From 9caebf8b1af163482333d9f8c3aae5f9313bb340 Mon Sep 17 00:00:00 2001
From: el-termikael <58733007+el-termikael@users.noreply.github.com>
Date: Thu, 5 Sep 2024 12:13:46 +0000
Subject: [PATCH] automatically update translations
---
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../current.json | 2 +-
.../current/adguard-vpn-for-linux/feedback.md | 2 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 42 +--
.../setting-up-on-a-router.md | 12 +-
.../current/adguard-vpn-for-mac/overview.md | 8 +-
.../adguard-vpn-for-windows/installation.md | 2 +-
.../adguard-vpn-for-windows/overview.md | 8 +-
.../current/general/how-vpn-works.md | 4 +-
.../set-up-adguard-vpn-on-your-router.md | 14 +-
.../current/general/vpn-issues.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../current.json | 2 +-
.../current/adguard-vpn-for-ios/overview.md | 2 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../current/general/why-adguard-vpn.md | 2 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 29 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../adguard-vpn-for-windows/overview.md | 2 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../adguard-vpn-for-ios/installation.md | 32 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
.../setting-up-on-a-router/asuswrt-merlin.md | 283 ++++++++++++++++++
.../setting-up-on-a-router/keenetic.md | 27 +-
.../setting-up-on-a-router/openwrt.md | 2 +-
.../setting-up-on-a-router.md | 4 +-
97 files changed, 6408 insertions(+), 362 deletions(-)
create mode 100644 i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
create mode 100644 i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/cs/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/da/docusaurus-plugin-content-docs/current.json b/i18n/da/docusaurus-plugin-content-docs/current.json
index b3110ab2e3..9178ab7b10 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current.json
+++ b/i18n/da/docusaurus-plugin-content-docs/current.json
@@ -52,7 +52,7 @@
"description": "The label for category AdGuard VPN for Linux in sidebar sidebar"
},
"sidebar.sidebar.category.Setting up on a router": {
- "message": "Setting up on a router",
+ "message": "Opsætning på en router",
"description": "The label for category Setting up on a router in sidebar sidebar"
}
}
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/feedback.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/feedback.md
index 8a1657a8b2..da8f9144a5 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/feedback.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/feedback.md
@@ -1,5 +1,5 @@
---
-title: Feedbackindsendelse
+title: Indsendelse af feedback
sidebar_position: 6
---
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 8f1417d07e..68f84cbfa7 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: Sådan opsættes AdGuard VPN til Linux på en Keenetic-router
-sidebar_position: 3
+sidebar_position: 2
---
:::info Systemkrav
@@ -67,7 +67,7 @@ Erstat `192.168.1.1` med routerens aktuelle IP-adresse.
1. Er første gang, der oprettes forbindelse til routeren via SSH, vises en meddelelse i stil med denne:
-```bash
+```text
Ægtheden af værten '192.168.1.1 (192.168.1.1)' kan ikke fastslås.
ECDSA-nøglefingeraftryk er SHA256:...
Sikker på, at der fortsat skal oprettes forbindelse (ja/nej/[fingeraftryk])?
@@ -121,13 +121,13 @@ Eksekvér i SSH-klienten flg. kode for at installere de pakker, som kræves til
opkg install curl sudo ca-certificates
```
-Gå til mappen `cd/opt` og eksekvér AdGuard VPN CLI installations-scriptet:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-Svar `y` på forespørgslen `Skal den binære linkes til /usr/local/bin?`. Mislykkes det at linke den binære, eksekvér denne linje:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Opret forbindelse til VPN
- Importér SSL-certifikatet før tilslutning ved at eksekvere flg. kommando:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
Dette skal gøres før hver session.
@@ -233,15 +234,15 @@ Dette trin er designet til at opsætte firewall-regler på en Keenetic-router ti
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ Dette trin er designet til at opsætte firewall-regler på en Keenetic-router ti
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
Dette opretter et nyt shell-script ved navn `001-adguardvpn.sh` i mappen `/opt/etc/ndm/netfilter.d/`, hvilket er hvor netværksrelaterede scripts typisk lagres på en Keenetic-router.
Scriptet opretter en tilpasset firewall-regel for at sikre, at trafik fra LAN'et (`br0`) rutes igennem AdGuard VPN-grænsefladen (`tun0`). Det rydder først op i tidligere regler relateret til denne opsætning og opsætter dernæst nye regler til korrekt rutning af trafikken.
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index cb7a9a8d0d..6200dbcbbf 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: Sådan opsættes AdGuard VPN til Linux på en OpenWRT-router
-sidebar_position: 2
+sidebar_position: 3
---
:::info Systemkrav
@@ -159,25 +159,25 @@ curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/sc
adguardvpn-cli connect
```
- AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+ AdGuard VPN vælger den hurtigste lokation tilgængelig og husker den til fremtidige hurtige forbindelser.
-3. Adjust your settings
+3. Justér indstillingerne
- Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+ Få en liste over alle tilgængelige AdGuard VPN-kommandoer og tilpas VPN-klienten efter behov.
- To view all commands, type:
+ For at se alle kommandoer, skriv:
```jsx
adguardvpn-cli --help-all
```
- AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+ AdGuard VPN CLI opretter en tun0-grænseflade til VPN-tunneling.
-## 6) Set up firewall rules
+## 6) Opsæt firewall-regler
-You can do it in the web interface or in the command line. Steps below describe setup via SSH command line.
+Det kan gøres via webgrænsefladen eller på kommandolinjen. Trinene nedenfor beskriver opsætning via en SSH-kommandolinje.
-1. Add a new unmanaged interface via SSH
+1. Tilføj en ny ikke-håndteret grænseflade via SSH
```shell
ssh admin@router_ip
@@ -188,20 +188,20 @@ You can do it in the web interface or in the command line. Steps below describe
/etc/init.d/network reload
```
-2. Add tun0 to WAN zone
+2. Tilføj tun0 til WAN-zonen
- For traffic to go through VPN, add tun0 to WAN zone.
- The WAN interface which connects to the Internet will typically be in a zone named `wan` or something similar. Check your router's configuration files or firewall settings to find out which zone is associated with the WAN interface.
+ For at trafikken skal rutes igennem VPN, tilføj tun0 til WAN-zonen.
+ WAN-grænsefladen, der forbinder til internet, vil typisk være i en zone ved navn 'wan' eller noget tilsvarende. Tjek routerens opsætningsfiler eller firewall-indstillinger for at finde ud af, hvilken zone der tilknyttet WAN-grænsefladen.
- To do so, list the existing firewall zones:
+ For at gøre dette, oplist de eksisterende firewall-zoner:
```shell
uci show firewall
```
- This will show a config file with all zones listed. Look for a section like `firewall.@zone[1]` or similar where `option name 'wan'` is defined. The number `[1]` could be different depending on your configuration.
+ Dette vil vise en opsætningsfil med alle zoner oplistet. Se efter en sektion såsom `firewall.@zone[1]` el.lign., hvor `indstillingsnavn 'wan'` er defineret. Tallet "[1]" kan være anderledes afhængigt af opsætningen.
- Run this SSH command, replace `zone[1]` with correct ‘wan’ zone identified before:
+ Eksekvér denne SSH-kommando, erstat 'zone[1]' med den korrekte 'wan'-zone identificeret tidligere:
```shell
uci show firewall | grep "=zone"
@@ -210,7 +210,7 @@ You can do it in the web interface or in the command line. Steps below describe
/etc/init.d/firewall reload
```
- If you want to disable all traffic that is not protected by VPN, run the following command. This way you won’t have an Internet connection at all if VPN disconnects. If you choose not to do this step, your real IP will be exposed if the VPN disconnects.
+ Vil man deaktivere al trafik, som ikke er beskyttes af VPN, eksekvér flg. kommando. På denne måde vil der slet ikke være internetforbindelse, hvis VPN afbrydes. Vælger man ikke at udføre dette trin, vil den reelle IP blive afsløret, hvis VPN afbrydes.
```shell
uci del_list firewall.@zone[1].network='wan'
@@ -219,7 +219,7 @@ You can do it in the web interface or in the command line. Steps below describe
/etc/init.d/firewall reload
```
- If you’ve changed your mind and want to allow direct traffic, run the following command:
+ Ombestemmer man sig og vil tillade direkte trafik, eksevér da flg. kommando:
```shell
uci add_list firewall.@zone[1].network='wan'
@@ -228,11 +228,11 @@ You can do it in the web interface or in the command line. Steps below describe
/etc/init.d/firewall reload
```
-## 7) Set up automatic launch for AdGuard VPN CLI
+## 7) Opsæt automatisk start af AdGuard VPN CLI
-To automatically launch AdGuard VPN CLI after rebooting the router, create a file at `…/etc/init.d/adguardvpn`.
+For automatisk at starte AdGuard VPN CLI efter genstart af routeren, opret en fil på `…/etc/init.d/adguardvpn`.
-Paste this into the file:
+Indsæt følgende i filen:
```text
#!/bin/sh /etc/rc.common
@@ -251,7 +251,7 @@ stop() {
}
```
-Run this to grant access for auto-launch and enable it:
+Eksekvér dette for at give adgang til — og aktivere — auto-start:
```jsc
chmod +x /etc/init.d/adguardvpn
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..46acb82729 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -1,12 +1,14 @@
---
-title: Setting up on a router
+title: Opsætning på en router
sidebar_position: 1
---
-Learn how to set up AdGuard VPN for Linux on a router.
+Læs, hvordan AdGuard VPN til Linux opsættes på en router.
-- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
+- [Vejledning til Keenetic-routere](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Vejledning til OpenWRT-routere](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-More instructions for other router brands and firmware options will be added here soon.
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
+
+Flere vejledninger til andre routermærker og firmwaremuligheder tilføjes snart her.
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-mac/overview.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-mac/overview.md
index fe9c228c4b..33c68e1a93 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-mac/overview.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-mac/overview.md
@@ -39,12 +39,12 @@ Man kan ikke blot føje websteder til Undtagelser, men også vælge blandt liste
Undtagelser-listen kan nemt opsættes. Har man tilføjet et domæne og nogle af dets underdomæner, grupperes disse under roddomænet. Ved tilføjelse af et roddomæne (`eksempel.com`), tilføjes også dets maske (`*.eksempel.com`).
-:::info Browsers added to Exclusions
+:::info Webbrowsere føjet til Undtagelser
-Starting with the version 2.4, all browsers are automatically added to the list of exclusions when the VPN is active only for selected apps and websites. This change brings more convenience for users who were often confused and didn’t know whether to consider their browsers as apps or not. It applies under the following conditions:
+Fra og med version 2.4 føjes alle webbrowsere automatisk til listen over undtagelser, når VPN kun er aktiv for udvalgte apps og websteder. Denne ændring er mere bekvemmelig for brugere, som ofte var forvirrede og ikke vidste, om deres webbrowsere skulle betragtes som apps eller ej. Det gælder under flg. betingelser:
-- The user has installed AdGuard VPN for the first time
-- The user did not modify the Exclusions settings prior to v2.4
+- Brugeren har installeret AdGuard VPN for første gang
+- Brugeren har ikke ændret indstillingerne for undtagelser før v2.4
:::
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/installation.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/installation.md
index c9194bcd69..cb72a34a07 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/installation.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/installation.md
@@ -43,7 +43,7 @@ Fungerer alm. afinstallation af en eller anden grund ikke, kan en avanceret meto
:::
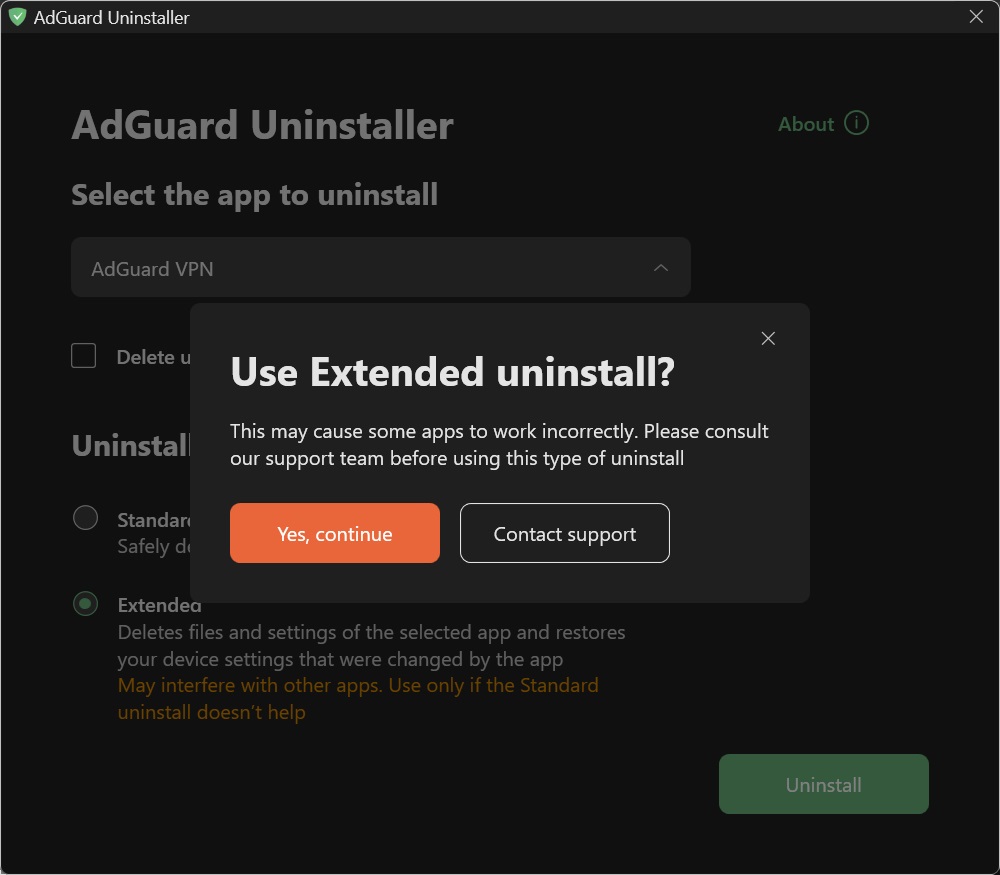
-1. Vælg *AdGuard VPN* og afinstallationstypen *Udvidet*, og klik dernæst på *Afinstallér*. Click *Yes, continue* in the window prompt:
+1. Vælg *AdGuard VPN* og afinstallationstypen *Udvidet*, og klik dernæst på *Afinstallér*. Klik på *Ja, fortsæt* i vinduesprompten:
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/overview.md b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/overview.md
index 5cc55d983c..be52df78c8 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/overview.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/overview.md
@@ -43,12 +43,12 @@ Når domæner tilføjes manuelt, bør der tages højde for visse detaljer. Undta
Vi anbefaler at bruge indstillingen **Fra listen**. Websteder grupperes i otte kategorier: Sociale netværk, Messengers, Video- og musikstreamingtjenester, Spil, Shopping, Søgemaskiner og Arbejdskommunikationsværktøjer. Vi har placeret de mest populære tjenester dér, inkl. alle domænenavne og underdomæner relateret til hver platform.
-:::info Browsers added to Exclusions
+:::info Webbrowsere føjet til Undtagelser
-Starting with the version 2.4, all browsers are automatically added to the list of exclusions when the VPN is active only for selected apps and websites. This change brings more convenience for users who were often confused and didn’t know whether to consider their browsers as apps or not. It applies under the following conditions:
+Fra og med version 2.4 føjes alle webbrowsere automatisk til listen over undtagelser, når VPN kun er aktiv for udvalgte apps og websteder. Denne ændring er mere bekvemmelig for brugere, som ofte var forvirrede og ikke vidste, om deres webbrowsere skulle betragtes som apps eller ej. Det gælder under flg. betingelser:
-- The user has installed AdGuard VPN for the first time
-- The user did not modify the Exclusions settings prior to v2.4
+- Brugeren har installeret AdGuard VPN for første gang
+- Brugeren har ikke ændret indstillingerne for undtagelser før v2.4
:::
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/general/how-vpn-works.md b/i18n/da/docusaurus-plugin-content-docs/current/general/how-vpn-works.md
index 4beb65f50f..ed13bf2f8a 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/general/how-vpn-works.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/general/how-vpn-works.md
@@ -43,7 +43,7 @@ Ud over disse VPN-protokoller findes der andre (f.eks. TLS, SSTP, IKEv2), men de
-AdGuard VPN har også sin egen [_protokol_](/general/adguard-vpn-protokol). En af dens fordele er, at trafik sendt vha. AdGuard VPN-protokollen er svær at skelne fra almindelig trafik. The VPN tunnel looks like normal HTTPS traffic, making it extremely difficult to detect and block. Den er desuden baseret på mekanismerne i den moderne HTTP/2-protokol, hvilket sikrer høj forbindelseshastighed.
+AdGuard VPN har også sin egen [_protokol_](/general/adguard-vpn-protokol). En af dens fordele er, at trafik sendt vha. AdGuard VPN-protokollen er svær at skelne fra almindelig trafik. VPN-tunnelen ligner normal HTTPS-trafik, hvilket gør den ekstremt svært at opdage og blokere. Den er desuden baseret på mekanismerne i den moderne HTTP/2-protokol, hvilket sikrer høj forbindelseshastighed.
@@ -69,7 +69,7 @@ Vores VPN-tjeneste har flere vigtige [fordele](/general/why-adguard-vpn):
- [_Proprietær VPN-protokol_](/general/adguard-vpn-protocol), der fungerer stabilt selv på en langsom internetforbindelse og camouflerer sig som normal trafik, hvilket gør den sværere at spore og blokere
-- [_Nul logning-politik_](https://adguard-vpn.com/privacy.html), hvilket betyder, at ingen personlige data kan overføres til tredjeparter, fordi AdGuard VPN aldrig indsamler sådanne data
+- [_Nul logning-politik_](https://adguard-vpn.com/privacy.html), hvilket betyder, at ingen personlige informationer kan deles med tredjeparter, da de ikke indsamles af AdGuard VPN
- _Flere end 50 VPN-servere i snesevis af lande_
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/general/set-up-adguard-vpn-on-your-router.md b/i18n/da/docusaurus-plugin-content-docs/current/general/set-up-adguard-vpn-on-your-router.md
index 4dc91a3f8d..22080da6ce 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/general/set-up-adguard-vpn-on-your-router.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/general/set-up-adguard-vpn-on-your-router.md
@@ -3,11 +3,11 @@ title: Sådan opsættes AdGuard VPN på en router
sidebar_position: 8
---
-By setting up AdGuard VPN on your router, you can protect your data on devices where you cannot install VPN apps, such as smart TVs, smart media devices, and game consoles.
+Ved at opsætte AdGuard VPN på routeren kan man beskytte sine data på enheder, hvor VPN-apps ikke kan installeres, såsom smarte medieenheder og spillekonsoller.
:::note
-This option is only available if you have an AdGuard VPN subscription and your router supports IPsec in its _VPN Client_ (**Not** _VPN Server_) settings.
+Denne mulighed er kun tilgængelig med et AdGuard VPN-abonnement og en router, hvis indstillinger understøtter IPsec for _VPN-klient_ (**ikke** _VPN-server_).
:::
@@ -33,7 +33,7 @@ This option is only available if you have an AdGuard VPN subscription and your r
5. Aktivér _VPN-klient_ og klik på _Tilføj VPN-server_.
-6. Select IPsec-client (it may for some router brands be called IKEv2; not L2TP/IPsec).
+6. Vælg IPsec-klient (den kan på visse routermærker hedde IKEv2; ikke L2TP/IPsec).
7. Angiv legitimationsoplysningerne oprettet på trin 3.
@@ -51,11 +51,11 @@ Routerindstillingerne vil skulle opdateres, hvis der ændres VPN-serverlokation.
- Med AdGuard VPN på routeren har hverken VPN-udbyderen eller nogen andre adgang til internetaktiviteten
- Installation af AdGuard VPN på routeren sikrer hele netværket, hvilket betyder, at alle enheder, som er tilsluttet det, er beskyttet
-- You can enhance security and protect your data on devices where it’s not possible to install AdGuard VPN apps — smart TVs, smart media devices, and game consoles
+- Man kan forbedre sikkerheden og beskytte sine data på enheder, hvor det ikke er muligt at installere AdGuard VPN-apps — smarte medieenheder og spillekonsoller
## Enheder, som kan tilsluttes en router med AdGuard VPN
-- **PlayStation, Xbox, and Nintendo Switch**: To enjoy seamless online gaming and enhanced security on PS4, PS5, Xbox One, Xbox Series, and Nintendo Switch, [set up AdGuard VPN on your router](#how-to-set-up-adguard-vpn-on-your-router) and connect your console to it
+- **PlayStation, Xbox og Nintendo Switch**: For problemfri onlinespil og forbedret sikkerhed på PS4, PS5, Xbox One, Xbox Series og Nintendo Switch, [opsæt AdGuard VPN på routeren](#how-to-set-up-adguard-vpn-on-your-router) og forbind konsollen til den
- **Apple TV**: Følg vejledningen for at [opsætte AdGuard VPN på routeren](#how-to-set-up-adguard-vpn-on-your-router) og dernæst tilslutte Apple TV'et
@@ -71,8 +71,8 @@ Routerindstillingerne vil skulle opdateres, hvis der ændres VPN-serverlokation.
2. Hvis man allerede har en AdGuard-konto, log ind på kontoen. Er man ny AdGuard-bruger, angiv en e-mailadresse og følg skærmvejledningen
3. Åbn appen, vælg den ønskede lokation, og opret forbindelse
-## Routers known to be incompatible with AdGuard VPN
+## Routere kendt for at være inkompatible med AdGuard VPN
- **ASUS**
- - Only has IPsec in the _VPN Server_ settings, and not in the correct _VPN Fusion_/_VPN Client_ settings
+ - Har kun IPsec i _VPN Server_-indstillingerne og ikke i de korrekte _VPN Fusion_/_VPN Client_-indstillinger
- **FRITZ!Box**
diff --git a/i18n/da/docusaurus-plugin-content-docs/current/general/vpn-issues.md b/i18n/da/docusaurus-plugin-content-docs/current/general/vpn-issues.md
index d9e05e9433..b76963c923 100644
--- a/i18n/da/docusaurus-plugin-content-docs/current/general/vpn-issues.md
+++ b/i18n/da/docusaurus-plugin-content-docs/current/general/vpn-issues.md
@@ -3,7 +3,7 @@ title: 'Sådan benyttes AdGuard VPN i lande med internetrestriktioner'
sidebar_position: 10
---
-In certain regions, such as China, Iran, and Russia, users might experience problems connecting to AdGuard VPN. Her er de tiltag, som kan hjælpe.
+I visse regioner, såsom Kina, Iran og Rusland, kan brugere have problemer med at oprette forbindelse til AdGuard VPN. Her er de tiltag, som kan hjælpe.
## Adgang til AdGuard VPNs websted
@@ -25,7 +25,7 @@ Efter man har ændret region eller knyttet en anden konto til App Store, [instal
### AdGuard VPN til Android
-If you experience problems with Google Play, download the APK file from [AdGuard VPN’s mirror website](https://adguardvpn-help.com/android/overview.html).
+Opleves problemer på Google Play, download i stedet APK-filen fra [AdGuard VPNs spejlwebsted](https://adguardvpn-help.com/android/overview.html).
### AdGuard VPN til Mac
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index bb63c2a240..3ba648fbf9 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: So richten Sie AdGuard VPN für Linux auf einem Keenetic-Router ein
-sidebar_position: 3
+sidebar_position: 2
---
:::info Systemanforderungen
@@ -67,7 +67,7 @@ Ersetzen Sie `192.168.1.1` durch die IP-Adresse Ihres Routers.
1. Wenn Sie sich zum ersten Mal über SSH mit dem Router verbinden, werden Sie eine Meldung sehen wie diese:
-```bash
+```text
Die Authentizität des Hosts '192.168.1.1 (192.168.1.1)' konnte nicht festgestellt werden.
Der Fingerabdruck des ECDSA-Schlüssels lautet SHA256:...
Möchten Sie die Verbindung wirklich fortsetzen (Ja/Nein/[Fingerabdruck])?
@@ -121,13 +121,13 @@ Führen Sie in Ihrem SSH-Client den folgenden Code aus, um die für AdGuard VPN
opkg install curl sudo ca-certificates
```
-Öffnen Sie den Ordner `cd/opt` und führen Sie das AdGuard VPN CLI Installationsskript aus:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-Auf die Frage `Möchten Sie die Binärdatei mit /usr/local/bin verknüpfen?`, antworten Sie mit `y`. Wenn Sie die Binärdatei nicht verknüpfen können, führen Sie diese Zeile aus:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Mit VPN verbinden
- Importieren Sie das SSL-Zertifikat vor der Verbindung, indem Sie diesen Befehl ausführen:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
Dies muss vor jeder Sitzung ausgeführt werden.
@@ -233,15 +234,15 @@ Dieser Schritt dient dazu, Firewall-Regeln auf einem Keenetic-Router zu konfigur
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ Dieser Schritt dient dazu, Firewall-Regeln auf einem Keenetic-Router zu konfigur
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
Dadurch wird ein neues Shell-Skript mit dem Namen `001-adguardvpn.sh` im Ordner `/opt/etc/ndm/netfilter.d/` erstellt, in dem netzwerkbezogene Skripte normalerweise auf einem Keenetic-Router gespeichert werden.
Das Skript erstellt eine benutzerdefinierte Firewall-Regel, um sicherzustellen, dass der Datenverkehr aus Ihrem LAN (`br0`) über die AdGuard VPN-Schnittstelle (`tun0`) geleitet wird. Er bereinigt zunächst alle früheren Regeln, die sich auf diese Konfiguration beziehen, und erstellt anschließend neue Regeln, um den Datenverkehr entsprechend zu leiten.
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index 6d2e5544a1..3e940edf0d 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: So richten Sie AdGuard VPN für Linux auf einem OpenWRT-Router ein
-sidebar_position: 2
+sidebar_position: 3
---
:::info Systemanforderungen
diff --git a/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index 737756795c..2333dc9054 100644
--- a/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/de/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Erfahren Sie, wie Sie AdGuard VPN für Linux auf einem Router einrichten.
+- [Anleitung für Keenetic-Router](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Anleitung für OpenWRT-Router](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Anleitung für Keenetic-Router](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
Weitere Anleitungen für andere Router-Marken und Firmware-Optionen werden hier bald hinzugefügt.
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/es/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/fi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/fr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/hr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/it/docusaurus-plugin-content-docs/current.json b/i18n/it/docusaurus-plugin-content-docs/current.json
index 6bd8008202..95d909ebb0 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current.json
+++ b/i18n/it/docusaurus-plugin-content-docs/current.json
@@ -44,7 +44,7 @@
"description": "The label for category AdGuard VPN browser extensions in sidebar sidebar"
},
"sidebar.sidebar.category.solving-problems": {
- "message": "risoluzione dei problemi",
+ "message": "risoluzione-dei-problemi",
"description": "The label for category solving-problems in sidebar sidebar"
},
"sidebar.sidebar.category.AdGuard VPN for Linux": {
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-ios/overview.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-ios/overview.md
index 82125e465a..8ac3c3a7fc 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-ios/overview.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-ios/overview.md
@@ -65,7 +65,7 @@ You can do it in four steps:
To open General settings:
-1. Tap the Settings icon (⚙) in the bottom right corner of the app’s main screen.
+1. Toccare il pulsante Impostazioni (⚙) nell'angolo in basso a destra della schermata principale dell'app.
2. Tap *General*.
Here, you can configure AdGuard VPN for iOS as you need using different options: *DNS server*, *Theme*, *Advanced*, *Send technical and interaction data* and *Kill Switch*.
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/it/docusaurus-plugin-content-docs/current/general/why-adguard-vpn.md b/i18n/it/docusaurus-plugin-content-docs/current/general/why-adguard-vpn.md
index 8b76690766..4c7154acef 100644
--- a/i18n/it/docusaurus-plugin-content-docs/current/general/why-adguard-vpn.md
+++ b/i18n/it/docusaurus-plugin-content-docs/current/general/why-adguard-vpn.md
@@ -31,7 +31,7 @@ Consigliamo di utilizzare un server di AdGuard DNS: blocca gli annunci e i tracc
-## 4. Località ultraveloci
+## 4. Posizioni ultraveloci

diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/ja/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/ko/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/nl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/pt-BR/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/pt/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 4a69401a02..322b4b9254 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: Как настроить AdGuard VPN для Linux на роутере Keenetic
-sidebar_position: 3
+sidebar_position: 2
---
:::info Системные требования
@@ -67,7 +67,7 @@ ssh admin@192.168.1.1
1. Если вы впервые подключаетесь к роутеру через SSH, вы увидите такое сообщение:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ ssh admin@192.168.1.1
opkg install curl sudo ca-certificates
```
-Перейдите в папку `cd/opt` и запустите скрипт установки AdGuard VPN CLI:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-На вопрос `Хотите ли вы связать двоичный файл с /usr/local/bin?` ответьте `y`. Если вам не удалось связать двоичный файл, выполните эту строку:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Подключитесь к VPN
- Перед подключением импортируйте SSL-сертификат, выполнив следующую команду:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
Это необходимо делать перед каждым сеансом.
@@ -213,7 +214,7 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
adguardvpn-cli --help-all
```
-4. Введите `yes` на вопрос «Хотите ли вы установить маршруты по умолчанию в режиме TUN?»
+4. Введите `yes` на вопрос Would you like to set default routes in TUN mode?
AdGuard VPN CLI создаст интерфейс tun0 для VPN-туннелирования
@@ -233,15 +234,15 @@ AdGuard VPN CLI создаст интерфейс tun0 для VPN-туннели
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ AdGuard VPN CLI создаст интерфейс tun0 для VPN-туннели
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
Это создаст новый скрипт оболочки с именем `001-adguardvpn.sh` в каталоге `/opt/etc/ndm/netfilter.d/`, где на роутере Keenetic обычно хранятся скрипты, связанные с сетью.
Скрипт создаёт пользовательское правило фаервола, чтобы гарантировать, что трафик из вашей локальной сети (`br0`) будет направляться через интерфейс AdGuard VPN (`tun0`). Сначала он очищает все предыдущие правила, связанные с этой конфигурацией, а затем настраивает новые правила для правильной маршрутизации трафика.
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index 7bf4a7fe6f..24010b7537 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: Как настроить AdGuard VPN для Linux на роутере OpenWRT
-sidebar_position: 2
+sidebar_position: 3
---
:::info Системные требования
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index 55017160ca..feca742725 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Узнайте, как настроить AdGuard VPN для Linux на роутере.
+- [Инструкции для роутеров Keenetic](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Инструкции для роутеров OpenWRT](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Инструкции для роутеров Keenetic](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
В ближайшее время сюда будут добавлены инструкции для других марок роутеров и вариантов прошивок.
diff --git a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/overview.md b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/overview.md
index c11d65ef38..51f44f3238 100644
--- a/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/overview.md
+++ b/i18n/ru/docusaurus-plugin-content-docs/current/adguard-vpn-for-windows/overview.md
@@ -120,7 +120,7 @@ WinTun — это драйвер маршрутизации трафика, об
Во вкладке **О программе** вы найдёте информацию о текущей версии AdGuard VPN для Windows, кнопку проверки наличия обновлений, а также ссылки: на сайт AdGuard VPN, Лицензионное соглашение и Политику конфиденциальности.
-### Личный кабинет
+### Аккаунт
Здесь размещена информация о статусе вашей лицензии, а также ссылка на ваш личный кабинет AdGuard, где вы можете купить новую подписку, улучшить или продлить уже существующую.
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/sk/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/sl/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/sr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index 2f85dffbff..b05b48405f 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index da7f98e824..891bba0958 100644
--- a/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/tr/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Linux için AdGuard VPN'in yönlendiriciye nasıl kurulacağını öğrenin.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
Diğer yönlendirici markaları ve donanım yazılımı seçenekleri için daha fazla talimat yakında buraya eklenecektir.
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-ios/installation.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-ios/installation.md
index 0cad3c0dad..9a75272e66 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-ios/installation.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-ios/installation.md
@@ -5,41 +5,39 @@ sidebar_position: 2
## System requirements
-AdGuard VPN can only be installed on devices with **iOS 14.2 and iPadOS 14.2 or later**.
+AdGuard VPN chỉ có thể được cài đặt trên các thiết bị có **iOS 14.2 và iPadOS 14.2 hoặc phiên bản mới hơn**.
### If AdGuard VPN has been removed from the App Store
-If you don’t see AdGuard VPN in the App Store, try changing the country or region in your Apple ID settings. Another option is to create a new Apple account and connect it to the App Store. [Instructions for both cases](/adguard-vpn-for-ios/solving-problems/app-store) are described in a separate article.
-
-After you change the region or link a different account to the App Store, [install AdGuard VPN](https://apps.apple.com/us/app/adguard-vpn-unlimited-fast/id1525373602).
+Nếu bạn không thấy AdGuard VPN trong App Store, hãy thử thay đổi quốc gia hoặc vùng trong cài đặt Apple ID của bạn. Một tùy chọn khác là tạo một tài khoản Apple mới và kết nối nó với App-Store. [Hướng dẫn cho cả hai trường hợp](/adguard-vpn-for-ios/solving-problems/app-store) được mô tả trong một bài viết riêng.
## How to install AdGuard VPN for iOS
-You can download and install the *AdGuard VPN for iOS* app for free in the *App Store*.
+Bạn có thể tải xuống và cài đặt miễn phí ứng dụng *AdGuard VPN cho iOS* trong *Cửa hàng ứng dụng*.
-To do this, [go to App Store](https://agrd.io/ios_vpn) and tap *GET*.
+Để làm điều này, [truy cập Cửa hàng ứng dụng](https://agrd.io/ios_vpn) và nhấn vào *NHẬN*.
-Or you can use App Store’s search to find AdGuard VPN:
+Hoặc bạn có thể sử dụng chức năng tìm kiếm của Cửa hàng ứng dụng để tìm AdGuard VPN:
-1. Open the *App Store* app on your iOS device and tap *Search* 🔍 in the bottom right corner of the screen.
+1. Mở ứng dụng *Cửa hàng ứng dụng* trên thiết bị iOS của bạn và nhấn vào *Tìm kiếm* 🔍 ở góc dưới bên phải của màn hình.
- 
+ 
-1. Next, in the search bar, start typing *"AdGuard"* and select *"adguard vpn"* from the list of suggested options.
+1. Tiếp theo, trong thanh tìm kiếm, bắt đầu nhập *"AdGuard"* và chọn *"adguard vpn"* từ danh sách các tùy chọn được đề xuất.
- 
+ 
-1. Select *AdGuard VPN - Unlimited & Fast* from the list of suggested apps and tap *GET*. If necessary, enter your Apple ID account password in the opened window.
+1. Select *AdGuard VPN - Unlimited & Fast* from the list of suggested apps and tap *GET*. Nếu cần, hãy nhập mật khẩu tài khoản Apple ID của bạn trong cửa sổ vừa mở.
1. Wait for the download to finish and tap *OPEN* to open the app.
-That’s it! AdGuard VPN for iOS has been successfully installed on your device.
+Xong rồi! AdGuard VPN cho iOS đã được cài đặt thành công trên thiết bị của bạn.
-## How to uninstall AdGuard VPN for iOS
+## Cách gỡ cài đặt AdGuard VPN cho iOS
-If you have decided to delete AdGuard VPN for iOS, find and hold its icon on the home screen. In the menu that opens, tap *Remove App*.
+Nếu bạn đã quyết định xóa AdGuard VPN cho iOS, hãy tìm và giữ biểu tượng của nó trên màn hình chính. Trong danh sách xuất hiện, nhấn vào *Gỡ bỏ ứng dụng*. Trong menu xuất hiện, nhấn vào *Gỡ bỏ ứng dụng*.
-
+
-You can learn more about the AdGuard VPN app for iOS in [this article](adguard-vpn-for-ios/overview).
+Bạn có thể tìm hiểu thêm về ứng dụng AdGuard VPN cho iOS trong [bài viết này](adguard-vpn-for-ios/overview).
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/vi/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/zh-CN/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
new file mode 100644
index 0000000000..d6a179373d
--- /dev/null
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md
@@ -0,0 +1,283 @@
+---
+title: How to set up AdGuard VPN for Linux on an Asuswrt-Merlin router
+sidebar_position: 4
+---
+
+:::info System requirements
+
+1. AdGuard VPN CLI requires at least 22 MB of free storage space on your router’s disk or external USB after installing necessary packages.
+2. **Asuswrt-Merlin firmware**: Make sure your router is running the Asuswrt-Merlin firmware.
+3. **USB drive**: A USB drive formatted in a native Linux file system (ext2, ext3, or ext4). We will go through the formatting process in this guide.
+
+:::
+
+## 1. Determine your router’s IP address
+
+The default IP address for most routers is `192.168.1.1` or `192.168.0.1`. If you’ve changed the IP address or if you’re unsure, you can find it by checking the IP configuration on a connected device.
+
+### On Windows
+
+1. Open Command Prompt:
+
+ ```bash
+ ipconfig
+ ```
+
+2. Look for the _Default Gateway_ under your active network connection. This is your router’s IP address.
+
+### On Mac/Linux
+
+1. Open Terminal and run this command for Linux:
+
+ ```bash
+ ip route | grep default
+ ```
+
+ Or this one for Mac:
+
+ ```bash
+ route -n get default
+ ```
+
+2. Look for the _default_ entry. The IP address next to it is your router’s IP address.
+
+## 2) Make sure SSH and **JFFS custom scripts are e**nabled on the router
+
+First, make sure that SSH access is enabled on your router. This setting is usually found in the router’s web interface. JFFS custom scripts will be used to set routing rules.
+
+1. Log in to the web interface. This is usually accessible via a web browser at [`http://192.168.1.1`](http://192.168.1.1/). Otherwise, replace [`192.168.1.1`](http://192.168.1.1/) with your router’s IP address.
+
+2. Scroll down to **Advanced settings**, **Administration** → **System**.
+
+3. Scroll to **Service**, click **Enable SSH** → **LAN**.
+
+4. Select **22** in **Port** and **Yes** in **Allow Password Login**.
+
+5. Go up to **Persistent JFFS2 partition** and enable **JFFS custom scripts and configs**.
+
+6. Click **Apply** at the bottom of the page.
+
+## 3) Use an SSH client to connect to the router
+
+You’ll need an SSH client. Most Linux and macOS systems come with an SSH client pre-installed. For Windows, you can use PowerShell, the built-in SSH client in Windows 10/11, or a third-party application like PuTTY.
+
+### Built-in SSH client (Linux/macOS/Windows 10/11)
+
+1. Open Terminal or PowerShell.
+
+2. Run the SSH command:
+
+ ```bash
+ ssh admin@192.168.1.1
+ ```
+
+ Replace `192.168.1.1` with your router’s IP address and `admin` with your admin username.
+
+3. If this is your first time connecting to the router via SSH, you’ll see a message like this:
+
+ ```text
+ The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
+ ECDSA key fingerprint is SHA256:...
+ Are you sure you want to continue connecting (yes/no/[fingerprint])?
+ ```
+
+ Type `yes` and press Enter.
+
+4. Enter the router’s password when prompted. The SSH login username and password are the same as the admin credentials.
+
+### PuTTY (Windows below 10)
+
+1. Download and install PuTTY from [the official website](https://www.putty.org/).
+2. Open PuTTY.
+3. In the _**Host Name (or IP address)**_ field, enter your router’s IP address (e.g., `192.168.1.1`).
+4. Make sure the _**Connection type**_ is set to SSH.
+5. Click _**Open**_.
+6. When the terminal window opens, enter the router’s credentials. The SSH login username and password are the same as the admin credentials.
+
+## 4) Install Entware using SSH
+
+Once logged into your SSH client, you can use various commands to interact with your router’s Linux-based operating system. To proceed, you will need to install Entware OPKG Manager. It allows you to install third-party software packages to expand router capabilities. Skip to the next step if you already have it installed.
+
+Note that you cannot use both Optware (outdated alternative) and Entware at the same time.
+
+The Asus DownloadMaster is based on Optware, and therefore is not compatible with Entware. You will have to uninstall DownloadMaster and look at the alternatives provided by Entware.
+
+After uninstalling, make sure that "asusware.arm" or "asusware.\*" dir on the mounted disk partition is deleted. Otherwise, Entware won't work properly. After uninstalling DownloadMaster, make sure the router is rebooted.
+
+You will need to plug a USB disk that's formatted in a native Linux file system (ext2, ext3 or ext4). To format a disk, use amtm. Plug a USB disk into your router, then start amtm with:
+
+```bash
+amtm
+```
+
+Use this option to format a disk and mount it to router:
+
+```bash
+fd
+```
+
+Go through the formatting process and select the recommended options. All files from the USB disk will be deleted. For this setup to work, USB disk should always stay connected.
+
+After mounting your USB, the router will reboot. To start the installation process, first reconnect to your router over SSH.
+
+Then launch the amtm application by simply running:
+
+```bash
+amtm
+```
+
+The menu will offer you the option `ep` to initiate the Entware installation.
+
+If you are running a firmware version older than 384.15 (or 384.13_4 for the RT-AC87U and RT-AC3200), then you start the installation by running the following command instead.
+
+```bash
+entware-setup.sh
+```
+
+If the entware-setup.sh script is not found, download and run the following script to install Entware:
+
+```bash
+wget -O - http://bin.entware.net/armv7sf-k3.2/installer/generic.sh | sh
+```
+
+Exit amtm by pressing `e`.
+
+## 5. Install AdGuard VPN CLI
+
+Update the package lists:
+
+```bash
+opkg update
+```
+
+Install required packages:
+
+```bash
+opkg install curl ca-certificates
+```
+
+Go to /opt folder by running `cd /opt` and run the AdGuardVPN CLI installation script:
+
+```bash
+curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
+```
+
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `y`. If failed to link the binary, run this line:
+
+```bash
+ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
+```
+
+Import the SSL certificate and the tun module and set an alternative folder for the user directory. By default, it will be stored in /tmp and you’ll lose your settings after a reboot. Run this before each new session.
+
+```bash
+export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+export HOME=/opt/home/admin
+modprobe tun
+```
+
+## 6. Set up AdGuard VPN CLI
+
+1. Log in to your account
+
+ To use AdGuard VPN for Linux, you need an AdGuard account.
+
+ You can sign up on our [website](https://auth.adguard.info/login.html) or in the Terminal.
+
+ To sign up or log in, type:
+
+ ```jsx
+ adguardvpn-cli login
+ ```
+
+2. Connect to VPN
+
+ Select a VPN server location that best suits your needs.
+
+ In general, the closer the server, the faster the connection.
+
+ To view available locations, type:
+
+ ```jsx
+ adguardvpn-cli list-locations
+ ```
+
+ To connect to a specific location, type:
+
+ ```jsx
+ adguardvpn-cli connect -l LOCATION_NAME
+ ```
+
+ Replace LOCATION_NAME with the city, country, or ISO code of the location you want to connect to.
+
+ For quick connect, type:
+
+ ```jsx
+ adguardvpn-cli connect
+ ```
+
+ AdGuard VPN will choose the fastest available location and remember it for future quick connections.
+
+ Enter `yes` when asked “Would you like to set default routes in TUN mode?”
+
+ AdGuard VPN CLI will create a tun0 interface for VPN tunneling.
+
+3. Adjust your settings
+
+ Get a list of all available AdGuard VPN commands and customize the VPN client to your needs.
+
+ To view all commands, type:
+
+ ```jsx
+ adguardvpn-cli --help-all
+ ```
+
+## 7) Set up your firewall rules and auto-launch for AdGuard VPN
+
+This step configures firewall rules on an Asuswrt-Merlin router to route traffic through AdGuard VPN.
+
+1. Create a new script by running the following command:
+
+ ```bash
+ cat << 'EOF' > /jffs/scripts/wan-event
+ #!/bin/sh
+
+ if [ "$2" = "connected" ]; then
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ /opt/adguardvpn_cli/adguardvpn-cli connect &
+ for ipt in iptables ip6tables; do
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ done
+ exit 0
+ fi
+ EOF
+ ```
+
+ And make it executable:
+
+ ```bash
+ chmod a+rx /jffs/scripts/wan-event
+ ```
+
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
+ This script will ensure that all traffic goes through the VPN tunnel. After rebooting or reconnecting to the Internet AdGuard VPN will connect automatically to your last used location.
+
+2. Reboot your router to finish the setup.
+
+ Congrats! Now you have a router secured with AdGuard VPN.
+
+ If you want to SSH into your router again to send any commands to AdGuard VPN, make sure to run this first:
+
+ ```bash
+ export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
+ modprobe tun
+ ```
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
index 787f2880af..bc13684383 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on a Keenetic router
-sidebar_position: 3
+sidebar_position: 2
---
:::info System requirements
@@ -67,7 +67,7 @@ Replace `192.168.1.1` with your router’s IP address.
1. If this is your first time connecting to the router via SSH, you’ll see a message like this:
-```bash
+```text
The authenticity of host '192.168.1.1 (192.168.1.1)' can't be established.
ECDSA key fingerprint is SHA256:...
Are you sure you want to continue connecting (yes/no/[fingerprint])?
@@ -121,13 +121,13 @@ In your SSH client, execute the following code to install the packages required
opkg install curl sudo ca-certificates
```
-Go to `cd/opt` folder and run the AdGuard VPN CLI installation script:
+Go to the `/opt` folder by typing `/cd opt` and run the AdGuard VPN CLI installation script:
```bash
curl -fsSL https://raw.githubusercontent.com/AdguardTeam/AdGuardVPNCLI/master/scripts/release/install.sh | sh -s -- -v
```
-When asked `Would you like to link the binary to /usr/local/bin?`, reply `y`. If you fail to link the binary, run this line:
+When asked “Would you like to link the binary to /usr/local/bin?“, reply `n` and run this line:
```bash
ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
@@ -169,10 +169,11 @@ ln -s /opt/adguardvpn_cli/adguardvpn-cli /opt/bin
2. Connect to VPN
- Import the SSL certificate before connecting by running this command:
+ For Keenetic routers, be sure to import the SSL certificate and select a folder for the user directory by running this command before connecting:
```bash
export SSL_CERT_FILE=/opt/etc/ssl/certs/ca-certificates.crt
+ export HOME=/opt/home/admin
```
This must be done before each session.
@@ -233,15 +234,15 @@ This step is designed to configure firewall rules on a Keenetic router to route
```bash
- cat << EOF > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
+ cat << 'EOF' > /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
#!/opt/bin/sh
for ipt in iptables ip6tables; do
- \$ipt -D FORWARD -j ADGUARD_FORWARD || true
- \$ipt -F ADGUARD_FORWARD || true
- \$ipt -X ADGUARD_FORWARD || true
- \$ipt -N ADGUARD_FORWARD
- \$ipt -I FORWARD -j ADGUARD_FORWARD
- \$ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
+ $ipt -D FORWARD -j ADGUARD_FORWARD || true
+ $ipt -F ADGUARD_FORWARD || true
+ $ipt -X ADGUARD_FORWARD || true
+ $ipt -N ADGUARD_FORWARD
+ $ipt -I FORWARD -j ADGUARD_FORWARD
+ $ipt -A ADGUARD_FORWARD -i br0 -o tun0 -j ACCEPT
done
EOF
```
@@ -252,6 +253,8 @@ This step is designed to configure firewall rules on a Keenetic router to route
chmod +x /opt/etc/ndm/netfilter.d/001-adguardvpn.sh
```
+ If you have more brX interfaces, make sure to include them in the script as well to route their traffic. Alternatively, make sure to specify a different routing rule for those interfaces.
+
This will create a new shell script named `001-adguardvpn.sh` in the `/opt/etc/ndm/netfilter.d/` directory, which is where network-related scripts are typically stored on a Keenetic router.
The script creates a custom firewall rule to ensure that traffic from your LAN (`br0`) is routed through the AdGuard VPN interface (`tun0`). It first cleans up any previous rules related to this configuration, then sets up new rules to direct the traffic appropriately.
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
index ba3d5e5775..7e0b75c637 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md
@@ -1,6 +1,6 @@
---
title: How to set up AdGuard VPN for Linux on an OpenWRT router
-sidebar_position: 2
+sidebar_position: 3
---
:::info System requirements
diff --git a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
index cbdacbf1ae..4b4b867f79 100644
--- a/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
+++ b/i18n/zh-TW/docusaurus-plugin-content-docs/current/adguard-vpn-for-linux/setting-up-on-a-router/setting-up-on-a-router.md
@@ -5,8 +5,10 @@ sidebar_position: 1
Learn how to set up AdGuard VPN for Linux on a router.
+- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+
- [Instructions for OpenWRT routers](/adguard-vpn-for-linux/setting-up-on-a-router/openwrt.md)
-- [Instructions for Keenetic routers](/adguard-vpn-for-linux/setting-up-on-a-router/keenetic.md)
+- [Instructions for Asuswrt-Merlin routers](/adguard-vpn-for-linux/setting-up-on-a-router/asuswrt-merlin.md)
More instructions for other router brands and firmware options will be added here soon.