-
-| roleArn |
-The Amazon Resource Name (ARN) of the role to assume |
-Optional |
-
-
-| roleSessionName |
-An identifier for the assumed role session |
-Optional |
-
-
-| roleSessionDuration |
-The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. |
-Optional |
-
-
-
-
-Context Output
-There is no context output for this command.
-Command Example
-!aws-cloudtrail-start-logging name=test
-Context Example
-There is no context output for this command.
-Human Readable Output
-
-6. Stop recording logs
-
-Suspends the recording of AWS API calls and log file delivery for the specified trail. Under most circumstances, there is no need to use this action. You can update a trail without stopping it first. This action is the only way to stop recording. For a trail enabled in all regions, this operation must be called from the region in which the trail was created, or an InvalidHomeRegionException will occur. This operation cannot be called on the shadow trails (replicated trails in other regions) of a trail enabled in all regions.
-Base Command
-aws-cloudtrail-stop-logging
-Input
-
-
-
-| Argument Name |
-Description |
-Required |
-
-
-
-
-| name |
-Specifies the name or the CloudTrail ARN of the trail for which CloudTrail logs AWS API calls |
-Required |
-
-
-| region |
-The AWS Region, if not specified the default region will be used |
-Optional |
-
-
-| roleArn |
-The Amazon Resource Name (ARN) of the role to assume |
-Optional |
-
-
-| roleSessionName |
-An identifier for the assumed role session |
-Optional |
-
-
-| roleSessionDuration |
-The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role |
-Optional |
-
-
-
-
-Context Output
-There is no context output for this command.
-Command Example
-!aws-cloudtrail-stop-logging name=test
-Context Example
-There is no context output for this command.
-Human Readable Output
-
-7. Search API activity events
-
-Looks up API activity events captured by CloudTrail that create, update, or delete resources in your account. Events for a region can be looked up for the times in which you had CloudTrail turned on in that region during the last seven days.
-Base Command
-aws-cloudtrail-lookup-events
-Input
-
-
-
-| Argument Name |
-Description |
-Required |
-
-
-
-
-| attributeKey |
-Specifies an attribute on which to filter the returned events |
-Required |
-
-
-| attributeValue |
-Specifies a value for the specified AttributeKey
- |
-Required |
-
-
-| startTime |
-Specifies that only events that occur on or after the specified time are returned |
-Optional |
-
-
-| endTime |
-Specifies that only events that occur on or before the specified time are returned |
-Optional |
-
-
-| region |
-The AWS Region, if not specified the default region will be used |
-Optional |
-
-
-| roleArn |
-The Amazon Resource Name (ARN) of the role to assume |
-Optional |
-
-
-| roleSessionName |
-An identifier for the assumed role session |
-Optional |
-
-
-| roleSessionDuration |
-The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. |
-Optional |
-
-
-
-
-Context Output
-
-
-
-| Path |
-Type |
-Description |
-
-
-
-
-| AWS.CloudTrail.Trails.Events.EventId |
-string |
-The CloudTrail ID of the returned event |
-
-
-| AWS.CloudTrail.Trails.Events.EventName |
-string |
-The name of the returned event |
-
-
-| AWS.CloudTrail.Trails.Events.EventTime |
-date |
-The date and time of the returned event |
-
-
-| AWS.CloudTrail.Trails.Events.EventSource |
-string |
-The AWS service that the request was made to |
-
-
-| AWS.CloudTrail.Trails.Events.Username |
-string |
-User name or role name of the requester that called the API in the event returned |
-
-
-| AWS.CloudTrail.Trails.Events.ResourceName |
-string |
-The type of a resource referenced by the event returned. When the resource type cannot be determined, null is returned. Some examples of resource types are: Instance for EC2, Trail for CloudTrail, DBInstance for RDS, and AccessKey for IAM. |
-
-
-| AWS.CloudTrail.Trails.Events.ResourceType |
-string |
-The name of the resource referenced by the event returned. These are user-created names whose values will depend on the environment. For example, the resource name might be "auto-scaling-test-group" for an Auto Scaling Group or "i-1234567" for an EC2 Instance. |
-
-
-| AWS.CloudTrail.Trails.Events.CloudTrailEvent |
-string |
-A JSON string that contains a representation of the returned event |
-
-
-
-
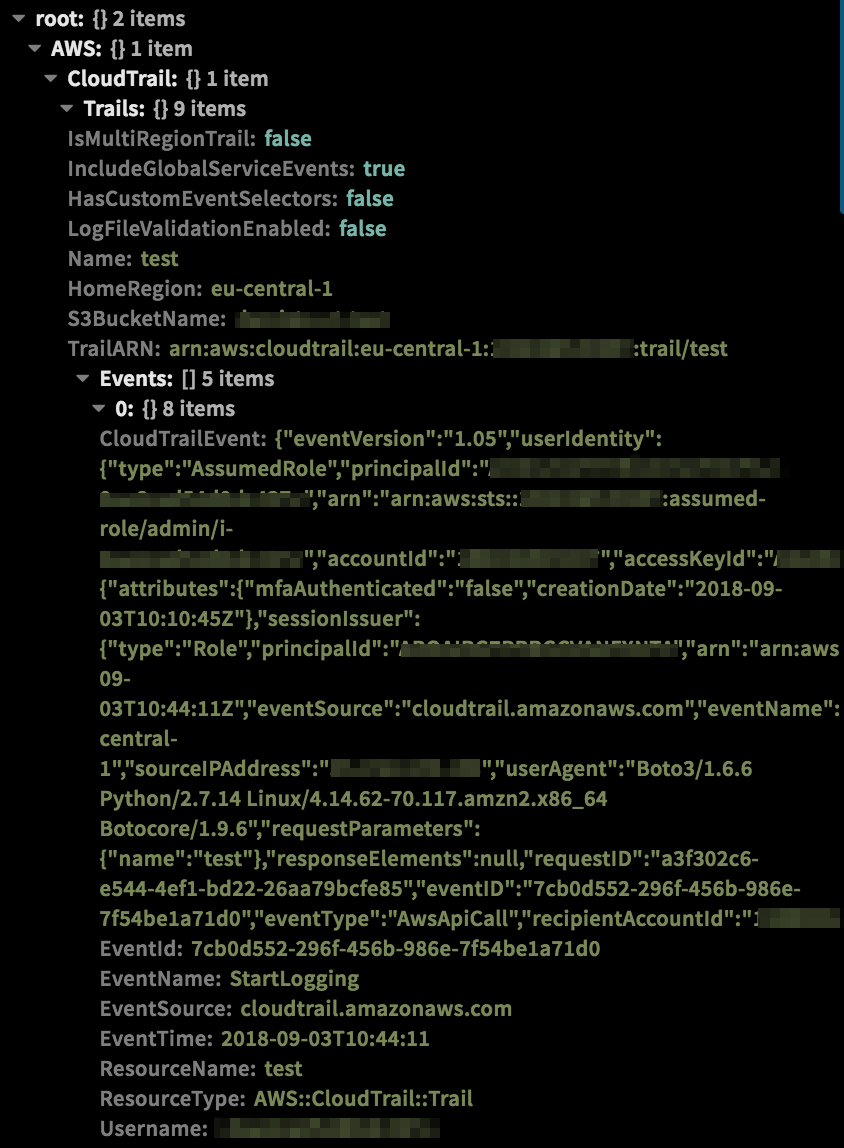
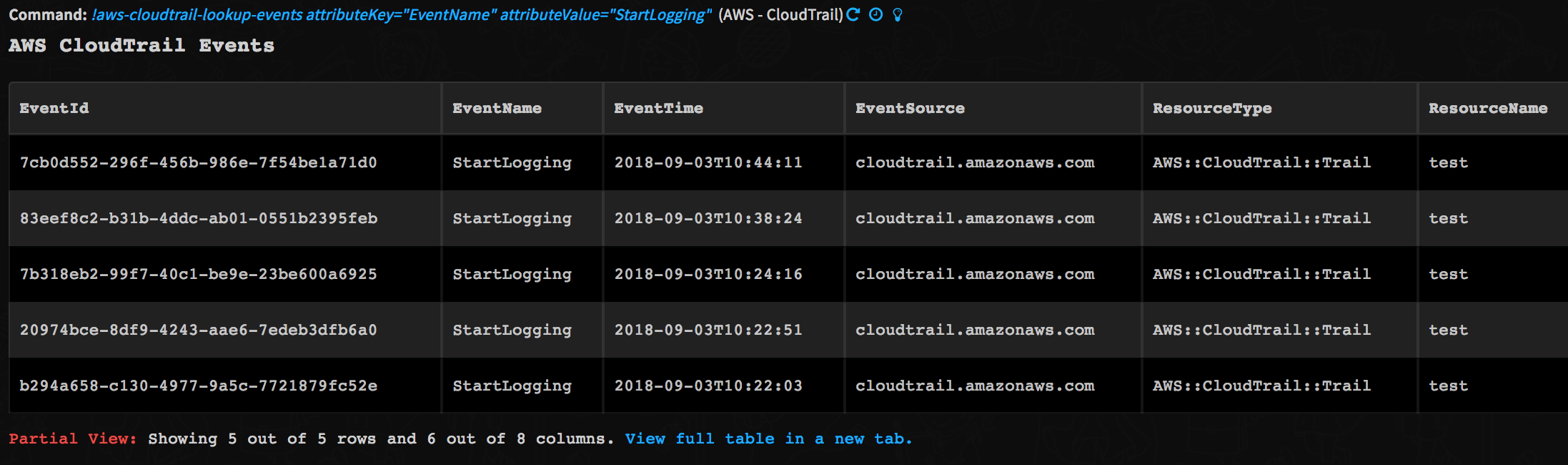
-Command Example
-!aws-cloudtrail-lookup-events attributeKey=EventName attributeValue=StartLogging
-Context Example
-
-Human Readable Output
-
\ No newline at end of file
+Amazon Web Services CloudTrail.
+This integration was integrated and tested with version 1.0.11 of AWS - CloudTrail.
+
+## Configure AWS - CloudTrail on Cortex XSOAR
+
+1. Navigate to **Settings** > **Integrations** > **Servers & Services**.
+2. Search for AWS - CloudTrail.
+3. Click **Add instance** to create and configure a new integration instance.
+
+ | **Parameter** | **Required** |
+ | --- | --- |
+ | AWS Default Region | False |
+ | Role Arn | False |
+ | Role Session Name | False |
+ | Role Session Duration | False |
+ | Access Key | False |
+ | Secret Key | False |
+ | Access Key | False |
+ | Secret Key | False |
+ | Trust any certificate (not secure) | False |
+ | Use system proxy settings | False |
+
+4. Click **Test** to validate the URLs, token, and connection.
+
+## Commands
+
+You can execute these commands from the Cortex XSOAR CLI, as part of an automation, or in a playbook.
+After you successfully execute a command, a DBot message appears in the War Room with the command details.
+
+### aws-cloudtrail-create-trail
+
+***
+Creates a trail that specifies the settings for delivery of log data to an Amazon S3 bucket. A maximum of five trails can exist in a region, irrespective of the region in which they were created.
+
+#### Base Command
+
+`aws-cloudtrail-create-trail`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| name | Specifies the name of the trail. | Required |
+| s3BucketName | Specifies the name of the Amazon S3 bucket designated for publishing log files. | Required |
+| s3KeyPrefix | Specifies the Amazon S3 key prefix that comes after the name of the bucket you have designated for log file delivery. | Optional |
+| snsTopicName | Specifies the name of the Amazon SNS topic defined for notification of log file delivery. | Optional |
+| includeGlobalServiceEvents | Specifies whether the trail is publishing events from global services such as IAM to the log files. Possible values are: True, False. | Optional |
+| isMultiRegionTrail | Specifies whether the trail is created in the current region or in all regions. The default is false. Possible values are: True, False. | Optional |
+| enableLogFileValidation | Specifies whether log file integrity validation is enabled. The default is false. Possible values are: True, False. | Optional |
+| cloudWatchLogsLogGroupArn | Specifies a log group name using an Amazon Resource Name (ARN), a unique identifier that represents the log group to which CloudTrail logs will be delivered. Not required unless you specify CloudWatchLogsRoleArn. | Optional |
+| cloudWatchLogsRoleArn | Specifies the role for the CloudWatch Logs endpoint to assume to write to a user's log group. | Optional |
+| kmsKeyId | Specifies the KMS key ID to use to encrypt the logs delivered by CloudTrail. The value can be an alias name prefixed by "alias/", a fully specified ARN to an alias, a fully specified ARN to a key, or a globally unique identifier. | Optional |
+| region | The AWS Region, if not specified the default region will be used. | Optional |
+| roleArn | The Amazon Resource Name (ARN) of the role to assume. | Optional |
+| roleSessionName | An identifier for the assumed role session. | Optional |
+| roleSessionDuration | The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. | Optional |
+
+#### Context Output
+
+| **Path** | **Type** | **Description** |
+| --- | --- | --- |
+| AWS.CloudTrail.Trails.Name | string | Specifies the name of the trail. |
+| AWS.CloudTrail.Trails.S3BucketName | string | Specifies the name of the Amazon S3 bucket designated for publishing log files. |
+| AWS.CloudTrail.Trails.IncludeGlobalServiceEvents | boolean | Specifies whether the trail is publishing events from global services such as IAM to the log files. |
+| AWS.CloudTrail.Trails.IsMultiRegionTrail | boolean | Specifies whether the trail exists in one region or in all regions. |
+| AWS.CloudTrail.Trails.TrailARN | string | Specifies the ARN of the trail that was created. |
+| AWS.CloudTrail.Trails.LogFileValidationEnabled | boolean | Specifies whether log file integrity validation is enabled. |
+| AWS.CloudTrail.Trails.SnsTopicARN | string | Specifies the ARN of the Amazon SNS topic that CloudTrail uses to send notifications when log files are delivered. |
+| AWS.CloudTrail.Trails.S3KeyPrefix | string | pecifies the Amazon S3 key prefix that comes after the name of the bucket you have designated for log file delivery. |
+| AWS.CloudTrail.Trails.CloudWatchLogsLogGroupArn | string | Specifies the Amazon Resource Name \(ARN\) of the log group to which CloudTrail logs will be delivered. |
+| AWS.CloudTrail.Trails.CloudWatchLogsRoleArn | string | Specifies the role for the CloudWatch Logs endpoint to assume to write to a user's log group. |
+| AWS.CloudTrail.Trails.KmsKeyId | string | Specifies the KMS key ID that encrypts the logs delivered by CloudTrail. |
+| AWS.CloudTrail.Trails.HomeRegion | string | The region in which the trail was created. |
+
+### aws-cloudtrail-delete-trail
+
+***
+Deletes a trail. This operation must be called from the region in which the trail was created. DeleteTrail cannot be called on the shadow trails (replicated trails in other regions) of a trail that is enabled in all regions.
+
+#### Base Command
+
+`aws-cloudtrail-delete-trail`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| name | Specifies the name or the CloudTrail ARN of the trail to be deleted. The format of a trail ARN is: arn:aws:cloudtrail:us-east-1:123456789012:trail/MyTrail. | Required |
+
+#### Context Output
+
+There is no context output for this command.
+### aws-cloudtrail-describe-trails
+
+***
+Retrieves settings for the trail associated with the current region for your account.
+
+#### Base Command
+
+`aws-cloudtrail-describe-trails`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| trailNameList | Specifies a list of trail names, trail ARNs, or both, of the trails to describe. If an empty list is specified, information for the trail in the current region is returned. | Optional |
+| includeShadowTrails | Specifies whether to include shadow trails in the response. A shadow trail is the replication in a region of a trail that was created in a different region. The default is true. Possible values are: True, False. | Optional |
+| region | The AWS Region, if not specified the default region will be used. | Optional |
+| roleArn | The Amazon Resource Name (ARN) of the role to assume. | Optional |
+| roleSessionName | An identifier for the assumed role session. | Optional |
+| roleSessionDuration | The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. | Optional |
+
+#### Context Output
+
+| **Path** | **Type** | **Description** |
+| --- | --- | --- |
+| AWS.CloudTrail.Trails.Name | string | Name of the trail set by calling CreateTrail. |
+| AWS.CloudTrail.Trails.S3BucketName | string | Name of the Amazon S3 bucket into which CloudTrail delivers your trail files. |
+| AWS.CloudTrail.Trails.S3KeyPrefix | string | Specifies the Amazon S3 key prefix that comes after the name of the bucket you have designated for log file delivery. |
+| AWS.CloudTrail.Trails.SnsTopicARN | string | Specifies the ARN of the Amazon SNS topic that CloudTrail uses to send notifications when log files are delivered. |
+| AWS.CloudTrail.Trails.IncludeGlobalServiceEvents | boolean | Set to True to include AWS API calls from AWS global services such as IAM. Otherwise, False. |
+| AWS.CloudTrail.Trails.IsMultiRegionTrail | boolean | Specifies whether the trail belongs only to one region or exists in all regions. |
+| AWS.CloudTrail.Trails.HomeRegion | string | The region in which the trail was created. |
+| AWS.CloudTrail.Trails.TrailARN | string | Specifies the ARN of the trail. |
+| AWS.CloudTrail.Trails.LogFileValidationEnabled | boolean | Specifies whether log file validation is enabled. |
+| AWS.CloudTrail.Trails.CloudWatchLogsLogGroupArn | string | Specifies an Amazon Resource Name \(ARN\), a unique identifier that represents the log group to which CloudTrail logs will be delivered. |
+| AWS.CloudTrail.Trails.CloudWatchLogsRoleArn | string | Specifies the role for the CloudWatch Logs endpoint to assume to write to a user's log group. |
+| AWS.CloudTrail.KmsKeyId | string | Specifies the KMS key ID that encrypts the logs delivered by CloudTrail. |
+| AWS.CloudTrail.HasCustomEventSelectors | boolean | Specifies if the trail has custom event selectors. |
+
+### aws-cloudtrail-update-trail
+
+***
+Updates the settings that specify delivery of log files. Changes to a trail do not require stopping the CloudTrail service.
+
+#### Base Command
+
+`aws-cloudtrail-update-trail`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| name | Specifies the name of the trail or trail ARN. | Required |
+| s3BucketName | Specifies the name of the Amazon S3 bucket designated for publishing log files. | Optional |
+| s3KeyPrefix | Specifies the Amazon S3 key prefix that comes after the name of the bucket you have designated for log file delivery. | Optional |
+| snsTopicName | Specifies the name of the Amazon SNS topic defined for notification of log file delivery. | Optional |
+| includeGlobalServiceEvents | Specifies whether the trail is publishing events from global services such as IAM to the log files. | Optional |
+| isMultiRegionTrail | Specifies whether the trail applies only to the current region or to all regions. The default is false. If the trail exists only in the current region and this value is set to true, shadow trails (replications of the trail) will be created in the other regions. If the trail exists in all regions and this value is set to false, the trail will remain in the region where it was created, and its shadow trails in other regions will be deleted. | Optional |
+| enableLogFileValidation | Specifies whether log file validation is enabled. The default is false. | Optional |
+| cloudWatchLogsLogGroupArn | Specifies a log group name using an Amazon Resource Name (ARN), a unique identifier that represents the log group to which CloudTrail logs will be delivered. Not required unless you specify CloudWatchLogsRoleArn. | Optional |
+| cloudWatchLogsRoleArn | Specifies the role for the CloudWatch Logs endpoint to assume to write to a user's log group. | Optional |
+| kmsKeyId | Specifies the KMS key ID to use to encrypt the logs delivered by CloudTrail. | Optional |
+| region | The AWS Region, if not specified the default region will be used. | Optional |
+| roleArn | The Amazon Resource Name (ARN) of the role to assume. | Optional |
+| roleSessionName | An identifier for the assumed role session. | Optional |
+| roleSessionDuration | The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. | Optional |
+
+#### Context Output
+
+| **Path** | **Type** | **Description** |
+| --- | --- | --- |
+| AWS.CloudTrail.Trails.Name | string | Specifies the name of the trail. |
+| AWS.CloudTrail.Trails.S3BucketName | string | Specifies the name of the Amazon S3 bucket designated for publishing log files. |
+| AWS.CloudTrail.Trails.IncludeGlobalServiceEvents | boolean | Specifies whether the trail is publishing events from global services such as IAM to the log files. |
+| AWS.CloudTrail.Trails.IsMultiRegionTrail | boolean | Specifies whether the trail exists in one region or in all regions. |
+| AWS.CloudTrail.Trails.TrailARN | string | Specifies the ARN of the trail that was created. |
+| AWS.CloudTrail.Trails.LogFileValidationEnabled | boolean | Specifies whether log file integrity validation is enabled. |
+| AWS.CloudTrail.Trails.SnsTopicARN | string | Specifies the ARN of the Amazon SNS topic that CloudTrail uses to send notifications when log files are delivered. |
+| AWS.CloudTrail.Trails.S3KeyPrefix | string | pecifies the Amazon S3 key prefix that comes after the name of the bucket you have designated for log file delivery. |
+| AWS.CloudTrail.Trails.CloudWatchLogsLogGroupArn | string | Specifies the Amazon Resource Name \(ARN\) of the log group to which CloudTrail logs will be delivered. |
+| AWS.CloudTrail.Trails.CloudWatchLogsRoleArn | string | Specifies the role for the CloudWatch Logs endpoint to assume to write to a user's log group. |
+| AWS.CloudTrail.Trails.KmsKeyId | string | Specifies the KMS key ID that encrypts the logs delivered by CloudTrail. |
+| AWS.CloudTrail.Trails.HomeRegion | string | The region in which the trail was created. |
+
+### aws-cloudtrail-start-logging
+
+***
+Starts the recording of AWS API calls and log file delivery for a trail. For a trail that is enabled in all regions, this operation must be called from the region in which the trail was created. This operation cannot be called on the shadow trails (replicated trails in other regions) of a trail that is enabled in all regions.
+
+#### Base Command
+
+`aws-cloudtrail-start-logging`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| name | Specifies the name or the CloudTrail ARN of the trail for which CloudTrail logs AWS API calls. | Required |
+| region | The AWS Region, if not specified the default region will be used. | Optional |
+| roleArn | The Amazon Resource Name (ARN) of the role to assume. | Optional |
+| roleSessionName | An identifier for the assumed role session. | Optional |
+| roleSessionDuration | The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. | Optional |
+
+#### Context Output
+
+There is no context output for this command.
+### aws-cloudtrail-stop-logging
+
+***
+Suspends the recording of AWS API calls and log file delivery for the specified trail. Under most circumstances, there is no need to use this action. You can update a trail without stopping it first. This action is the only way to stop recording. For a trail enabled in all regions, this operation must be called from the region in which the trail was created, or an InvalidHomeRegionException will occur. This operation cannot be called on the shadow trails (replicated trails in other regions) of a trail enabled in all regions.
+
+#### Base Command
+
+`aws-cloudtrail-stop-logging`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| name | Specifies the name or the CloudTrail ARN of the trail for which CloudTrail logs AWS API calls. | Required |
+| region | The AWS Region, if not specified the default region will be used. | Optional |
+| roleArn | The Amazon Resource Name (ARN) of the role to assume. | Optional |
+| roleSessionName | An identifier for the assumed role session. | Optional |
+| roleSessionDuration | The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. | Optional |
+
+#### Context Output
+
+There is no context output for this command.
+### aws-cloudtrail-lookup-events
+
+***
+Looks up API activity events captured by CloudTrail that create, update, or delete resources in your account. Events for a region can be looked up for the times in which you had CloudTrail turned on in that region during the last seven days.
+
+#### Base Command
+
+`aws-cloudtrail-lookup-events`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| attributeKey | Specifies an attribute on which to filter the events returned. Possible values are: AccessKeyId, EventId, EventName, Username, ResourceType, ResourceName, EventSource, ReadOnly. | Required |
+| attributeValue | Specifies a value for the specified AttributeKey. | Required |
+| startTime | Specifies that only events that occur after or at the specified time are returned. | Optional |
+| endTime | Specifies that only events that occur before or at the specified time are returned. | Optional |
+| region | The AWS Region, if not specified the default region will be used. | Optional |
+| roleArn | The Amazon Resource Name (ARN) of the role to assume. | Optional |
+| roleSessionName | An identifier for the assumed role session. | Optional |
+| roleSessionDuration | The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. | Optional |
+
+#### Context Output
+
+| **Path** | **Type** | **Description** |
+| --- | --- | --- |
+| AWS.CloudTrail.Events.EventId | string | The CloudTrail ID of the event returned. |
+| AWS.CloudTrail.Events.EventName | string | The name of the event returned. |
+| AWS.CloudTrail.Events.EventTime | date | The date and time of the event returned. |
+| AWS.CloudTrail.Events.EventSource | string | The AWS service that the request was made to. |
+| AWS.CloudTrail.Events.Username | string | A user name or role name of the requester that called the API in the event returned. |
+| AWS.CloudTrail.Events.ResourceName | string | The type of a resource referenced by the event returned. When the resource type cannot be determined, null is returned. Some examples of resource types are: Instance for EC2, Trail for CloudTrail, DBInstance for RDS, and AccessKey for IAM. |
+| AWS.CloudTrail.Events.ResourceType | string | The name of the resource referenced by the event returned. These are user-created names whose values will depend on the environment. For example, the resource name might be "auto-scaling-test-group" for an Auto Scaling Group or "i-1234567" for an EC2 Instance. |
+| AWS.CloudTrail.Events.CloudTrailEvent | string | A JSON string that contains a representation of the event returned. |
+
+### aws-cloudtrail-get-trail-status
+
+***
+Returns a JSON-formatted list of information about the specified trail. Fields include information on delivery errors, Amazon SNS and Amazon S3 errors, and start and stop logging times for each trail.
+
+#### Base Command
+
+`aws-cloudtrail-get-trail-status`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| trailNameList | Specifies the names of multiple trails. | Optional |
+| region | Specifies the region of the trail. | Required |
+| roleArn | The The Amazon Resource Name (ARN) of the role to assume. | Optional |
+| roleSessionName | An identifier for the assumed role session. | Optional |
+| roleSessionDuration | The duration, in seconds, of the role session. The value can range from 900 seconds (15 minutes) up to the maximum session duration setting for the role. | Optional |
+| name | Specifies the name of the trail. | Required |
+
+#### Context Output
+
+| **Path** | **Type** | **Description** |
+| --- | --- | --- |
+| AWS.CloudTrail.TrailStatus.IsLogging | boolean | Whether the CloudTrail trail is currently logging Amazon Web Services API calls. |
+| AWS.CloudTrail.TrailStatus.LatestDeliveryError | string | Displays any Amazon S3 error that CloudTrail encountered when attempting to deliver log files to the designated bucket. |
+| AWS.CloudTrail.TrailStatus.LatestNotificationError | string | Displays any Amazon SNS error that CloudTrail encountered when attempting to send a notification. |
+| AWS.CloudTrail.TrailStatus.LatestDeliveryTime | date | Specifies the date and time that CloudTrail last delivered log files to an account’s Amazon S3 bucket. |
+| AWS.CloudTrail.TrailStatus.LatestNotificationTime | date | Specifies the date and time of the most recent Amazon SNS notification that CloudTrail has written a new log file to an account’s Amazon S3 bucket. |
+| AWS.CloudTrail.TrailStatus.StartLoggingTime | date | Specifies the most recent date and time when CloudTrail started recording API calls for an Amazon Web Services account. |
+| AWS.CloudTrail.TrailStatus.StopLoggingTime | date | Specifies the most recent date and time when CloudTrail stopped recording API calls for an Amazon Web Services account. |
+| AWS.CloudTrail.TrailStatus.LatestCloudWatchLogsDeliveryError | string | Displays any CloudWatch Logs error that CloudTrail encountered when attempting to deliver logs to CloudWatch Logs. |
+| AWS.CloudTrail.TrailStatus.LatestCloudWatchLogsDeliveryTime | date | Displays the most recent date and time when CloudTrail delivered logs to CloudWatch Logs. |
+| AWS.CloudTrail.TrailStatus.LatestDigestDeliveryTime | date | Specifies the date and time that CloudTrail last delivered a digest file to an account’s Amazon S3 bucket. |
+| AWS.CloudTrail.TrailStatus.LatestDigestDeliveryError | string | Displays any Amazon S3 error that CloudTrail encountered when attempting to deliver a digest file to the designated bucket. |
diff --git a/Packs/AWS-CloudTrail/ReleaseNotes/1_1_0.md b/Packs/AWS-CloudTrail/ReleaseNotes/1_1_0.md
new file mode 100644
index 000000000000..093334440231
--- /dev/null
+++ b/Packs/AWS-CloudTrail/ReleaseNotes/1_1_0.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### AWS - CloudTrail
+
+- Added the **aws-cloudtrail-get-trail-status** command, use this command to get information about the trail status.
\ No newline at end of file
diff --git a/Packs/AWS-CloudTrail/pack_metadata.json b/Packs/AWS-CloudTrail/pack_metadata.json
index 77a04fb47596..1471a042792a 100644
--- a/Packs/AWS-CloudTrail/pack_metadata.json
+++ b/Packs/AWS-CloudTrail/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "AWS - CloudTrail",
"description": "Amazon Web Services CloudTrail.",
"support": "xsoar",
- "currentVersion": "1.0.12",
+ "currentVersion": "1.1.0",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",

